
Spam in the spotlight
In the run-up to the summer, spammers offered their potential customers seedlings and seeds for gardening. In addition, English-language festive spam in May was dedicated to Mother’s Day – the attackers sent out adverts offering flowers and candies.
Holiday spam for Mom
As usual, the spammers were very busy in the run-up to the Mother’s Day celebration in May, sending out adverts for flowers and candies ahead of the holiday. To get the attention of the recipient, the subject of the email contained the name of the holiday while the body of the message included colorfully decorated promises of generous discounts and prompt delivery.
However, most links in these emails redirected the user to completely different pages instead of the advertised sites. The redirects went to newly created domains which were used not only in the links in the body of the message but also as a server domain name in the sender address. Some emails also included a link which would supposedly enable recipients to unsubscribe from further mailings. In fact, this link was used to collect users’ email addresses and send them new spam messages.
Spam for gardeners
It’s no secret that Americans are enthusiastic about their gardens – and gardening is one of the most popular hobbies in the country. With summer fast approaching, the spammers started spreading more offers of seeds for lawns and flowers, as well as berries and fruits. Potential buyers were lured in by phrases like “special,” “limited offer” and offers of a free plant for every two bought. The messages included colorful images and contained a link. Interestingly, most of the domains to which these links led had been created less than a week before launching the mass mailing.
Diplomas and degrees
In May, we came across a lot of mailings advertising schools and colleges that provided distance learning services. However, there were also mailings in which spammers invited users to simply buy a qualification. All that was required was to make a donation to a church, which would then officially award an honorary doctorate to the benefactor.
In Germany, for example, only universities and similar higher education institutions have the right to award doctorates. However, the situation is somewhat different when it comes to so-called honorary doctorate degrees that are awarded on behalf of a church. Although getting this doctorate does not entail any learning or writing of dissertations, the spam mailings used images of students and other university themes to advertise the service.
There were also many offers to help struggling graduates repay their student loans. These messages urged recipients to follow a link to a site where they would find adverts for organizations that recruit volunteers and staff for non-profit institutions. In the US it is possible to enroll in state programs that offer credits to people who do some kind of service for their community, and these credits can offset student loans. However, the mailings came from unknown accounts that regularly change their email addresses, and not from an official source. The links in the messages went to newly created websites that prompted users to submit personal data.
To get the recipient interested, such emails often contained a personal appeal: “Still can’t repay your student loan? I’ve found an interesting program for you that is definitely worth reading. It will help significantly reduce your monthly payments”.
Insuring everyone against everything
Yet another popular topic last month was insuring against different risks, mainly life insurance, although we saw offers of car insurance.
These mailings aimed to redirect users to sites where they could compare the cost of insurance cover from different insurers and choose the most favorable terms. In other cases, the links in the emails led to the spammer parked page where the visitor was offered a wider choice of the types of insurance, companies and programs. Having made his choice and clicked on one of the proposed options, the user entered another resource. The links in the messages might also lead to a site advertising one particular insurance company; typically it was a recently established medium-sized firm.
One unusual type of insurance offer that was limited to English-speaking spam, was burial insurance. In fact, it is an extended version of life insurance: a larger insurance premium means the insurance policy includes funeral services in the event of a sudden death. In May, such messages came in the form of images containing a hyperlink leading to the notorious parked page of the insurance company. These links varied from email to email, but they were always based on different domains registered by the spammers shortly before launching the mailings.
The percentage of spam in email traffic
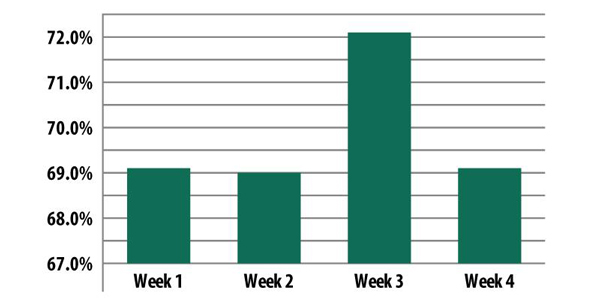
The percentage of spam in email traffic in May averaged 69.8%, which is 1.3 percentage points less than in April. The highest spam levels were seen during the third week of the month (72.1%), and the lowest levels were seen in the middle of the month (69%).
Malicious attachments in email
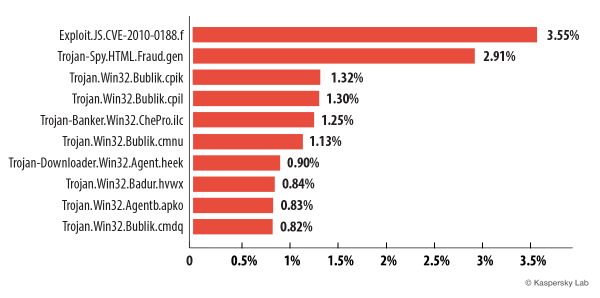
The graph below shows the Top 10 malicious programs spread by email in May.
