
Spam: features of the quarter
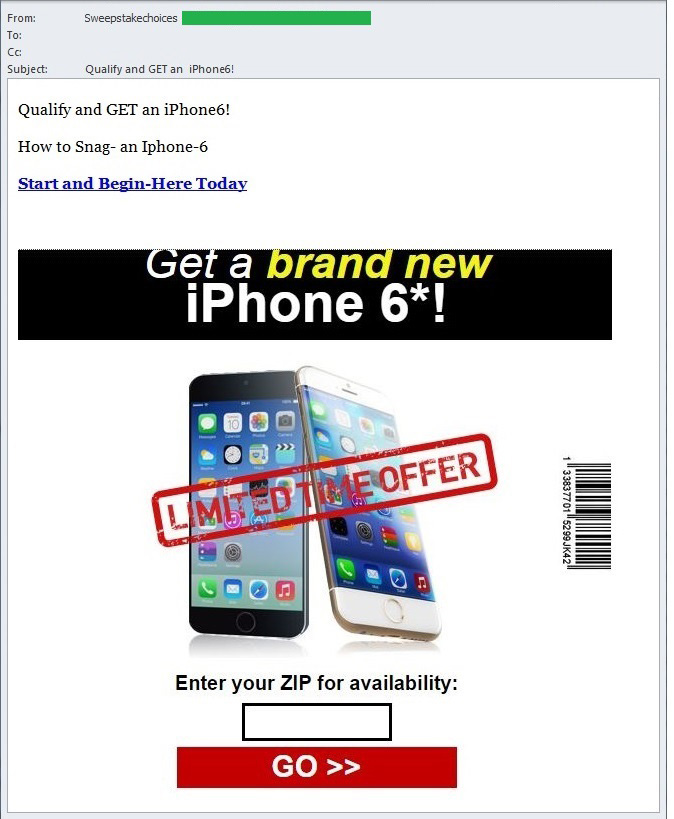
Appearance of the iPhone 6
In September there was a significant event in the IT industry – the iPhone 6 smartphone was presented to the public and put on sale. Not surprisingly, this was big news in the cybercriminal and spamming community as well and throughout the quarter we saw a sharp increase in spam about the famous brand. The number of phishing messages claiming to come from popular Apple services also significantly increased around the release date.
Spammers started offering the new smartphone long before its official release – as a prize for participating in questionnaires and special offers, as a gift when purchasing goods or using services offered in spam; the stylish accessory was the prize in various lotteries and featured in many false win notifications. Finally the iPhone 6 was offered for unbelievably low prices (compared to the official price).
Compared to the previous models the design of the iPhone 6 has several noticeable changes – including the size of the screen. This caused a burst of spam from factories producing all manner of accessories, actively offering protective cases and the like in the new size.
This all shows how a single event can trigger an increase in many different kind of spam, both swindles and adverts. In many cases it was also a powerful hook to draw attention to letters; the mere mention of the new iPhone in the subject header greatly increased the chances of the message being read.
Spam as a way to steal mail addresses
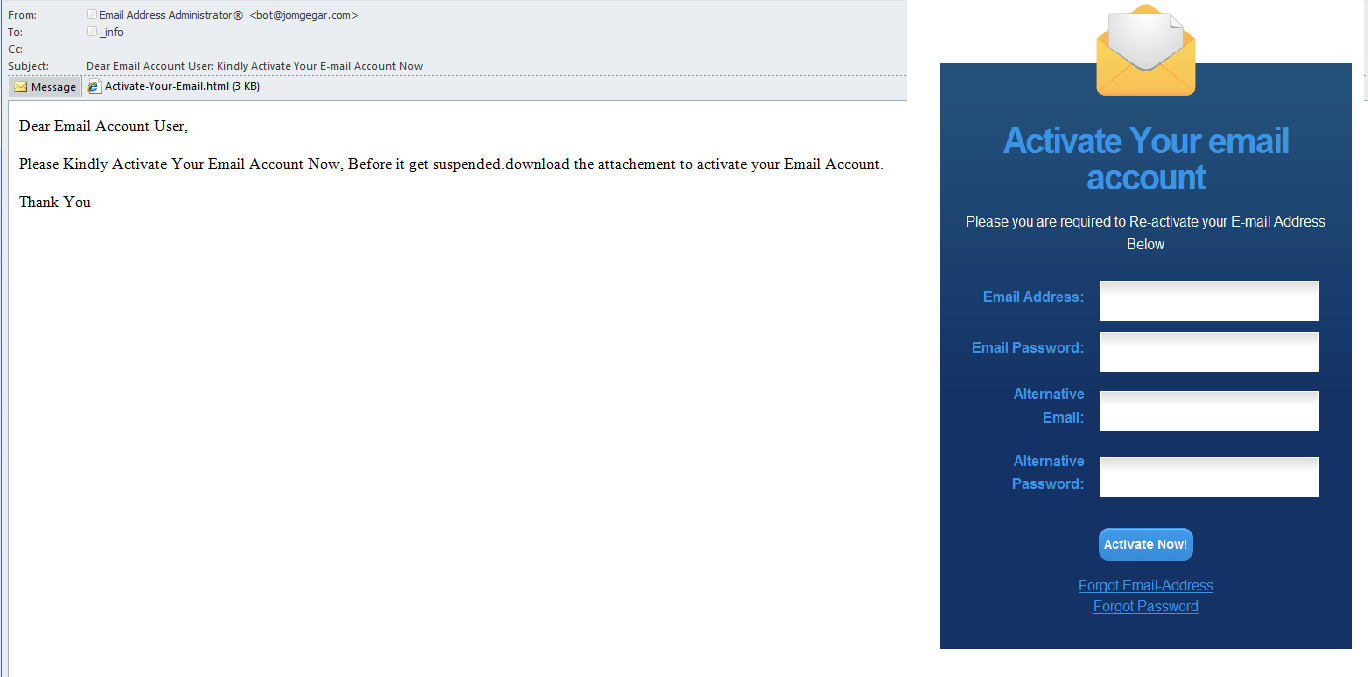
The last quarter saw several leaks of account logins and passwords from major mail systems. The data appeared on the net, which worried users and prompted lively discussions about confidentiality. At the same time the companies owning the mail services announced that most of the published data was from long abandoned accounts and the few that were still active were probably hijacked by phishing.
We note that the ID data for an email account doesn’t just give wrongdoers access to the owners’ personal correspondence and their address books; it also opens up other services provided by the mail host. Logins and passwords for other resources could also fall into unwelcome hands, especially those for social networks and online stores registered to that mailbox. The demand for email logins and passwords is underlined by the volume of phishing communications we have found that were designed specifically for this purpose that. In the third quarter we encountered phishing letters using various methods to con people out of their data. Here are a few examples:
- Communications in which a phishing HTML-page is inserted directly into the letter.
