
June in figures
- The amount of spam in email traffic decreased by 1.9 percentage points compared to May and averaged 71.9%
- The share of phishing emails remained unchanged from May’s figure, accounting for 0.01% of all mail traffic
- Malicious files were found in 3% of all emails, an increase of 0.2 percentage points compared with the previous month
Spam in the spotlight
New to malicious spam
In our spam reports we often write about new methods used by the spammers to distribute malicious code. We have already mentioned that malicious code is the most dangerous and dynamic type of spam. Fraudsters often apply new social engineering techniques in their mass mailings. In June, they added a number of new tricks to their repertoire, and as always we’re letting you know what to look out for.
Going on holiday with malicious code
In spring we forecasted an increase in the amount of spam devoted to travel and tourism to coincide with the beginning of the holiday season. The explosion of activity for this type of mass mailing usually falls in early summer. To our surprise it was not the case this time round. This summer the spammers decided to distribute malicious code.
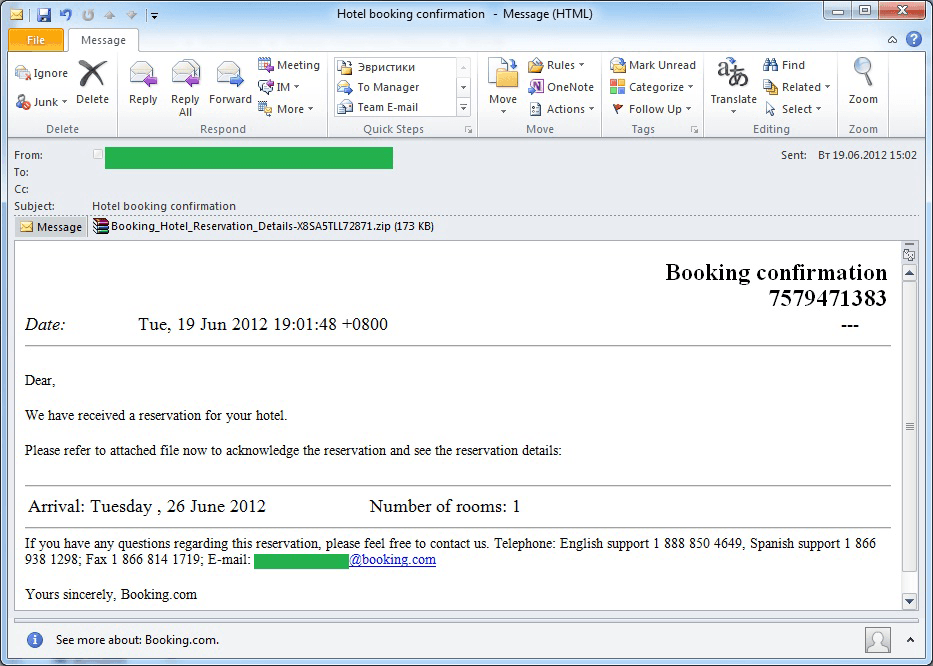
In March we wrote about a mass mailing that imitated a message from an airline inviting users to check in to a US Airways flight online. The technique was adapted slightly in June, with emails containing fake hotel booking confirmations. The malicious part was contained in the attachment that supposedly provided the confirmation details.
It would appear that spammers are now offering a full malicious “tourist package”. The quality of this mass mailing is poor, but in the midst of the holiday season lots of people will still fall victim to the fraudsters. We recommend all users to be especially attentive when booking trips online. Remember, respectable companies will not send confirmations in a zipped archive. Additionally, if you doubt the authenticity of an email, you can always contact the company involved using the contact details provided on their official site.
The malicious photo
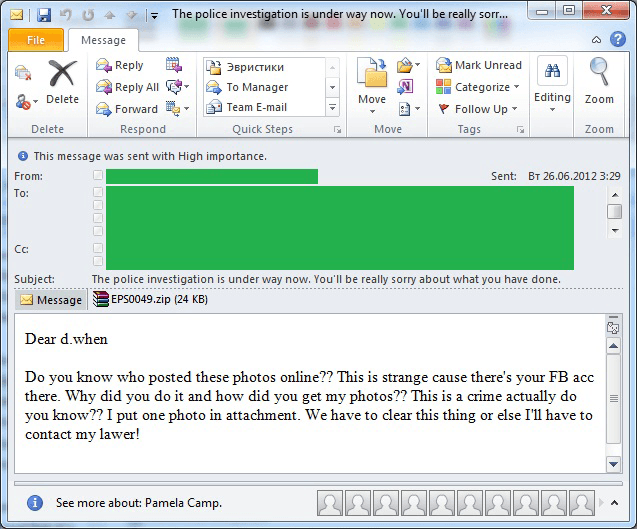
Not so long ago spammers were making active use of the following social engineering trick: they would distribute malicious code in an email attachment containing a photo of a girl who wanted to befriend the recipient. This trick may not be as popular these days, but the technique of masking a malicious program with a photo is still used by the spammers. For example in June we registered a mass mailing where the recipient was threatened with legal action for posting photos on the Internet without the owner’s consent. The photos in question were supposedly attached to the email in the form of a zipped archive.