May brought a new leader in our rating – Exploit.JS.CVE-2010-0188.f pushed the notorious Trojan-Spy.HTML.Fraud.gen to 2nd place. Exploit.JS.CVE-2010-0188.f is a malicious program that is distributed in the form of a PDF file and exploits a vulnerability in version 9.3 and lower of Acrobat Reader. The vulnerability becomes apparent when addressing a field that contains a TIFF image formed in a certain way.
In May, representatives of the Bublik family occupied 3rd, 4th, 6th and 10th places. In the previous month eight of the top 10 malicious programs were part of this group. Their main functionality is the unauthorized download and installation of new versions of malware onto victim computers. Once the task is fulfilled, the program does not remain active: it copies itself into the %temp% file imitating an Adobe application or document. Trojan.Win32.Bublik.cpik and Trojan.Win32.Bublik.cpil download the notorious ZeuS/Zbot. Although this malicious program is able to execute a variety of malicious actions it is most often used to steal banking information. It can also install CryptoLocker, a malicious program that encrypts user data and demands a ransom to decipher it.
Trojan-Banker.Win32.ChePro.ilc, a banking Trojan targeting the users of Brazilian banks, came 5th. As is typical for this type of malware, it steals bank information and passwords.
The infamous Trojan-Downloader.Win32.Agent.heek came 7th in May’s Top 10. Its task is to download Trojan spyware designed to steal financial information. Most of these programs target Brazilian and Portuguese banks.
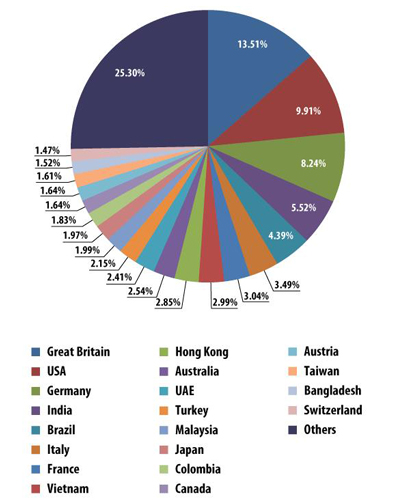
The UK was the country with the highest proportion of email antivirus detections with 13.5% (up 3.5 percentage points from April). The US (9.9%) dropped to second. Germany (8.2%) stayed in third.
Columbia (1.83%) was a new entry to the top 20 in May while Russia dropped off the list.
The percentage of email antivirus detections in other countries did not change much in May.
Special features of malicious spam
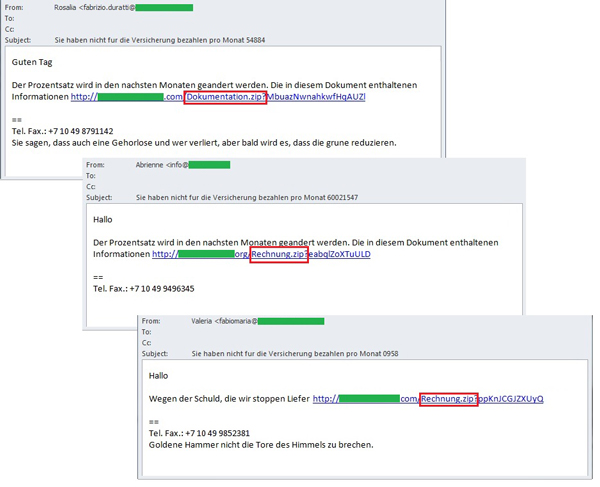
The insurance theme did not just feature in spam advertising this month – it was also used in mass mailings that spread malicious attachments. For example, we came across German-language messages with the subject “You have not paid your monthly premium”, with a warning that next month the interest rate would change. These emails contained a link to allegedly more detailed information and once the recipient clicked on it, a ZIP archive with the name ‘Dokumentation’ (documentation) or ‘Rechnung’ (bill) was downloaded on the computer. In both cases the archive contained Backdoor.Win32.Androm.dsqy. This member of the Andromeda family is a backdoor that allows attackers to control infected computers while remaining unnoticed. The infected computers often become part of a botnet.
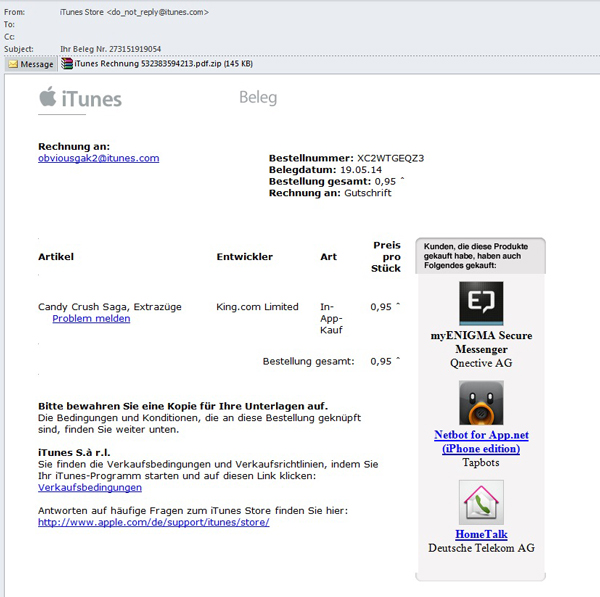
In May, the attackers sent out fake notifications on behalf of the popular iTunes Store. The recipient was informed about the alleged purchase of an application; the email even specified the name of the product and the price. The attached file, which was supposedly the invoice, in fact contained Trojan-Banker.Win32.Shiotob.f. This family of Trojans steals passwords stored in FTP clients and monitors browser traffic to intercept login details.