- Communications with phishing links in the text of the letter. The false link might be tied to a text fragment or shown in the text of the letter. Often the swindlers place phishing pages on specially created third-level domains.
- Communications in which an email address and password have to be sent to a specific electronic address.
Among the most popular tricks used for stealing data are warnings about exceeding the size of a mailbox, system updates and blocking mailboxes. And although these phishing letters frequently imitate communications from specific mail services the great majority of them are just general requests to confirm logins and passwords for email addresses. Probably this is because the conmen are sending false warnings to a whole database of addresses at once rather than going through the unprofitably time-consuming process of selecting specific mail services.
Spam is going beyond mail
Offers to conduct marketing campaign that will develop business and attract new clients is a popular and widespread trend in spam. Typically these involve mass mailshots to advertise services. Increasingly, though, these campaigns are moving away from mail services and email addresses and targeting mobiles and smartphones.
In the third quarter of 2014 spammers started offering SMS and instant messaging advertising more often. Does this mean that classic email spam is going to take a back seat and surrender its predominance to SMS spam? Having analyzed the link between SMS spam and email spam we came to the conclusion that this is unlikely. Firstly, more and more countries are alert to the problem of SMS spam and taking legislative measures banning this type of mass advertising. Secondly there is an obvious connection between all the media platforms used to distribute unwanted adverts and classic email spam.
The fact is, to find customers for their new products spammers continue to use old-fashioned techniques — with the help of spam mailings. There is even a specific type of email sendout in which spammers offer to buy readymade databases of electronic addresses and telephone numbers created using specific criteria to target a specific audience. There are also phishing mailshots aimed at collecting the personal data of users and organizations with the aim of consolidating them into databases for sale or use in mailshots. In this way spam is used to collect data for databases that are then offered for sale or used to send more spam. Spammers continue to use classic email spam to sell telephone numbers for use in SMS spam, and find buyers for their services.
Social networks are another media platform where spam distribution is growing. These have audiences in the millions and are gaining popularity all the time. At the same time hundreds of thousands of these accounts are “dead souls” – bots created specially for sending spam and stealing personal data from real users. In the last quarter we increasingly found spam content in apparently legal formal communications from social networks. What is happening is that almost all accounts in social networks are linked to the email addresses of their owners and messages distributed within the network are sent by email. The contents of such messages are typical spam: “Nigerian” stories of millions of dollars available to a helpful contact, offers of financial help to start a business or simply adverts for various goods.
This suggests that SMS mailshots and messages in social networks are not new types of spam but new methods that spammers have developed to deliver advertising to users. These are, in one way or another, linked to email spam. Moreover spammers can send the same message by various channels, which creates the impression of an increase in the overall quantity of unwanted adverts being sent.
New developments in “Nigerian” spam
In the third quarter conmen used the political situation in Ukraine and the media storm around the Ebola virus as inspiration for their “Nigerian-style” tales. Politics is a popular topic for this type of conman, as can be seen by the large percentage of letters discussing political themes or well-known public figures. It’s not surprising, then, that the situation in Ukraine was actively used during the third quarter. When creating the supposed authors of these messages the conmen didn’t just invent Ukrainians in various professions; they also conjured up politicians and businessmen offering cash rewards for help in transferring or investing large sums of money.
Letters concerning the Ebola virus were usually sent in the name of individuals from West Africa infected with the deadly virus. But there were unusual variations, for example invitations to related conferences. Regardless of the author of the letter and the convincing tales within the aim of the conmen does not change from year to year — to relieve the victims of their money.
Malicious email attachments
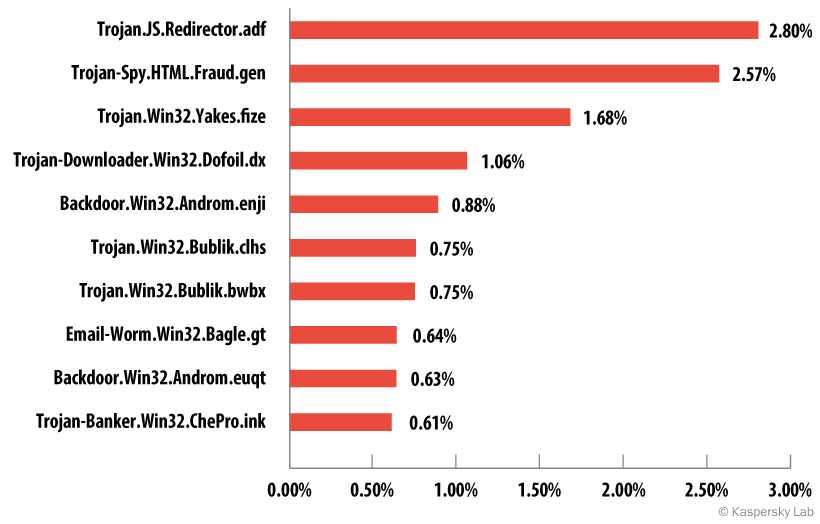
Top 10 malicious programs sent by email,
third quarter of 2014
In the third quarter of 2014 Trojan.JS.Redirector.adf was the malicious program most often distributed via email, according to our ranking. It appears as an HTML page which, when opened by users, redirects them to an infected site. There it usually offers to load Binbot — a service for the automatic trading of binary options, which are currently popular on the net. The malware spreads via email in a passwordless ZIP archive.
Next comes Trojan-Spy.HTML.Fraud.gen. This program was top of the list for several previous quarters but has finally been pushed down. Trojan-Spy.HTML.Fraud.gen is a phishing HTML page on which the user is asked to enter their confidential data. All the entered information is then sent to cybercriminals. Compared to the last quarter the figure for this malware has fallen by 0.62 percentage points.
In third place is Trojan.Win32.Yakes.fize, a Trojan loader of the Dofoil type. Its relative, Trojan-Downloader.Win32.Dofoil.dx, is in fourth. Malware programs of this type download another malicious program onto the user’s computer, start it and use it to steal assorted user information, especially passwords.
In fifth and ninth places are two members of the universal bot module family Andromeda/Gamarue – Backdoor.Win32.Androm.enji and Backdoor.Win32.Androm.euqt. The main features of these malware programs are the ability to download, store and run executable files, downloading and loading DLL (without saving on disk), downloading plugins and the capability of updating and deleting themselves. The bot’s functionality is enhanced with a system of plugins which can be downloded by the cybercriminals whenever necessary.
The sixth and seventh positions are taken by Trojan.Win32.Bublik.clhs and Trojan.Win32.Bublik.bwbx respectively. These are modifications of the well-known Bublik malware— a Trojan-loader that downloads a malicious file onto the user’s computer and launches it.
In eighth place is the mail worm Email-Worm.Win32.Bagle.gt. The main function of all mail worms is to collect email addresses from infected computers. A mail worm of the Bagle family can also accept remote commands to install other malicious programs.
