
Over the previous weekend, social networks were hit with a wave of posts that falsely claimed that major airlines were giving away tickets for free. Users from all over the world became involved in this: they published posts that mentioned Emirates, Air France, Aeroflot, S7 Airline, Eva Air, Turkish Airlines, Air Asia, Air India, and other companies. We cannot rule out that similar posts mentioning other brands may appear in the nearest future as well.
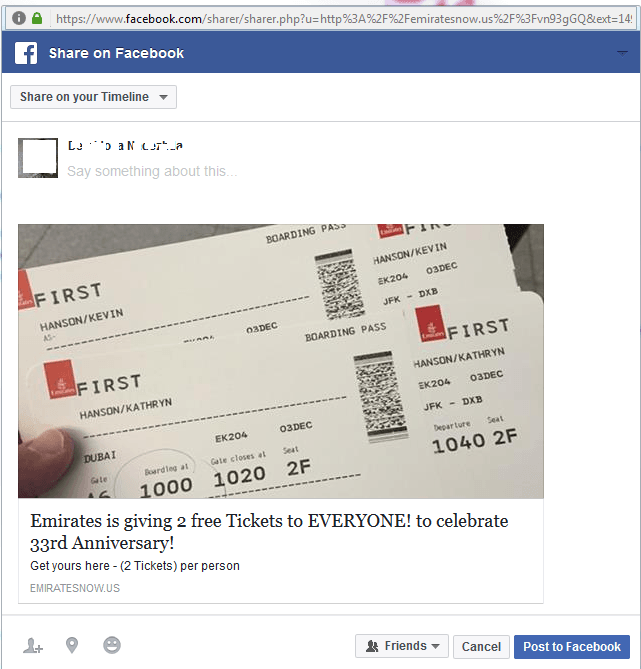
Naturally, there have been no promotions to give away airline tickets. Users were addressed by fraudsters who assumed the names of the largest airlines in order to subscribe their victims to paid mobile services, collect personal data, install malware, and increase traffic to websites with advertisements and dubious content. To do this, fraudsters have been registering a multitude of domains, where they host