
Quarterly highlights
Blockchain and spam
Cryptocurrencies have been a regular theme in the media for several years now. Financial analysts predict a great future for them, various governments are thinking about launching their own currencies, and graphics cards are swept off the shelves as soon as they go on sale. Of course, spammers could not resist the topics of cryptocurrency, mining and blockchain technology.
Last quarter we wrote that many Trojans were downloading ‘miners’ as a payload on victims’ computers, and in third quarter of 2017 this practice became even more widespread.
Fraud, cryptocurrencies and binary options
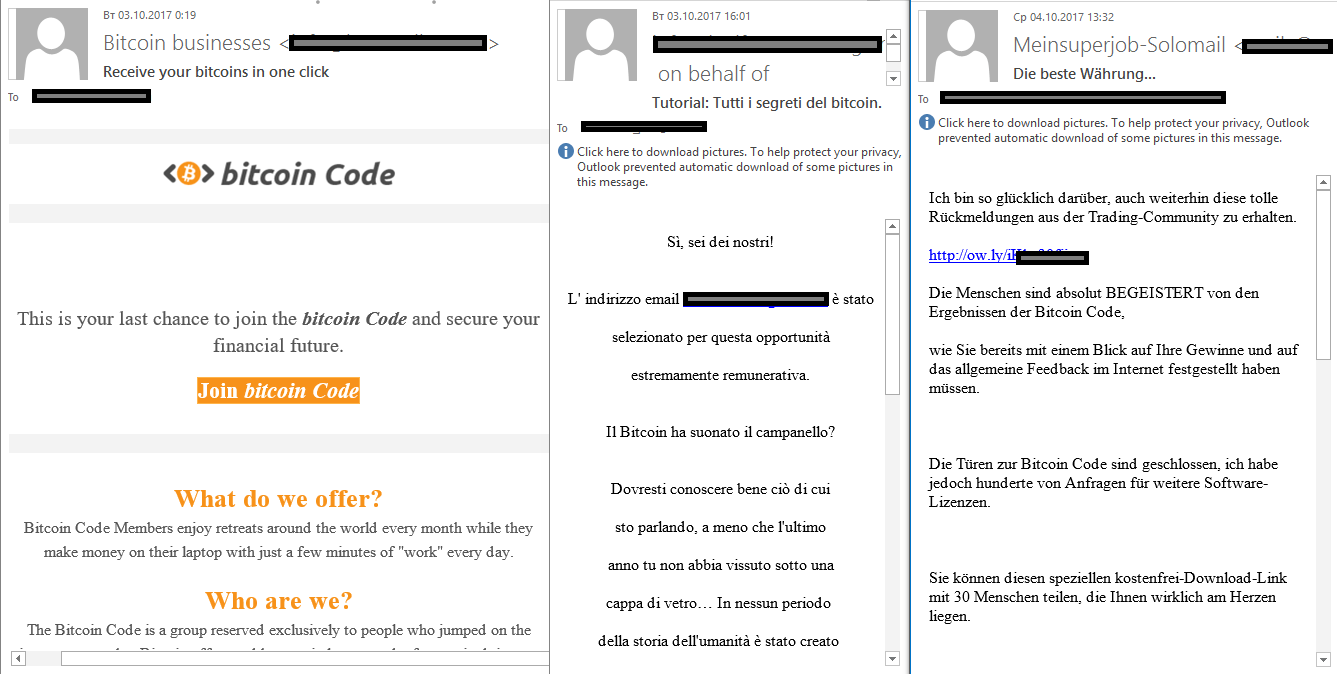
Financial fraud makes very active use of the cryptocurrency topic: users receive messages that vividly describe the use of special software for trading on the cryptocurrency market and how it can secure their financial future.
After clicking on a link, users end up on a site where they are once again persuaded to join the ranks of the rich who only have one problem in life – how to spend their money. In reality, such sites are partners for shady brokerage houses, and purveyors of new, inexperienced customers. It is there that new users are redirected.
The plan is to get the victim to deposit a certain amount to their account, usually several hundred dollars, for the opportunity to start trading. We should note here that we’re no longer talking about cryptocurrencies – in most cases, trading involves binary options.
The problem is not even in the questionable legality of the actual trading, but that no one guarantees the honesty of the brokerage offices and, consequently, there are no guarantees that the invested funds will be returned. The fraudsters start by motivating people to invest more and more money, and then simply disappear, leaving the victim to read angry reviews on the Internet from other cheated depositors.
There are also more primitive types of fraud, where the email directly asks the recipient to transfer bitcoins to a specific wallet, with a promise to return the investment with interest five days later. But only the most naïve recipients are likely to fall for such an offer.
Webcasts
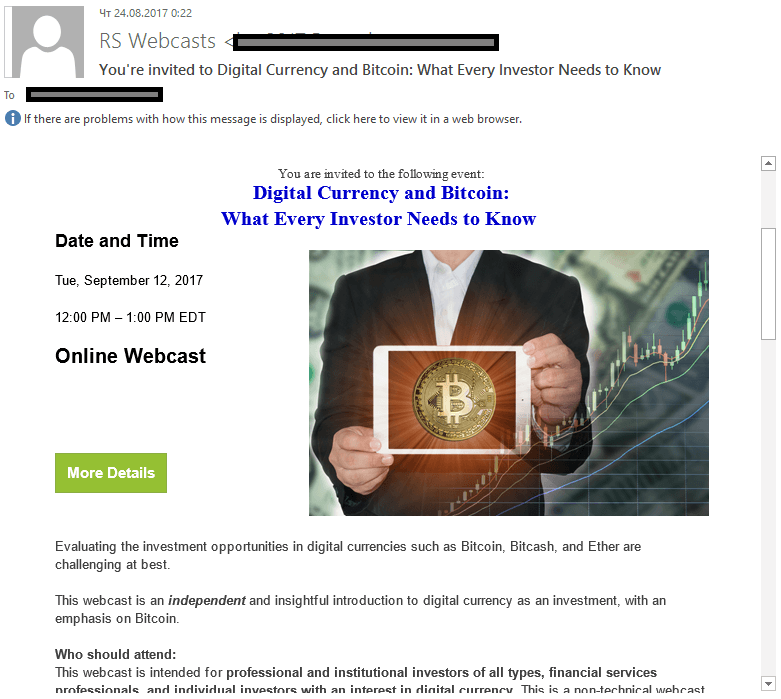
Another example of the cryptocurrency theme being used in spam is that of webcasts. In most cases, scammers suggest taking a study course that will help the user understand more about cryptocurrencies and how to invest in them. Of course, the sums invested in “training” will result in huge profits in the near future, according to the organizers.