Our rating is completed by Trojan-Banker.Win32.ChePro.ink. This downloader is created in the form of a CPL-applet (a control panel component) and downloads Trojans designed to steal confidential financial information. Most programs of this type are aimed at Brazilian and Portuguese banks.
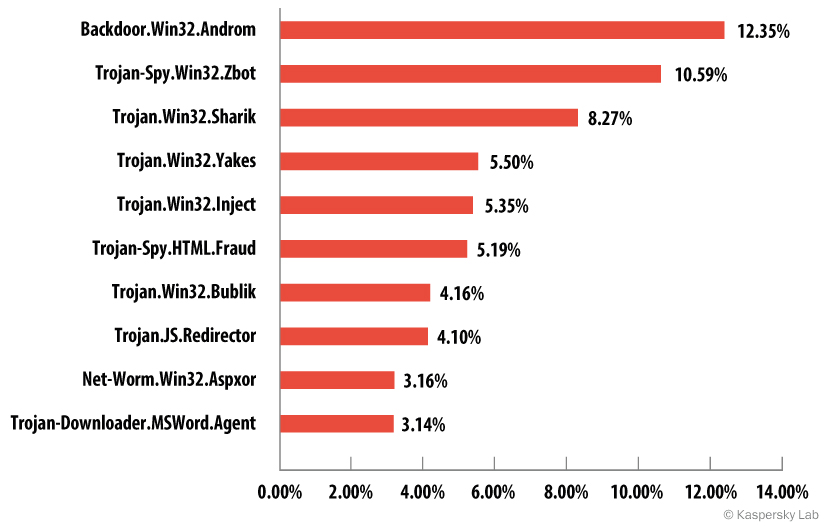
Distribution of email malware by family
As regards the most popular families of malicious programs, their email distribution is as follows:
TOP 10 families of malware programs distributed by email,
third quarter of 2014
Heading the rating is the Andromeda family, which accounts for 12.35% of all malware. In second place is ZeuS/Zbot: members of this family are designed for attacks on servers and users’ computers and also for capturing data. Although ZeuS/Zbot is capable of carrying out various harmful actions it is most often used to steal banking information. It can also install CryptoLocker – a malicious program that extorts money to decrypt users’ data.
Bublik, which often loads Zbot, also made the top 10 most frequently encountered malware families.
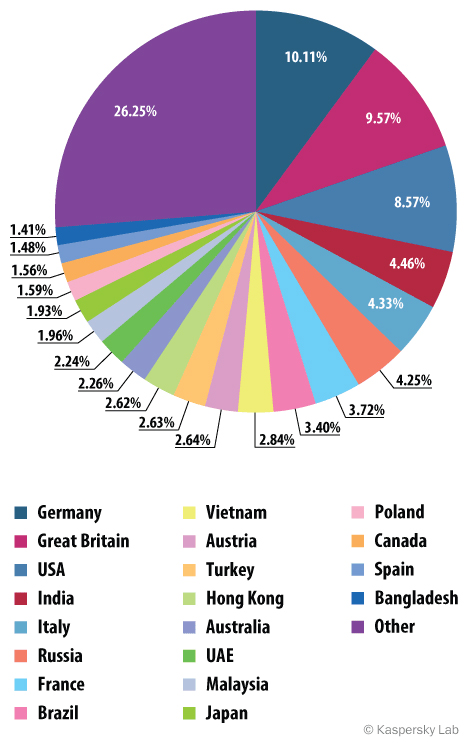
Countries targeted by malicious mailshots
Distribution of email antivirus activations by country,
third quarter 2014
In the third quarter there were some changes in the countries targeted by mailshots with malicious contents. Now we see Germany in top spot with 10.11%. Britain drops to second, losing 1.22 percentage points compared to the second quarter. In the third place is the USA, down 1.77 percentage points.
Russia, which in the second quarter was in 19th place with 1.48%, climbed to 6th place this quarter (4.25%); the share of malicious spam directed at the country increased almost threefold.
Special features of malicious spam
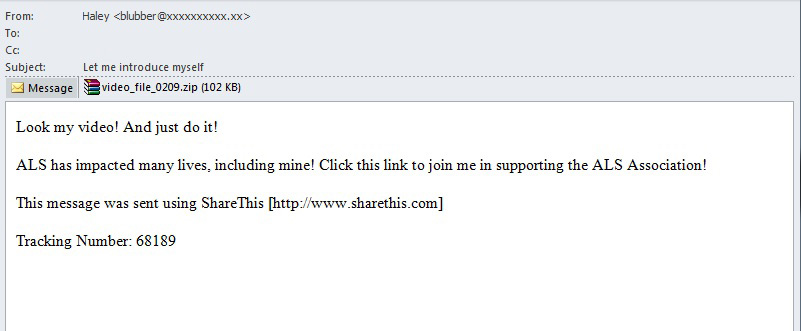
Ice Bucket Challenge
During the past quarter cybercriminals continued to use high profile events to attract attention to mailshots containing malware. This time around the Ice Bucket Challenge, a hugely popular summer campaign, was one of these events. The aim of this campaign was to raise awareness of amyotrophic lateral sclerosis, and also to collect funds to research the disease. An enormous number of people took part, many of them famous: actors, politicians, sportsmen and women, businessmen, and musicians poured ice-cold water over themselves, uploading videos of the process and passing the baton on further. At the peak of its popularity conmen got involved, seeing the campaign as a chance to attract attention to their malicious communications.
As a result unsuspecting users began to receive letters with offers to join the ALS association and change their lives, as thousands of others had already done. The recipients were offered an inspiring video to watch, located in an archive attached to the letter. But in place of the promised video a malicious program such as Backdoor.Win32.Androm.eu.op lay in wait. Such programs allow cybercriminals to infect computers, which often become part of botnets.
