
Spam: features of the quarter
“Noising” domains
We have already analyzed the situation with regard to the considerable increase in the number of new domain zones as well as mass generation of spammer domains in these zones, specifically those designed to send out illegitimate mass mailings. The further analysis of spam mailings shows that spammers rely not only on a huge number of new domains which they can change even within one thematic mass mailing, but also on the ways they are implemented in the text. For example, in Q1 we registered various cases of “noising” domains in links used to go to spam resources, as well as cases of code obfuscation in the HTML structure of the messages in the mass mailing.
In many mass mailing, spammers used IP addresses of sites, instead of domain names, in links to advertising resources. However they provided modified rather than direct IP addresses, representing them using the octal or hexadecimal numerical system, adding an arbitrary number of zeros to the beginning of the address. This did not change the IP address, but increased the number of possible variants of its representation (variations within one mass mailing); which, as spammers hoped, would help deceive the spam filter. Such alternative methods of representing IP addresses were used by spammers both in direct links and in “noised” redirects.
Spammers also used noised domains. For example, they represented a domain name using both upper and lower case characters (NEEDHosT.niNjA), as well as using several different codes in the HTML structure of the message. They attempted to hide their domains by changing one of the characters in the name of the domain zone for the same from the other code or similar to it. So, for example, it might look like this – domainname.com , domainname.cⓞ
Spammers often applied several methods of noising in one email: they used both the alternative representation of the IP address or domain distortion, as well as the traditional use of meaningless “junk” text in the body of the message, in order to completely conceal the spam theme of the message.
World events in “Nigerian” spam
In the second quarter of 2015, “Nigerian” letters exploited the themes of the earthquake in Nepal, the presidential election in Nigeria and the Olympics in Rio de Janeiro. Tragic events widely covered in the world media are usually exploited by fraudsters to trick users, and their stories hardly change.
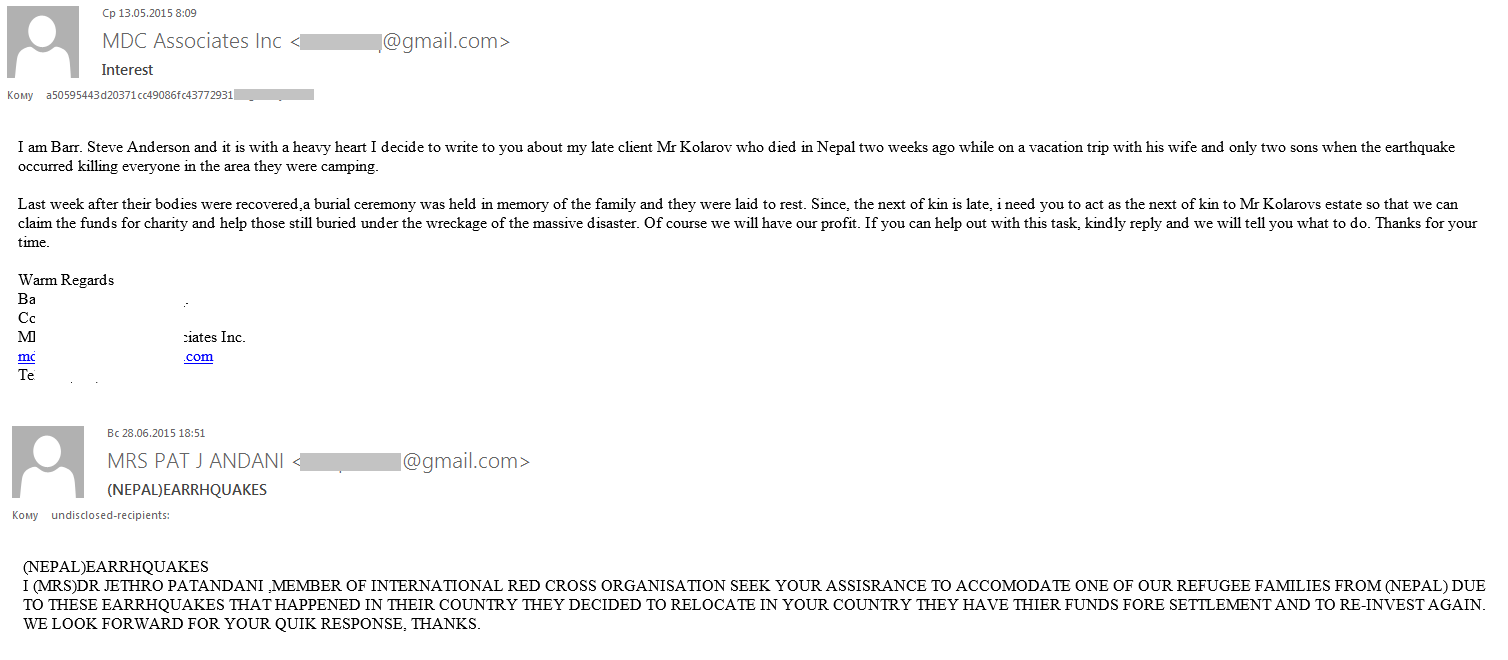
In the email written on behalf of a lawyer whose client died in Nepal, the scammers asked the recipient to play the role of the victim’s relative and help in receiving their inheritance, in return for financial remuneration. In the other mass mailings, the fraudsters distributed emails in the name of various organizations asking to help the earthquake victims. For example, “a representative of the Red Cross” asked the recipient to assist in accommodating a family of refugees who had decided to move to another country and invest their funds there.