Natural disasters and the ‘White House administration’
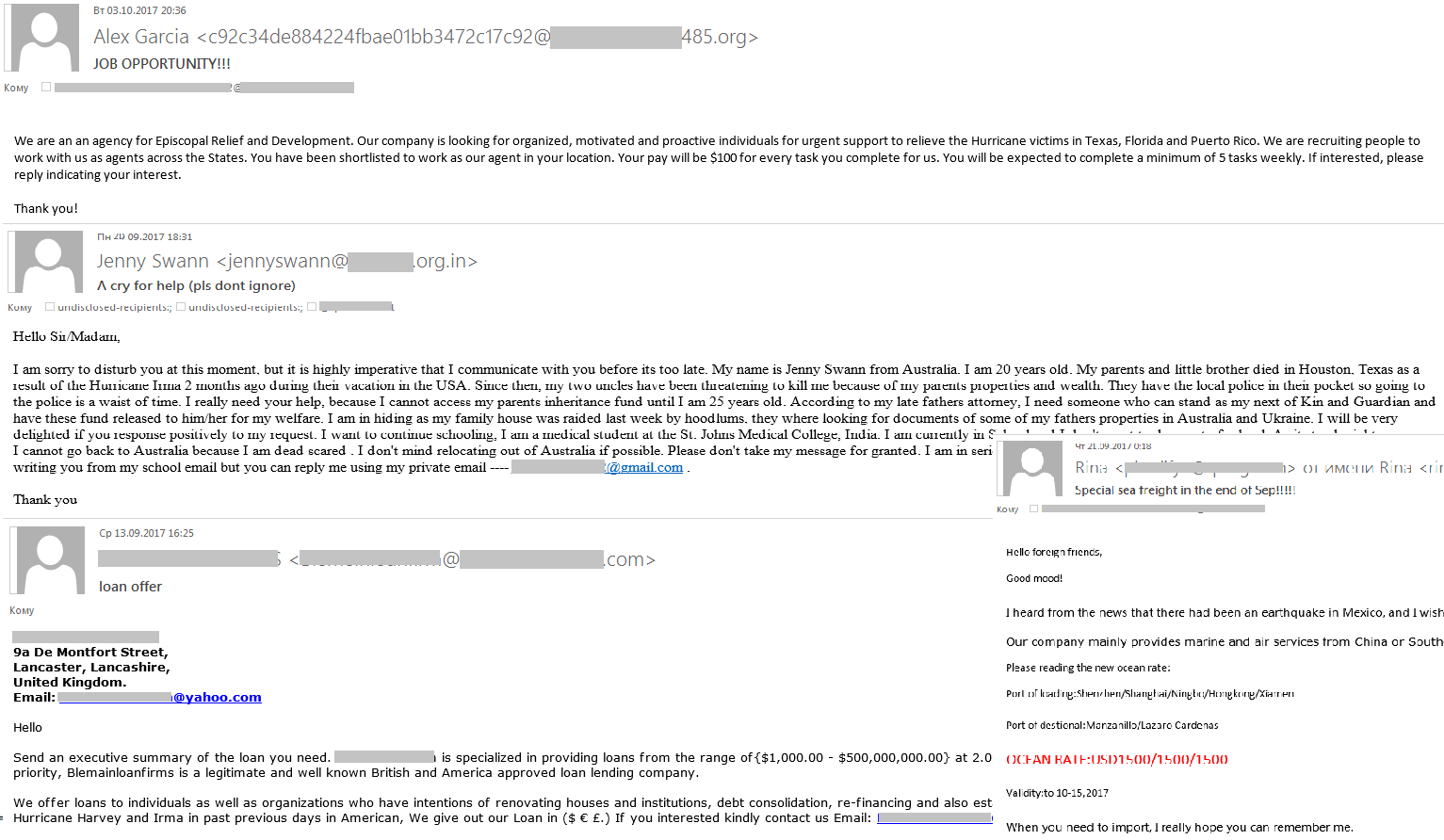
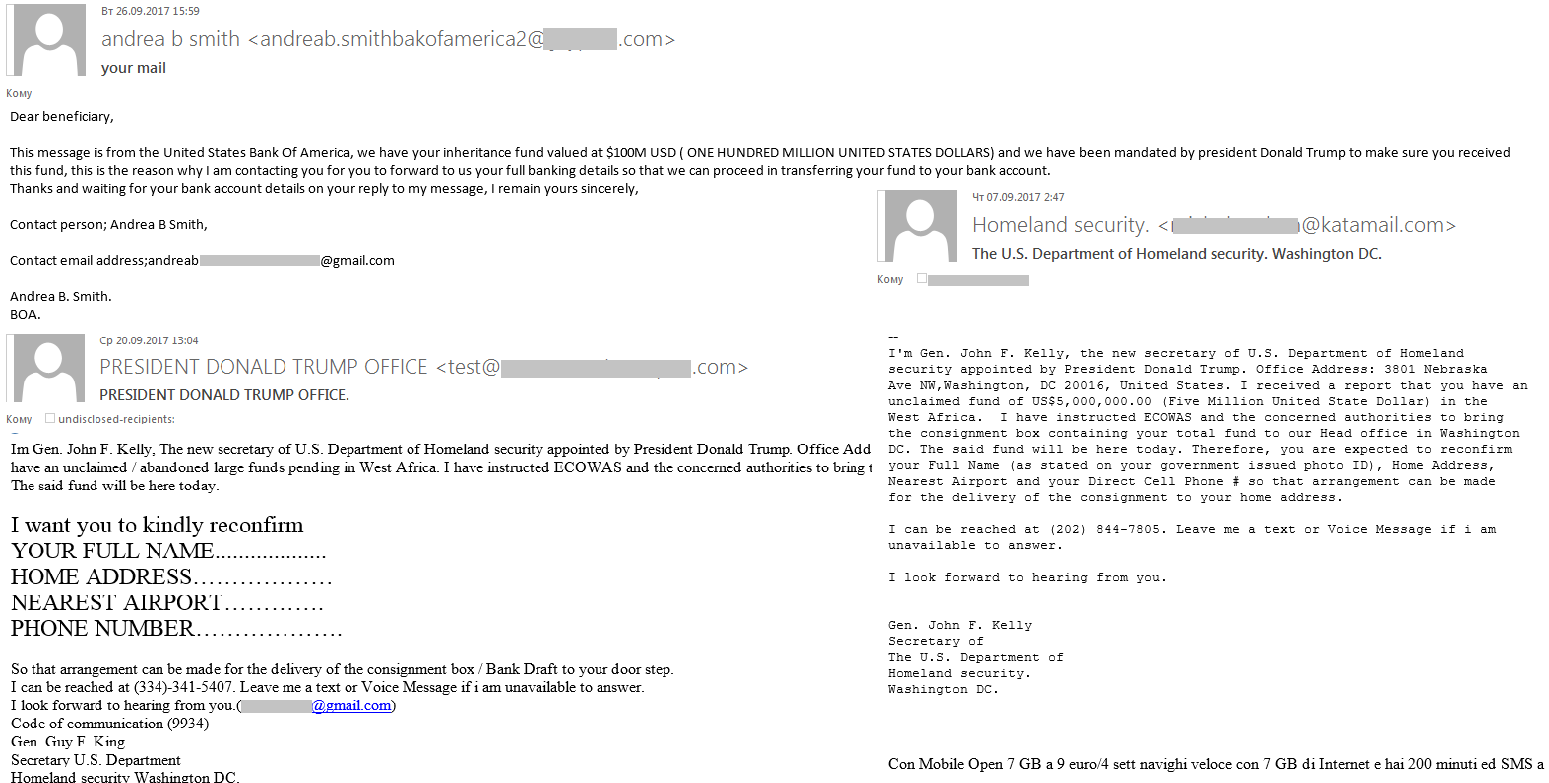
In August and September, the world’s attention was focused on hurricanes Irma and Harvey, and the earthquake in Mexico. There were dozens of victims of these disasters, and the damage caused was estimated to be billions of dollars. These tragic events inevitably attracted the attention of so-called Nigerian scammers trying to cash in on people’s grief. They sent messages on behalf of family members whose relatives died during the hurricanes and asked for help obtaining an inheritance left by them. Natural disasters were also mentioned in emails promoting job offers and loans.
In the third quarter, ‘Nigerian’ letters also mentioned the name of Donald Trump, the current US president. The authors pretended to be representatives of state or banking organizations, and to make their message sound more important they claimed they were appointed by the US president or were acting on his behalf. The spammers spun the standard tales in their fraudulent letters, promising millions of dollars to users, with the scammers asking for personal information so that they could supposedly track the money transfer. The letters contained identical text but with different layouts and contact details.