content on behalf of well-known brands. At the mentioned resources, users are congratulated on winning two airline tickets. Then, they’re asked to perform a series of actions to receive the gift. As a result, the victim ends up on another website that belongs to fraudsters, which monetizes their “work” and spreads information about the nonexistent campaign on a social network.
An example of a social-network post with a link to a fraudulent website
This is by no means the first case where users themselves have started spreading fraudulent content on social networks. We have previously about a fake petition in defense of Suarez, which was distributed by Facebook users, fake donations, and pornware. All of the incidents have one thing in common: the threats are distributed over social networks, which users themselves often participate in.
The attack model
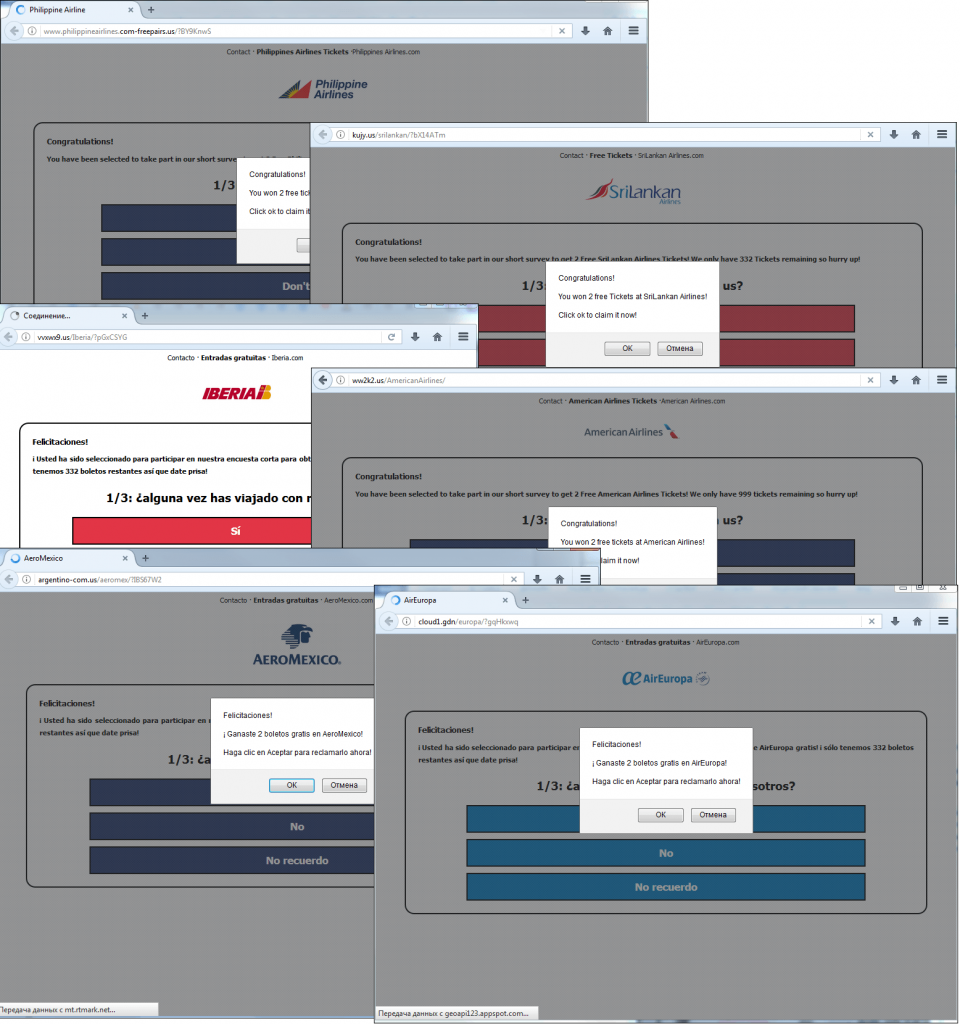
