Kaspersky Lab congratulates the royal couple on the birth of their new baby boy and wish them all well for the future. It is truly joyous news that is being celebrated in the UK and in the rest of the world.
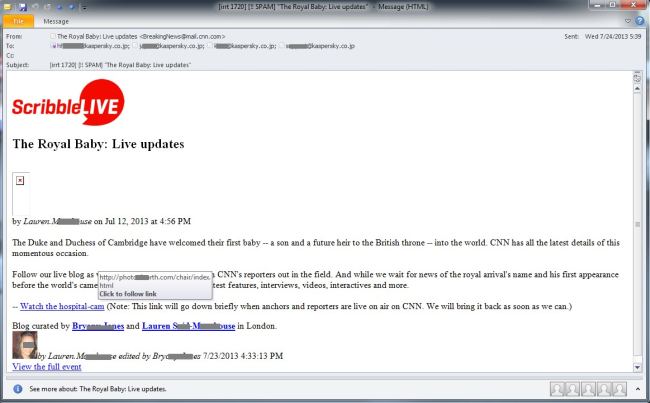
However because it is such big news, it didn’t take long for malicious elements to misuse it as follows: “The Royal Baby: Live updates” promises an email arriving at our spam traps today. A link named “Watch the hospital-cam” is the contained trap which leads to … nowhere because it seems that it has already been cleaned. By the looks of it, it may be a compromised legitimate website which got cleaned.
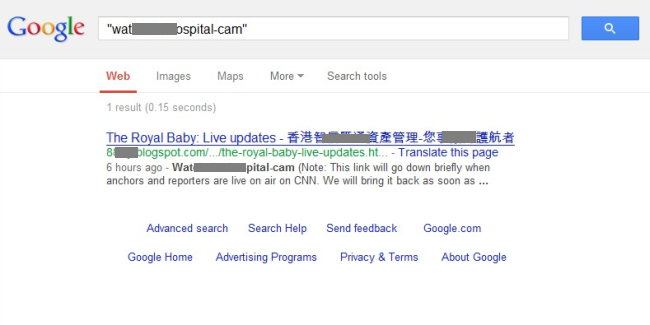
But we are still interested in what the malicious content could be and we didn’t need to search for long. Exactly _one_ hit for our web search was shown at the time of writing this article.
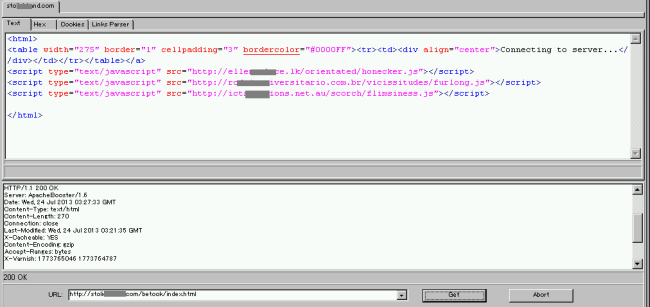
What we find there is basically the same textual content as we had seen in the email but there is one difference: the contained link to the “hospital-cam” is currently still alive. It contains three links with *.js naming on yet another set of hosts.
Checking these, we finally see what it is all about, namely a “Blackhole Exploit Kit” serving URL – a drive-by approach to infect unprotected users “on the fly”.
Kaspersky Lab products detect this threat as “Trojan-Downloader.JS.Expack.aiy”.





















Royal Baby Lures to Blackhole Site