
In recent spam mails we have often noticed links to *.html files with random names. Another trend is that the cybercriminals do not even bother to register domains for their dirty deeds, but simply plant their malicious code on compromised hosts. “Simply?” one may ask, and sadly the answer seems to be “yes” based on our observations.
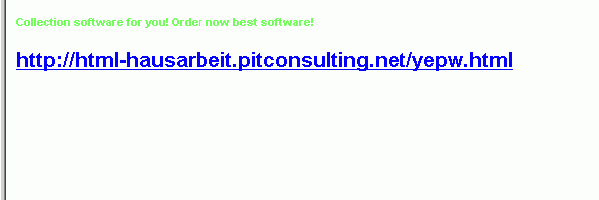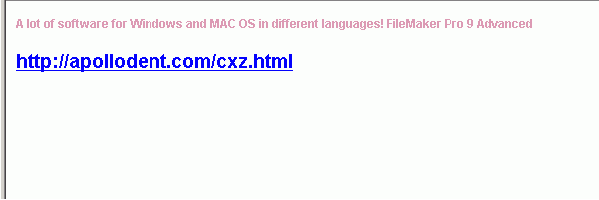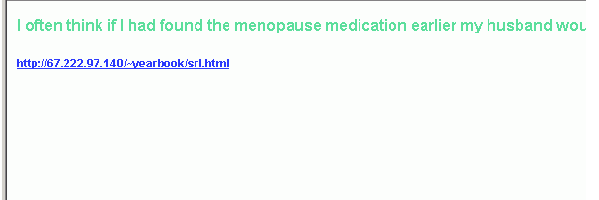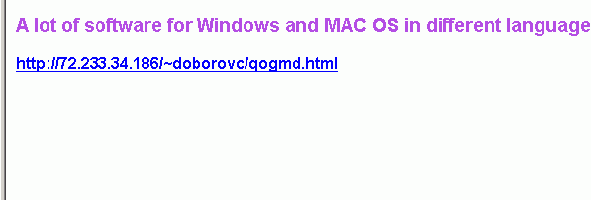
For example, we have collected some hundred mails of a certain type promoting online software shops – a small portion is shown in the animated gif image below.
All of the samples stick out by virtue of the fact that they contain colored text/links which point to compromised legitimate websites. The links also show that the locations of the files are directly on the root URLs and not in a subfolder of some vulnerable application as we usually see.
We can assume that the intruders have ‘write’ access, at least to the www root of the involved sites – a very worrying fact. We have also confirmed that in many cases not only were the abovementioned spam links stored on the victim’s servers, but additionally, malicious iframes or javascript snippets were injected into the main content of the sites.
Another sample reaching us today just confirms that the cybercriminals are not sparing with the domains they abuse, and indeed seem to have a pool of unknown quantity at their disposal. The capture below shows a spam mail where each of the 12 links in the mail body points to a unique site. All of these sites also contain malicious code in their root which we detect as ‘Trojan-Clicker.JS.Agent.*’
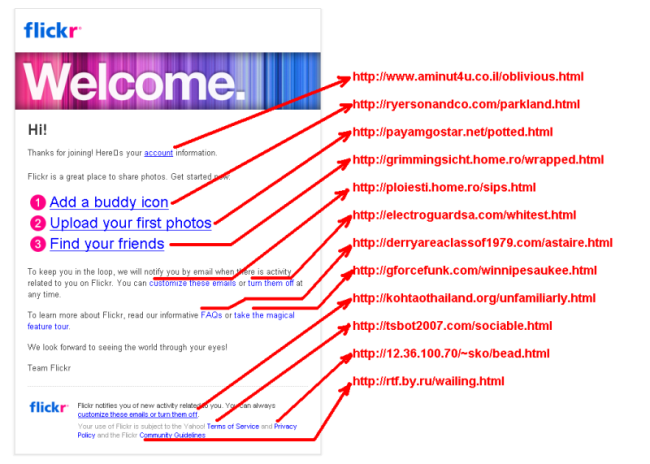
Please do not attempt to visit these links shown if you are not sure of what you are doing.




















Spammers hacked pool