
Spam in the spotlight
Spammers actively sent out Valentine’s Day offers in February, while ‘Nigerian’ scammers exploited the political situation in Ukraine and the tragic events there to trick users out of their money. Among the most notable mailings of the month was an offer to win free laser eye surgery.
‘Nigerian tourists’ in Ukraine
Political unrest rarely goes unnoticed by the scammers, so it came as no surprise to see the events in Ukraine appearing more frequently in ‘Nigerian’ scam letters in February. The fraudsters cited some familiar stories about valuables being stolen followed by a request to provide financial help to an unfortunate tourist.
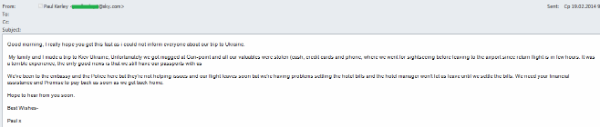
One fraudulent mailing from an unlucky tourist told the sad story of a family trip to Kiev that turned into a nightmare after unidentified armed criminals took all their valuables, leaving only their passports. The local police and the embassy couldn’t help the tourists and the hotel manager wouldn’t let them stay because they had no money to pay the bill. The unlucky travelers were now asking for help from strangers capable of providing financial support. They claimed they urgently needed money because there wasn’t much time left before their flight, but they promised to return the entire sum once they got home.
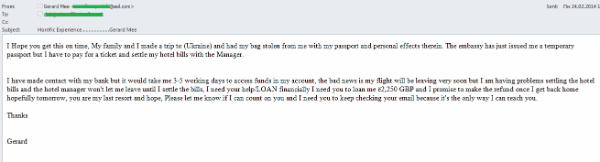
Another ‘Nigerian’ email was also allegedly sent by a tourist who had come to Ukraine with his family. His bag with all his documents had been stolen. The embassy issued him a temporary passport, but the ‘Nigerian’ tourist did not have money to buy a ticket or pay the hotel bill. Unlike the previous email, the scammers ask for a specific amount of money, but they also ask the recipient to respond immediately to the email because there is not much time left before the flight and the bank needs a few days to transfer money to the tourist.
Stories about tourists who have been robbed, just like other fraudulent stories, are universal – they can be used for almost any event which has received international publicity. But all these stories mentioning real events are merely scammer tricks and a victim who responds to such a request doesn’t actually help anyone and will never get his money back.
Holiday spam
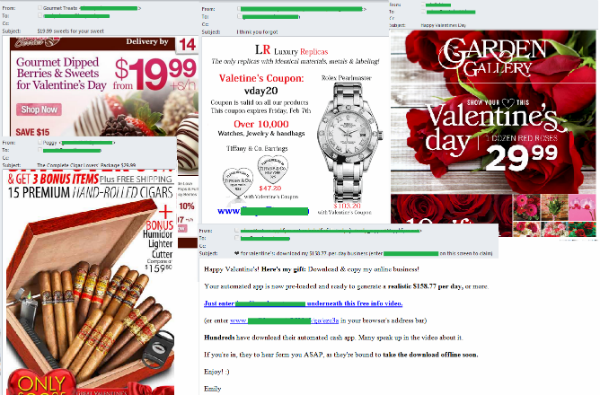
English-language spam exploiting the Valentine’s Day theme contained adverts for fake designer goods as well as offers of flowers and gourmet sweets. The messages were decorated with a Valentine’s theme. We also came across a fraudulent email offering recipients a chance to earn a large sum of money with the help of a special application that was sent out as a gift for Valentine’s Day.
We expect that in March, spammers will continue to exploit holiday themes (St. Patrick’s Day, etc.) in order to send unsolicited emails advertising various products and services.