Let us return to the most recent case and examine it a bit closer. By following the link from a social network news feed, a user navigates to a fraudulent website. We have found a series of domains that belong to fraudsters: deltagiveaway.com, vvxwx9.us, aeroflot-com.us, aeroflot-ticket.us, qq3mz9.us, emiratesnow.us, emiratesgo.us, com-beforeitsends.us, emirates.iwelltrip.us, and many others.
Some examples of fraudulent websites that make use of famous airline brands
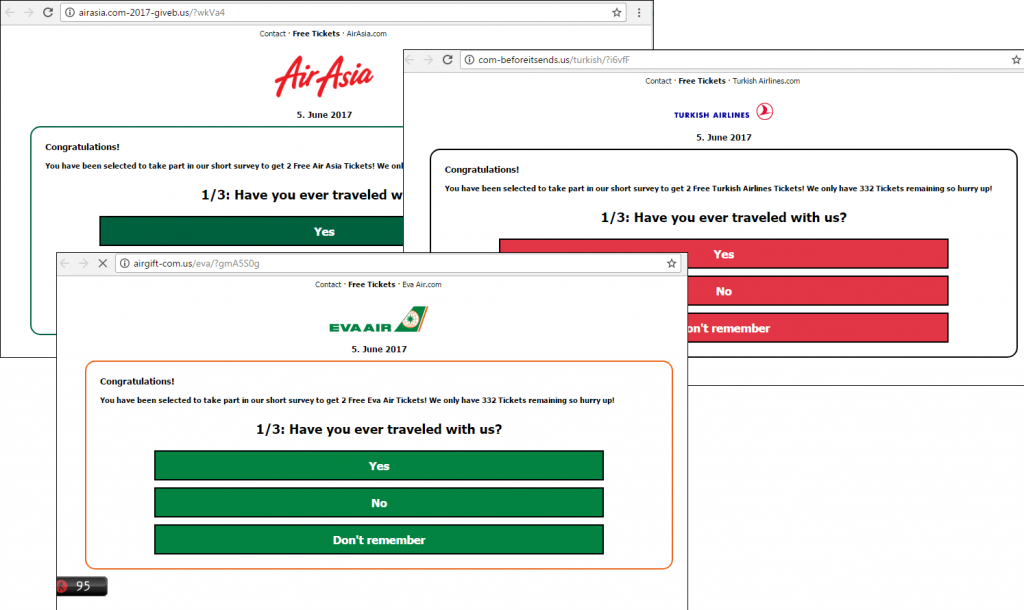
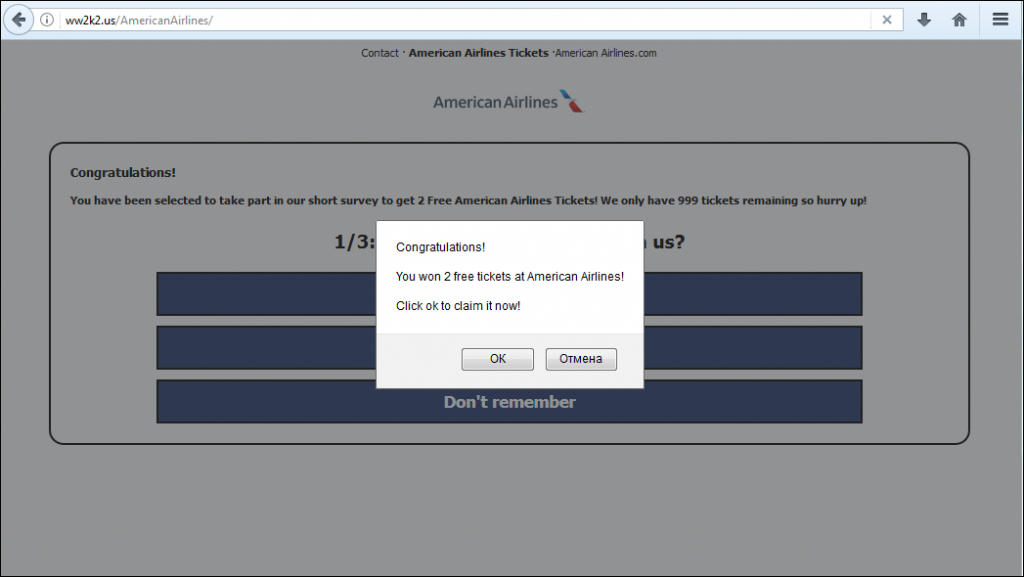
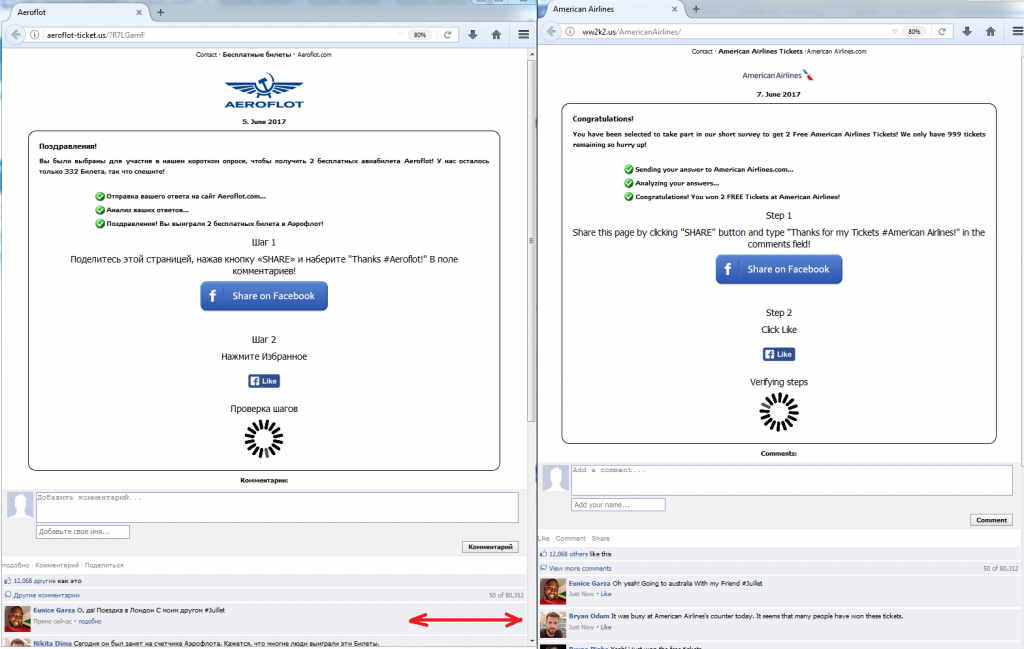
Since the fraudulent schemes only varied by logo, language, and color scheme, depending on the brand, let’s take one website out of the many and discuss it. The website that claims to belong to American Airlines contains information about a promotional giveaway of two tickets to respondents who must answer three questions.