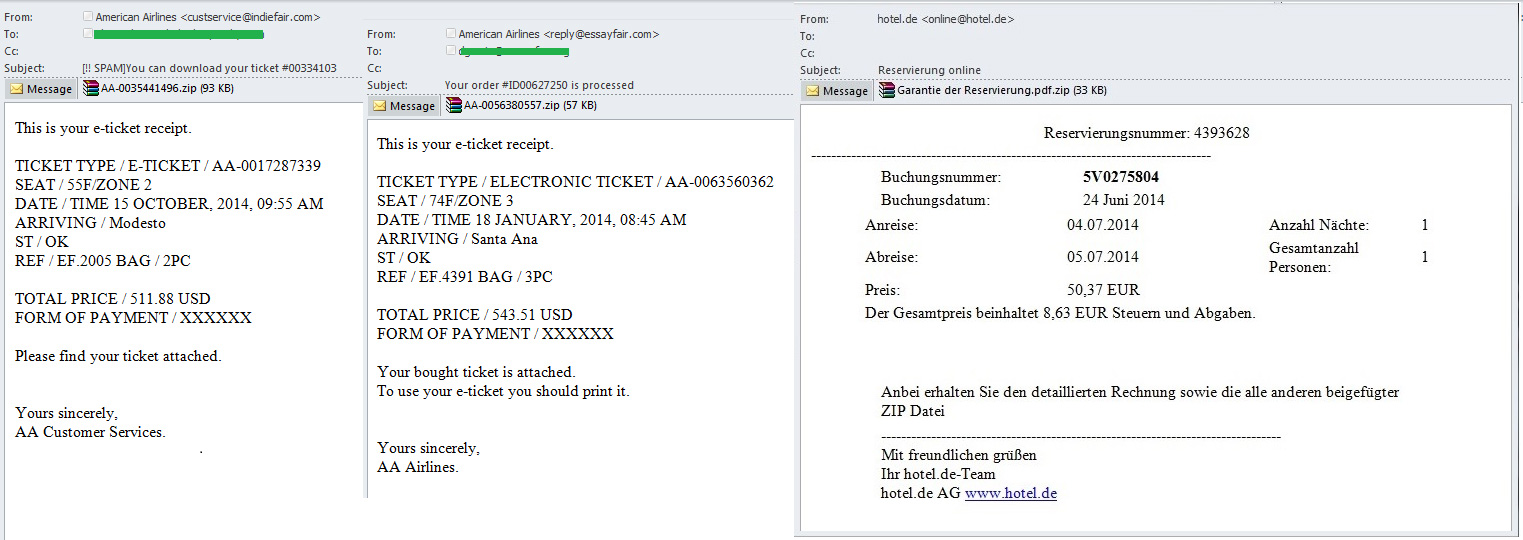
“Malicious messages” from booking systems
In the third quarter of 2014 cybercriminals sent some seasonal malicious spam tying in with the themes of the summer holidays. Spam traffic featured false messages from hotels, booking services and airlines in English and German. Traditionally the conmen try to convince users that a ZIP archive contains information about hotel bookings or air tickets.
Among others we found false communications from American Airlines; executable files were attached to letters that contained malware from the Net-Worm.Win32.Aspxor family. These net worms can send spam, download and run other programs, collect valuable data from the victim’s computer (saved passwords, mail and FTP accounts) and also automatically search for vulnerable sites for further infections to keep spreading the bot.
Forged letters in German, supposedly sent by an Internet portal for booking hotels in Germany, contained the malware Trojan-Spy.Win32.Ursnif. This Trojan steals confidential data and is capable of monitoring net traffic, loading and running other malware programs and also switching off several system applications.
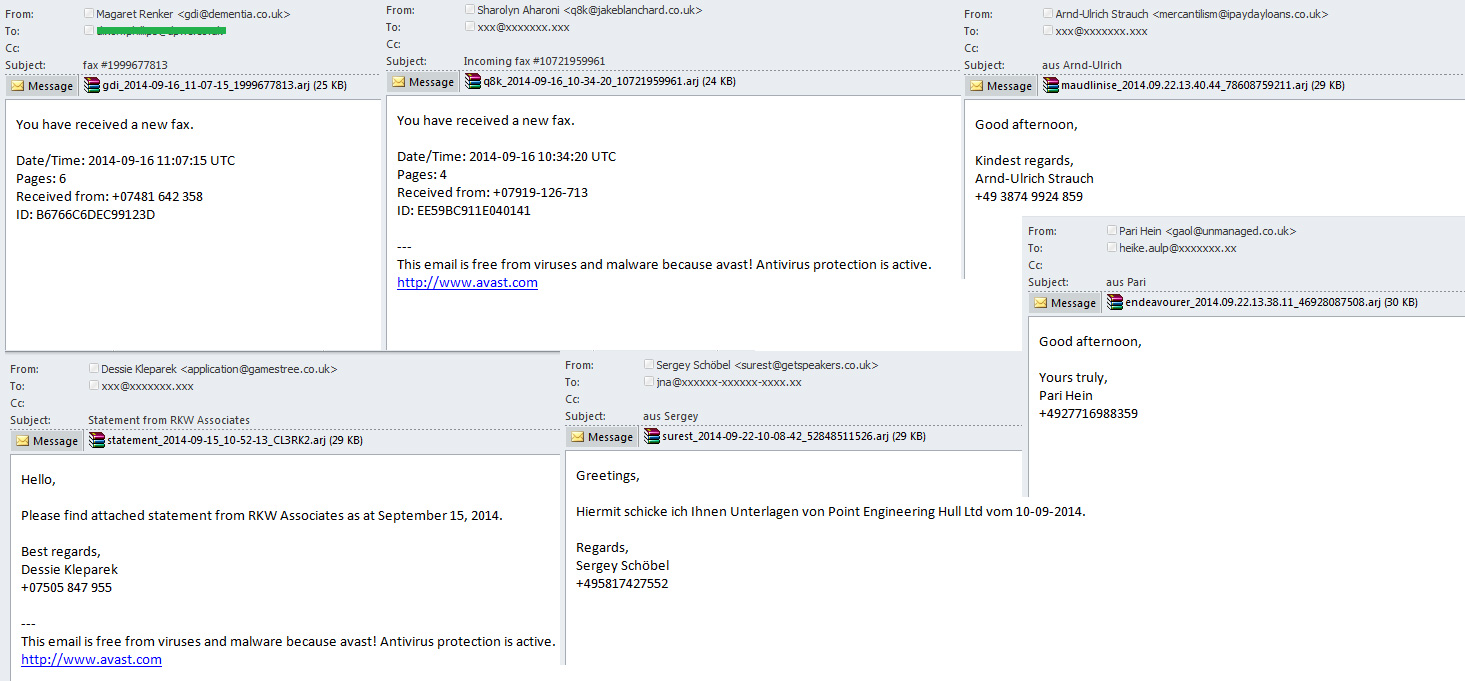
Malware in ARJ archives
In September we detected a major malicious mailout with an unusual attachment for spam letters — an archive in ARJ format. It should be noted that this choice of file archiver was probably made precisely because of the unusual file format. The criminals assumed users would be aware of the potential dangers of ZIP and RAR archive attachments but may be less suspicious of an unfamiliar tag. Furthermore the ARJ archiver allows the file size to be reduced considerably and its source code is available to all for study and modification.
The cybercriminals sent several types of malicious letter within one mailout. These were an announcement about receipt of a fax, an account statement from a specific company and a personal communication with a greeting in the body of the letter. All the letters had an attachment in the form of a malicious program from the family Trojan-Downloader.Win32.Cabby, which distracts victims with an RTF or DOC document and loads a malware program from the ZeuS/Zbot family at the same. All attachment filenames were generated using the same format. To give the letters a unique feel the cybercriminals changed several fragments of the text and the antivirus automatic signature.