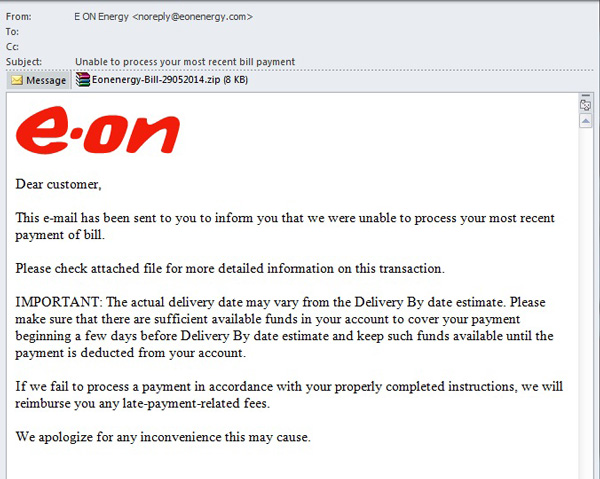
Customers of energy company E.ON, which generates and supplies electricity and heating in many countries, were also targeted by a similar scam. An email with the company logo sent on behalf of E.ON read: “This email is to bring to your notice that we were unable to process your last payment. See the details in the attachment”. The attached archive contained Trojan-Spy.Win32.Zbot.svvs, a representative of the popular Zbot family designed to steal personal data, especially banking information.
Phishing
In May, Email search sites (32.2%) topped the rating of organizations most frequently targeted by phishers with a slight growth of 0.5 percentage points from the previous month. Second came Social networks (23.9%), headed by Facebook. Financial and payment organizations were in third place with 12.8% (+0.2 percentage points) followed by Online stores (12.1%) whose share also grew 0.2 percentage points from April. The percentage of attacks targeting Telephone and Internet service providers fell by 0.4 percentage points compared with the previous month.The ranking is based on Kaspersky Lab’s anti-phishing component detections that are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
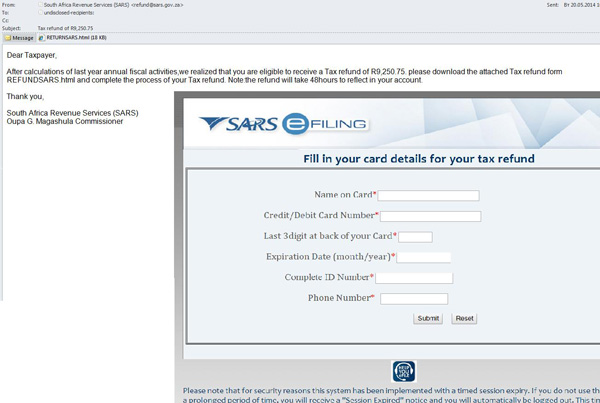
Fake tax notifications are frequently sent by fraudsters in order to install various malware on users’ computers. In May, we came across a fake notification supposedly sent on behalf of the State Tax Service of South Africa. The attachment contained a phishing HTML page rather than a malicious file. The attackers tried to persuade the recipient to enter his bank card details into a form on the pretext of returning overpaid tax. To make the page look legitimate the scammers used the logo of the Service and in the ‘From’ field they specified not only the name of the government organization but also its official address – sars.gov.za – as the server domain name.
Conclusion
The proportion of spam in global email traffic in May dropped 1.3 percentage points and averaged 69.8%.
The summer season and the end of the school year were used by spammers to spread tourism-themed spam advertising different summer vacation ideas for children, offers of help with academic work and invitations to buy ready-made qualifications from any higher education establishment. The annual increase in the quantity of tourist spam in the run-up to the holiday season is expected this summer too.
Mother’s Day was actively used in English-language spam to advertise various gifts. Insurance was another popular theme in May. Most Russian-language adverts offered car insurance, while in the English-speaking segment it was mostly life insurance.
The list of malware spread by email was again topped by Trojan-Spy.HTML.Fraud.gen. There were fewer members of the Bublik family in the May ranking – just five, compared with eight in April.
In May there was no big change in the organizations most frequently targeted by phishers. Email search sites (32.2%) were in first place, followed by Social networks (23.9%). Financial and payment organizations (12.8%) completed the top three.





















Spam in May 2014