
Most spam, especially the sort that is mass-mailed on behalf of businesses, has quite an impersonal format: spammers create a message template for a specific mailing purpose and often drastically diversify the contents of that template. Generally, these kinds of messages do not personally address the recipient and are limited to common phrases such as “Dear Client”. The most that personal data is ever involved is when the name of the mailbox (or part of it) is substituted with the electronic address that the spammer has. Any specifics that may help the recipient ascertain whether the message is addressed personally to him or not, for example, an existing account number, a contract number, or the date of its conclusion, is missing in the message. This impersonality, as a rule, attests toa phishing attempt.
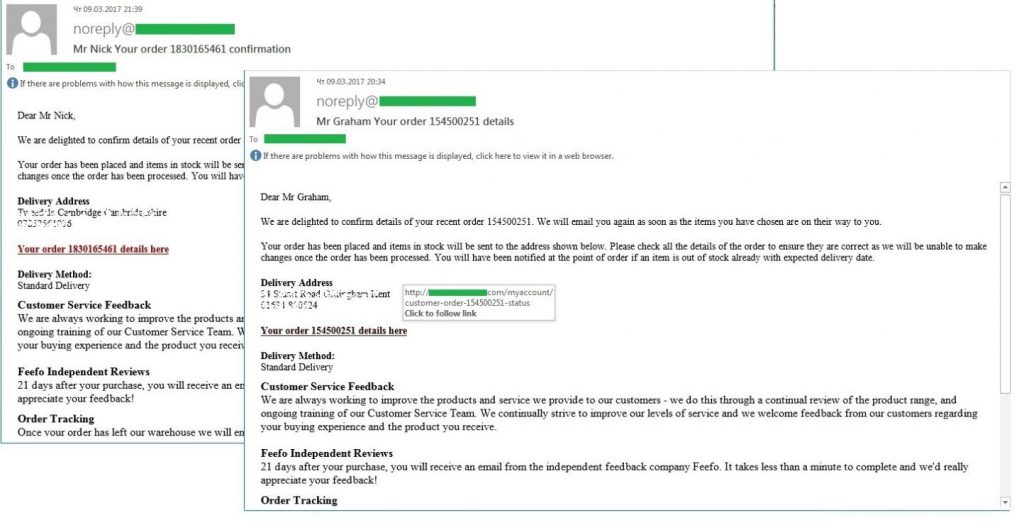
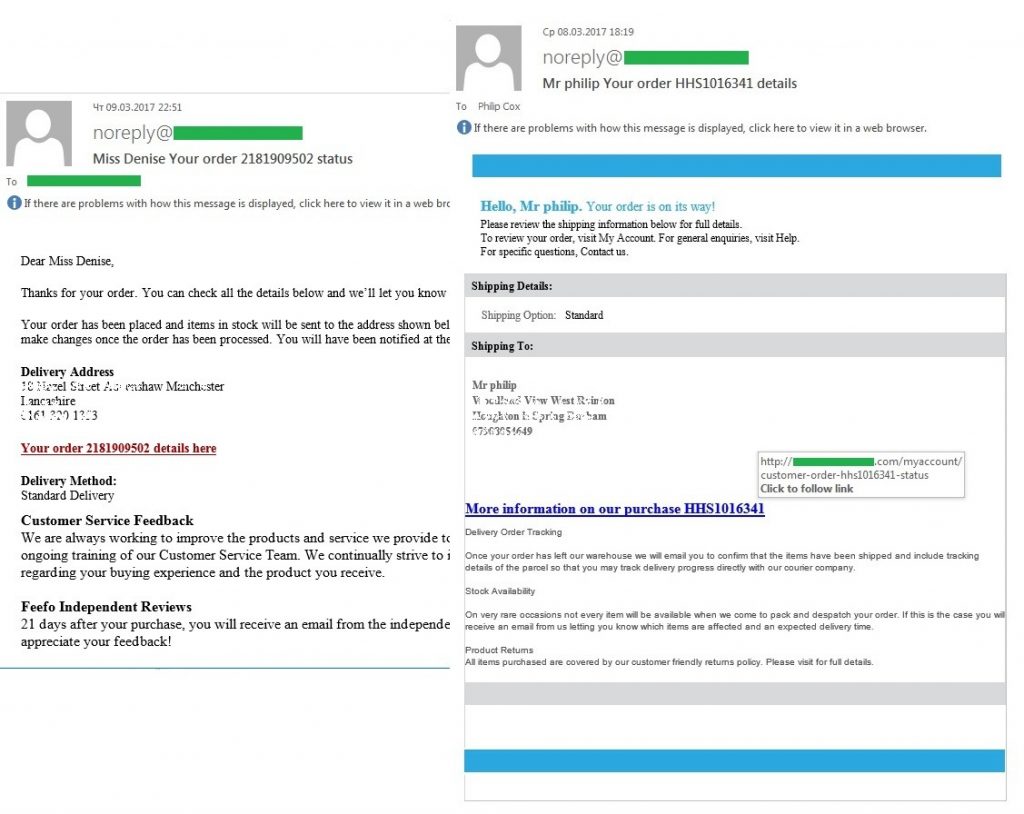
Lately, however, we have been noticing an opposite tendency occurring quite often, wherein fraud becomes personalized and spammers invent new methods to persuade the recipient that the message is addressed personally to him. Thus, in the malicious mailing that we discovered last month, spammers used the actual postal addresses of the recipients in messages to make them seem as credible as possible. This information is sold to evildoers as ready-to-use databases with physical addresses (they are frequently offered for sale in spam messages), collected by evildoers from open sources, or obtained by evildoers when hacking email accounts, for example. Of course, cybercriminals will not have very many of these addresses at their disposal (compared to generated addresses), but they are much more valuable.
The way spammers organize their personalized attacks plays an important role as well. In general, messages are mass mailed on behalf of an existing company, while the technical headers of fake messages use the company’s actual details.
There are several ways to use valid details. The most unsophisticated method is spoofing, which is substitution of technical headers in messages. The headers can be easily placed with any mass mailing program. In particular, during the spoofing process, the “From” field contains the real address of the sender that the fraudsters have. In this case, spam will be mass-mailed on behalf of the spoofed company, which can stain the company’s reputation quite seriously. Yet, not all technical headers can be substituted when spoofing, and good anti-spam filters will not let these messages through.
