
Yesterday Kaspersky Lab detected the first rootkit banker created to infect 64-bit systems. It was detected in a drive-by-download attack made by Brazilian cybercriminals.
We found a malicious Java applet inserted in a popular Brazilian website. The attack was made using a malicious applet in such a way as to infect users running old versions of the JRE (Java Runtime Environment) and was prepared to infect users running versions of both 32 and 64 bits systems.
Inside this applet we found some interesting files:
The entire malicious scheme is simple yet interesting. The file add.reg will disable the UAC (User Account Control) and modify the Windows Registry by adding fake CAs (Certification Authorities) in the infected machine:
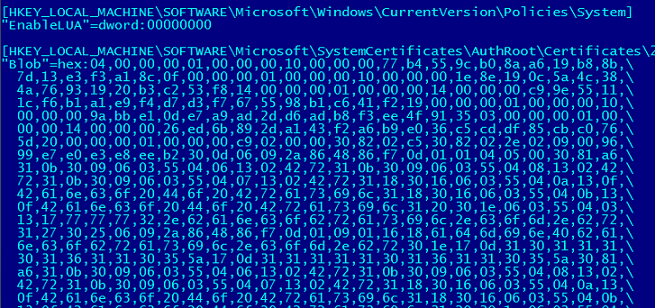
The file cert_override.txt is a fake digital certificate signed by the fake CA registered in the system. The main purpose of this attack is to redirect the user to a phishing domain. The fake website will then show an icon of an https connection, simulated to be the real page of the bank. This scheme to register a malicious CA in an infected system has been used by Brazilian bad guys since last year.
The file aaa.bat will run and execute the file bcdedit.exe, a legitimate tool developed by Microsoft aimed to edit the boot configuration of Windows Vista and later versions. Using this tool and some parameters like “DISABLE_INTEGRITY_CHECKS”, “TESTSIGNING ON” and “type= kernel start= boot error= normal” the files plusdriver.sys and plusdriver64.sys will be copied to the drivers folder and registered as active drivers during the next reboot. This technique allows them to launch their driver without a legitimate signature, was described recently by my colleague Vyacheslav.
After they are registered, the malicious drivers will execute some commands to change the hosts file by adding a redirection to a phishing domain as well as removing some files belonging to a security plugin used by Brazilian banks:
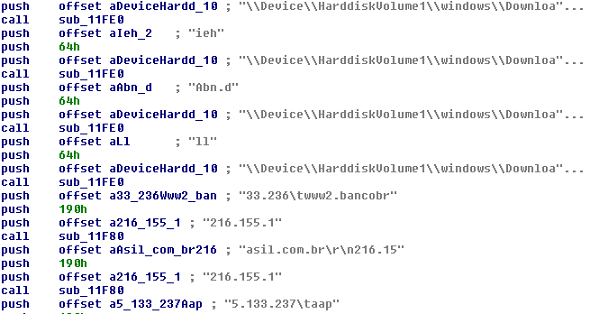
The malicious files are detected as
Rootkit.Win64.Banker.a, Rootkit.Win32.Banker.dy and the malicious applet as Trojan-Dropper.Java.Agent.e.





















Rootkit Banker – now also to 64-bit