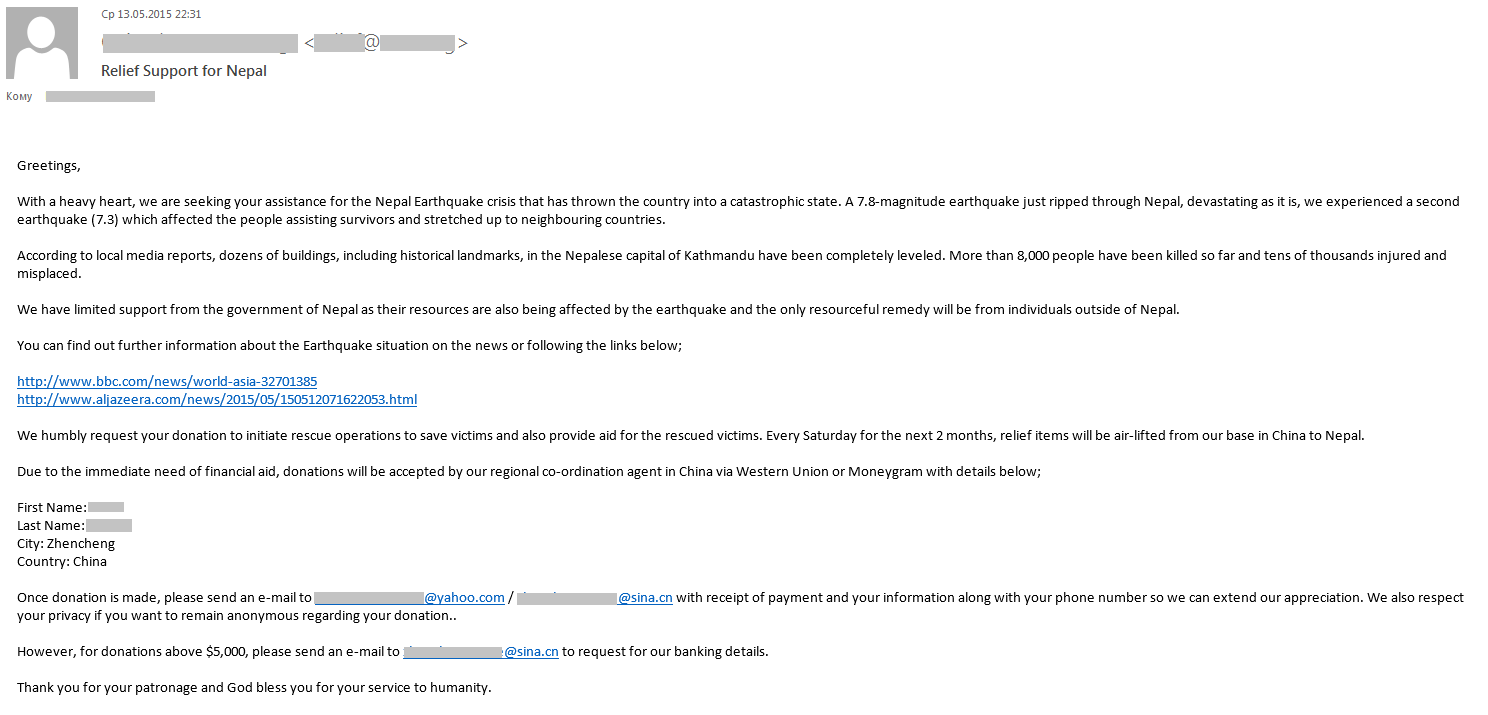
Generally, the addresses of those who send “Nigerian” letters were registered on free e-mail services, even if the author of the email was a representative of an organization, as in the above case. However, some tricky fraudsters tried to make the name and the address of the sender look more legitimate. They sent out fake messages asking the recipients to make a voluntary donation to help the victims of the earthquake in Nepal.
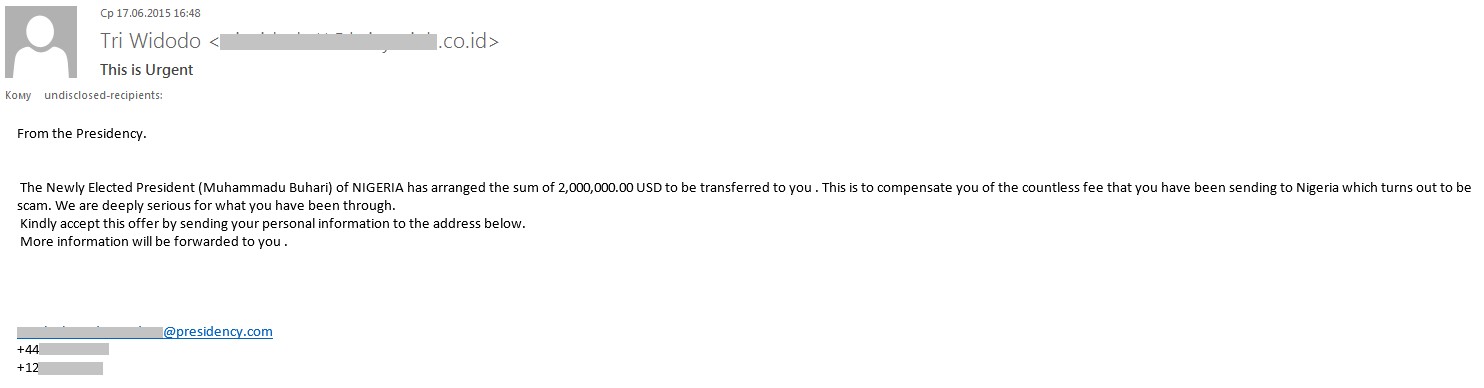
“Nigerians” could not let political events go unnoticed. In one of the mass mailings, the fraudsters tried to lure the recipient with the sum of $2 million, which the newly elected President of Nigeria was allegedly ready to send to the user as compensation for the fraud committed by the citizens of his country.