B2B fakes in malicious emails
There is still a tendency to create emails with malicious attachments for fake commercial offers. At times their quality is so good that you suspect they could be a man-in-the-middle attack.

The file in the attachment is detected as HEUR: Trojan.Java.Agent.gen. This malware is written to startup and tries to close programs such as Process Hacker, system explorer and security software processes. It then communicates with the remote server and waits for the command to install other malicious programs

The attachment is detected as HEUR: Exploit.MSOffice.Generic, exploiting the vulnerability CVE-2017-0199 in MS Word. As a result, other malicious programs are downloaded to the victim’s computer

Both archives contain the same malicious object, detected as Trojan.Win32.VBKrypt.xtgt. It collects information from the victim’s computer and transfers it to the remote server
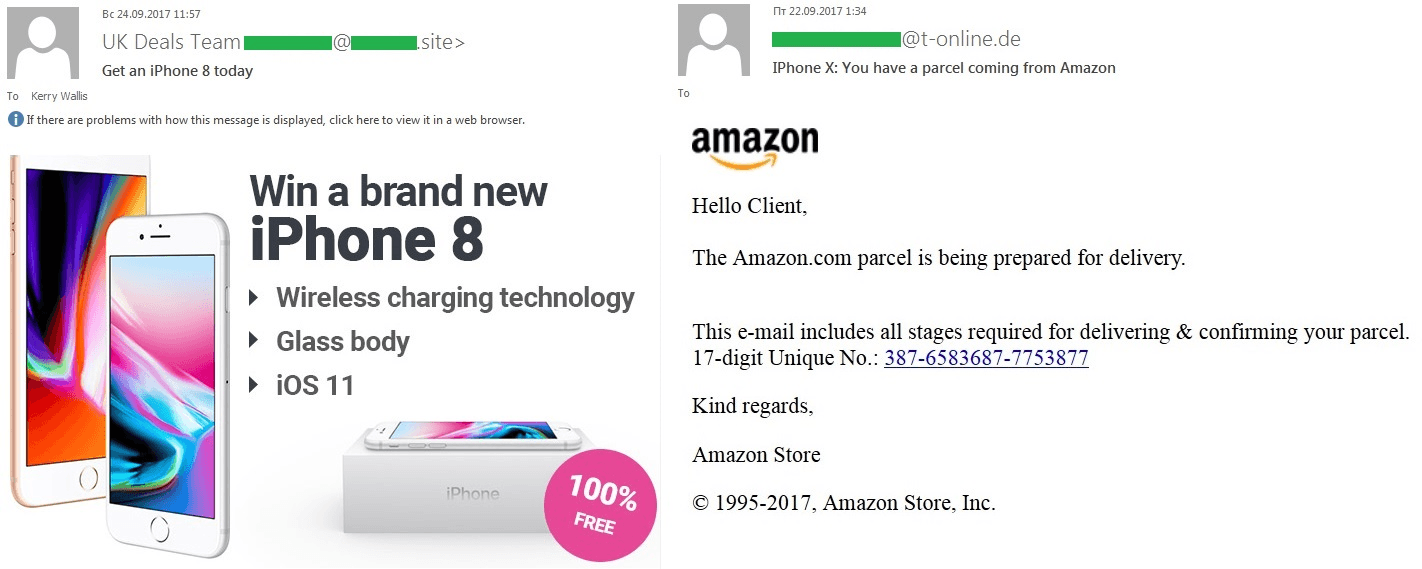
Release of new iPhone
In September, Apple unveiled the new models of its smartphone – iPhone 8 and iPhone X. This event was widely covered in the media, and spammers, weren’t going to miss out.
