
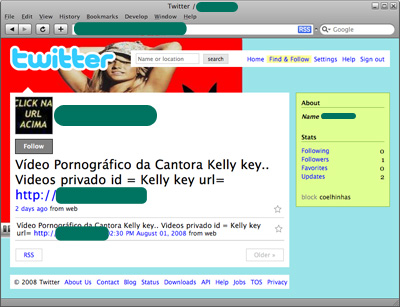
This week it’s Twitter’s turn to host an attack – one that is targeting both Twitter users and the Internet community at large. In this case it’s a malicious Twitter profile twitter.com/[skip]/ with a name that is Portuguese for ‘pretty rabbit’ which has a photo advertising a video with girls posted.
This profile has obviously been created especially for infecting users, as there is no other data except the photo, which contains the link to the video.
If you click on the link, you get a window that shows the progress of an automatic download of a so-called new version of Adobe Flash which is supposedly required to watch the video. You end up with a file labeled Adobe Flash (it’s a fake) on your machine; a technique that is currently very popular.In reality, this is a Trojan downloader that proceeds to download 10 banker Trojans onto the infected machine, all of which are disguised as MP3 files. We first detected the downloader proactively as Heur.Downloader and then added a signature to detect it also as Trojan-Downloader.Win32.Banload.sco. Only 1 person is following this profile currently:
We assume this is one of the authors. The person following the malicious profile is doing 1 thing only as well – following yet a third profile.
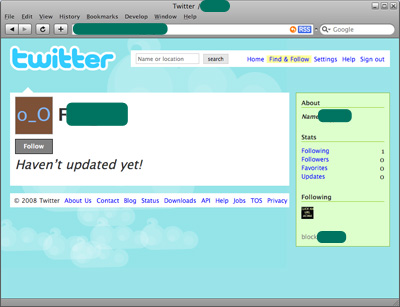
The footprints of this particular crime are pure Brazilian – ranging from the Portuguese, to the web servers hosting the banking malware to the email embedded in the malware which is used for receiving data from infected machines.
This technique does not require any serious programming skills – buy some Trojans, upload them onto a web server and create a chain of Twitter profiles following each other.
Then you only need to post the link in a social network. Unfortunately, Google indexes un-protected Twitter profiles, so malicious pages built and marketed with good social engineering tactics end up high in the rankings.
It gets even scarier if you combine this attack with something like an auto follow-me vulnerability on Twitter – Ryan wrote about this just last week.
Luckily, we haven’t found any links to this particular profile in forums, blogs or other social networks…yet.
But – this method is being used successfully on Twitter since the end of 2007. This is just one example – something I found over the weekend. We are monitoring this particular profile and keeping a sharp lookout for similar cases.





















Social engineering on Twitter