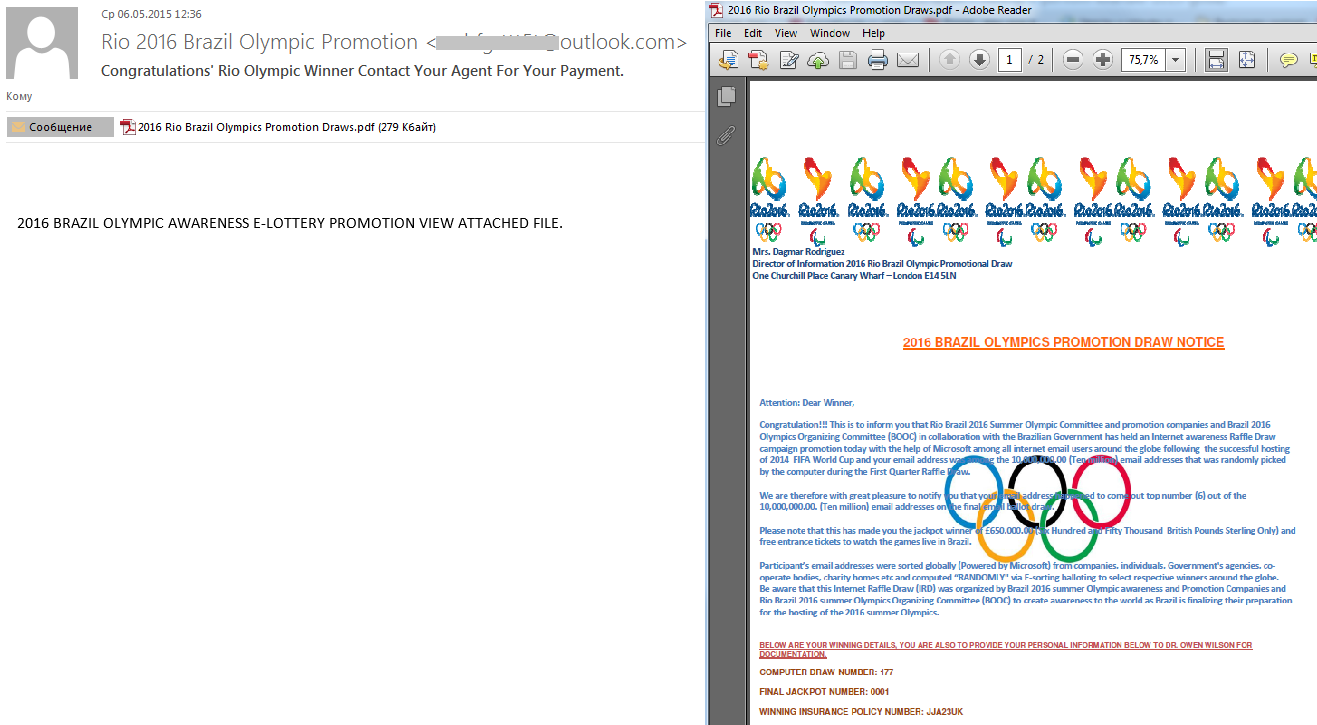
The next Olympic Games in Brazil will not be held until 2016, but we are already registering fraudulent notifications of lottery wins dedicated to this popular sporting event. Interestingly, a large number of emails of this type was sent out in the run-up to the World Cup, while the Olympics were not mentioned. The content of the messages is standard: the lottery was held by the official organization, the recipient’s address was randomly selected out of millions of email addresses, to receive the win it is necessary to respond to the email and provide the specified personal information.
Noticeably, emails containing a short text in the body of the message, with detailed information provided in an attached PDF or DOC file, are gaining popularity with spammers. This may be because an email with a short text has more chance of passing through a spam filter as legitimate. Emails with attached files are especially dangerous because a user is likely to open the attachment to learn about the the content, which can result in malware infection.
