
Spammers frequently use redirects in their emails: after clicking on a link in a spam message, the recipient is often taken through a series of websites before reaching the destination resource.
There are many reasons for using redirects. In most cases, they help spammers to hide the data that enables spam filters to classify a message as unwanted – e.g., the website or contact phone number of the spammers’ customer. As a result, the recipient (as well as the spam filter) sees no links to the website being advertised in the message, no telephone numbers or email addresses that can be used to contact those who ordered the spam mailing. The message only contains a link to an intermediary resource. In addition, if the spammer is a member of an affiliate program, he will need to know how many users followed the link, because his income directly depends on that. As a result the chain of websites through which a user is sent may include redirector sites which function as counters.
We will look at the most popular spammer tricks that use redirects in one way or another, the most common and widely used types of redirect, as well as the distinguishing features and subjects of spam messages containing redirects. All of these give users all over the world a great deal of trouble every day.
Types of redirect
Redirects can be classified based on different criteria. We will categorize them based on the objects they use to perform redirects. The two most commonly used methods are redirects using links and redirects using HTML attachments.
Links
Using links to redirect users is a commonplace spam tactic. As a rule, after clicking one of these links users are taken to a web page from which spammers redirect them to the target resource using one of the redirect techniques discussed later in the text.
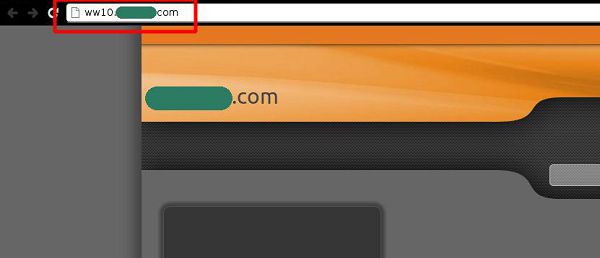
Another simple trick used to mask spam links is to use URL shortening services. These provide spammers with a way to quickly create a masked link to their site, as in the sample message shown below.
There are many of these services nowadays. They are mostly used to create short links, particularly for services like Twitter which have strict character counts on their texts. Rather than using existing URL shortening services, spammers sometimes create their own. These ‘in-house’ link shortening services have one big advantage – nobody checks where the spammers’ links lead. Their shortcoming is that any spam filter can ban the service as a whole, immediately blocking all of the spammer’s emails.
HTML attachments
To perform redirects, spammers often use specially crafted HTML files. When opened, these redirect the user to a spammer website. This involves a variety of tricks and techniques, which are discussed later in the document. These files are attached to spam messages and the attackers just need to find a way to lure the user into opening the attachment.
Spammers keep making the source code of HTML pages attached to their messages more complicated and convoluted to hide the fact that it performs a redirect from spam filters. In addition, once in a while they completely change their redirection methods.
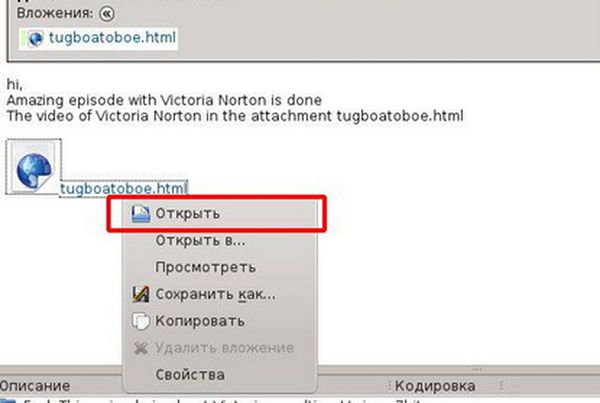
Here is a sample of the messages we detected last summer:
The text in the message typically encourages the recipient to have a look at the attachment. But what do we see when we open the file? Instead of the Victoria Norton video promised by the spammers, we find ourselves on a spammer site – and all we did to get there was open the attached HTML file.
In the message shown in the first example, we were at least redirected to the watch advert promised by the spammers – but in the second case we were taken to a website with no advertising content, which had been compromised by the spammers. These emails demonstrate that it is sometimes more important for spammers to obtain active email addresses and make money by having their owners follow links (which is what happens when the HTML attachment is opened) than to advertise specific goods.
Both redirecting links and HTML files used for redirects are often found in spam. Although each of these methods uses the browser on the victim’s computer, the implementation of redirects at the source code level differs significantly and so do the techniques used by spammers to make these redirects work on user machines.
Techniques
The spammer techniques which go alongside redirects are well known. Some of them have been employed for over a decade and are still in active use. Most are designed to evade spam filters and hide the fact that a redirect is present in an email at all. We will look at the most commonly used approaches to implementing redirects.
