
Not only Windows users are a target of bad guys that want to distribute rogueware. Now they are also attacking Mac users using the same and old blackhat SEO techniques, poisoning search results in popular search engines.
During our research about Osama Bin Laden’s death we saw the same malicious domains serving two rogueware applications specific to Mac OSX, called Best Mac Antivirus and MACDefender.
When doing searches the user can be redirected to some malicious domains, like this for example:
***-antivirus.cz.cc/fast-scan2/
So the malicious pages check for: browser agent (it must be Safari), the IP address (only US domains now) and the referrer (if it is Google or other search engine). After these checks the malicious page will show a fake scan screen:
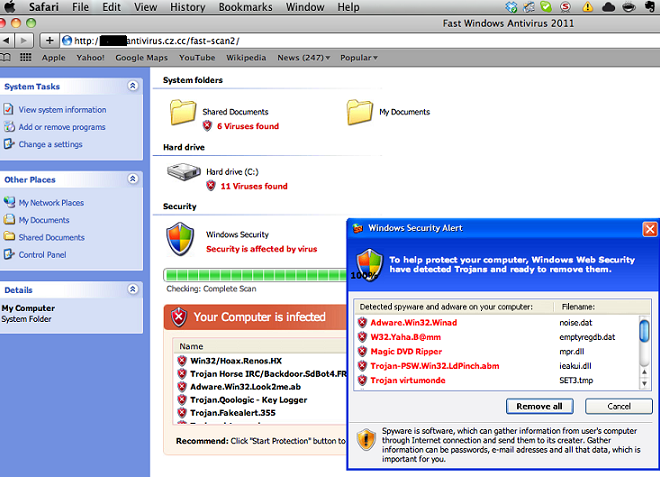
Even though the page is showing a fake Windows screen, the file offered will be a .mpkg: the installer of the rogue application:
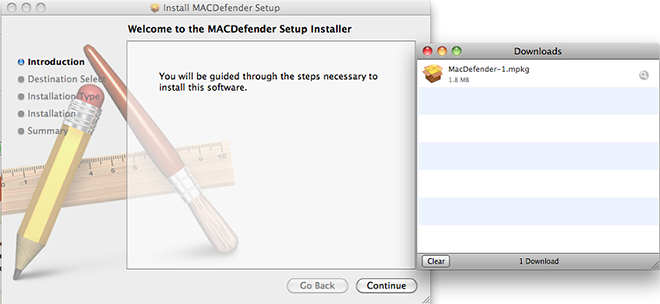
For the application to be installed, the user needs to input his root password.
This is the main window of the rogue application:
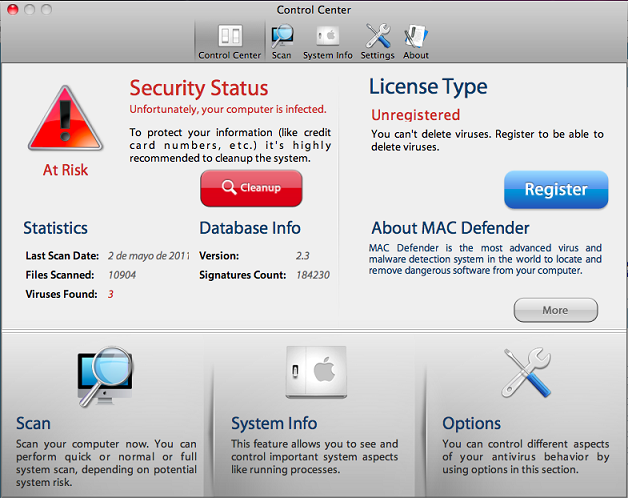
And the fake scanning:
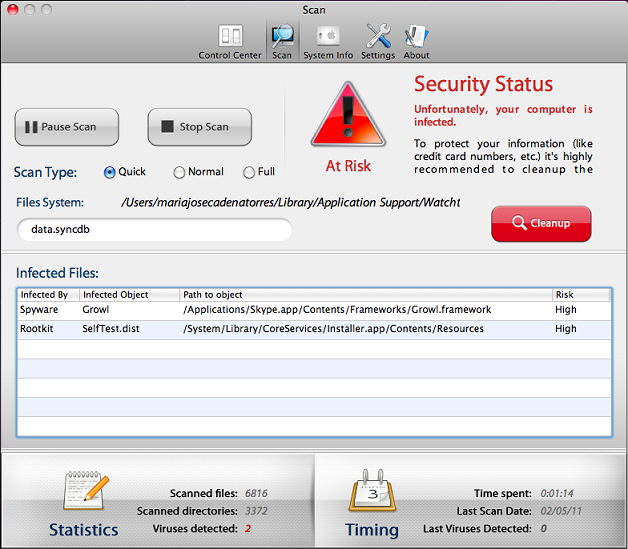
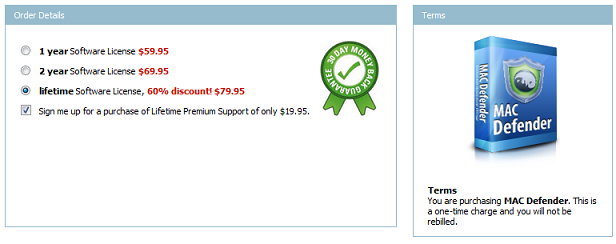
The malicious application also displays gay-porn website and asks the user to pay US $79,95 to buy it:
As our researcher Kurt Baumgartner pointed out last April this was expected:
While the FakeAv rotation through .co.cc is not a shocker to security researchers at this point, one interesting domain popped out from the tens of thousands of .co.cc sub domain fakeav hits over the past day…”antispyware-macbook(dot)co(dot)cc”. This marketing quirk is odd, even for these guys. Does this domain suggest that another Apple based malware is in the works? Possibly.”
Both applications are detected by Kaspersky Antivirus for Mac.




















Rogueware campaign targeting Mac users