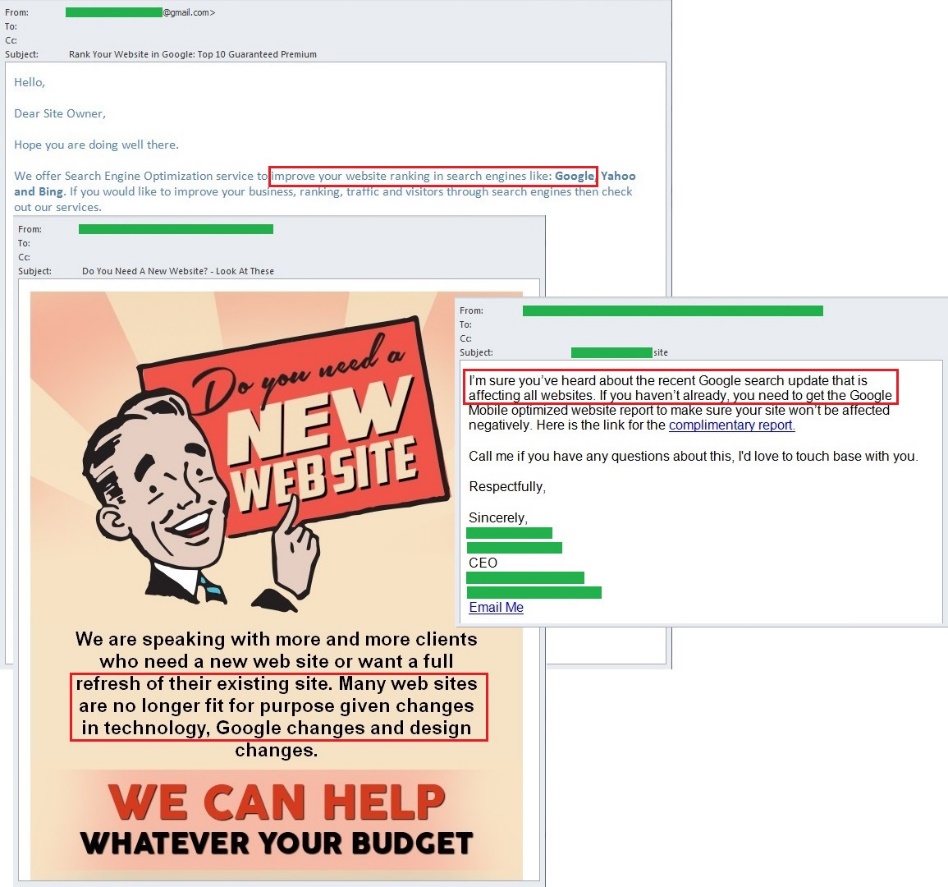
The Google search algorithm update
Yet another event exploited in spam in the second quarter of 2015 was the release of regular update to the Google search algorithm. This changed the mobile web search results so that the sites adapted for mobile phones were displayed on top positions.
This news resulted in a significant increase in the amount of spam relating to SEO (search engine optimization) and promotion of sites. Spammers sent out offers advertising the creation of sites of any complexity and purpose, as well as services to attract new customers. They emphasized the necessity to bring the site up-to-date by using the latest features of a popular search engine. Those site owners who still had doubts were threatened with ending up as the last pages in Google search results and the resulting loss of potential customers.
Statistics
Proportion of spam in email traffic
Proportion of spam in email traffic, January – June 2015
The worldwide decline in the share of spam in email traffic since the beginning of the year has almost stopped. In the second quarter of 2015 it stabilized, fluctuating between 53.5% in April and 53.23% in June.
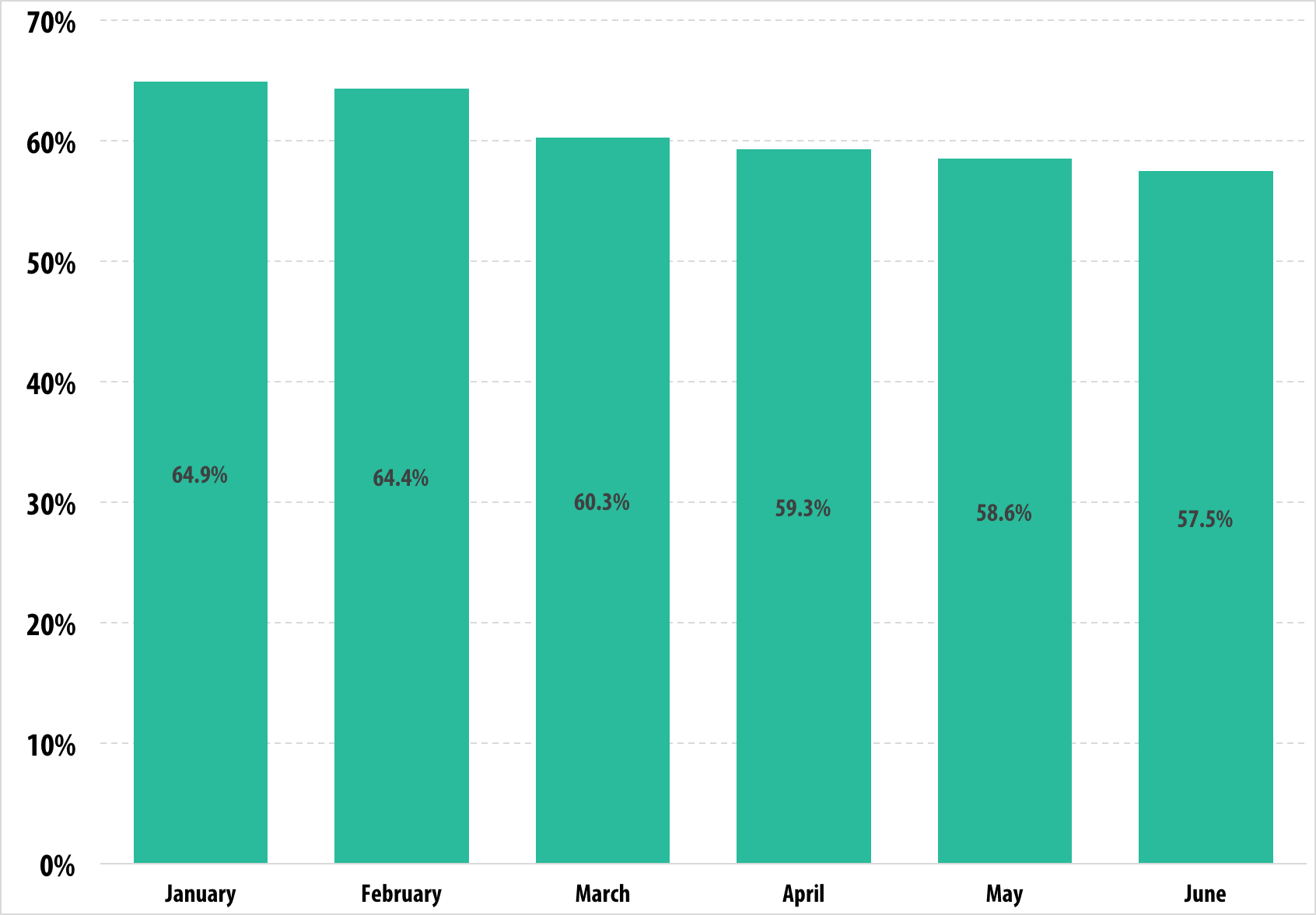
Proportion of spam in email traffic in Russia, January – June 2015
The situation with spam in Russia is almost the same as for worldwide email traffic. During the second quarter, the share of spam traffic decreased by approximately 1 percentage point per month. Thus, the maximum quantity of spam emails in Q2 was sent in April (59.32%), while the minimum amount was distributed in June (57.47%)
Spam sources by country
Countries that were sources of spam, Q2 2015
In the second quarter of 2015 the USA (14.59%) and Russia (7.82%) remained the biggest sources of spam. China came third with 7.14% of the world’s spam, compared to 3.23% in the previous quarter. It was followed by Vietnam (5.04% compared to 4.82% in Q1), Germany (4.13% compared to 4.39% in Q1) and Ukraine (3.90% compared to 5.56% in Q1).
Spam email size
Spam email size distribution, Q1 2015 and Q2 2015
The distribution of spam emails by size saw little change from the previous quarter. The leaders were very small emails of up to 2 KB (65.38%), although the proportion of such emails has gradually decreased (it accounted for 73.99% in Q1). The share of emails sized 20-50 KB grew by 4.81 percentage points and reached 8.80%, while the percentage of emails in the size range of 2 KB-5 KB (17.16%), 5-10 KB (3.32%) and 10-20 KB (2.94%) increased slightly – by about 1 percentage point each.
Malicious email attachments
Top 10 malicious programs sent by email, Q2 2015
