
A few days ago, we have notified you about malicious activities from the S.A.P.Z. botnet. And we provided evidence that this methodology of attack can be used to affect users of any Latin America bank, or any part of the world.
Now the S.A.P.Z. gang, which may be Peruvian, has resorted to another strategy. It is focusing on the theft of sensitive information, by spreading a variant of Palevo worm, detected by Kaspersky Lab as P2P-Worm.Win32.Palevo.cudq.
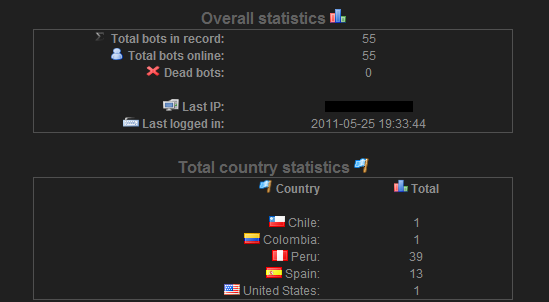
The key element of this is that with S.A.P.Z., the cyber-criminals have used the functionalities of an old web application created for the administration of stolen data, called Blackshades. As indicated in this image, now they’re not only focusing on Peruvian users, but also others countries such as Chile, Colombia, Spain and USA.
This web application is very old crimeware in the cyber-crime environment, but clearly the target is Latin America.
In this way, the cyber-criminals have expanded the attack, stealing sensitive information about bank through local pharming using S.A.P.Z., as well as serial numbers of several applications and authentication data from different web services. Here is a short list of the application “victims”:
- CD Keys, Windows Product Keys,
- Windows Live Messenger, Yahoo Messenger, Google Talk, AOL Instant Messenger, Trillian,
- GMail, Yahoo! Mail, Hotmail/MSN mail, ICQ Lite, GAIM/Pidgin, MySpace IM
- Outlook Express, Microsoft Outlook (POP3, IMAP, HTTP and SMTP Accounts), among others.
DDoS attacks are also in the list of these Latin American cyber-criminals, as well as self-defense measures which basically consist of acting as a “cleaner” to remove from the victim machine a number of potential competitors, including the malware variants Apocalypse RAT, Bandook RAT, Bff BOT, Cybergate, PoisonIvy, Schwarze Sonne RAT, Solitude RAT, SpyNet RAT y ZeuS.
The cyber-criminals activities in Latin America are becoming more aggressive. And certainly the development of crimeware seeks to reach a threshold that gradually becomes more and more worrying in an emerging region that, in the eyes of criminals, has become a significant environment in which to operate cyber-criminal activities.




















S.A.P.Z. Botnet, new perspective of attack