An example of a fraudulent website that uses American Airlines branding.
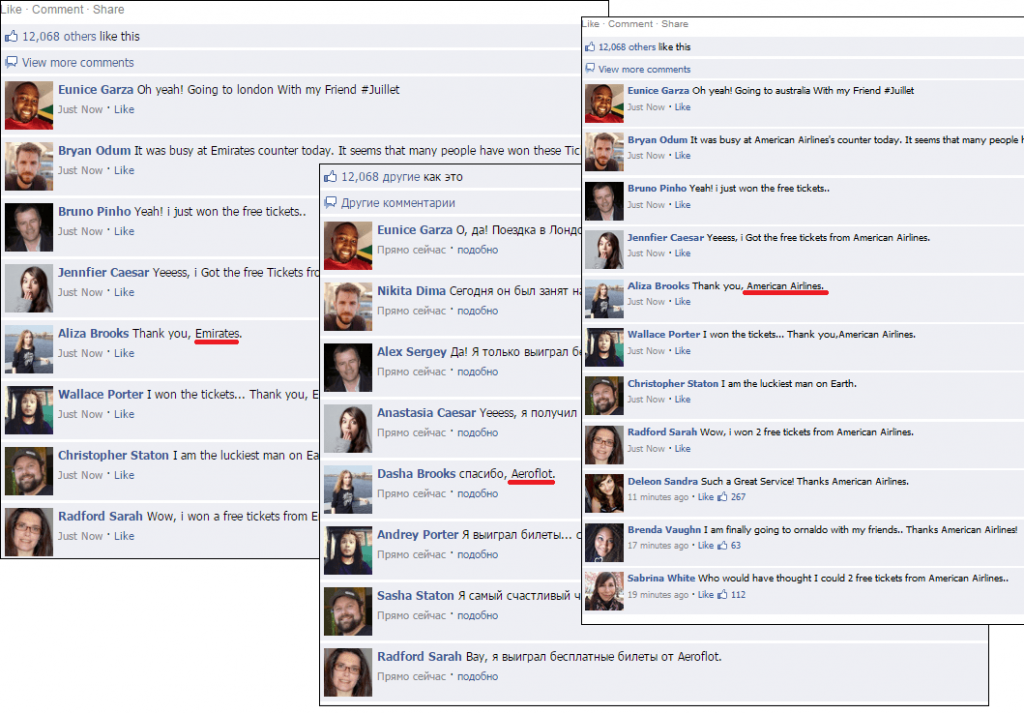
After completing the survey, the victim is asked to take two more steps. First, the victim is asked to post the promotional information on his or her page on a social network and thank the airline in the comment. Secondly, the victim has to click the “Like” button. It should be noted that the web page shows what appear to be Facebook comments from users who have already won tickets. An investigation showed that the comments are actually fake. We can even leave our own comment, but it will disappear after the page is refreshed. All of this is directed at coaxing a victim into believing that the page is legitimate.
We would like to note that most comments are posted in various languages by the same people, and the messages are similar in content and most likely are translated using machine translation.
