Spam in the spotlight
In October, spammers continued to actively use the names of well-known companies to spread malicious ZIP files. We registered several mass mailings offering rather unusual, if not to say exotic, services – love spells, incantations to enhance careers and other forms of white and black magic. There were significantly more mailings offering souvenirs with company logos, and the product range was greater than ever. These mass mailings were distributed in almost every major language. Naturally enough, various holiday-related spam was dedicated to Halloween and the upcoming Christmas and New Year holidays. In addition, spammers exploited the conflict in Syria to trick users.
Otherworldly spam
As expected, in October the number of mailings exploiting the Halloween theme increased.
In English-language spam there were the usual adverts for Halloween costumes and various gifts. This year spammers used largely the same designs as last year, changing only the address in the From field and adding links to newly created redirecting sites. The representatives of small and medium-sized businesses offered potential customers festive-style goods or invited them to Halloween parties.
In October, webinar organizers sent out invitations decorated Halloween-style with macabre color schemes, images of tombstones and a skeletal hand pointing to a link containing more information on the event. Typically, the topic of the webinar had nothing to do with the holiday: the unusual festive designs were simply trying to grab the attention of recipients.
In the run-up to the holiday we received several mass mailings from Chinese factories offering costumes, masks and Halloween accessories. To get the user interested, some emails were decorated with a Halloween theme and contained prices for the goods on offer. Other messages only provided addresses for sites where acatalog was available.
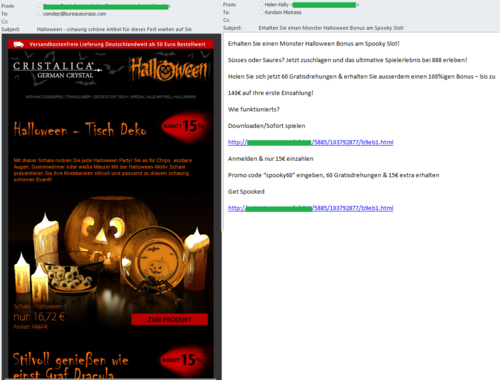
In October, we registered a German-language Halloween mass mailing. The spammers distributed emails advertising casinos which provided Halloween bonuses; some companies also offered holiday discounts. The emails had a distinct Halloween theme and the subject usually included the word “Halloween”.
Christmas spam
October saw a sharp increase in Christmas spam as people begin to prepare for the upcoming holidays.
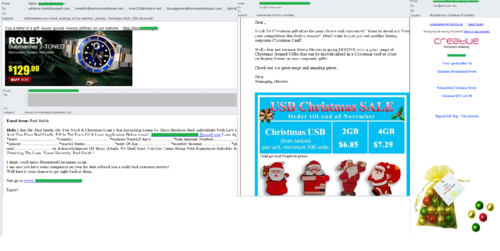
English-language Christmas mailings advertised replica designer watches or favorable loans; organizations were offered gifts for their customers – Santa-shaped USB-sticks or candy with a holiday logo or message.
Chinese manufacturers actively adopted the pre-holiday preparation theme to advertise their products. In October, they offered electric garlands for Christmas parties and other goods decorated in a festive style. These are in fact the first mass mailings containing offers of Chinese Christmas goods registered this year.
Last month, organizations offering services that had nothing to do with the holidays also tried to attract customers with Christmas discounts.
Syrian upheaval
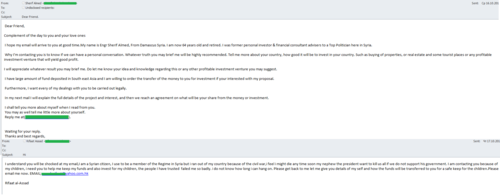
As we have already written in our blog, the complicated political situation in Syria is widely used by spammers to spread “Nigerian” scams. In October, we continued to register new examples of fraudulent emails.