Statistics
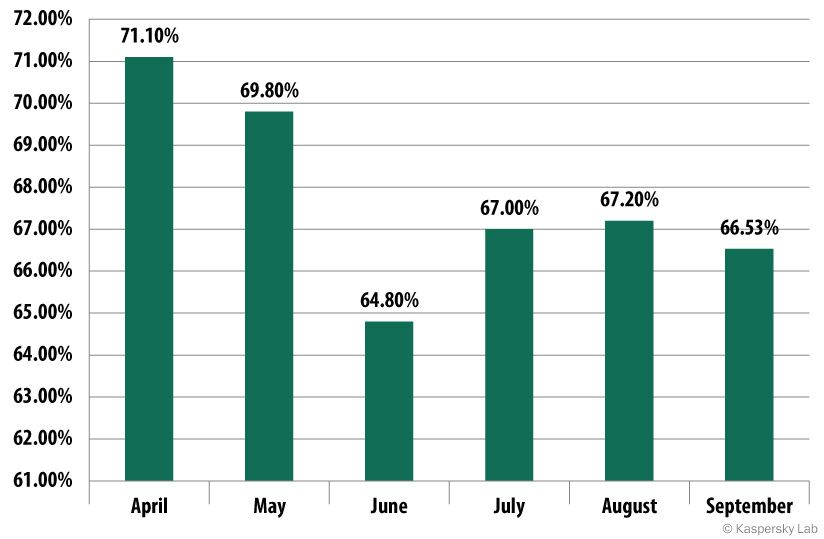
The proportion of spam in email traffic
The proportion of spam in email traffic,
April – September 2014
The proportion of spam in email traffic according to the figures for the third quarter of 2014 was 66.9%, which is 1.7 percentage points lower than in the previous quarter. The greatest amount of spam was sent in August and the least in September.
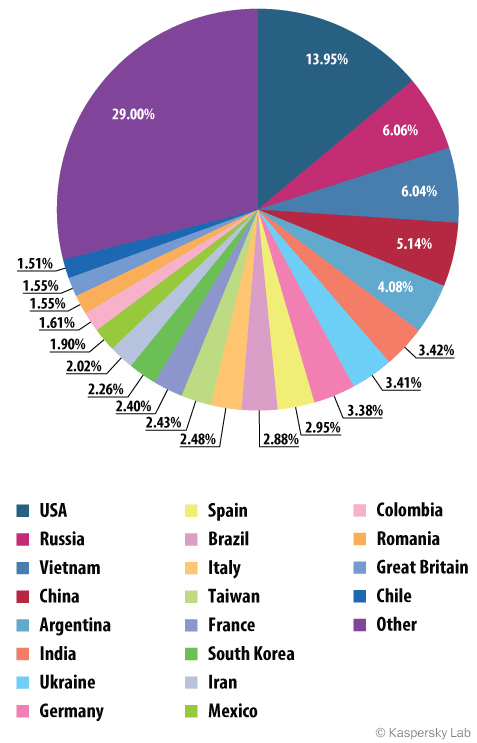
Spam source countries
Countries that are sources of spam,
third quarter 2014
In the third quarter of 2014 the USA remained the country that was the biggest source of spam, sending almost 14% of unwanted mail. In second place was Russia with 6.1%. Completing the trio of leaders was Vietnam with almost the same amount as Russia at 6% of the world’s spam.
The distribution of sources of spam had few surprises. China (5.1%), Argentina (4.1%), and Germany (3.5) made it into the top ten with Brazil in tenth place at 2.9%.
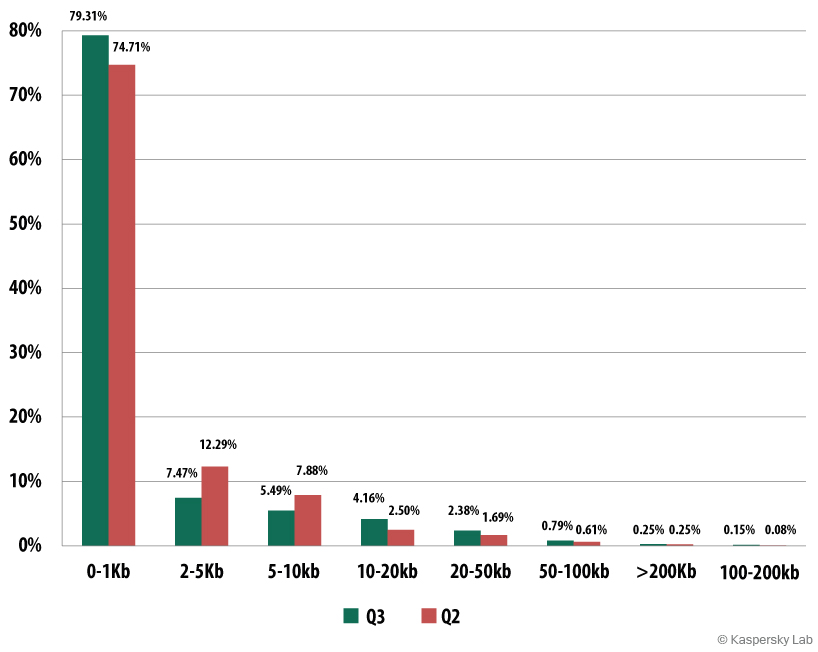
The size of spam letters
The sizes of spam letters,
third quarter 2014
The distribution of spam by size has hardly changed from the second quarter. The leaders remain very short letters of up to 1 Kb, which are quick and easy to handle in mass mailings. The proportion of these letters increased by 4.6 percentage points.
There was a slight reduction in the proportion of letters in the size range 2 Kb — 5 Kb — by 4.8 percentage points. There was also a small reduction in the amount of spam in the 5-10 Kb range, by 2.5 percentage points. However there was a 1.7 percentage point increase in the share of letters with a size of 10-20 Kb.
Phishing
In the third quarter of 2014 the computers of users of Kaspersky Lab products recorded 71,591,006 instances that triggered the “Antiphishing” system. This is 11.5 million more than in the last quarter.
As in the second quarter, the largest single group of users subjected to phishing attacks was in Brazil — the number was up 3.53 percentage points to 26.73%.