Vision correction
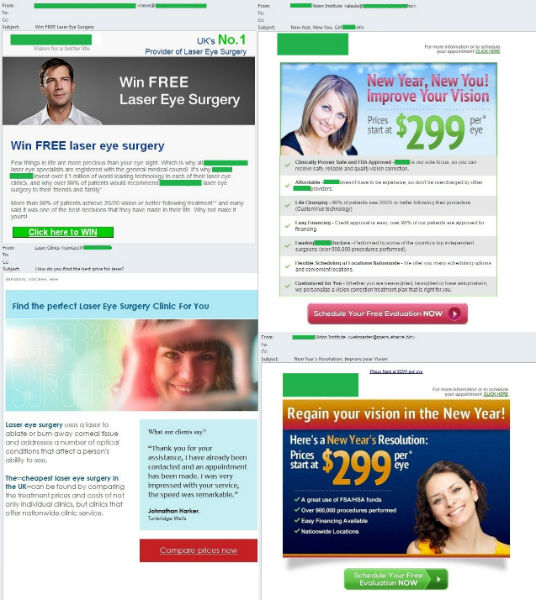
In February English-language spammers actively advertised laser vision correction which in some cases was offered with a big discount or even for free. The content of the messages was that of a promotional flyer with a clickable area that, after a series of redirects, led to a spammer resource offering laser vision correction as well as other goods and services. Most of the emails provided the name of the advertised clinic which the user could find with the help of a search engine if desired. To look even more convincing some messages even contained recommendations from grateful patients.
Cartridges for printers and copiers
Yet another theme of the month was a series of offers for printer and copier cartridges. Over the last couple of years the amount of cartridge-related spam has increased. The messages appeared in various languages, though the method and design of the mailings were generally similar.
Mass mailings in English, Swedish and other languages mainly offered cartridges for ink printers. The advert usually contained a list of printer models and the prices for cartridges. Some emails tried to grab the recipients’ attention with discount coupons and short-term promotions. One manager from China, the supposed sender of one of the mass mailings, boasted of his company’s successful participation in an international trade show in Germany and even attached photos from the exhibition.
Statistics
Proportion of spam in email traffic
The percentage of spam in email traffic remained almost unchanged throughout the month except for a slight increase in the third week of February. The proportion of spam in February’s email traffic averaged 69.9%.
Spam sources
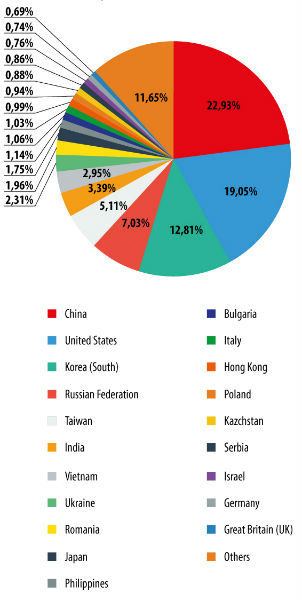
In February, the list of sources distributing spam worldwide was as follows.
After finishing in second place in January, China (22.9%) returned to the top of the rating after an increase of 7 percentage points in its share of distributed spam. It was followed by the USA (19.1%), last month’s leader, whose share fell by 2.8 percentage points. South Korea completed the Top 3, accounting for 12.8% of worldwide spam distribution which is almost the same as the previous month.
Russia (7%) ended the month in fourth place with an increase of 1.1 percentage points. Taiwan (5.1%) dropped to fifth place after its share decreased by 1.1 percentage points compared to January.
India (3.4%), Vietnam (3%), Ukraine (2.3%) and Romania (2%) all experienced an average decline of 0.2 percentage points in the proportion of distributed spam.
In February, Japan’s share (1.8%) fell 0.3 percentage points compared with the previous month, resulting in a drop of one place in our rating to tenth place.
Noticeably, February saw a slight increase in spammer activity in Germany (0.7%) and the UK (0.7%) that pushed these two countries into the Top 20.
South Korea remained the leading source of spam sent to European users (48.6%) in February: its share grew by 1.2 percentage points from the previous month. Next came the USA whose contribution also increased by almost 3 percentage points, pushing it up one position to second place. In January the USA was third with 5.3% of all spam sent to European users. Taiwan (5.5%) is now in third place after its share fell 0.3 percentage points.
Russia (5%) moved up one place fourth with an increase of 2 percentage points in its share of spam in Europe. It is followed by China which surged up the rating from eleventh place in January to fifth in February after its contribution rose by 2.3 percentage points and averaged 3.9%.
Ukraine (2.3%) and Vietnam (1.8%) also experienced slight growth of 0.5 percentage points. While this didn’t significantly affect Ukraine’s position in the rating – it only moved up one place from eighth to seventh – it meant Vietnam jumped a total of eight places and entered the Top 10.
India rounded off the Top 10 with 1.6% of spam sent to European users. The UK and Germany’s figures are slightly lower – 1.5% and 1.4% respectively.
In February, Italy (1%) fell seven places and dropped out of the Top 10 after the country’s share decreased by more than 1 percentage point. A decline was also registered in Spain (0.8%) and Argentina (0.7%). Spain also left the Top 10 in February despite finishing in sixth place the previous month.