Even before the official presentation, we began to record spam mailings with offers to test the updated phone for free and participate in a prize draw to win one. Some mailings even reported the recipient had won a device before it was publicly unveiled. In most cases, the links in these emails could end up downloading Reimage Repair ‘advertising software’. Immediately after the release of the smartphone, Chinese factories got in on the act, sending out emails advertising various accessories for the new model. Our traps also recorded a large volume of phishing associated with the purchase and delivery of the popular gadget.
Statistics
Proportion of spam in email traffic
In the third quarter of 2017, the largest share of spam was recorded in September – 59.56%. The average share of spam in global email traffic was 58.02%, which was almost 1.05 p.p. more than the average for the previous quarter.
Sources of spam by country
According to the results for the third quarter of 2017, China (12.24%) became the biggest source of spam, after finishing third the previous quarter. Last quarter’s leader Vietnam (11.17%) was second after a decrease of 1.2 p.p. The US fell one place to third (9.62%), while India (8.49%) remained fourth in this rating. Iran rounded off the top 10, accounting for 2.07% of all spam.
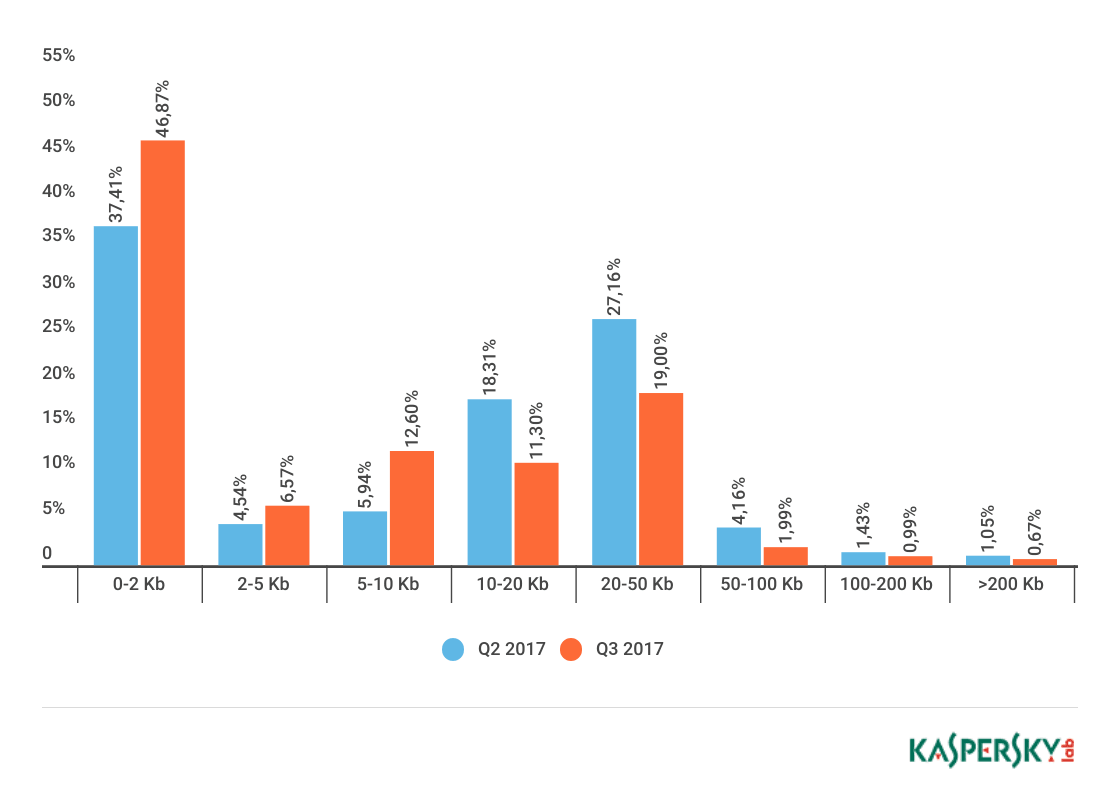
Spam email size
The share of very small emails (up to 2 KB) in spam increased by 9.46 p.p. to 46.87% in the third quarter. The proportion of emails between 5 and 10 KB in size also increased by 6.66 p.p. compared with the previous quarter and amounted to 12.6%.
The number of emails between 10 and 20 KB decreased, however, with their share falling by 7 p.p. There was also a decrease in emails sized 20 to 50 KB. Their share this quarter amounted to 19%, which was a fall of 8.16 p.p. compared to the previous reporting period.
Overall, the number of very small emails continues to grow.
Malicious attachments in email
Top 10 malware families
Backdoor.Java.QRat (3.11%) became the most widespread malicious program family in email traffic. Next came the Trojan-Downloader.VBS.Agent family (2.95%), followed by Trojan-Downloader.JS.SLoad (2.94%). The newcomers in this rating – Trojan.Win32.VBKrypt and Trojan-Downloader.VBS.SLoad (a VBS script that downloads and launches other malicious programs on the victim machine, usually cryptographers) occupy fifth and eighth places with 2.64% and 2.02% respectively. The Trojan.PDF.Badur family (1.79%) rounds off the top 10.
Countries targeted by malicious mailshots
Germany remained the country targeted most by malicious mailshots in the third quarter of 2017. Its share increased by 6.67 p.p. and amounted to 19.38%.
China came second, with 10.62% of mail antivirus verdicts recorded there – a drop of 1.47 p.p. compared to Q2. Russia, which came fifth the previous quarter, completed the top three (9.97%) after its share increased by 4.3 p.p. Fourth and fifth were occupied by Japan (5.44%) and Italy (3.90%) respectively.
Phishing
In the third quarter of 2017, the anti-phishing system prevented 59,569,508 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 9.49% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q3 2017.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks was once again Brazil (19.95%, +1.86p.p.).

