
When we talk about phishing, top of mind are fake banking sites, payment systems, as well as mail and other globally popular services. However, cybercriminals have their fingers in far more pies than that. Unobviously, perhaps, students and university faculties are also in the line of fire. The reason is the research they carry out and the potentially valuable results.
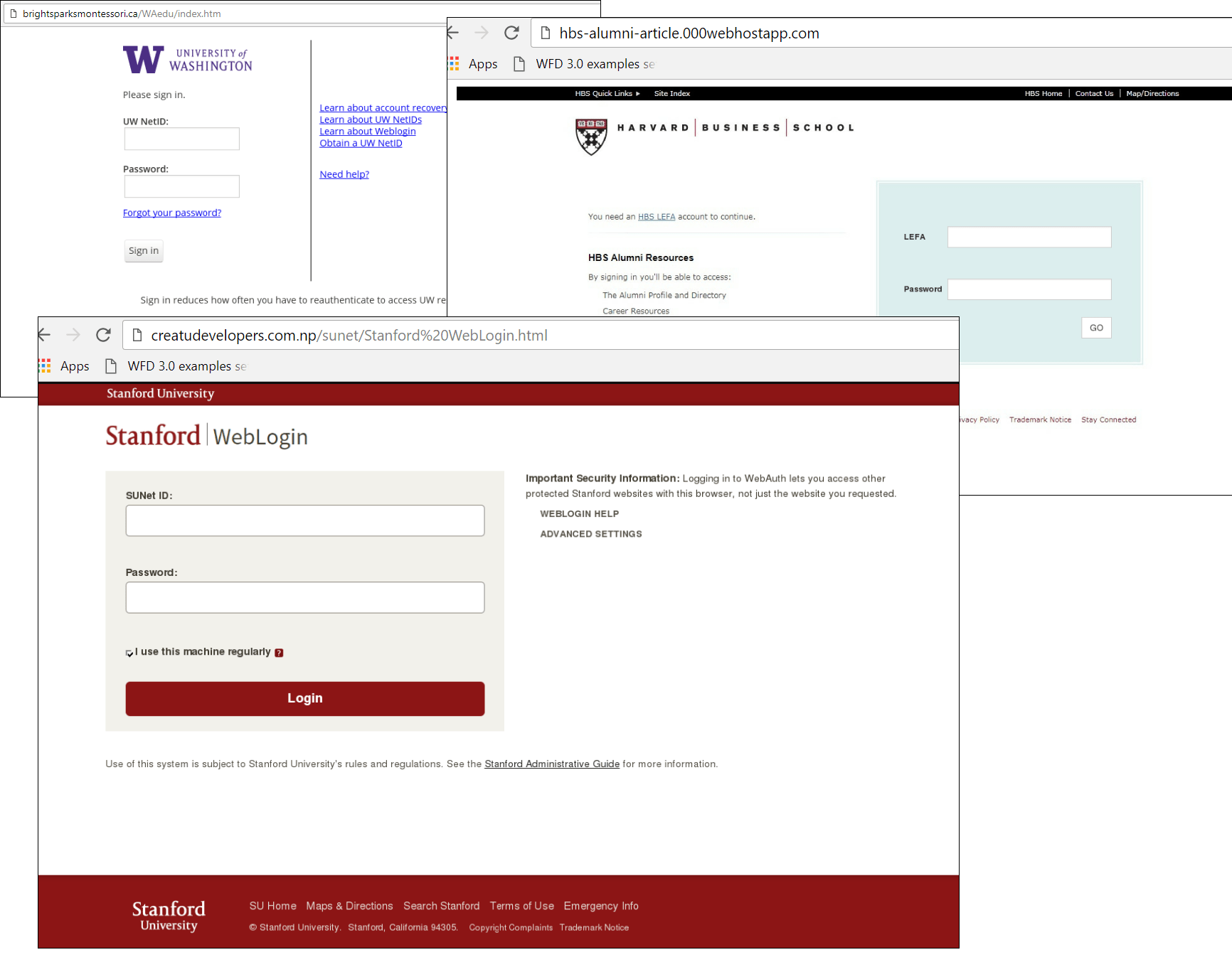
Examples of phishing pages mimicking the login pages of the University of Washington, Harvard Business School, and Stanford University websites
Over the past year, we’ve registered phishing attacks against 131 universities in 16 countries. More than half (83 universities) are located in the US, followed by Britain (21), and Australia and Canada (7 each). Several well-known universities in Finland, Colombia, Hong Kong, India, Israel, the Netherlands, New Zealand, Poland, South Africa, Sweden, Switzerland, and the UAE have also experienced at least one phishing attack in the past year. The most popular universities for fraudsters so far this year are: University of Washington (11.6% of attacks), Cornell University (6.8%), University of Iowa (5.1%).
Although universities are aware of the need to protect their resources, fraudsters exploit the traditional weakest link: user inattentiveness. Depending on the level of access (lecturer, student, research associate), personal accounts on the university site can provide access to both general information as well as paid services and research results. Moreover, a lecturer’s account, for example, can provide attackers with information about salary, schedule, etc. All this can be used for identity theft or a targeted attack.

Cornell NetID is a unique electronic identifier used in combination with a password to provide access to non-public resources and university information
Phishing pages typically differ from the original only by the web address. However, despite the browser warning and, as in the case of the Cornell University fake page, the prompt to check the address bar (copied by the attackers from the original site), users often fail to spot the difference.

Besides login credentials, phishing pages can collect other information for bypassing anti-fraud systems
While analyzing the scripts of one of the phishing pages, we noticed that alongside user names and passwords, fraudsters collect information about IP addresses and the victim’s location. Cybercriminals can use this data to circumvent anti-fraud systems by masquerading as account holders.
How to stay protected
An old, but still important tip is to check the address bar of the site on which confidential data is about to be entered. But since this method relies solely on the human factor, the main recommendation for educational institutions is to use two-factor authentication, and for users — a software solution with anti-phishing capability.
























Phishing for knowledge