
The title of this blog reminds me of the old zombie horror movies back from the 80-ies, but what im going to write here is more like a comedy. Some of you guys have probably read my blog post about the time when i tricked them into accessing websites under my control, which led to me collecting alot of information about the callers.
After that blog post i didnt receive any calls… until today. I was sitting in my home office, drinking my daily smoothie and writing on my paper for the Virus Bulletin magazine, and suddenly i hear the phone ringing. I dont care about that anymore, because i hear that my wife answers the phone, but after a few minutes she enters my room and tells me that “they” are calling again.
As always, i booted up my VMware image with a totally FRESH installation of Windows XP and start talking to the scammers. For you who are not familiar with the scam, please read my other blog post which can be found below because i wont cover it in this post.
https://securelist.com/trying-to-unmask-the-fake-microsoft-support-scammers/33734/
This time the scammers where using some different methods trying to convince me that my compute where infected with some malware. They even gave me the name “Frozen Trojan”, and went to Google and tried to look it up for me. But they only ended up on results talking about the bird flue and other biological viruses which i thought was quite entertaining.
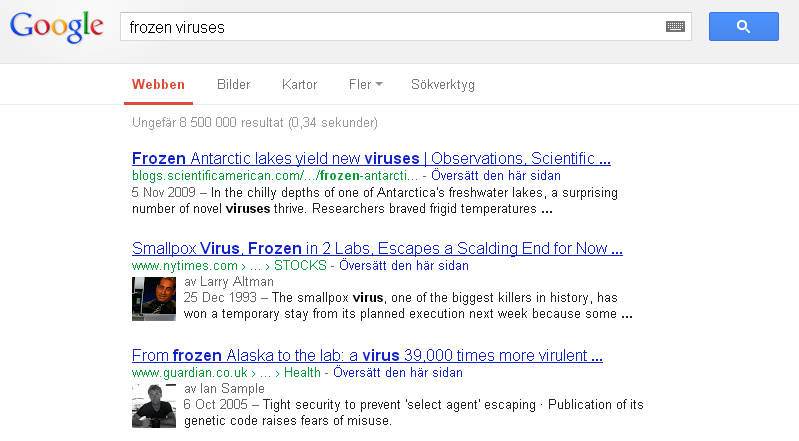
What is new is that the scammers are now using a search function within the indexing services for Microsoft Windows to trick victims. They are telling me on the phone that my Software License Service is not working, and thats why my security is failing. They then have me search for the keywords “software warranty”, and i do get up a error message saying “Service is not running”.
After this they transfer a file to my computer, which they say is the “state of the art” security scanning software. The software is called “Advanced Windows Care 2 Personal”, and when they scan my freshly installed Windows XP, not FRESHLY INSTALLED computer they still find tons of problems.
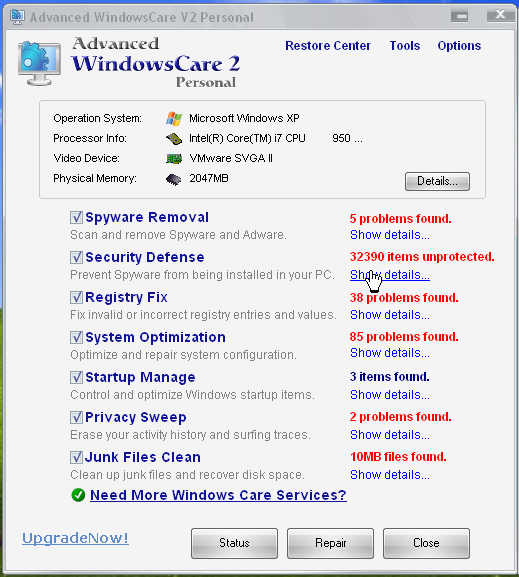
The scammers they continue, just as last time that they can offer me the best solution. They even tell me that if i dont fix this problem, this virus can infect my printer, camera and other devices which are connected. But the solution is not far away, if i only pay for a “Subscription Fee”, everything will be fine! The program is for free, but i need to pay for the subscription. The prices they told me are very high.
- 2 years for 245 eur
- 3 years for 345 eur
- 4 years for 445 eur
- 10-15 years for 501 eur
Finally, they want to go through with the payment, and we visit their landing page, which this time looks like this:

At this time i also play along, and tell them that my credit card is not working, but i have a backup on my webserver, and i try to access this file. Once again the file only contains the string: “Permission Denied, you are trying to access a restricted file via a proxy! Try from another computer!“, and after about 20 minutes i get the scammers to try from their side, and i get their IP number… *AGAIN*
115.xxx.xxx.xxx – – [21/Nov/2012:10:19:18 +0100] “GET /xxx/.txt HTTP/1.1” 200 422 “-” “Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.11 (KHTML, like Gecko) Chrome/23.0.1271.64 Safari/537.11”.
All information has been sent over to law enforcement. I just think its strange that they keep calling. I want to ask everyone who is reading this post to tell their relatives and friends about this, so they are aware that they phone scammers are still calling people.
Return of the Indian phone scammers!





















Mel
Been scammed by these guys too!!! They are tricky and just do enough work to seem legit. Was told by my bank that it is like taking my car to a repair shop, I still have to pay for services rendered even if they don t fix the problem. This is how they are able to stay up and running. These people use fear as a motivator to engage the use of their services. It was just amazing how callers trying to hack into my computer would call shortly before or after this PC repair company would call and say they are receiving error messages and that my computer was at risk. What was more amazing was that these supposed hacker jerks would sound like the company representatives from this PC Enterprises company or whatever name they are using. I am 99% certain that it was all part of the hack. Complain to your bank if you have been scammed, especially if services paid for have not been done. They may or may not be able to do anything, but get the word out. It is embarrassing to be caught up in a scam, but I am not going to let my pride get in the way of warning others. So good on you for posting this blog.
Julian Waade
I too suspect I have been scammed yesterday by Southend Enterprises (30/09/2014) & paid £99.99 for the service (2year cover!) after pleading poverty. I continually asked them to reassure me that they represented Microsoft Windows. Same MO as above – I have been able to temporarily stop payment on yesterday’s transaction. I found they had left a programme running allowing remote access which I disabled but don’t now know if it is resident in my computer but hidden. Can anyone tell me if it is likely that my card details will be used again? Am I vulnerable in my computer?
Julian Waade
I should also point out while they had control of my PC they entered my email & sent an authorisation for payment to themselves from me & did not follow up with any promised Invoice etc. I should have been more careful!
bill
I have had these scammers, and just play with them at one time I was on the phone with them for 45 minutes acting deaf. Giving them wrong info, when even they were getting upset
,I loved it
Shilpa MV
I worked for that company for 2 weeks. when i attended interview they said its tech suport. Left th job when i understood its total scam.