The notorious Trojan-Spy.HTML.Fraud.gen topped the rating. As we have written before, this program is a fake HTML page which is sent via email, imitating an important notification from a large commercial bank, an online store, a software developer, etc. This threat appears as an HTML phishing website where a user has to enter his personal data which is then forwarded to cybercriminals.
Second and third positions are occupied by Trojan-Downloader.HTML.Agent.aax and Trojan-Downloader.HTML.Meta.as. Both are HTML pages which, when opened by users, redirect them to a rigged site. There, a victim is usually faced with a phishing page or is offered a download – Binbot, a binary option trading bot. The two malicious programs spread via email attachments and the only difference between them is the link which redirects users to rigged sites.
Trojan.Win32.Fsysna.brtr rounds off the Top3. It is just a common spam bot which redirects spam from the command center to the mail server on behalf of the infected machine.
Fourth is Trojan-Banker.Win32.ChePro.ink. This downloader, which was as low as sixth position in last year’s ranking, is a CPL applet (a Control Panel component) that downloads Trojans designed to steal confidential financial information. Most malicious programs of this type are aimed at Brazilian and Portuguese banks.
It is followed by Trojan-PSW.Win32.Fareit.auqm. Fareit Trojans steal browser cookies and passwords from FTP clients and email programs and then send the data to a remote server run by the fraudsters.
Seventh and eight places are occupied by downloaders from the Upatre family – Trojan-Downloader.Win32.Upatre.fbq and Trojan-Downloader.Win32.Upatre.fca, respectively, which are usually disguised as PDF or RTF documents. Their main task is to download, unpack and run additional applications.
Exploit.MSWord.CVE-2014-1761.k. is tenth in the Q2 rating of the most popular malicious programs sent by email. It is a Word document containing an exploit which uses an appropriate vulnerability to download to the victim computer other malicious programs designed to steal user personal data.
Malware families
If popular malware families, rather than specific malicious programs, are ranked, Upatre heads the Q2 rating. Malware from the Upatre family downloads the Dyre (aka Dyreza, Dyzap) Trojan banker. The list of financial organizations attacked by this banker depends on the configuration file which is loaded from the command center.
The MSWord.Agent family is gaining popularity, although in Q1 it only occupied third position in the Top 10. These malicious programs are DOC files with an embedded macro written in Visual Basic for Applications (VBA), which runs on opening the document. It downloads and runs other malware, such as malicious programs from the Andromeda family.