The popularity of social networking sites has led to a new type of malicious spam containing fake photos: the message informs the recipient that someone has posted private photos of him/her on a social networking site. The user is invited to view the photos by either following a link or downloading the attached archive.
Yet another photo-related trick is that of fake notifications about fines for traffic violations. The email attachment contains a malicious archive passed off as the set of photos taken by video surveillance cameras. Another variant of this type of spam is an email that appears to have been sent by the recipient’s friend who has allegedly been caught drink driving on camera in one of these fake notification scams.
Hot topics in June
Euro spam
Among the most high-profile events of the month was the European Football Championship which lasted the whole of June. The spammers couldn’t resist exploiting all the interest and even started spreading Euro 2012-related mass mailings at the beginning of the year.
We have written more on this theme in a recent blog, but to recap, the ‘football’ spam began with offers of the tickets. When the tickets sold out the spam turned to the theme of apartments for rent or hotel rooms in the cities hosting the championship. In May, the spammers started offering tickets to the live broadcasts of matches on big screens in various European cities. In spring spam traffic also saw a surge in ‘Nigerian letters’ promising sport-related lottery wins.
In June spammers widened their range of offers with adverts for football sites dedicated to Euro 2012 including those with live online football streaming.
US Independence Day
On 4 July the US celebrates one of its main national holidays – Independence Day. As is the case with any other major holiday in the western hemisphere it is accompanied by a wave of spam offering fake designer watches and various other accessories as gift ideas.
There were also mass mailings advertising flags to help Americans express their patriotic feelings.
Statistical summary
Sources of spam by country
Below are the Top 20 ratings for the countries that sent most spam to Europe and the USA in May.
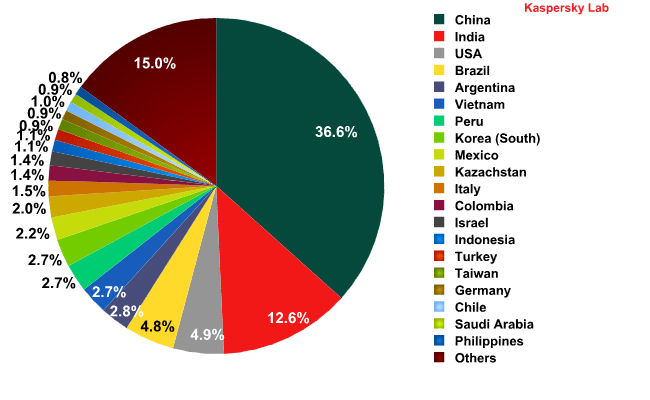
Top 20 sources of spam sent to European users in June 2012
In June, the share of all spam received by European users that originated in China increased by almost 50% compared to the previous month.
The UK was the only European country in May’s rating that didn’t make it into June’s Top 20. Among the leading distributors of spam in the European region were two other European countries – Italy (1.5%) and Germany (0.91%).
More than half of all the spam distributed in Europe still comes from Asia.
The Top 20 rating of countries that distributed spam on the territory of the US in June was topped by the US itself. For the second month in a row over one third of all US spam is “homemade”, with an increase of 5 percentage points compared with the previous month.
A quarter of the spam distributed on US territory is of Asian origin.
