Back in March 2012 we teamed up with Crowdstrike, the Honeynet Project and Dell SecureWorks in disabling the second version of the Hlux/Kelihos-Botnet. We thought that now would be a good time for an update on what has happened to that sinkhole-server over the last 19 months.
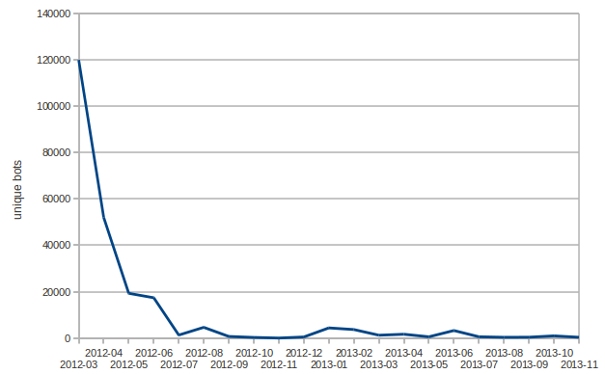
What we see now is what we expected. The botnet is getting smaller and smaller – victims have been disinfecting or reinstalling their PCs over time. At the moment we’re counting about 1000 unique bots on average per month:

Number of unique bots since March 2012
Due to the botnet’s peer-to-peer-design, there could still exist an independent subset of the initial botnet which never connected to our sinkhole. But we think that the bot-count for any such subset would have evolved in a similar way, because most likely the bot-herders would leave them alone as well and concentrate on establishing “Hlux 3”.
Most of the bots are still running under Windows XP. But we also saw some bots running under Windows Server 2008:

OS (last 14 days)
Most of the infected clients are located in Poland:

Countries (last 14 days)
The group behind Hlux is known to be adept at quickly renewing their illegal infrastructure. Since the group is also known to be behind the Waledac botnet, we think that this is unlikely to be the last we hear about this gang.
Last but not least, a quick review about the story of Hlux/Kelihos:
In September 2011 we performed the first takedown of Hlux. The criminals responsible for that botnet didn’t show a major interest in taking counter-measures – they abandoned the botnet to its fate (of being under our control now) and immediately began to build a new botnet. So after a short time, Hlux 2 appeared on the radar and we did it again – poisoning the p2p-network to sinkhole it. And again, the criminals quickly rebuilt their botnet and Hlux 3 was born – within 20 minutes! In March 2013 the bad guys were faced with a new shutdown operation – initiated and performed live at the RSA Conference 2013 by our friends over at Crowdstrike.




















Sinkholing the Hlux/Kelihos Botnet – What Happened?