In Q2 2015, ZeuS/Zbot re-entered the Top 3. The members of this family are designed to carry out attacks on servers and users’ computers and also for capturing data. Although ZeuS/Zbot is capable of carrying out various harmful actions, it is most often used to steal banking information. It can also install CryptoLocker – a malicious program that extorts money to decrypt the data that is has encrypted.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q2 2015
In the second quarter of 2015, there were major changes in the Top 3 countries most often targeted by mailshots. Germany (19.59%), which was only fourth in Q1, topped this quarter’s rating: every fifth antivirus detection was registered on the territory of this country. Great Britain, which headed the rating in Q1 2015, moved down to second position (6.31%). Brazil settled in third (6.04%).
The USA (5.03%), which was traditionally the country most often targeted by malicious mailshots, was in fourth place.
Of note is the fact that Russia (4.74%), which came only 10th in the previous quarter, climbed to fifth position in Q2 2015.
Special features of malicious spam
In the Q2 spam traffic we continued to register malicious emails with macro viruses, although the peak of distribution for these fell in the previous quarter. Although their number decreased, they still posed a serious threat: the macros we found belonged to the category of Trojan downloaders and were designed to download other malicious programs. Fraudsters trying to convince the recipient of the legitimacy of the email masked their messages as business correspondence and passed malicious attachments off as financial documents or orders.
In some emails the attackers specified the sender’s contact details, inserted logos to make the email look official and took the email address indicated in the email from the “From” field. This made the fraudulent email look even more credible for the recipient.
In Q2 2015, we also came across emails imitating official messages from real companies, and the attackers matched the content of the message to the area of the company’s activity. For example, the emails in one of the mass mailings notified the user about the alleged text message sent by the company providing telecommunications services. The recipient was told they could read it by opening the Microsoft Word attachment, but in fact the message contained Trojan-Downloader.VBS.Agent.amj.