Geography of phishing attacks*, Q3 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
Australia (16.51%) came second after its share increased by 3.81 p.p. In third place was New Zealand (15.61%, + 3.55pp). China (12.66%) fell from second place to fourth, with its share losing 0.19 p.p. Next came France (12.42%), Peru (11.73%), Argentina (11.43%), Canada (11.14%), Qatar (10.51%,) and Georgia (10.34%).
| Brazil | 19.95% |
| Australia | 16.51% |
| New Zealand | 15.61% |
| China | 12.66% |
| France | 12.42% |
| Peru | 11.73% |
| Argentina | 11.43% |
| Canada | 11.14% |
| Qatar | 10.51% |
| Georgia | 10.34% |
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In the third quarter of 2017, almost half (47.54%) of the heuristic components of the anti-phishing system were recorded on pages with references to brands from financial categories such as Banks (24.1%, + 0.61 p.p.), Payment systems (13.94%, -4.46 p.p.) and Online stores (9.49%, -0.08 p.p.).
Hot topics this quarter
Airline tickets
Last quarter we described a scam involving a free giveaway of airline tickets supposedly by popular airlines, with information being spread via reposts from victims on a social network. In the third quarter, scammers continued to spread the ‘giveaway’ using WhatsApp instead. Judging by the decrease in the number of anti-phishing verdicts in the Airlines category, however, we can assume that this approach wasn’t as effective.
The downturn may also be due to the fact that scammers switched to ‘prize draws’ not only for air tickets but also other prizes, for example, sports shoes, cinema tickets, gift cards for Starbucks, etc.
Before you could claim your prize you had to share information about the prize draw with eight contacts on WhatsApp.
After clicking the button, users are redirected to WhatsApp.
After sending the message to their contacts the victim, instead of winning a prize, is redirected to some dubious resource, for example, a page where malicious extensions are installed, a new survey, etc.
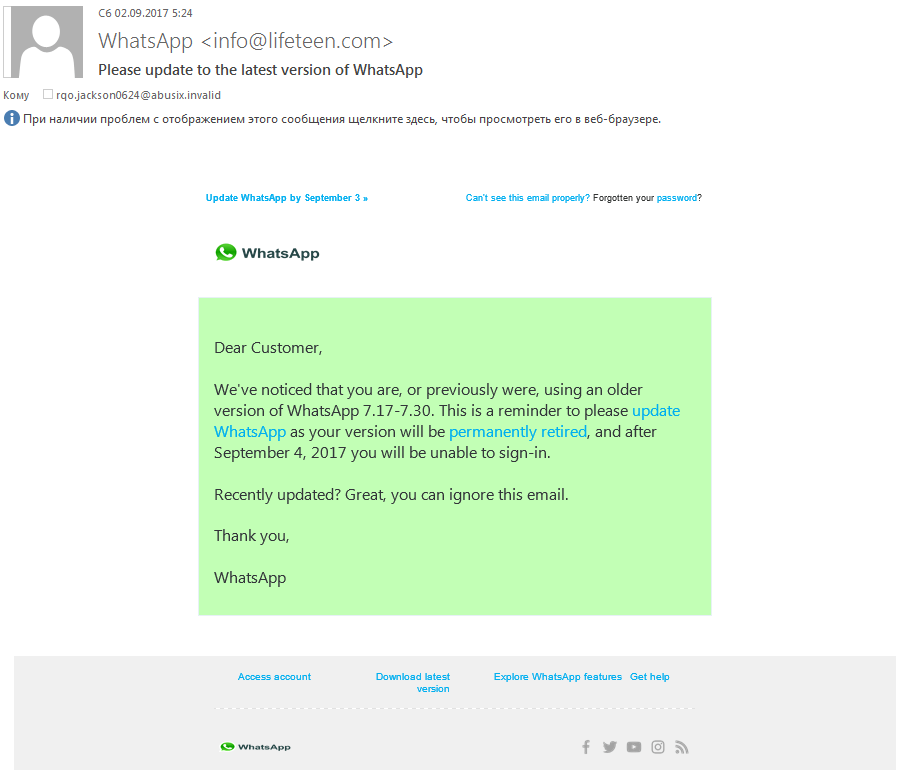
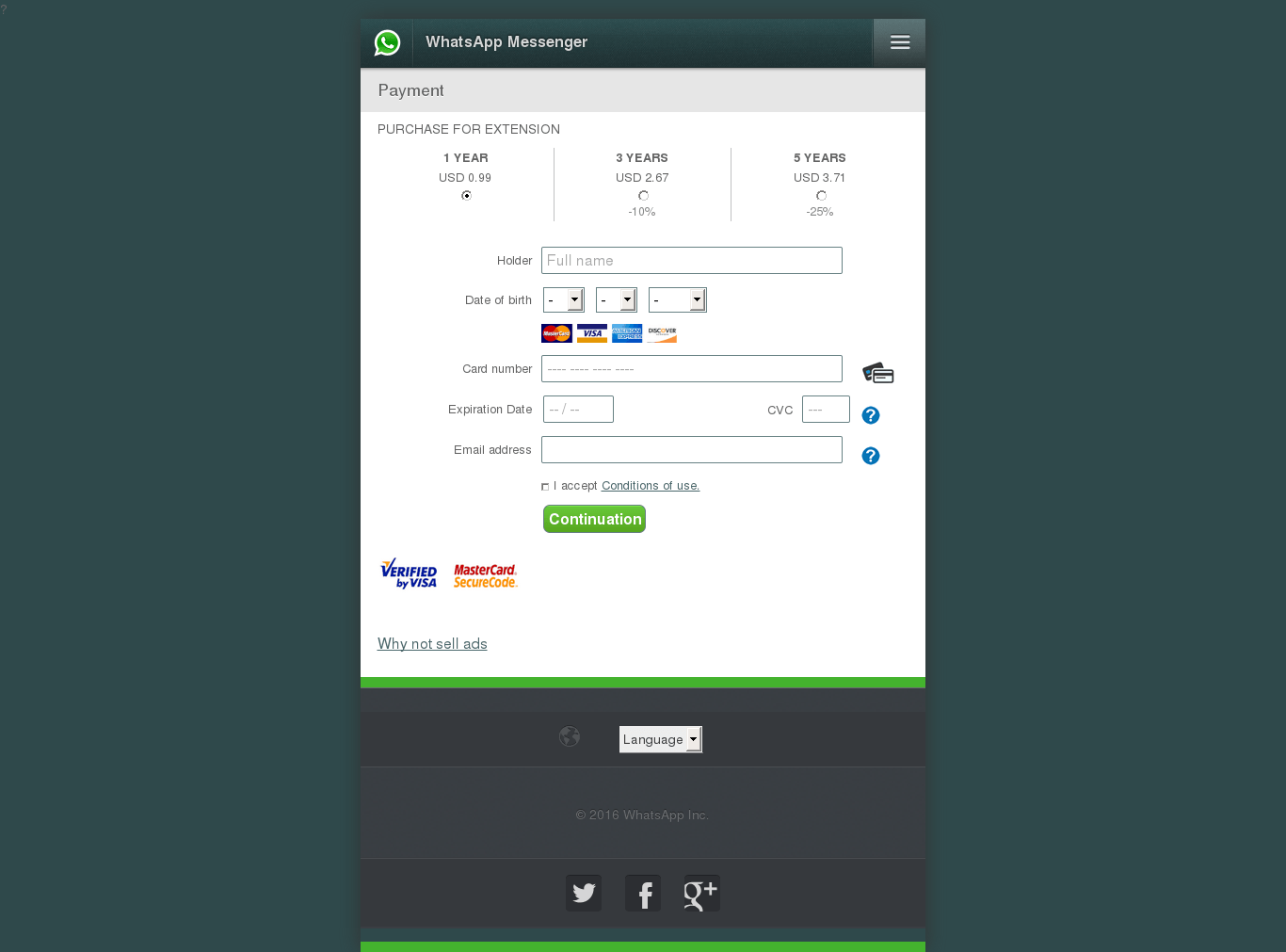
WhatsApp users are also subjected to phishing attacks that hide behind the app brand.