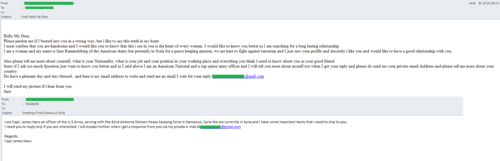
Some messages were sent in the name of an officer of the Syrian Armed Forces. Yet another mass mailing contained emails allegedly from a member of the peacekeeping mission in Syria. In both cases the scammers exploited the victims’ curiosity stating they had something important to say. This is a trick aimed at getting the victim’s attention and luring them into further communication.
Perhaps the most unusual of these mass mailings purported to come from a female member of the “peacekeeping mission” in Syria who was hoping to form a serious relationship with the recipient of the e-mail. On the face of it, a simple acquaintance would hardly seem to be the first step towards deception – yet that was exactly what happened. Once the scammers gained the victim’s confidence, the “pen pal” immediately hit a problem which only a money transfer from their new friend could solve. The fraudsters also resorted to the classic fairy tale about multi-million-dollar savings and promised a reward for a partner who could help them to transfer the money from their accounts. The result was always the same: users lost their money and the scammers stopped answering their emails and vanished just as suddenly as they had appeared.
In October, the fraudsters also actively spread stories written on behalf of Syrian citizens who needed help to invest their savings. The alleged authors of messages were both Syrians who had left the country because of the unrest and pensioners who had somehow scraped together a fortune. The fraudsters played on human greed and at the same time tried to evoke pity by telling the recipient about the persecution faced by families in Syria. To be more convincing, the scammers provided an email address and asked users to contact them for more information.
Masters of magic
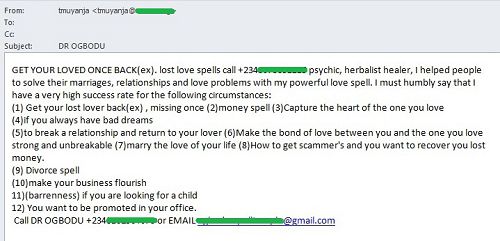
Magic, in all its forms, was a notable theme in October’s spam flows. White and black magicians alike offered their services in the Russian and English-language segments of the internet.
The most common service offered by the magicians was a spell which could solve any problem of the heart: the sorcerers guaranteed the return of an errant lover and the establishment of an unbreakable relationship with him/her. The authors of the mailings also offered powerful spells that could help to strengthen or break marriages, treat infertility, get a promotion, make business flourish or to solve other pressing issues. As a rule, these emails were impersonal and arrived from addresses registered on free email services. In addition to the list of services, they contained the magician’s email address, which differed from the sender’s address, and a contact telephone number.
Corporate souvenirs
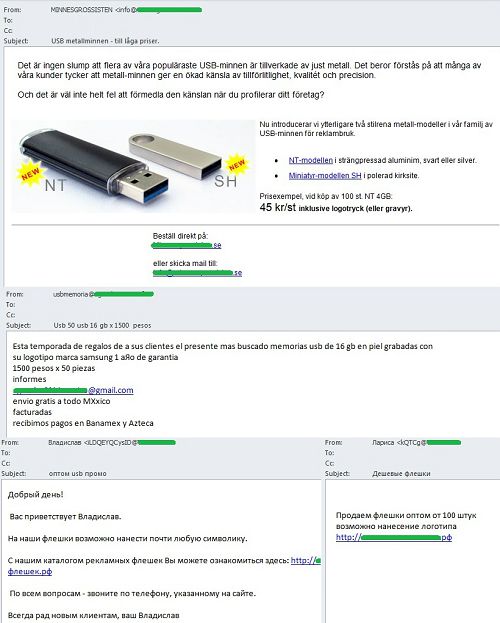
We often mention that spam mailings is one of the most popular ways of advertising branded merchandise such as calendars, pens, mugs and other goods.
