
The portmanteau-named SKYPEFALL.EXE is the latest, very active, malware-spamming campaign spreading through Skype. We first registered this attack on March 3 using both Spanish and English to lure victims. How does this attack work?
The victim receives a Skype message in the following format:
Oh, My God ! [user name in Skype] video: http://********skype.info/video/?n=[user name in Skype]
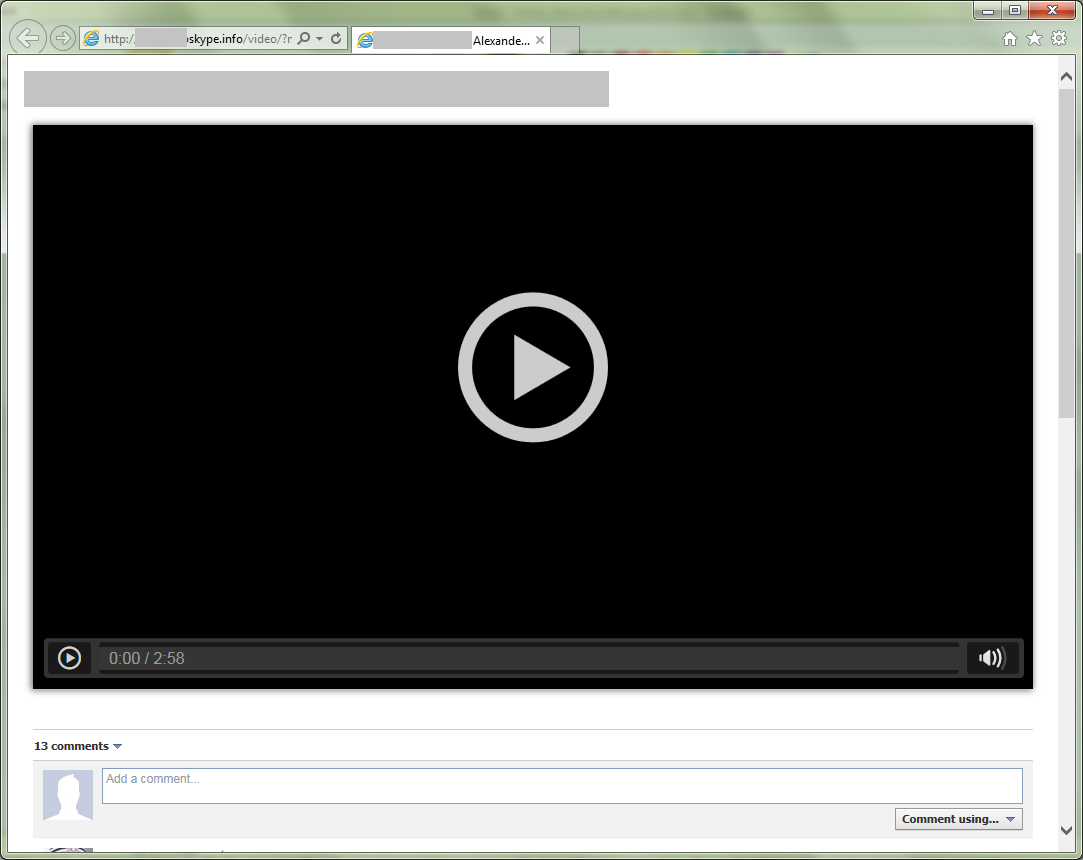
If they click on the link and use Internet Explorer, it leads them to a fake video Website full of fabricated comments meant to pique the users interest while inviting the victim to download a plugin in order to watch the video itself:
Again, the URL used in the malicious message sent through Skype is available only if the browser referrer points to Internet Explorer. If the victim uses any other browser, the URL is simply unavailable.