1. Redirects based on JavaScript
This is how the source code of an HTML attachment implementing a redirect might look:
The spammers are clearly making a more or less straightforward attempt to evade the filter by breaking the text up into short strings which together make up the link (shown in a frame on the screenshot above) and changing the value of the location object to perform the redirect:
window.location = “http://…”; – modifying this object is a common method of redirecting using JavaScript. The redirect is performed without any user input.
The same effect can be achieved with the following changes:
document.location.href = “http://…“
window.location.reload(“http://…“)
window.location.replace(“http://…“)
2. Using meta-tags
As an alternative to modifying the location object, spammers have another redirect method which achieves the same effect – the HTML meta-tag. Meta-tags are generally used to store a variety of information about the page, such as encodings, HTTP headers, content keywords etc.
One possible application of the tag is to use the refresh header with the url parameter, which also leads to the user being automatically redirected as the page is being loaded.
It is particularly worth noting the small size of the resulting HTML file. Since the meta-tag is described in HTML headers, the page need not have any content at all, as in the example above. This is why this trick is often used in HTML pages attached to spam messages.
3. iframe leading to a third-party website
Using an iframe tag to redirect the user to a spammer website makes it possible to display the content of an external page on the current page – inside a block of a given width and height.
When the user opens the attached HTML file, the browser loads the content from an external webpage into an area defined by the iframe. Spammers often specify a large size for the area (in this case, 100% width and 4700px height), making the content from an external site fill the current page. The screenshot below shows the result of opening one such attachment – a Romanian advertisement for English language courses was loaded from an external site into an iframe area which takes up all of the screen area in the browser.
4. Configuring .htaccess
Configuring .htaccess is rarely used on the server side, even though it is convenient for spammers. As a rule, spammers reconfigure these files on their own servers.
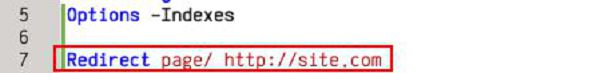
As a rule, the .htaccess file can only be accessed by the server’s administrator. If it was created in a directory on the server and is correctly configured, following links pointing to that directory will immediately redirect the user to the resource specified in .htaccess. For example, if the spammer has placed a specially formed .htaccess file into the /spamdir folder, all users who follow the link “http://example.org/spamdir” in a spam message will be automatically redirected by the web server to a different website, as located at the address specified in .htaccess.
In most cases, the Redirect directive is used in the file settings, specifying from which page of the site the user should be redirected to where (framed in red on the screenshot below).
Another way of creating a redirect is by using the RewriteCond directive, which defines a regular expression with which the link should be associated. This directive, together with RewriteRule , defines a rule to change the address of the user’s current page. If the IP address of a user visiting the page matches the regular expression defined in RewriteCond, the user will be redirected to the address defined by the rule in the RewriteRule directive.
Cybercriminals often use this technique to redirect users to websites of the affiliate programs that fit them best based on the country and region of their IP address. This makes redirects more targeted and effective.
Below is an example of a typical spammer.htaccess, which redirects visitors from the subnets listed.
5. Using PHP
A rare, though not quite forgotten, technique involves the use of the capabilities of different scripting languages to redirect users.
The simplest implementation of a redirect in PHP:
The Location HTTP header is passed to the browser, resulting in the user being redirected to the specified website.
Other headers are often used for the same purpose, as well: different HTTP status codes (3хх), which indicate that the page contains a redirect, are specified in the HTTP headers passed to the browser.
<?php header("HTTP/1.1 301 Moved Permanently “);
header(“Location: http://…”);
exit();
?>
Content obfuscation
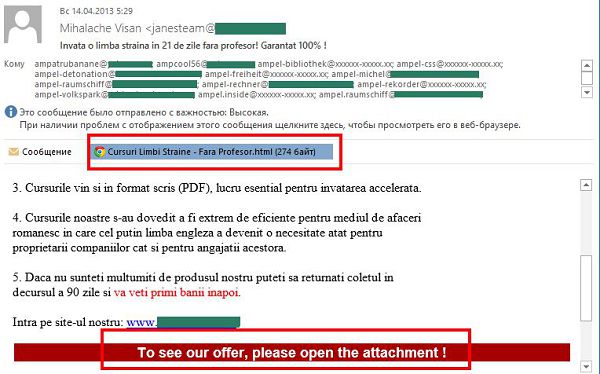
Here are samples of spam messages we detected in September.
Another spammer trick: a potential victim receives a fraudulent email with an HTML file attached, disguised as a transaction status report. As soon as the file is opened, the spammers inform the recipient unashamedly that he or she will now be forwarded to a different page – without mentioning that it is a phishing page.