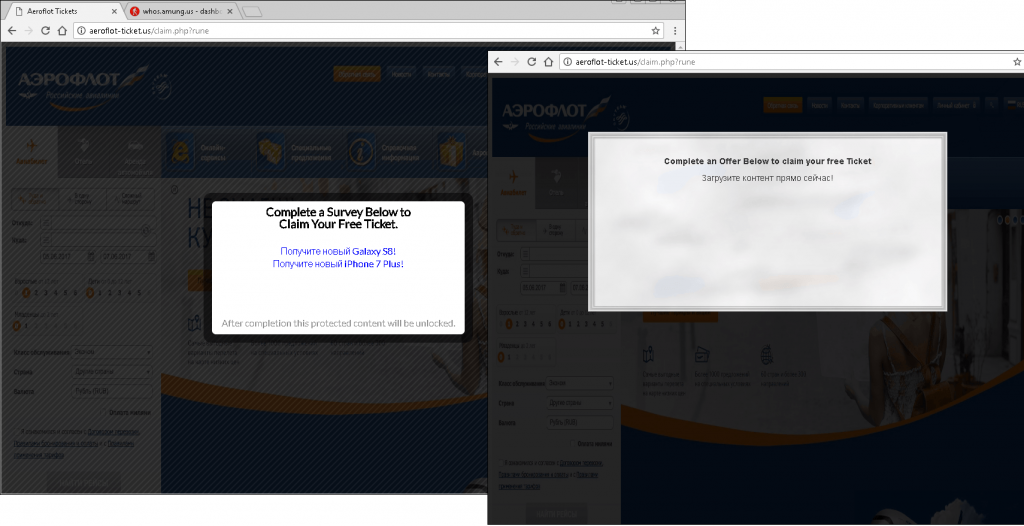
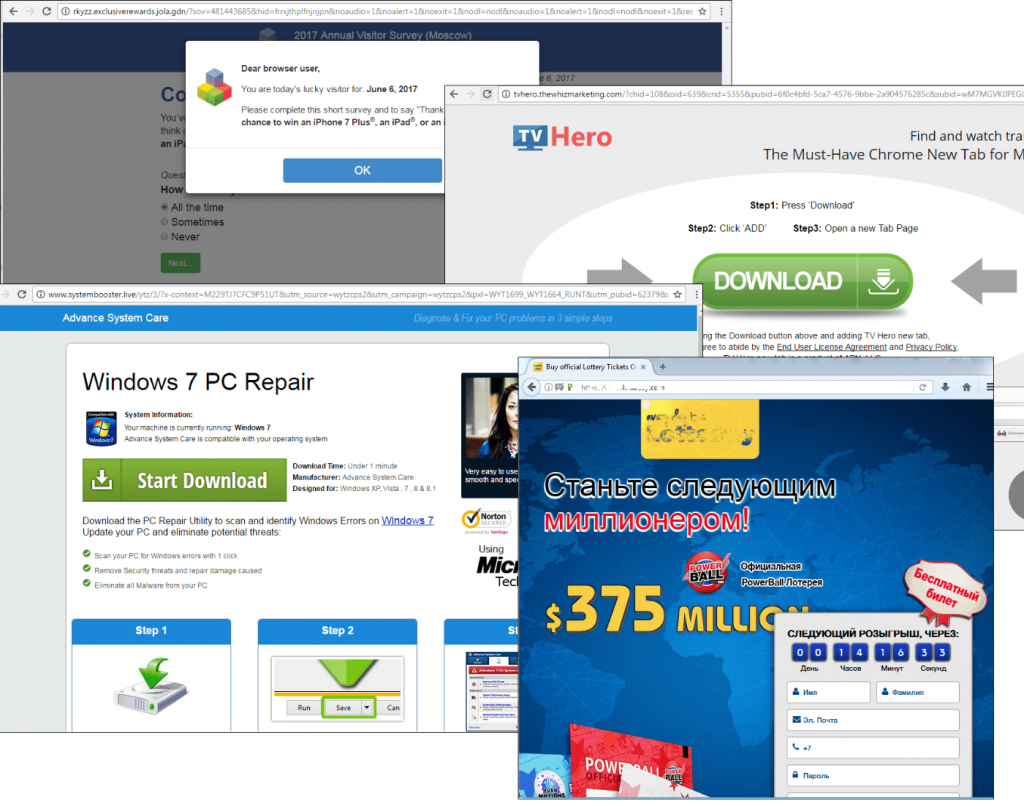
After performing all of the necessary actions, the website redirects the user to various web pages by using the geolocation feature. In some cases, we were redirected to the websites shown below.
Each time all of the same aforementioned actions are performed and the same survey is completed, the website does something different and may redirect users to various web pages. We have found websites with a variety of dubious content, including lotteries, advertisements, new surveys with giveaways, links to suspicious files that can be downloaded, and so on.