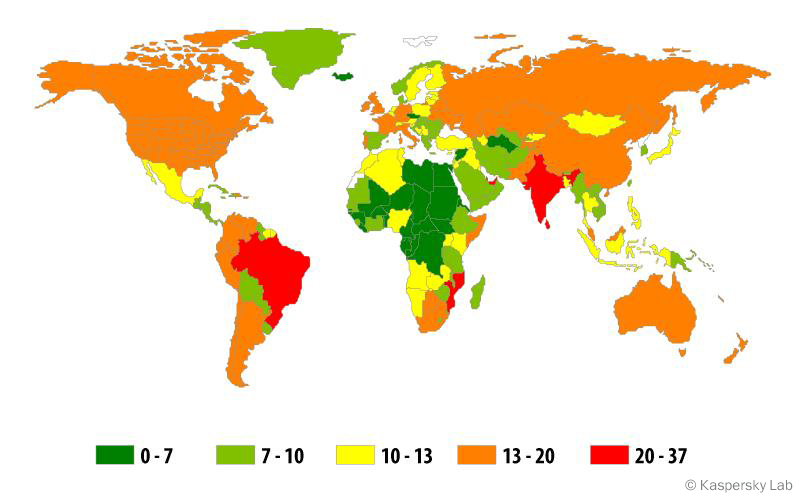
The geography of phishing attacks*,
third quarter of 2014
* The percentage of users on whose computers the “Antiphishing” system was triggered out of the total number of users of Kaspersky Lab products in the country
Top 10 countries by percentage of attacked users:
| Country | % of users | |
| 1 | Brazil | 26.73% |
| 2 | India | 20.08% |
| 3 | Australia | 19.37% |
| 4 | France | 18.08% |
| 5 | UAE | 17.13% |
| 6 | Canada | 17.08% |
| 7 | Kazakhstan | 16.09% |
| 8 | China | 16.05% |
| 9 | UK | 15.58% |
| 10 | Portugal | 15.34% |
There was a noticeable increase in attacked users in China (+4.74%), Australia (+3.27%), the UAE (+2.83%) and Canada (+1.31%).
Organisations under attack
The statistics on the targets of phishing attacks are based on the triggering of the heuristic component of the “Antiphishing” system. The heuristic component of the “Antiphishing” system is triggered when the user follows a link to a phishing page and there is no information about this page in the Kaspersky Lab databases. For this it is not important how the page was entered, as the result of clicking on a link in a phishing letter, a social network message or, for example, as the result of an action of a malicious program. As a result of the triggering the user sees a warning of the possible threat in the browser.
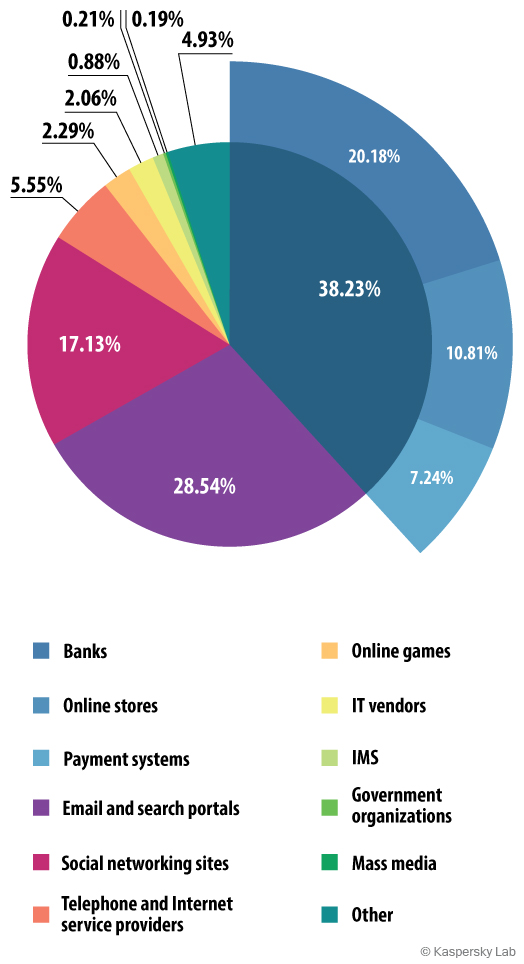
As before, the “Email and search portals” category (previously known as “Global Internet portals”) was the group of organizations most often subject to phishing attacks. However the share for this category has dropped sharply – by 22.15 percentage points – and in the third quarter it stands at 28.54%.
Distribution of organisations subject to phishing attacks,
third quarter of 2014
In the third quarter of 2014 the “Online finance” category saw a 13.39 percentage point rise to 38.23%. Within its sub-categories there were increases for the second quarter in a row for “Banks” (+6.16%), “Payment systems” (+5.85%) and “Online shops” (+3.18%).
Distribution of phishing attacks on payment systems,
third quarter 2014
Phishing attacks on payment systems are particularly attractive because conmen can get their hands directly on their victims’ money. Paypal was the most frequently targeted payment system (32.08%) with Visa (31.51%) close behind and American Express in third with 24.83%.
Phishing attacks on the users of payment systems are often conducted by sending false letters, apparently written by representatives of the financial organizations. These letters contain threats to block the account or stop account activity and are designed to startle users into a rash response, which could include transferring confidential information to cybercriminals.
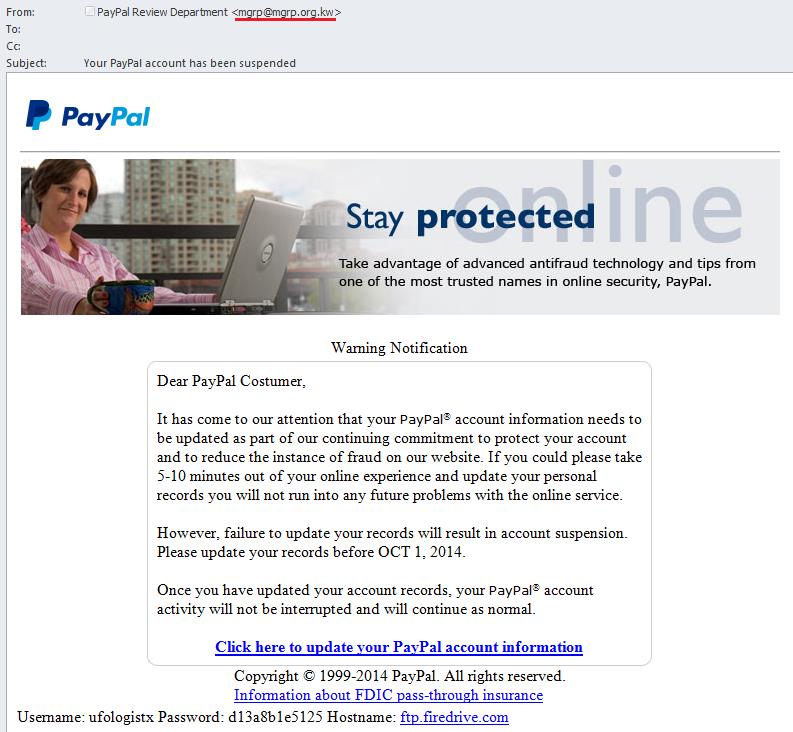
An example of a phishing letter with a threat to block the victim’s account
In this example the letter was sent from a suspicious address that didn’t match Paypal’s usual mailing address. There was a threat to the user that the account would be blocked if account data was not renewed, and a request to follow the link and enter personal data on the page that opened.
