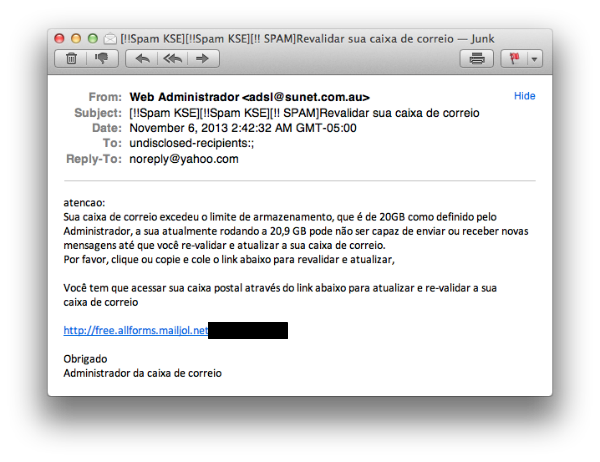
I just received a spam e-mail in Portuguese stating that my mailbox had exceeded its maximum storage.
Please click on or copy the link below to revalidate and to update it.
You have to access your email box via the link below to update and revalidate your email inbox.
Thank you,
Email Administrator.
It’s classic phishing, abusing Free online forms. If you click, you will see the next set of messages:
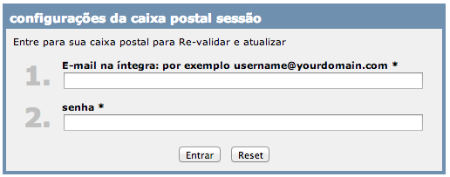

(This Captcha warning message is not in Portuguese anymore but in French)
Why do such simple attacks still work? Well, in Latin America, in the good sense of this word, people are very naïve. It’s clear that attacks do not need to be complex to be effective. Simple tricks used 10-15 years ago are still functioning for cybercriminals. And as you can see, there is no need to clone an original Web site, so any rookie cybercriminal is able to use such methods to steal users’ information.
I already reported the form as fraudulent and hope it will be taken down quickly.






















Stealing User’s Password with Free Online Forms