
Summer 2012 will be packed with sporting events. This week sees the Euro 2012 football championship kick off in Poland and Ukraine. The tournament will bring together 16 of Europe’s best teams, and football fans from all over the continent will be watching closely regardless of whether their country qualified for the finals or not. Official ticket sales for Euro 2012 were launched on 12 December 2011, but spammers – rather unusually for them – were in no hurry to exploit the event. The first mailing offering tickets to Euro 2012 was only detected at the beginning of January. Since Ukraine is one of the host countries for Euro 2012, there were lots of messages in Russian and Ukrainian. The afore-mentioned message offering tickets was just one of them.
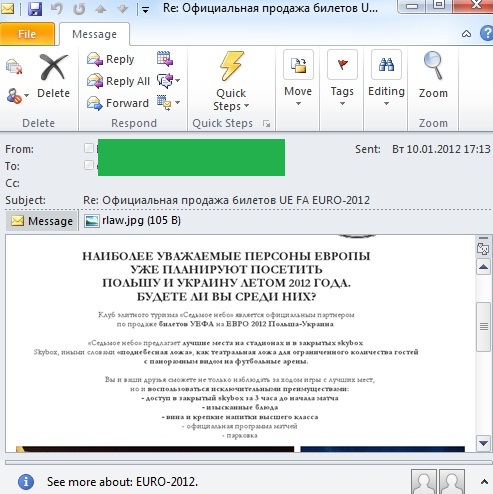
“The most respected persons of Europe are already planning to visit Poland and Ukraine in summer 2012. Will you be one of them?”
When the tickets sold out, mail traffic was flooded with spam offering apartments or hotel rooms for rent in the host cities. In addition, in May, there were some mailings offering tickets to live broadcasts of matches on big screens installed in various cities across Europe.
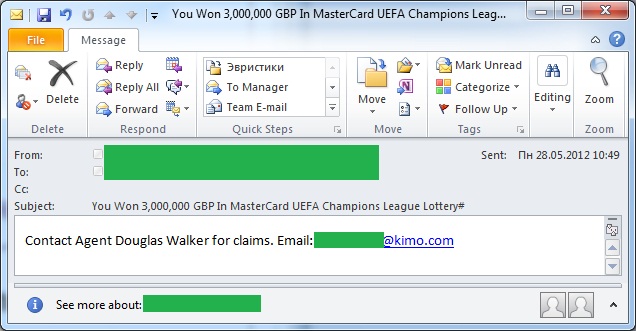
And only in the spring of 2012 did the Nigerian email messages promising football-related lottery wins appear:
The fact that Nigerian scammers waited so long to start using Euro 2012 for their own purposes is rather unexpected, especially in light of their keen interest in the 2010 World Cup, when we started detecting them almost six months before the tournament started.
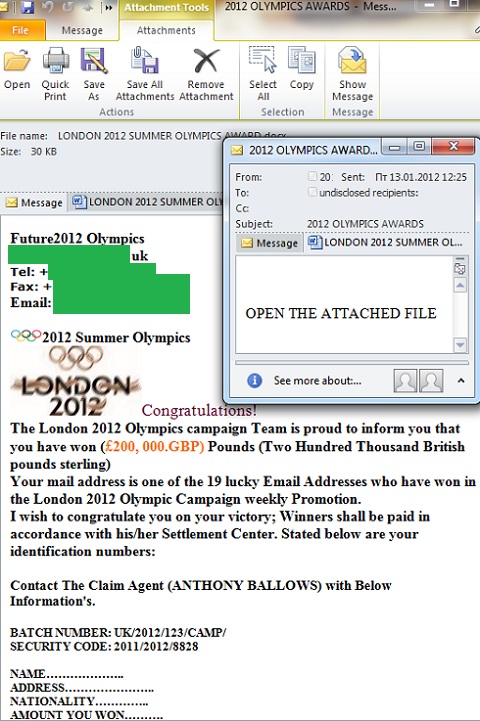
However, it’s pretty clear why Euro 2012 hasn’t resulted in the same volume of Nigerian scam messages as in 2010: shortly after the final game of Euro 2012 the Summer Olympics get under way in London. Since early January, we’ve registered several identical mailings with a short text in the message body and attachments in .Docx, or . Pdf. The attached files contain the text of a typical Nigerian message – it informs user that he/she has won a large sum of money and should immediately contact a representative of a “fund” or “lottery” and provide his/her contact details.
Apparently, the Olympics seemed important to the spammers, because it will bring together representatives from approximately 200 countries, and so the chances of reaching users interested in the event are significantly higher than in the case of Euro 2012.
In the past we’ve regularly seen spammers use international sporting events in their mailings. Of course, they do it solely for profit. Fake websites “selling tickets for the tournament”, malicious attachments, fake tickets or important information about events mailed to the user, Nigerian letters promising fantastic prizes from the relevant organizers – all this will still be seen in spam in 2012.
Remember that all information about tickets and lotteries conducted by the organizing committees of events can be found on their official websites, and spam messages cannot be regarded as a source of reliable information. And to be honest, they’re not worth reading at all.





















Spam: Euro 2012 vs Summer Olympics