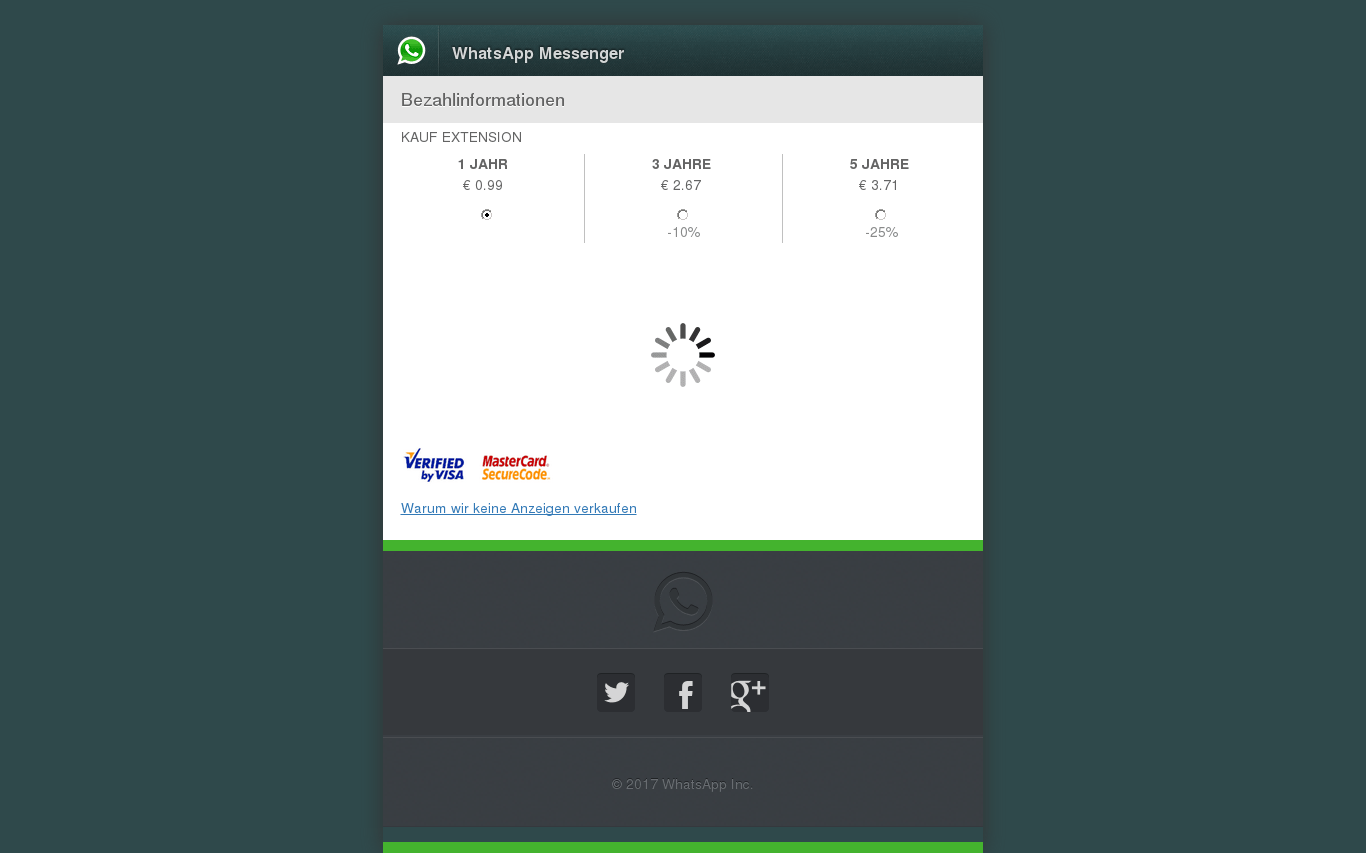
More often than not the scammers try to steal money on the pretext of updating the application or paying for a subscription. At one time WhatsApp really did request a subscription payment, although now it’s free.
Scammers offer a choice of subscription – for one year, three years or five. However, victims will lose much more than the stated amount if they enter their bank card details on such a site.