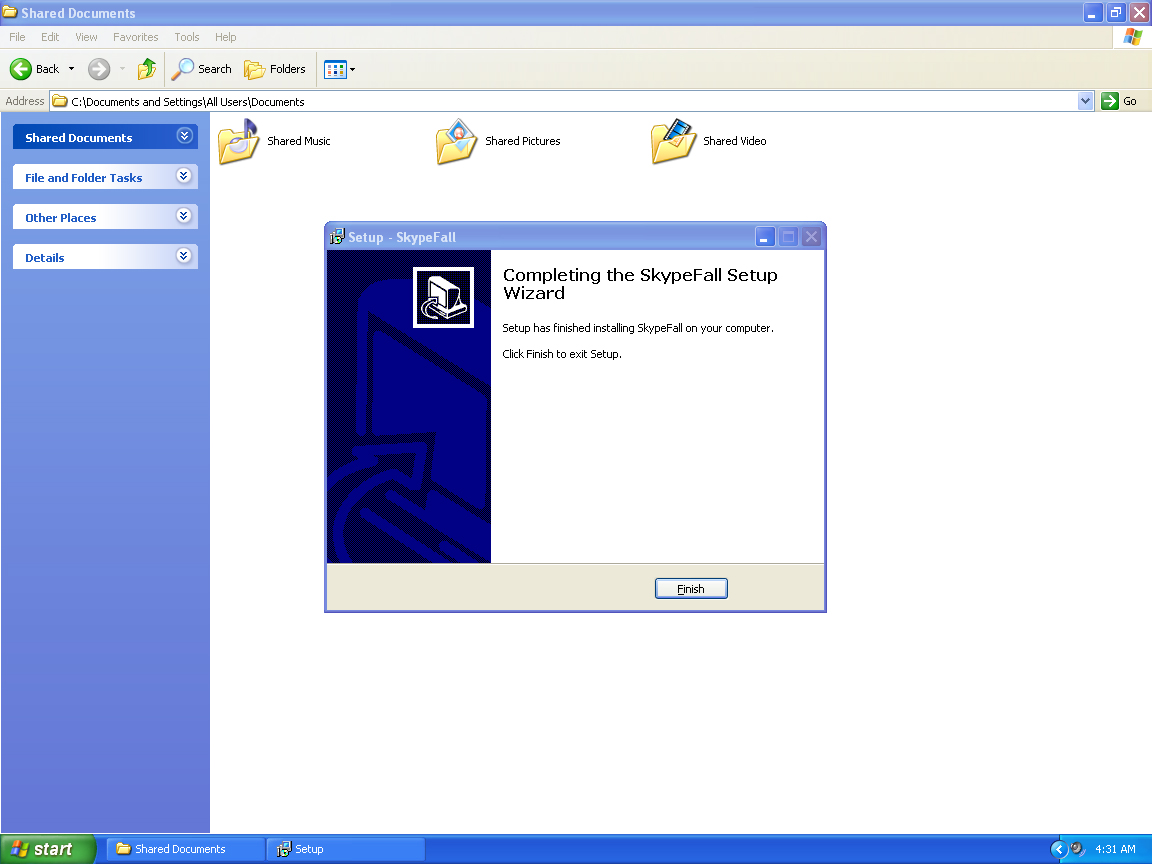
The initial setup.exe is a RAR auto-extractible file with embedded instructions. It includes a full GUI installation package.
The victim receives both Adware-like functionality as well as Backdoor capabilities. Once it is installed on the victim’s machine, it abuses the new victim’s Skype friends list to continue spamming the aforementioned messages. The instructions for its behavior are downloaded from another server and look like this:
“skype_restart_mins”: 120,
“old_friend_hours”: 48,
“del_msgs_limit”: 5,
“send_strategy”: 1,
“max_loc_msgs”: 60}
The malware also includes an embedded SMTP client that would potentially allow the attackers to send spam through the victim’s machine.
The attackers leading this campaign are changing this binary on the Web every few hours. In this way, they are trying to evade any consistent AV detection.
Kaspersky lab detects this threat as Trojan-Dropper.Win32.SkyDll.a.
























Skyfall Meets Skype