
Brazilian cybercrime is based primarily on the spread of Trojan bankers. For some time now the country’s bad guys have been investing their efforts in new monetization schemes, the latest includes the use of adware. And the perfect place for distributing this sort of malware? Yes, that’s right – social networks. This is how “PimpMyWindow”, an adware and click-fraud scheme that has infected several Brazilian Facebook users in recent days, works.
To spread quickly among innocent users the adware uses a “change the color of your profile” option that recently surfaced. The infected profiles are used to spread automatic messages to your Facebook contacts:
“Tired of the color of your profile? Install PimpMyWindow now”
The website offers a plug-in for the three most popular browsers: Chrome, Firefox and IE.
Sorry Opera users, no adware version available for you…
Once it’s installed, it’s programmed to display ads from Google’s Adsense on popular social network websites such as Ask.fm, Orkut, Facebook, Twitter, YouTube, webmail services such as Gmail and Hotmail, and the Google.com search engine.

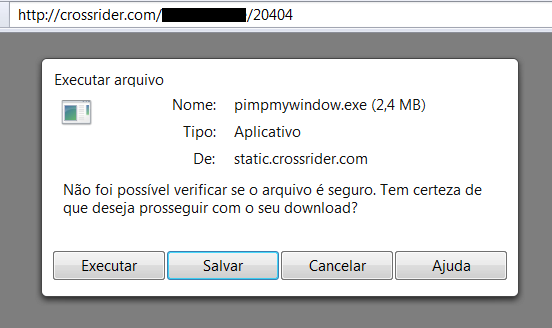
The entire malicious scheme used by this piece of adware is based on Crossrider, a legit platform to create and host multiplatform browser plugins, but used by the authors behind the Lilyjade worm. It shows how Brazilian bad guys are learning new monetization schemes:
Crossrider.com are hosting not only the installer but statistics pages as well
As online banking services are very popular in Brazil, the adware includes a module to display ads in the pages of your bank’s website as well, even if the pages are HTTPS enabled:
Banco do Brasil, Itau and Caixa Bank websites affected by the adware
It seems malicious users in Brazil are concentrating more of their efforts on coming up with different ways to gain money, even using ‘grey’ apps. Maybe it’s a reflection of the new national cybercrime law that makes it a crime to create trojan bankers.
We suggest that infected users remove any extensions called “PimpMyWindow” or “MudeACordoSeuPerfil” from their Google Chrome or Firefox browsers, as they pose a privacy risk. Kaspersky Anti-Virus users are protected; the various versions of this adware are blocked as AdWare.Win32.PimpMyWindow.
Update: Crossrider.com informed us they removed the files of this adware
PimpMyWindow – Brazilian adware
























Sandy Gonzalez
Hello I believe I got a Trojan when I opened the internet and there was some different web page instead of my Google , then there was a system pop up that had “XXX [don’t remember name] System Protector” programme and I click for a free scan, it completed scan. It ask for money. I declined than my Kaspersky showed it was unsafe had a Trojan, so I tried to close and it was downloading all by it self! All my icons on desk top turned white and will not open shows:
System call failed :{26EE0668-A00A-44D7-9371-BEB064C98683}
From my start up menu I can open some apps. outlook 2010, excel
bottom line Kaspersky Pure 3.0 says I have “not-a-virus:HEUR:Ad Ware.Win32.Kranet.heur” options are from Kaspersky 1]. to Delete
2] block or 3.] add to exclusions.
I am going to delete option 1]. please give me feed back? what in the world is this Adware?
Thank You Sandy