Asia (54%) remained the leading regional spam source in February with an increase of 5 percentage points from the previous month. North America came second having distributed 20% of global spam, a drop of 3.2 percentage points. Meanwhile, Eastern Europe’s share went up 1.2 percentage points, averaging 16.2% and placing the region third in the rating. Western Europe (4.5%), Latin America (2.7%) and the Middle East (2.4%) came fourth, fifth and sixth respectively.
Malicious attachments in email traffic
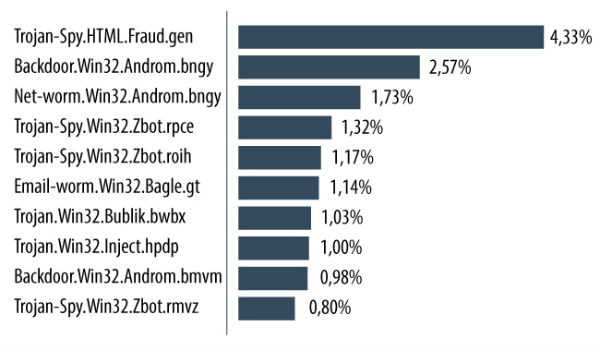
In February, the Top 10 malicious programs that spread via email were as follows:
Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. Fraud.gen belongs to a family of Trojan programs that use spoofing technology: these Trojans imitate HTML pages and are distributed via email, appearing in the form of notifications from major commercial banks, e-stores, software developers, etc.
Backdoor.Win32.Androm.bngy and Backdoor.Win32.Androm.bmvm. occupied second and eighth places. The Andromeda family of malware consists of backdoors that allow cybercriminals to secretly control the compromised computer. The machines infected by these programs often become parts of botnets.
In third place was the net worm Asprox designed to spread spam. It automatically infects sites, loads and runs other programs, and collects valuable information stored on the computer such as passwords and other data to access email and FTP accounts.
Trojan-Spy.Win32.Zbot.rpce and Trojan-Spy.Win32.Zbot.rpce. finished the month in fourth and fifth places repectively. Zbot is a family of Trojans that steal confidential user information. It can also installCryptoLocker, a malicious program that demands money to decrypt user data.
Next came Email-Worm.Win32.Bagle.gt, an email worm which sends copies of itself to all email addresses found on an infected computer. The worm also downloads files from the Internet without the user’s knowledge. Email-Worm.Win32.Bagle.gt uses its own SMTP library to send infected messages.
Eighth place is occupied by Trojan.Win32.Inject.hpdp which is a spyware and a keylogger (Limitless Logger) at the same time. The program steals keystrokes, system information, authentication data, passwords from email services and passwords from password storages.
February’s Top 10 was completed by Trojan.Win32.Bublik.cbds, a small Trojan-Downloader which downloads the Zbot family of Trojans.
Special features of malicious spam
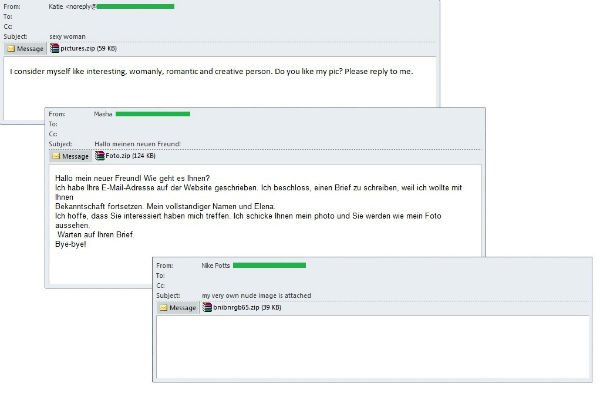
In the wake of the Valentine’s Day celebrations in February, the number of ‘online dating’ emails increased considerably. The emails from beautiful strangers wanting to start correspondence contained attached archives that instead of the promised photos included malware such as Trojan.Win32.Reconyc.rbc. This is a Trojan-Dropper that installs two malicious programs on the system: one is spyware that steals all document files (*. Docx, *. Xlsx, *. Pdf) from the computer and sends them to a specific mailbox; another is IRC-bot/worm called ShitStorm which can carry out DDoS attacks on websites and spread copies of itself via MSN and P2P services. In February we registered quite a lot of malware belonging to the ransomware group which blocks the user’s computer and demands money to unblock it. These include, for example, Trojan-Ransom.Win32.Gimemo.boyz.