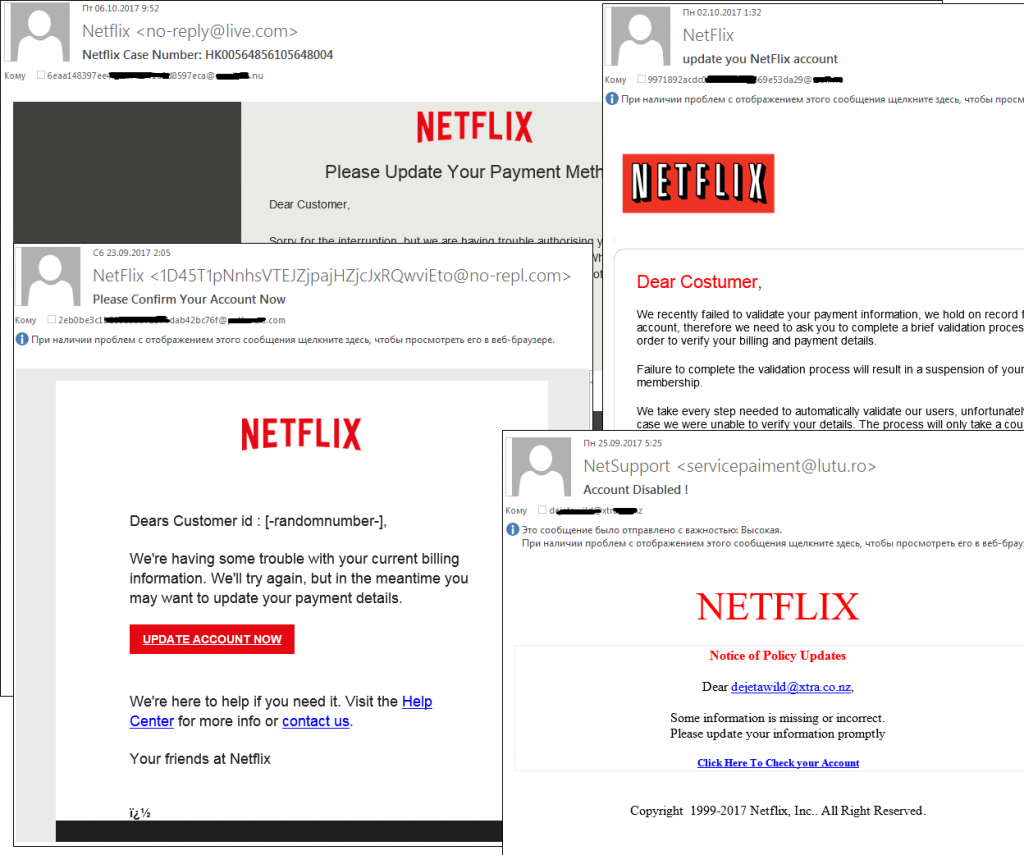
Netflix
Netflix users are another popular target of phishers. The number of attacks on them increased in the third quarter. The criminals usually coax bank card details from users on the pretext of a failed payment or other problems linked to subscription renewal.
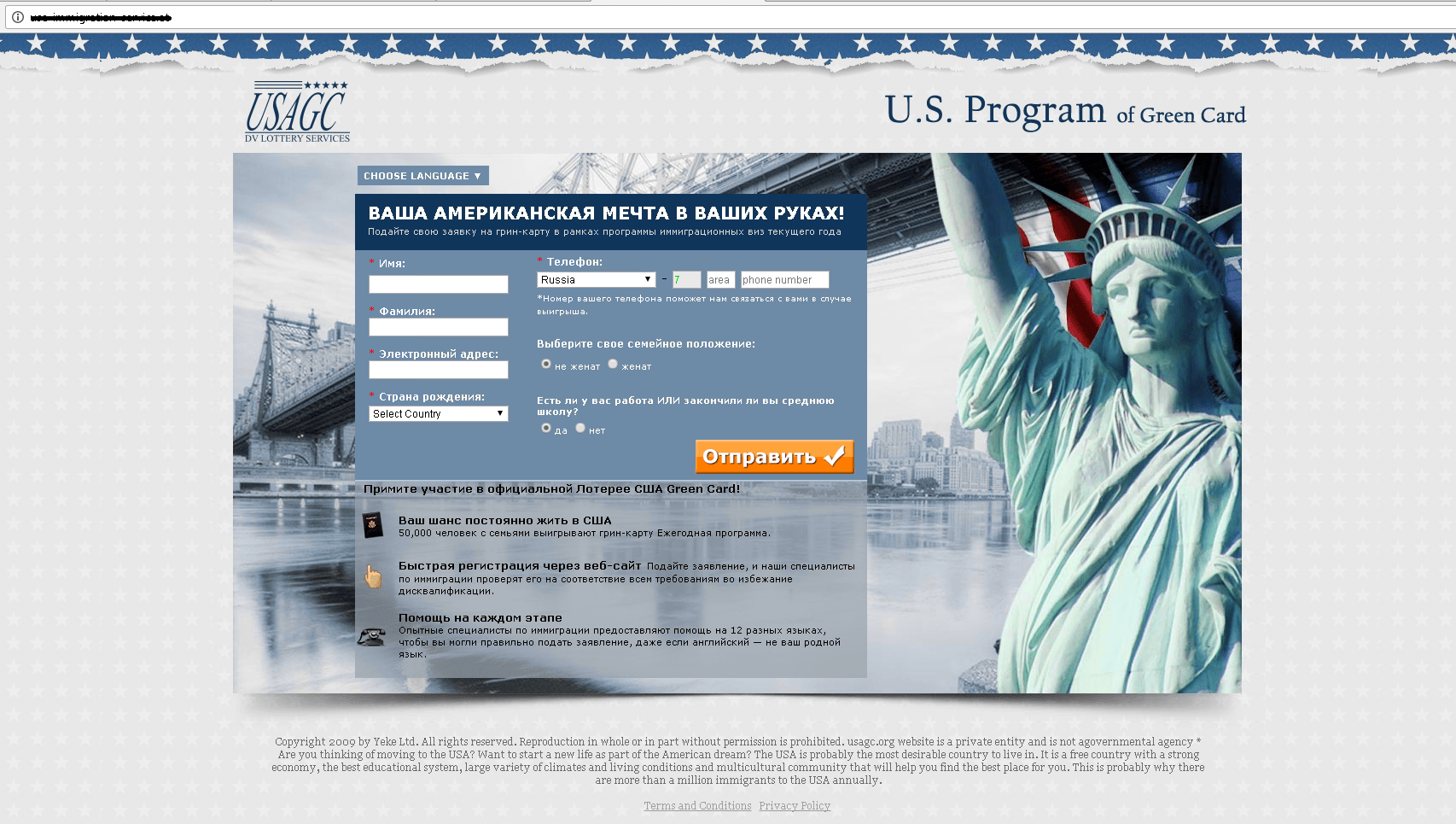
Green Card
On the eve of the Green Card lottery conducted by the US government in October-November of each year, we are seeing a surge in activity by scammers offering help to apply.