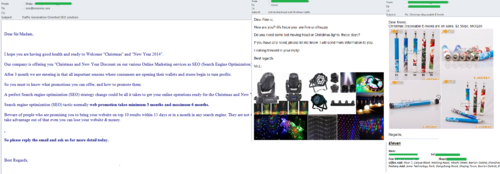
USB sticks and memory cards with company logos have recently become especially popular with the spammers. The authors of such mailings promise to imprint any logo on their products.
Such mailings appear regularly and in different languages (Russian, English, German, Spanish, Swedish, and others).
The geographical distribution of spam sources
In October 2013, the percentage of spam in email traffic was up 6.6 percentage points and averaged 72.5%. China remained in 1st place, accounting for 21.3% of all distributed spam; the USA came 2nd, (17.2%); South Korea was 3rd, averaging 13.3%. We recorded a slight decrease in the share of spam produced by these countries but this was less than 1 percentage point each. In total, these three countries distributed over half of all global spam.
Taiwan remained in 4th place, contributing 7.7% to the world spam flows, up 1.1 percentage points. Russia’s share increased 2 percentage points (6.8%) as it climbed to 5th place. India dropped from 5th to 8th place having distributed 3.5% of all spam (-1.5 percentage points). Japan (1.9%), which fell one place, completes the Top 10.
Noticeably, an increase in spammer activity in Hong Kong (0.9%) and Brazil (0.6%) brought these countries into the lower end of the ratings.
In October, South Korea remained the leading source of spam sent to European users (51.3%) even though its share dropped by 3.7 percentage points. Next came Taiwan (7.7%) followed by Russia (+0.9 percentage points) averaging 5.2%.
The share of spam that originated from Vietnam (2.61%) dropped 1.5 percentage points. India’s share (2%) slackened off too, losing 2.7 percentage points. As a result these two countries occupied 7th and 8th places respectively.
In October, Italy contributed 1.2 percentage points more spam and settled in 9th place. This month’s Top 10 also included Hong Kong, which came 6th with 2% of all distributed spam.
Kazakhstan completed the Top 10 (1.7%). The share of the other entries did not see any noticeable change.
In October Asia (56.4%) remained the leading regional spam source despite a slight drop (-2.4 percentage points) in spammer activity on this territory. North America came 2nd having distributed 19% of global spam, a decrease of 1 percentage point. Meanwhile, Eastern Europe’s share went up 3.8 percentage points, averaging 16%, which put the region in 3rd place in the rating. Western Europe (4%) and Latin America (2%) came 4th and 5th respectively.
Malicious attachments in email
In October, the Top 10 malicious programs that spread via email looked like this:
Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. Fraud.gen belongs to a family of Trojan programs which use spoofing technology: these Trojans imitate HTML pages and are distributed via email, appearing in the form of notifications from major commercial banks, e-stores, various services, etc.
Trojan-PSW.Win32.Fareit.amdp came 2nd in the rating. This malicious program is designed to steal logins and passwords from compromised computers. It doesn’t log key strokes but once executed it looks through registry and system files storing confidential data.
Email-Worm.Win32.Bagle.gt was in 3rd place. This mail worm is an executable file distributed in the form of email attachments. Like most mail worms it self-proliferates to addresses in the victim’s address book. It can also download other malicious programs onto a computer without the user’s knowledge. To spread malicious messages, Email-Worm.Win32.Bagle.gt uses its own SMTP library.
Malicious programs from the Bublik family are becoming more and more popular with spammers: there were four of them in September’s rating, while in October they accounted for five entries – 4th, 6th, 7th, 8th and 9th. Their main functionality is the unauthorized download and installation of new versions of malware on victim computers. Once the task is fulfilled, the program does not remain active: it copies itself into the %temp% file imitating an Adobe application or document.
Trojan-Ransom.Win32.Blocker.cmmb came 5th in October. These malicious programs are designed for blackmailing and extorting money from users. They block the work of the operating system and display a banner which orders users to send a paid text message to a premium-rate number. In return they are promised a code which disables the malicious program and unblocks the computer.