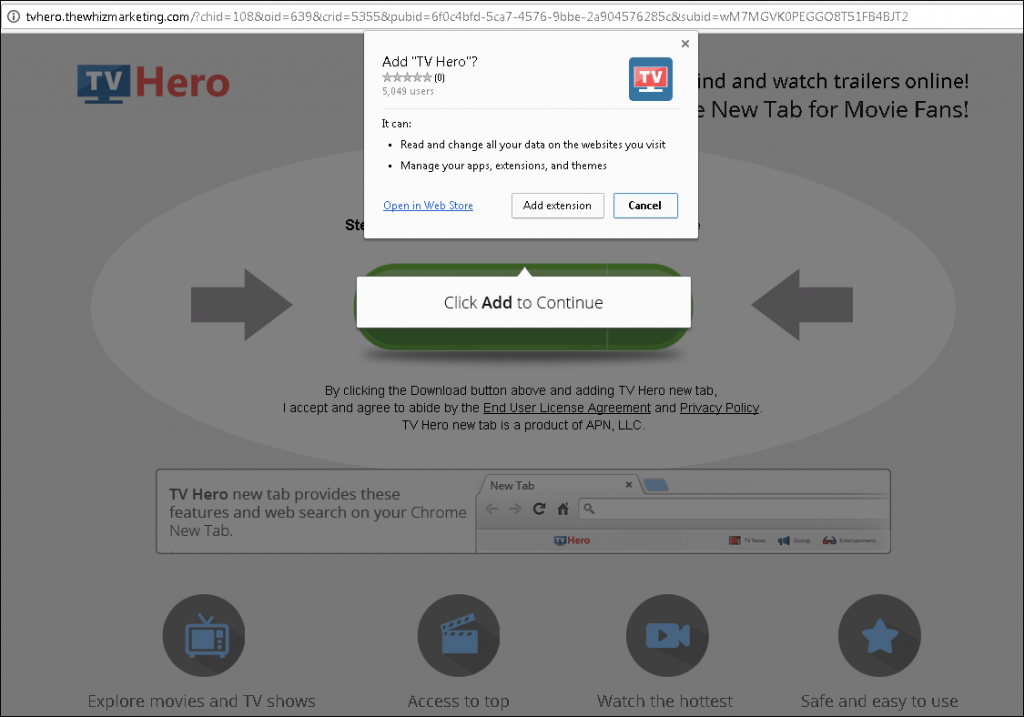
Among other things, some websites suggests users download a certain useful file and at the same time urge them to install a potentially dangerous extension for a browser. The extension obtains permission to read all of the data in a browser, potentially allowing fraudsters to get a hold of passwords, logins, credit-card data, and other confidential information entered by the user. Aside from that, later on, the extension may continue spreading links that redirect users to the extension itself on Facebook but on behalf of the user and among his or her friends. This is exactly the threat that was carried out by an attack that we discussed previously.
At the moment of publication, this indicated extension alone had been installed on the systems of over 5,000 users, according to the statistics of the web apps store.
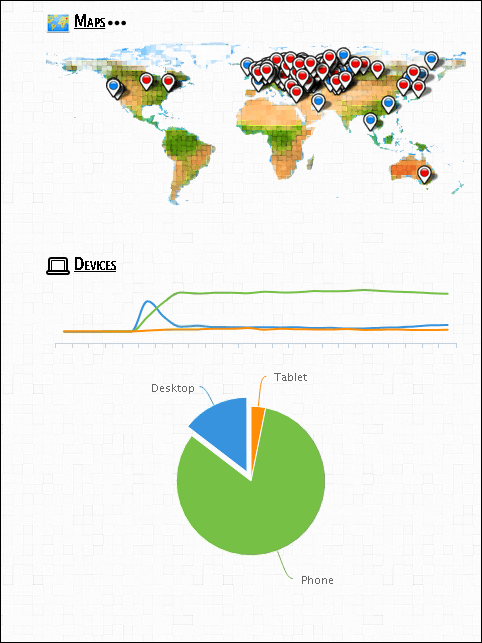
The number of victims and their location
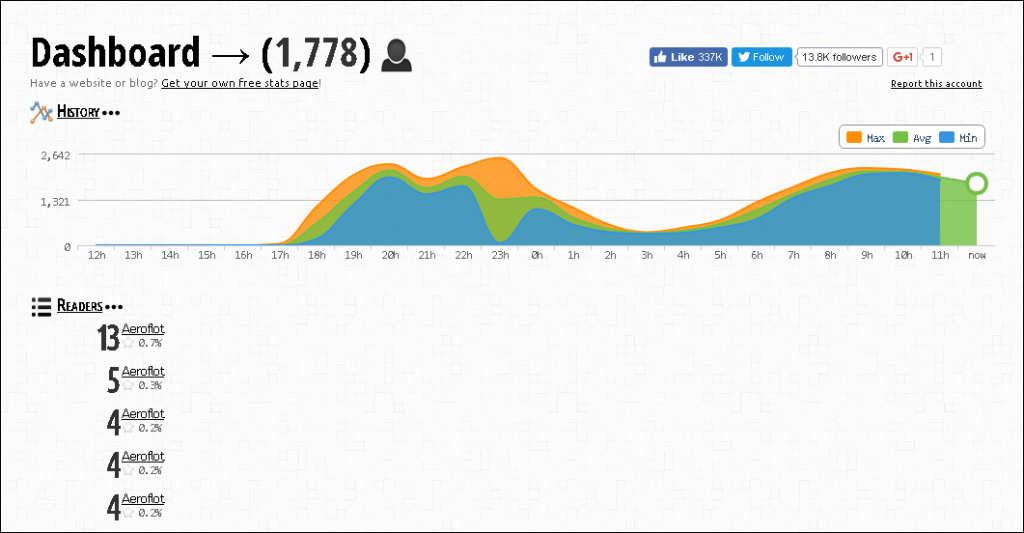
Most resources that utilize the fraudulent scheme contain links to external services that collect statistics for website traffic. These data show that the attack was widely distributed and was mostly directed at smartphone users. For example, here are some impressive statistics for only two of all the domains that we discovered.
Statistics for the aeroflot-ticket.us website
Statistics for the aeroflot-ticket.us website
Statistics for the emirateswow.us website
Unfortunately, numerous users took the bait of the fraudsters. These users tried their luck and did not pay attention to a multitude of signs that are typical for a scam, which resulted in spreading potentially dangerous content among friends over a social network.