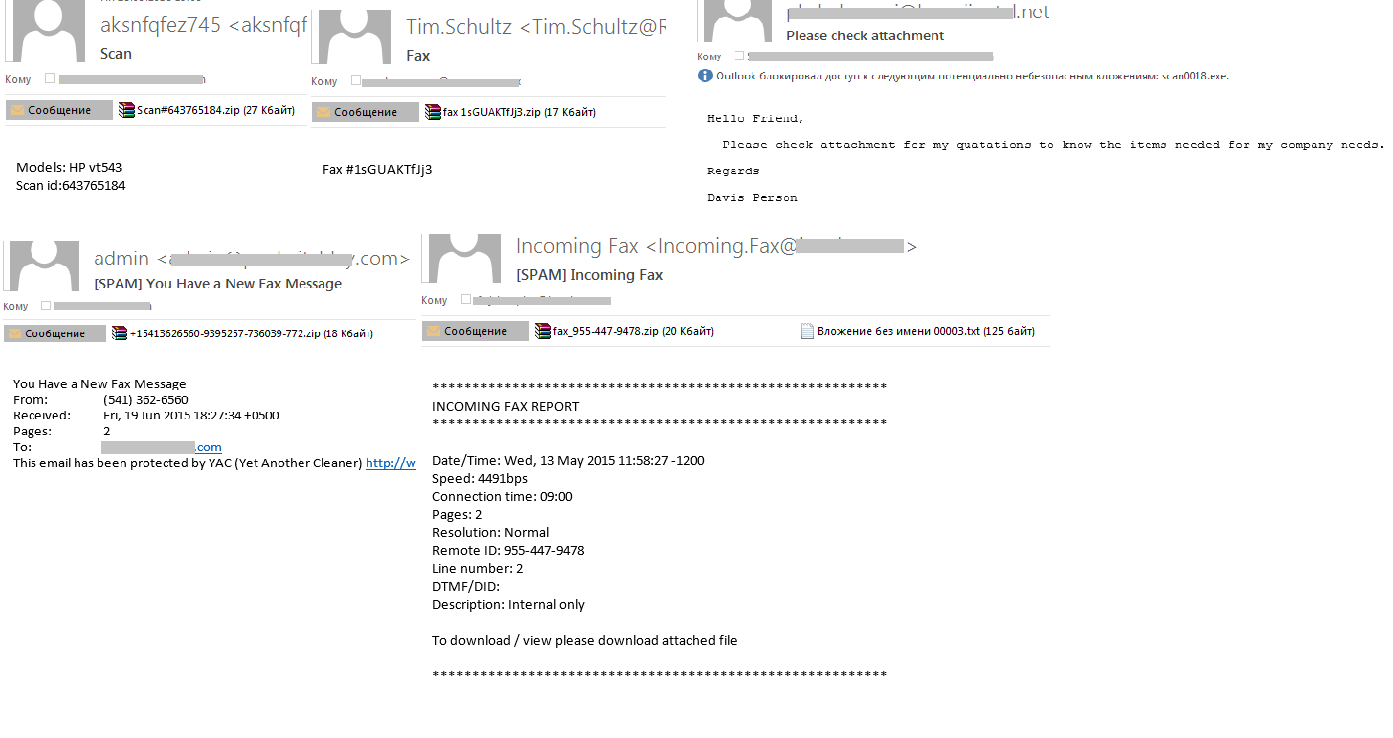
Yet another trick which remained popular with cybercriminals who specialize in sending out malicious spam was masking messages s notifications of receipt of faxes or scans of various documents. These fake notifications are written mainly in English or German, and the attachments imitating the files with faxes or scans contain different types of malware: Trojan.Upatre, Trojan.Downloader and HawkEyePHPLogger. The text in the body of such emails could be brief or, by contrast, contain detailed information about the received document
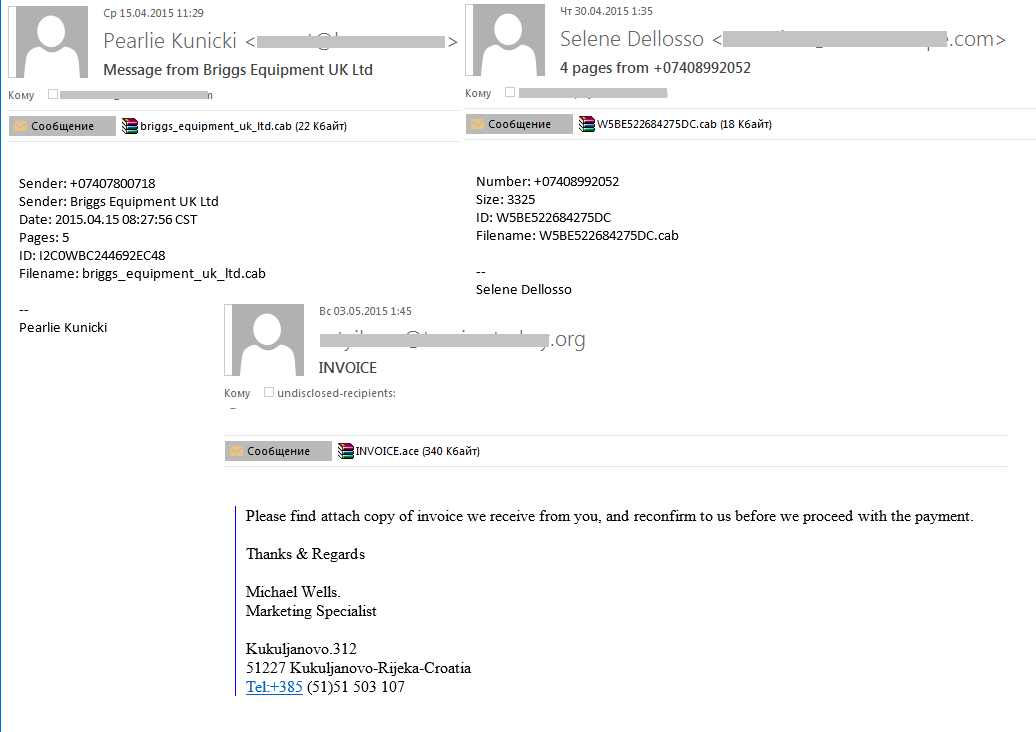
In September 2014, we registered a malicious mass mailing with an attachment that is not typical for spam – an archive in ARJ format. In 2015, fraudsters continue to use non-conventional archives to spread malware: April’s and May’s spam traffic distributed attached archives withCAB and ACE extensions, which are not common for today’s spam. The archives contained Trojan Trojan-Downloader.Win32.Cabby and HawkEye Keylogger. Unlike such popular spam extensions as ZIP and RAR, the CAB and ACE attachments may not always be recognized by users and thus cause less suspicion.
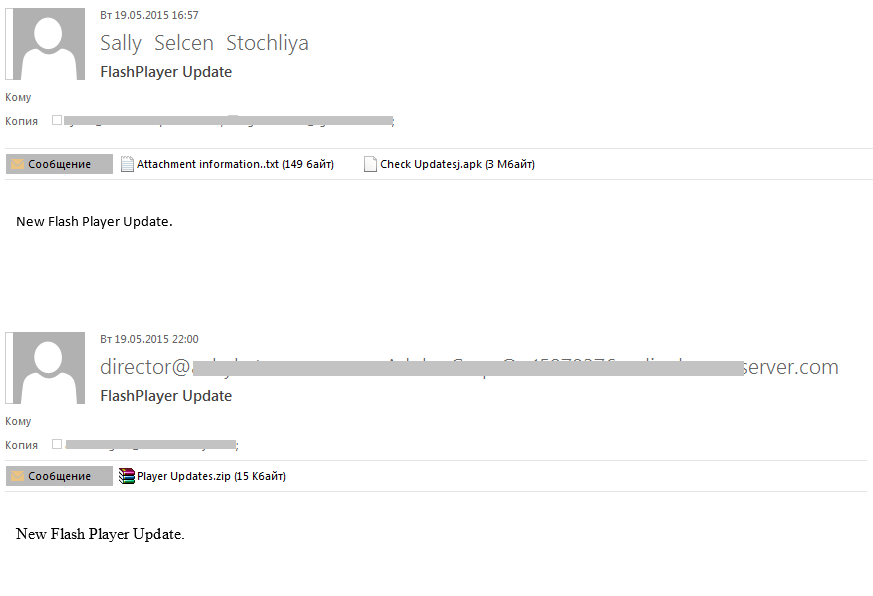
In Q2 2015, scammers distributed attached malicious ZIP and APK files within the framework of one mass mailing. If ZIP files are found in the majority of spam messages, APK files are relatively rare because they are archived executable application files for Android. The ZIP archives contained the Upatre family Trojan, while the file Check_Updatesj.apk was detected as the encryption Trojan SLocker for Android: when run, it encrypts images, documents and video files stored on the device. After that, the message is displayed to the user asking him to pay for decrypting the files. In sending malware in attached malicious ZIP and APK files, within the framework of one mass mailing, the scammers may have thought that they could trap not only PC users but the owners of Android-based smartphones and tablets working with e-mail from these devices.