Another method entails sending spam from so-called hijacked infrastructure, which is much harder to do technically, as the mail server of the target company has to be hacked. After gaining control over it, an evildoer can start sending messages with legitimate technical headers from any email address owned by the company and on behalf of any employee who works there. At the same time, the fake message looks quite credible for anti-spam filters and freely travels from server to server, as all of the necessary certificates and digital signatures in the header correspond to genuine counterparts. This would result in losses by both the recipient, who takes the bait of the evildoers (network infection and theft of personal data or business information), and the company, whose infrastructure is abused by the evildoers.
Usually, cybercriminals select small businesses (with up to several dozen employees) as victims for hacking. Owners of so-called parked domains are of particular interest, as parked domains are used by a company without creating a website on these domains.
In the samples detected by us, personalized malicious spam was mass-mailed on behalf of an existing business that was a small company specialized in staff recruitment. The messages contained order delivery notifications that are typical of malicious spam, but also indicated the real postal addresses of the recipients. The messages also contained URLs that were located on legitimate domains and were constantly changing throughout the mailings. If a user navigates to the URL, then malicious software will be downloaded to the user’s computer.
In this way, we may affirm that spam is becoming more personalized and mailing is becoming targeted. With the rising digital literacy of users, this is exactly what evildoers rely upon; It is not so easy to remember all your subscriptions, all your online orders, or where you’ve left your personal data, including addresses. Such an information load calls for the use of smart security solutions and the employment of security measures to protect your “information-driven personality”.
Personalized Spam and Phishing






















Grant Kirkbrigfht
I am sick to death with getting emails with my name stating that I have won a prize. I do nont know where they have received my details from, however I am absolutely fed up with receiving this crap. I wish I was able to stop them, however it is not always easy to trace.
TA
So how do you stop these companies from sending there inappropriate email to your email. Even though you have unsubscribe and unsubscribe and unsubscribe numerous numerous of times they still send those inappropriate email how can you block it off your smartphone anxious to find out