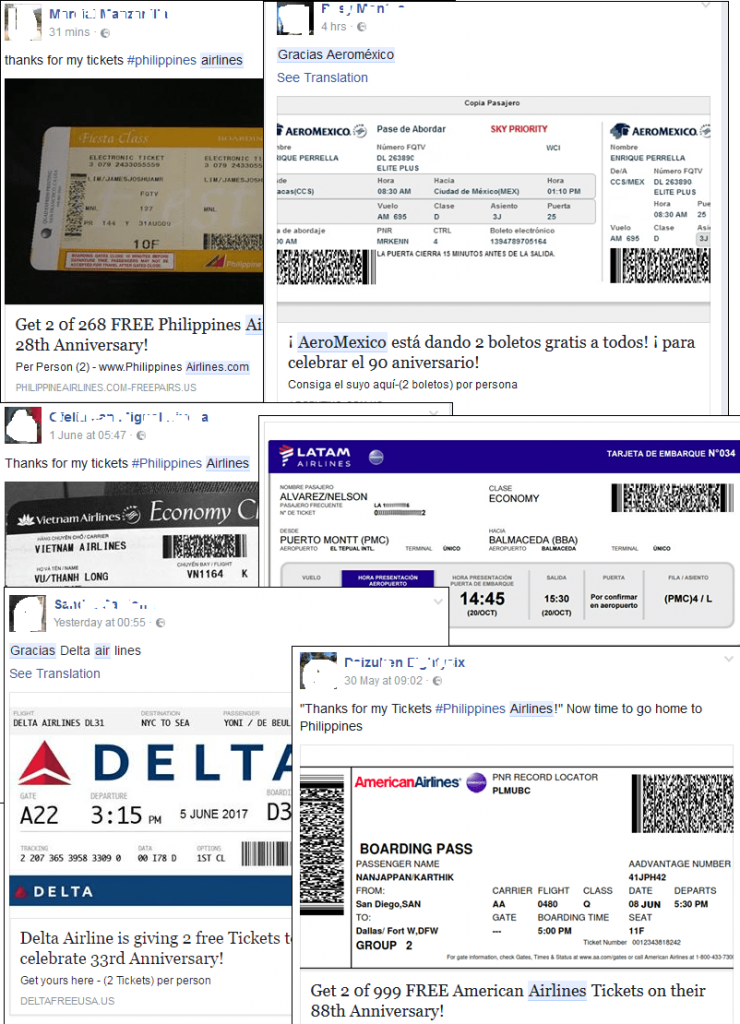
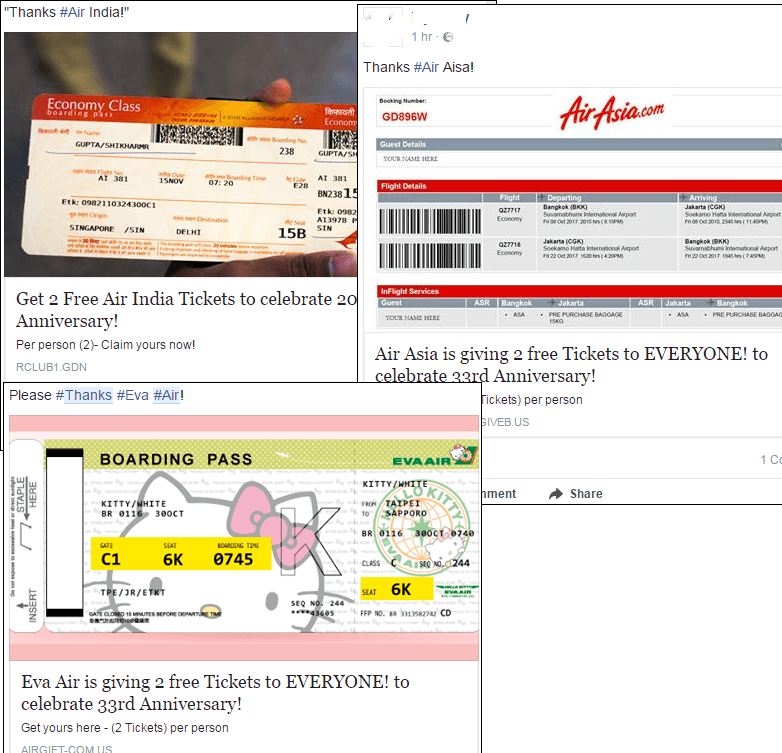
Some examples of published posts with links to fraudulent websites
Thus, fraudulent web resources and a plethora of their counterparts across the Internet gained huge popularity in a matter of hours.
The possibilities of social networks are endless when it comes to spreading information across the globe. These fraudsters only confirm this fact.
Some examples of published posts with links to fraudulent websites
Finally, here are a few pieces of advice.
- You should be sensibly skeptical about similar “promotions”. Before navigating to suspicious links and entering your personal data on a web resource, you should contact a representative of the company that is supposedly running the promotion and confirm the information.
- A scrupulous examination of a web resource’s address will help identify fraud. It may be a good idea to verify whether the domain belongs to the company indicated on the website or not. Services that provide whois data about domains may prove helpful in that endeavor.
- Be responsible when posting content from your account on a social network. In order to avoid becoming involved in a fraudulent scheme, do not spread information with questionable authenticity.
- Do not install suspicious browser extensions. Upon detection of an installed extension that seems suspicious or whose purpose you do not remember, delete the extension immediately in the settings section of your browser and change the passwords of websites that you visit, especially those dealing with online banking.
- Use security solutions that protect users from phishing, such as Internet Security-level solutions and higher. They will block any attempts to navigate your browser to fraudulent websites.
Two Tickets as Bait






















Lance
This is an old scam which had been run last year for a UK based airline. The same method was used to target a number of other major US based companies as well as well as Middle Eastern airlines. The script has some fake Facebook profiles to bait people and when people complete post and share then it replicates as more people get tricked. The main thing they seem to do is harvest facebook profiles. What they do with the data remains to be seen. This issue was raised with facebook security late last year on a number of occasions. The sharing capability also tried twitter but didnt get the same level of response,
stg
Question for the author:
In the diagram ‘Statistics for the aeroflot-ticket.us website’ the facebook button shows 337K likes. Does that mean that 337,000 individuals completed this process, getting as far as hitting the like button after completing the survey?
Thanks
Rita
one way pages get likes and replies is to post something innocent asking for likes. shares, and comments. That post then gets changed into something like the scam for the tickets. Thousands of people may have reacted to the post that has a sick child, free give away or prayer and have no idea that the subject would be changed to something like the hoax airline ticket giveaway