Phishing
In Q2 2015, the Anti-Phishing system was triggered 30,807,071 times on computers of Kaspersky Lab users. 509,905 masks of phishing URLs were added to the Kaspersky Lab databases over this period.
For several quarters in a row, the largest percentage of users affected by phishing attacks was in Brazil, although in Q2 2015 the number fell by half compared to the previous quarter. The same thing happened to the phishing numbers in many other countries.
Geography of phishing attacks*, Q2 2015
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
Top 10 countries by percentage of users attacked:
| Country | % of users | |
| 1 | Brazil | 9.74% |
| 2 | India | 8.3% |
| 3 | China | 7.23% |
| 4 | Russia | 6.78% |
| 5 | France | 6.54% |
| 6 | Japan | 5.93% |
| 7 | Malaysia | 5.92% |
| 8 | Poland | 5.81% |
| 9 | Kazakhstan | 5.79% |
| 10 | UАE | 5.75% |
Organisations under attack
The statistics on phishing attack targets are based on the heuristic component of the Anti-Phishing system being triggered. The heuristic component of Anti-Phishing is triggered when the user follows a link to a phishing page information on which is not yet included in Kaspersky Lab databases, regardless of the way in which the page was reached – as a result of clicking on a link in a phishing email, a message on a social network or, for example, as a result of a malicious program’s operation. When the component is triggered, it displays a banner in the browser, warning the user of a possible threat.
In the second quarter of 2015, the “Global Internet portals” category topped the rating of organizations attacked by phishers – its share increased by 2.78 percentage points from the previous quarter and accounted for 42.35%. The percentage of the “IMS” category (4.05%) also grew slightly (+0.13 percentage points) while the other categories showed a decline: “Social networking sites” lost 2.6 percentage points, “Banks” – 5.56 percentage points, “Online stores” – 1.56 percentage points, “E-pay systems” – 2.84 peercentage points, “Telephone and Internet service providers” – 1.33 percentage points, “Online games” – 0.78 percentage points.
Distribution of organizations affected by phishing attacks, by category, Q2 2015
Instant messaging services are popular with fraudsters for many reasons. For example, cybercriminals often use stolen accounts for sending out phishing emails or links to malicious programs to the email addresses registered in the victim’s list of contacts, distributing spam, extorting money and other fraudulent schemes.
Distribution of phishing attacks on IMS, Q2 2015
Most of the Anti-Phishing system activations in this category fall on the popular Chinese instant messaging service QQ, supported by the Tencent telecommunications company.
Phishing pages imitating QQ personal account login pages
Second comes Skype (8.88%) owned by Microsoft. Its share is incomparably smaller than that of the leader in this category.
Phishing page inviting Skype users to verify their personal account
Top 3 organizations attacked
As we have written in our previous reports, the biggest part of non-spear phishing attacks targets the users of a small group of popular companies with many customers around the world. In this way fraudsters are trying to increase their chances of hitting the target by organizing yet another phishing attack.
The Top 3 organizations most often attacked by phishers accounts for 45.14% of all detected phishing links.
| Organization | % of all detected phishing links | |
| 1 | Yahoo! | 29.03% |
| 2 | 10.44% | |
| 3 | 5.67% |
The top three organizations targeted by phishers remained unchanged from the previous quarter. It includes Yahoo! (+23.82 percentage points), Facebook (-0.53 percentage points) and Google (-2.44 percentage points). A considerable increase in the proportion of detections of fake Yahoo! pages became possible due to the general decrease in the number of detections; in terms of numbers, the quantity of fake Yahoo! page detections increased only insignificantly.
In Q2 2015, we came across a huge number of phishing pages which imitated the publication of a Facebook page containing an intimate YouTube video. When trying to play the video, a malicious program was downloaded to the victim’s computer.
Fake Facebook pages distributing malicious files
Conclusion
In Q2 2015, the percentage of spam in email traffic accounted for 53.4%, a drop of 5.8 percentage points from the previous quarter.
In the second quarter the stories contained in “Nigerian” letters were based on real events: the upcoming Olympic Games in Rio de Janeiro, the presidential elections in Nigeria, as well as the earthquake in Nepal. Fraudsters lured the recipients not only by promising rewards or compensation, but by mentioning lottery wins and asking for a donation for the victims of the earthquake in Nepal.
The increase in the amount of SEO spam was caused by the release of the Google Search algorithm update. The purpose of the update was to raise the sites adapted to mobile phones to a higher position in mobile search results.
In the second quarter of 2015 the top three sources of spam were the USA (14.59%), Russia (7.82%) and China (7.14%).
Trojan-Spy.HTML.Fraud.gen topped the rating of malicious programs sent by email. If popular malware families, rather than specific malicious programs, are ranked, Upatre headed the Q2 rating. Germany (19.59%) was the quarter’s leader as the country most often targeted by mailshots.
Fraudsters continued to pass off attached malicious files as faxes and scans, Flash Player updates and business correspondence. They also continued to send out macro viruses in Word and Excel documents and they used CAB and ACE archives and APK files which are not typical for spam.
In Q2 2015, the Anti-Phishing system was triggered more than 30 million times on computers of Kaspersky Lab users. The largest percentage of users affected by phishing attacks was in Brazil, although the number fell by half from the previous quarter.
Spam and phishing in Q2 2015




































Max
Very informative article. Thanks.