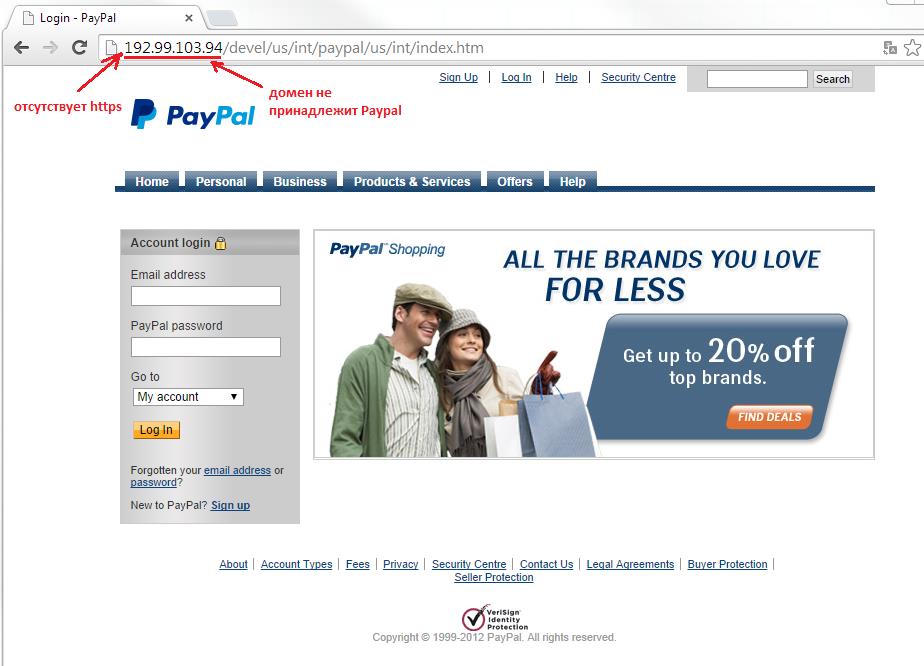
Phishing page imitating a Paypal website page
Following the link the user sees a page imitating the layout of the official Paypal website, with a form for the entry of personal data. However the connection to this page is not protected, which is shown by the lack of HTTPS in the address line and the indicated IP address does not belong to Paypal.
Top 3 attacked organizations
| Organization | % of phishing links | |
| 1 | 10.34% | |
| 2 | 10.21% | |
| 3 | Yahoo! | 6.36% |
The top three target organizations remain Google, Facebook and Yahoo!, however there have been changes within the top three. The numbers for Google (10.34%) and Facebook (10.21%) have increased slightly: these organizations have gone up a place in step. Yahoo!, which was the undisputed leader in the first half of 2014, has dropped down to third — the figure for the organization decreased by 24.62% to 6.36%.
Hot topics in phishing
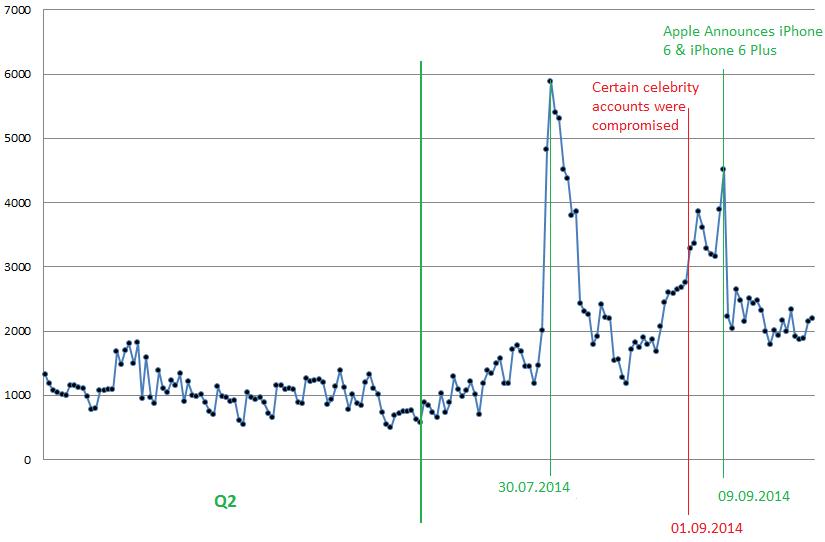
Apple was not in the top three, although it climbed in the rating of organizations subject to phishing attacks to reach fourth place with a figure of 1.39% (+0.98%). At the beginning of September the company was involved in a major scandal, connected with leaked photographs of famous people from its iCloud storage servcie. Apple dismissed rumours about the presence of vulnerabilities in the service leading to leaked data; it could be the result of a phishing attack targeting users of Apple products (it is not clear whether this was a targeted attack or if hackers were simply lucky that there were several stars among their victims).
In addition, the new iPhone 6 and 6 Plus were announced on 9 September. Major events in a company usually attract additional interest from swindlers so it is not surprising that we recorded a growth in the number of false communications sent in the name of representatives of Apple services such as iTunes and iCloud.
Conmen used the name of the company to attract users’ attention and frequently used the same letter format, changing only the name of the Apple service.
Number of daily phishing attacks imitating pages of Apple resources,
second and third quarters of 2014
Apple uses a two stage check for Apple ID to protect the personal data of users, including the registration of one or several trusted devices. The two stage check eliminates the possibility of unsanctioned access to or alteration of the user’s registered details and prevents outsiders from making purchases by using stolen registration details. On 5 September Apple announced that it would soon be taking additional safety measures which would inform users of suspicious activity on their accounts.