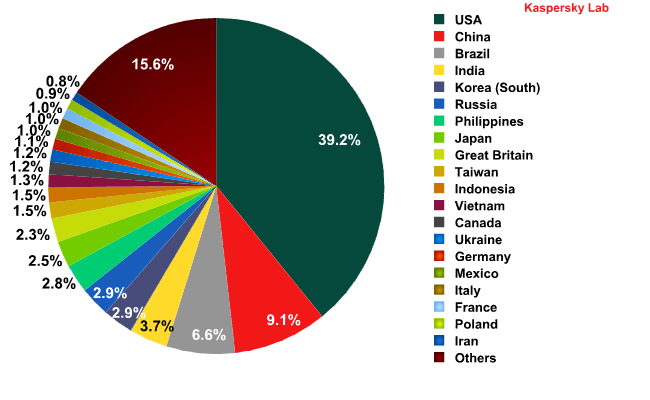
Top 20 sources of spam sent to US users in June 2012
Malware in mail traffic
In June malicious files were found in 3% of all emails, an increase of 0.2 percentage points compared with the previous month
Distribution of email antivirus detections, by country
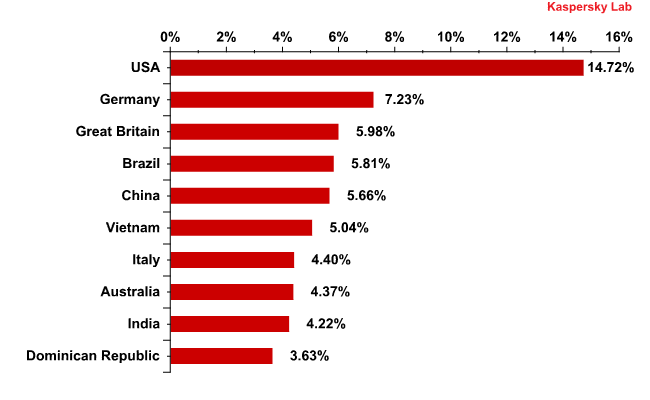
Distribution of email antivirus detections by country, June 2012
For five months in a row the US has topped the rating of email antivirus detections. In June, its share of Kaspersky Mail Antivirus detections decreased by 1.25 percentage points compared to May.
After coming 2nd in April and 4th in May, Vietnam fell two more places in June though the share of antivirus detections in country did not fall significantly (-0.8 percentage points).
Germany came an unexpected 2nd in May and remained there in June, with 7.2% of all Kaspersky Mail Antivirus detections registered there.
The UK’s position in the rating also remained unchanged with 6% of all registered antivirus detections occurring there.
The share of Kaspersky Mail Antivirus detections in Germany and the UK decreased by 2.43 and 2.95 percentage points respectively while the contribution of the other countries fluctuated within a range of 2 percentage points compared to May.
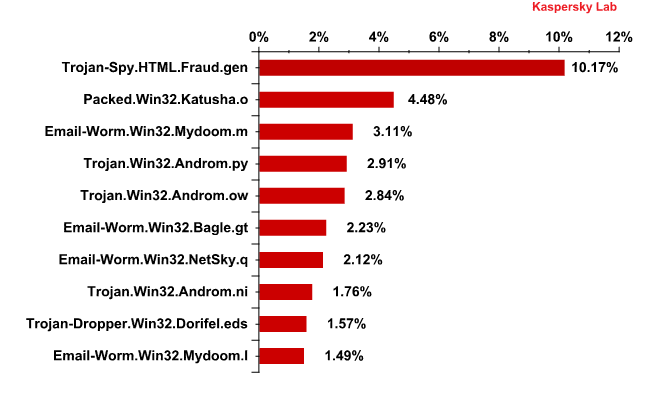
Top 10 malicious programs spread via email in June 2012
Top 10 malicious programs spread via email in June 2012
In June, rating leader Trojan-Spy.HTML.Fraud.gen accounted for more than 10% of all detections meaning every 10th malicious email contained the Trojan that makes use of spoofing technology and appears in the form of an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password.
Packed.Win32.Katusha.o came second in the rating. The packers in this family make regular appearances in this Top 10. They are used to pack other malicious programs (mostly fake AV) in order to bypass antivirus detection.
Mail worms still dominate among the most frequently detected malware, which is not surprising considering their uncontrolled mechanism of self-distribution. It’s worth mentioning that the presence of such ‘veterans’ as Mydoom and NetSky in spam traffic means many computers do not have real-time protection. In addition, many users continue to download and run malicious attachments. Given the majority of these detections occur in the developing world it is easy to assume that users in these countries are less aware of online security. To recap, these two mail worms have only two functions – to harvest email addresses and send copies of themselves to those addresses. Bagle.gt, a similar program that is a long-term resident in this rating, in addition to the usual functionality downloads malicious programs from the Internet.