We also came across text-free messages whose subject could be guessed from message headers such as “my very own nude image is attached”. The archives attached to these emails also contained, in particular, Backdoor.Win32.Androm.bnaf from the Andromeda family, which allows the attackers to control infected computers without the users’ knowledge.
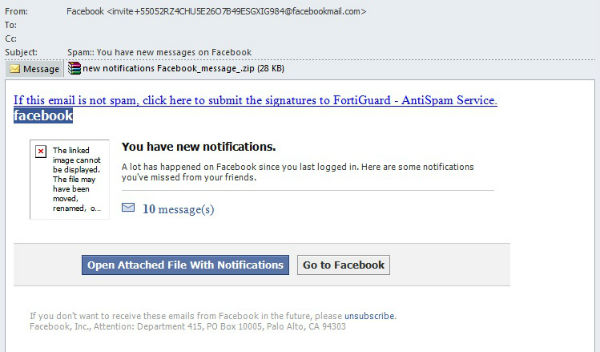
The same sort of malware was distributed in February using more conventional methods such as fake notifications from major social networking sites. The notifications were sent using the Facebook name and informed recipients that lots of friend activity had occurred since they last visited the site and were prompted to read about them in the archive attached to the email. The archive contained Backdoor.Win32.Androm.bmvv, a malicious program from the aforementioned Andromeda family.
Phishing
The ranking of organizations attacked by phishers did not change significantly in February.
The ranking is based on Kaspersky Lab’s anti-phishing component detections that are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
First place was once again occupied by social networking sites (27.3%) whose share decreased by just 0.06 percentage points. The share of email services (19.34%) also declined insignificantly, leaving this category in second place. Financial and e-pay organizations (16.73%) were third with a slight growth of 1.1 percentage points.
The share of search engines (16.51%) fell by 0.4 percentage points which saw the category drop to fourth place in the ranking. As in January, Telephony and Internet service providers (8.43%) and IT vendors (5.85%) came fifth and sixth respectively.
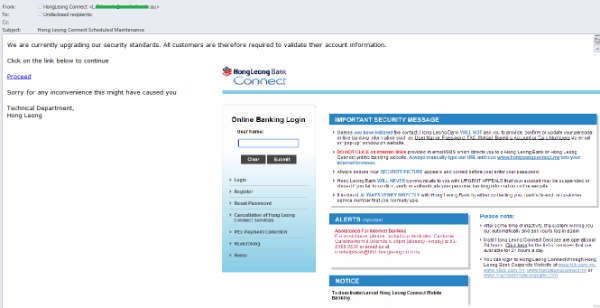
Phishing emails that use the names of major financial and e-payment organizations from different countries are actively spread by scammers to steal personal financial information. In February, we came across fraudulent notifications allegedly sent by the technical department of Malaysian bank HongLeong. The message reported that the bank was enhancing its data protection measures and all customers were asked to confirm their bank account data by clicking a link specified in the email. This directed the user to a phishing page imitating the official My Account page on the bank’s website. All the data entered was transferred to cybercriminals who got full access to the victim’s personal account. Noticeably, the address in the Sender field gave the game away – although the scammers used the name of the bank and tried to convince the victim that the email had arrived from a particular person, specifying the name and initials in the name of the mailbox, the domain name was completely different to the domain owned by the bank. It turned out to be a domain belonging to the University of Australia. Perhaps the scammers had got access to the email box and used it to distribute phishing mailings without the owner’s knowledge.
Conclusion
The proportion of spam in email traffic in February was up 4.2 percentage points and averaged 69.9%. This increase from January could have been caused by the lull in spammer activity at the beginning of the year.
In February, users of the Russian-language sector of the Internet received holiday offers of goods and services dedicated to Valentine’s Day. ‘Nigerian’ scammers tried to relax users’ vigilance by mentioning real events in Ukraine – they introduced themselves as tourists who had been stranded in the country without any money.
Emails with malicious attachments contained both standard fake notifications from the popular social networking sites and ‘online dating’ emails whose number increased in the run-up to Valentine’s Day.
In February, social networking sites remained the most popular phishing target. Email services were second in the rating of targeted organizations, while Financial and e-pay organizations came third with a slight increase of 1.1 percentage points in their share of phishing attacks.
























Spam report: February 2014