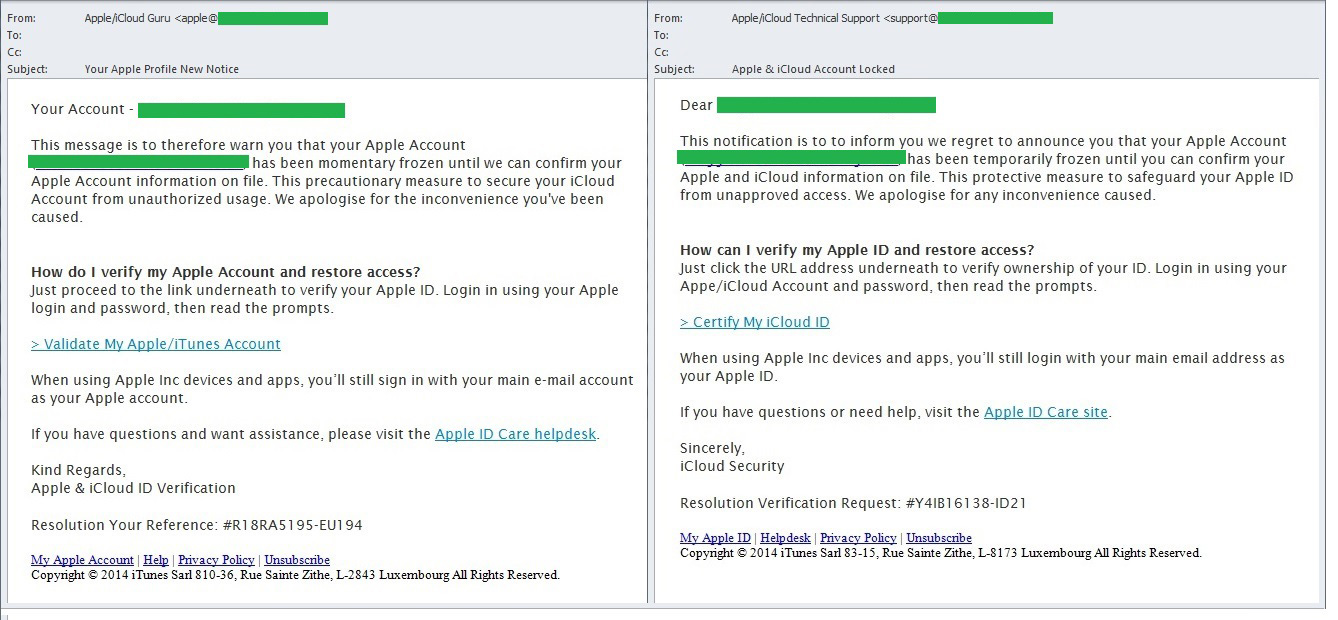
Example phishing pages requesting Apple ID data
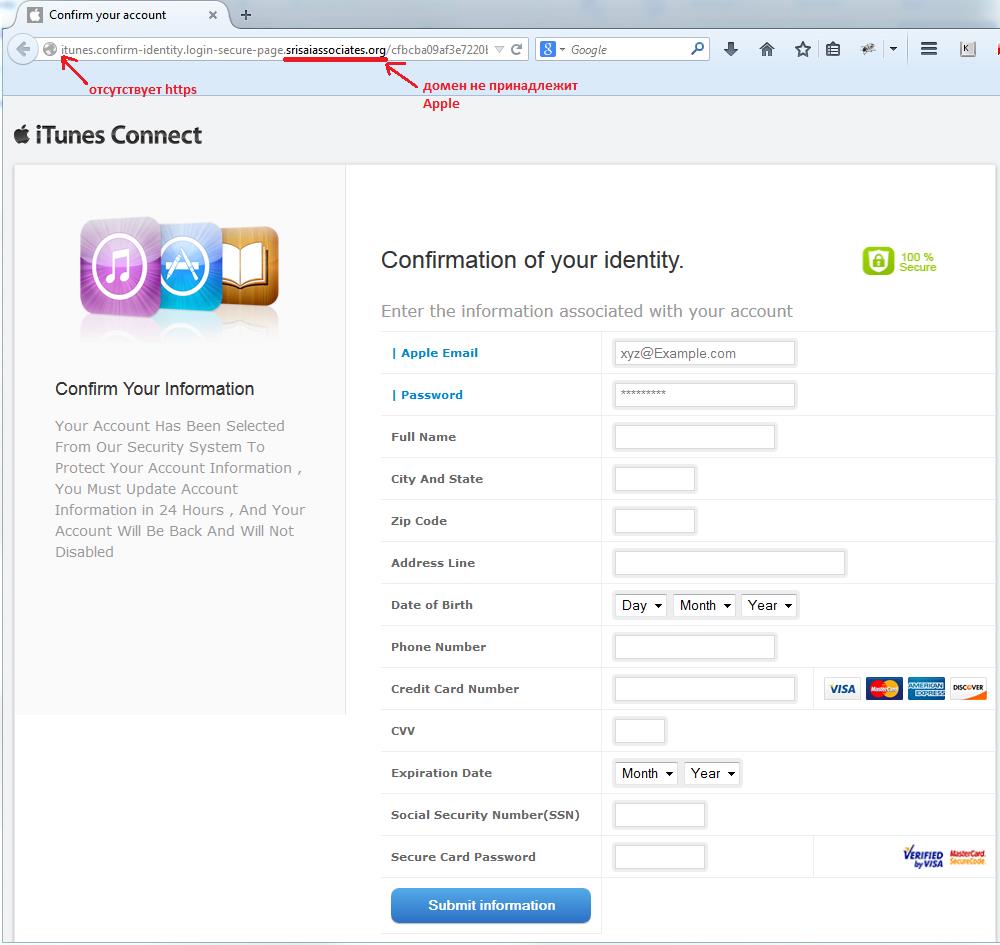
Among other things, users can improve their safety by attentively studying any page that asks for confidential information. Attention should be paid to the presence of a protected connection and whether the domain belongs to Apple. It is worth considering what information is being requested – conmen frequently ask for information unrelated to what is needed for using Apple ID; they often ask for bank card details under the pretext of linking them to the account. In these cases if the users independently supply the swindlers with financial information Apple’s defenses cannot protect them from the consequences.
Example of a phishing page imitating an Apple request for confirmation of personal information
Conclusion
The share of spam in email traffic for the third quarter of 2014 was 66.9%, which is 1.7 percentage points less than in the last quarter.
The topics of spam in the third quarter strongly reflected major news events such as the release of the iPhone 6, political developments in Ukraine, the leak of network passwords from major mail services, the Ice Bucket Challenge campaign and the summer holiday season. Major world events are also actively exploited in “Nigerian” spam.
The three leading source countries for spam sent across the world are the USA (14%), Russia (6.1%) and Vietnam (6%).
The rankings of malware programs sent by email, according to third quarter figures, are headed by Trojan.JS.Redirector.adf (2.8%), which sends users to an infected site. Among the families of malicious programs the Andromeda family was the leader with a 12.35% share of all malware. Users in Germany experience more attacks than those anywhere else.
The third quarter saw spam traffic consisting of phishing letters aimed at trying to steal logins and passwords for email accounts, and the release of the new iPhone saw a flare up of phishing communications apparently sent from the Apple iTunes and iCloud services.
In order to install their malicious programs on users’ computers in the third quarter cybercriminals sent out not only false communications from hotel booking services and airlines but also letters with long unused file archivers.
The growth of phishing attacks on organizations involved in online financial operations continued (banks, payment systems, online shops). There was a significant reduction in the number of attacks on organizations from the category “Email and search portals”, down to 28.54%. There was also a noticeable reduction in the proportion of attacks directed at Yahoo!, one of the organizations in this category.


























Spam and phishing in the Q3 of 2014