Sometimes spammers send the source code which implements a redirect in the message body rather than an HTML attachment, hoping that the user has an old version of the mail client (modern email software has protection against downloading any content from the web) and that the redirect will be triggered while the recipient is viewing the message:
Let’s have a look at the source code of the message and see how the redirect works:
We can see that the spammers have gone back to using JavaScript redirects, but this time the source code is much more heavily obfuscated. Spammers are also using arrays of constants — numeric values corresponding to characters, from which the spammer link is subsequently assembled (as it turns out, these values are also multiplied by a function of each element’s number in the array).
Let’s see what we get after de-obfuscating the code. After extracting the script from HTML code, we can use such resources as JsPretty in conjunction with jsbeautifier.
Now we can see that the spam link was, after all, in the script. But where and how was it stored?
To understand the techniques used by spammers to conceal the presence of a link and evade spam filters, we need to analyze all the operations performed by the de-obfuscation utility.
First of all, we need to format the script so that it is readable – insert the indents, spaces between operators and line feeds.
The code is now easier to understand, but this is not enough. We are going to further simplify it manually, trying to find out what it does:
- Remove unneeded variables and statements which are always executed.
- Track variable values and substitutions.
- See what calls we get as a result.
Now we can see that all the script does is:
- create string s, which contains executable code;
- 2.execute the code (the line containing window[eval]).
Finally, there it is — the much sought-after link that will be used to redirect the victim!
Now we understand the algorithm used by spammers when generating such JavaScript attachments:
- Break up the link into characters, take their byte values and save a function of these values in an array.
- Call functions in a loop to put the link together from values in an array.
- Add more operations which assign the values of some variables to other variables in order to modify and mask the original names.
- Add ifand try-catchblocks with true arguments to all parts of the code.
- Apply steps 1-4 several times until suitably unreadable code is obtained.
The entire redirect chain is presented below:
Subjects used in emails containing redirects
Redirects designed to conceal the actual links or spammer contact information are present in spam on virtually all subjects and are getting more popular every year.
In the case of messages with HTML pages attached, the situation is different. In these messages, links usually lead to phishing sites, with cybercriminals seeking passwords to mailboxes. It is less common for these links to go to adverts for different kinds of software or other services.
Recently, spam emails with redirects leading to online dating sites have become more numerous.
As mentioned above, depending on the IP address a user can be redirected to one of several spammer websites. Spammers use this trick to make more money from the same spam. They participate in several affiliate programs at the same time and redirect users to the most appropriate ones depending on their region. The upshot of this is that by following the same link, a user in Europe may be redirected to a phishing site and somebody in Russia – to an online dating site.
Conclusions
The use of different redirect techniques is a good example of the way spam evolves over time. Some techniques are simple and obvious for recipients, who realize they are being redirected to another resource. However other, more sophisticated methods are evolving simultaneously. These involve unsuspecting users being redirected across a chain of websites to the final page, which is the only one the users see. Moreover, a significant proportion of spam emails have spammer links deeply embedded in the source code of HTML attachments. Spam analysts have numerous tools that help them to ‘catch’ spam emails. For example, spam filters can perform full deobfuscation of all code, or use the presence of obfuscated code as an indication that an email is spam (the latter method can lead to false positives). It is actually easier to block a spam mailing based on its content or formal attributes than try to deobfuscate code in each message.
Redirects are particularly dangerous if the links contained in emails ultimately lead to malware, as well as when links are part of phishing or otherwise fraudulent emails. On the one hand, users are becoming more careful, which means that such spammer techniques should be getting less effective. But on the other hand, there are always new inexperienced users who are just getting to know what the Internet is all about, and who may struggle to recognize spam tricks. We would like to offer some basic advice that will help you to significantly increase the level of protection for your computer:
- Do not open HTML files attached to emails if you do not trust the sender. This also applies to all other types of attachments.
- Check where a link leads before following it. In most browsers and email clients, it is sufficient to hover the mouse pointer over a link to see where it leads. Do not click on a link if you have any doubts about the sender’s reliability.
- Do not try to unsubscribe from any spam mailings — this will only inform the spammers that your email address is ‘active’ and they will want to send more spam to it. It is better to delete any spam received at once.
- Use security solutions that offer antivirus and anti-spam technologies and regularly update them.
And do not forget about the general rules of Internet security — observing them will help you to avoid falling victim to attacks by fraudsters and other cybercriminals.
Redirects in spam
































Beat
good article about redirection techniques of spammers