Three newcomers to the Top 10 malicious programs spreading via email in June belong to the Trojan.Win32.Androm family. They occupied 4th, 5th and 8th places respectively. Once these malicious programs are installed on a computer, they start downloading other malware from the Internet.
Phishing
The proportion of phishing emails remained unchanged from May’s figure, accounting for 0.01% of all mail traffic.
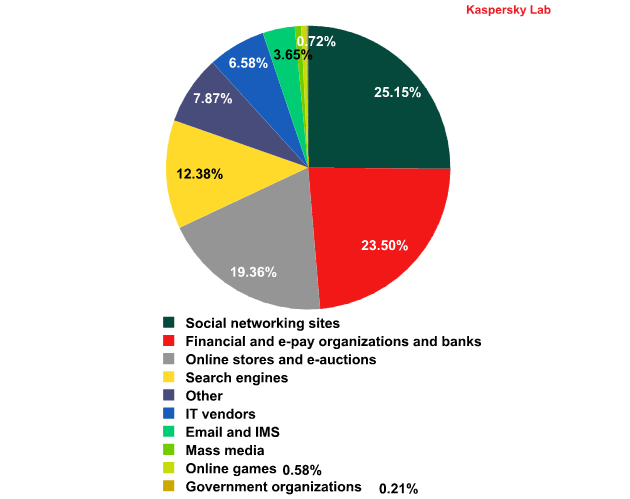
Top 100 organizations, by sphere of activity, targeted by phishers in June 2012
(based on anti-phishing component detections*)
*This rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
Previously we forecasted an increase in the share of attacks on social networking sites and online stores accompanied by a decrease in the intensity of attacks on financial organizations. This was linked to the start of the summer holidays for schools and universities and the holiday season in general. In June, business activity tends to ease off, while schoolchildren and students spend more time on communicating on social networking sites, playing online games and shopping online.
As expected, in June social networking sites returned to first place in the rating of organizations targeted most by phishers (25.2%). Facebook is still their prime target.
In May, the amount of attacks on online stores grew by 2 percentage points and in June its level remained unchanged.
It should be noted that in June Kaspersky Lab was among the most frequently attacked IT vendors. It looks like some cybercriminals tried to access the accounts of our users.
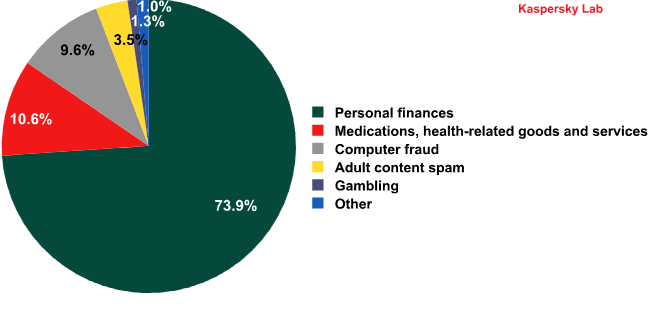
Spam by category
Spam by category in June 2012
In June, the share of the Personal Finance category almost tripled in size. This unexpected surge could be down to two factors. First of all, it could be related to people losing their jobs in the current economic downturn and spammers exploiting the situation. Secondly, the holiday season usually sees a decrease in consumer activity, which makes the advertising of goods unprofitable. Any unemployed users will remain Internet-active during the holiday season as they search for jobs or money-making schemes, and the spammers are only too happy to oblige.
The Computer Fraud category came second. The target audience here was both unemployed users and students who remained active on the Internet throughout the holidays.
Conclusion
The share of spam in mail traffic continued to fall in June, with a drop of nearly 2 percentage points compared with May’s figure.
This could be down to a seasonal fluctuation, with many spam bot computers turned off while their owners are on holiday.
However, this could also be a general downward trend in the quantity of spam because during the quiet season the volume of ‘clean’ email traffic falls too, and if the proportion of share decreases along with an overall fall in email traffic, it suggests the volume of spam traffic has decreased significantly. This drop in spam traffic is not just down to seasonal fluctuations.
We would like to draw your attention to the fact that during the summer holidays spammers tend to focus on children and students and the services they use – social networking sites and online stores. Teenagers should be aware of the risks that lie in wait for them on the Internet. At the very least, parents need to make sure their children have enough knowledge about IT security so they don’t pass on credit card data to cybercriminals while shopping online.


















Spam report: June 2012