Rounding off the Top 10 is the well-known Email-Worm.Win32.Mydoom.l, a network worm with backdoor functionality that is spread as an email attachment via file sharing services and writable network resources. It harvests email addresses from infected computers so they can be used for further mass mailings. The worm also connects directly to the recipient’s SMTP server.
Special features of malicious spam
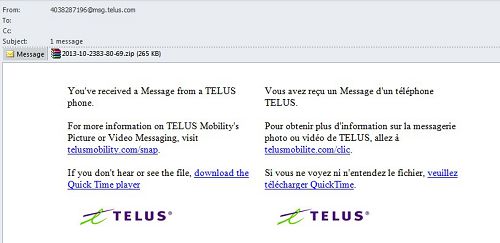
In October, we came across a mass mailing spread on behalf of Telus Mobility, a major Canadian telecommunication operator. The text in the emails was in English and French, Canada’s official languages, which read: “You’ve received a message from a TELUS phone. For more information on TELUS visit the company’s official site. If you don’t hear or see the file, download the Quick Time player”. The link in the message led to the official site of the operator while the link for downloading the player led to Apple’s site.
The attached ZIP archive allegedly contained the received message. In fact it included an executable file with a double extension, the first of which was graphical and could only present the attachment in the form of the image. The executable file was a malicious program belonging to one of the most widespread families distributed via email – Zeus/Zbot. Kaspersky Lab detects it as Trojan-Spy.Win32.Zbot.qmeb. These malicious programs are designed to steal all types of banking information from victim computers. Additionally, they use rootkit technologies which allow them to successfully hide their executable files and processes from the system (but not from antivirus programs).
Phishing
In October, the percentage of phishing emails in global spam traffic accounted for 0.027%.
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
The most attractive targets for phishing attacks did not vary significantly from the previous month. Social Networking Sites continued to top the list with 28.2%. The Top 3 also included Email and Instant Messaging Services (18.9%, up 0.8 percentage points) and Search engines (16.1%, up 0.9 percentage points).
The percentage of Financial and E-pay Services (15.4%) increased by 0.5 percentage points, keeping this category in 4th place. The share of the Telephone and Internet Service Providers category (8.4%), which remained 5th in the rating, did not change from September. IT vendors (7%) also held their 6th position despite a 0.9 point drop in their contribution.
Conclusion
In October, the level of global spam increased by 6.6 percentage points and averaged 72.5%. This was the result of a sharp increase in ordered spam. In October the total amount of spam returned to levels previously seen in spring, reflecting the usual trend of activity reviving after a summer lull.
Festive spam dedicated to Halloween and Christmas was actively used by the spammers to advertise various products and services – including those not directly associated with these holidays. Traditionally, spammers spread Christmas spam from October to December so in November we will most likely continue to register mass mailings exploiting the winter holiday theme.
Spammers also exploited global political events in October: the complex situation in Syria was mentioned in “Nigerian” scams to trick recipients and extort money from them.
In October, the rating of the most attractive targets for phishing attacks remained almost unchanged from the previous month. The four rating leaders slightly strengthened their position in the total flow of phishing emails. Social networking sites continued to lead although their share grew by only 0.04 percentage points. They are followed by Email and Instant Messaging Services and Search Engines. In November, we expect a rise in the number of attacks referring to financial institutions.
The fraudsters are increasingly using the names of well-known providers of telecommunications services to spread malicious programs. In September, they used the name of the UK’s BT Group to distribute the Trojan downloader Trojan-Downloader.Win32.Dofoil. In October, they targeted Canada’s national telecom operator Telus Mobility. Malicious programs of the Bublik family are becoming more and more popular with the spammers: in October, they accounted for half of the Top 10 malicious programs distributed via email.

























Spam in October 2013