After completing the form on the fraudulent site, the user is asked to pay for their application. If the victim enters their bank card details, much more money than the amount indicated on the site can end up being withdrawn from their account.
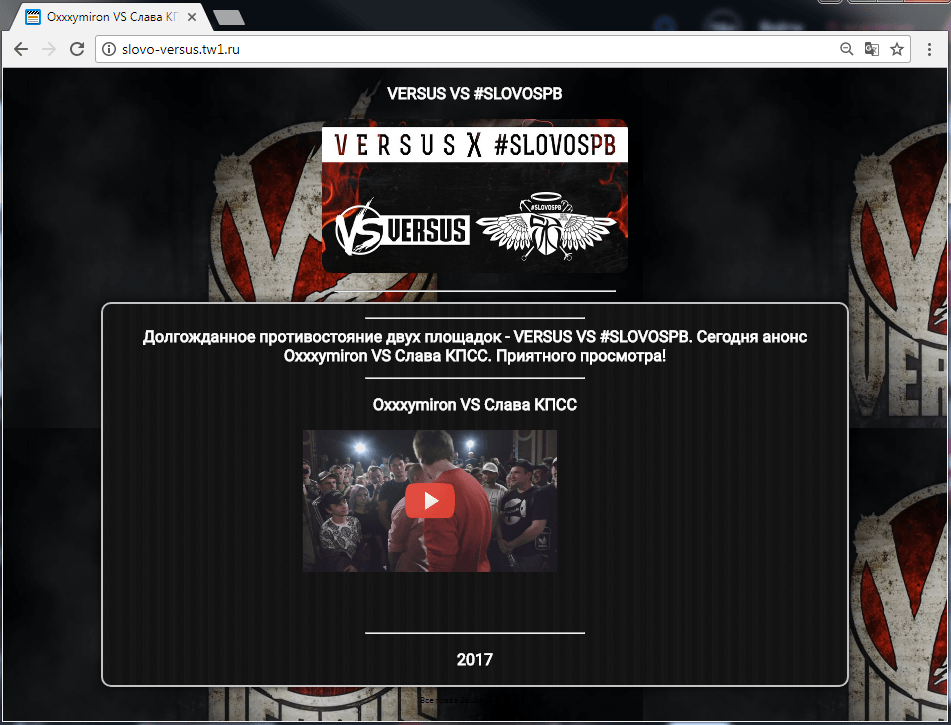
Rap battle
Even niche events can be good cover for phishing activity. On 15 October, a rap battle was held between Russian artist Oxxxymiron and Dizaster, one of the best battle MCs in the US. This followed another battle that took place just a few months earlier between Oxxxymiron and Slava KPSS. Less than 12 hours later a video of the event had gained around 5 million views – and it wasn’t just thematic sites writing about the battle but also a lot of the mainstream Russian media.
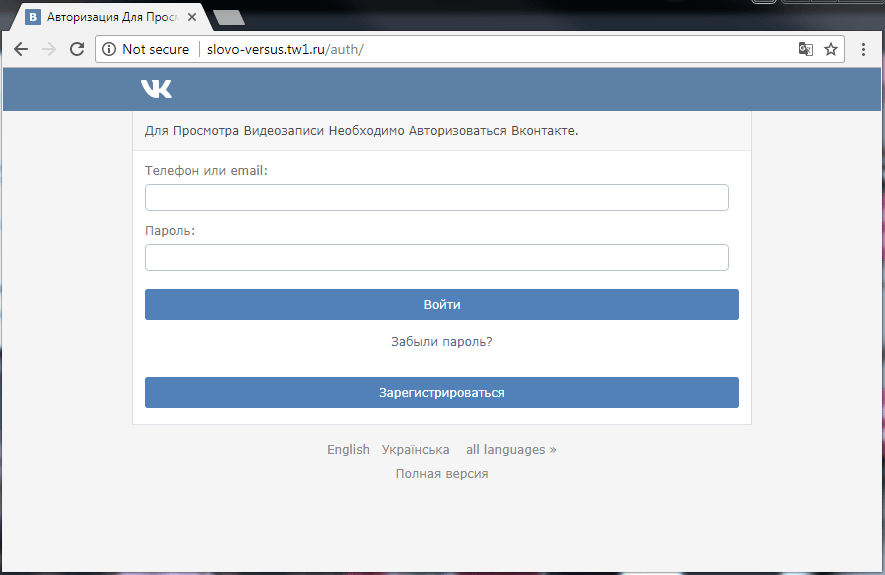
Shortly before the publication of the official video, phishing web pages dedicated to the event began to appear online:
If a user tried to view the video, they were prompted to first sign in to the popular Russian social network VKontakte.
After entering the login and password, the victim was redirected to the official page of the Versus site on the social network, and their personal data went to the scammers.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections by Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies. At the same time, the composition of the top three has remained unchanged for several quarters:
| Organization | % of detected phishing links |
| 7.96 | |
| Microsoft Corporation | 7.79 |
| Yahoo! | 4.79 |
Conclusion
In terms of the average share of spam in global email traffic (58.02%), the third quarter of 2017 was almost identical to the previous reporting period: once again growth was slightly more than one percentage point – 1.05 (and 1.07 p.p. in Q2 2017). As in previous quarters, spammers were quick to react to high-profile events and adapted their fraudulent emails to the news agenda. This quarter they were quickly to use the theme of natural disasters following hurricanes Irma and Harvey, and the earthquake in Mexico. The popular theme of cryptocurrency was also used: trusting victims were offered seminars and ‘help’ with trading that came with profits guaranteed.
Scammers continued to use all available communication channels to spread phishing content, including social networks and instant messengers: in the current quarter, the anti-phishing component prevented more than 59 million attempts to redirect to phishing pages, which is 13 million more than in Q2.
The most common malware family in the third quarter of 2017 was Backdoor.Java.QRat (3.11%), followed by Trojan-Downloader.VBS.Agent (2.95%), and Trojan-Downloader.JS.SLoad (2.94%).
































Spam and phishing in Q3 2017