
In developed countries, bank cards are very popular. Consumers don’t have to lug around wads of cash when they can opt for a slim piece of plastic that replaces a heavy purse or wallet. Just as on the High Street, Internet users also enjoy the advantages of flashing the plastic. It’s increasingly convenient to use credit and debit cards for online shopping, making hotel reservations, renting cars, and buying airline tickets online.
The list of online banking services often covers all the services available at brick-and-mortar locations. It’s handy to be able to use these services without even leaving the house, to manage your accounts, and conduct all manner of transactions and wire transfers, and even open and close deposit accounts or buy or sell foreign currency.
But there is another side, as well. Where once a pickpocket might be eying up a bulging wallet, today’s equivalent is keen to pinch the plastic. Whenever a cardholder makes an online payment or checks an Internet bank account, that risk is lurking in the background. After all, to do these things means entering confidential data on the store or bank’s website: first and last name, address, telephone number, and credit card details. If this information falls into the hands of malicious users, the cardholder could see his account cleaned out. There are also no small number of fraudulent online stores offering a wide selection of goods; but in the best case scenario, you won’t get what you pay for; in the worst case, you’ll lose all the money on your card.
What should you do to protect yourself and avoid the pitfalls of online scams? What rules should you follow when shopping online or conducting other business with bank cards on the Internet? This article will outline how you can keep it safe when making online payments.
Online shopping
Internet users need to be careful at all stages of making a purchase on the Internet. So what exactly should you pay attention to?
Using special cards for online shopping
First and foremost, if you don’t want to fall victim to online scammers and have your bank account cleaned out, you should take extra measures and get a separate plastic card to use especially for online transactions. You can keep smaller amounts of cash on such a card. Even if the card is stolen, cyber thieves will not be able to get their hands on all your money. You can also top-up your account directly before each purchase and arrange a maximum weekly withdrawal limit with your bank.
Choosing an online store
After deciding to buy something online, potential buyers should set about searching for and selecting an online store. It’s always best to do your online shopping at well known and highly recommended online resources. If for whatever reason that is not an option, then proceed with caution: scammers are constantly coming up with new tricks to fool consumers. Below we will identify some of the things you should look for.
The website’s appearance
When searching for an online store, there is always a risk that you might end up on a fraudulent website. Since fraudulent sites are usually short-lived, in Russia malicious users often do not spend a lot of time or effort on the design of their fake websites. Fake sites may look unprofessional and have bugs (i.e., links don’t work, fonts are inconsistent, the text is poorly formatted, etc.) and some tabs and websites may not even function properly or result in error messages.
Information about the store
If you don’t know anything about the online store and if you have any doubts at all about its legitimacy, you absolutely must do an online search to find out more information about it. You can look for reviews of the store with key words such as “[the shop’s name] reviews” or “[the shop’s name] scams fraud.” If the store is not an honest operation, then there will certainly be victims who have posted their complaints on the Internet. Also look to see if the shop has any contact phone numbers, a physical mailing address, and bank details available. This information should also be checked, using a search engine if need be. If you are in any doubt, the best thing to do would be to find a different online store you can trust.
Information about the domain
Pay attention to the store’s URL. Legitimate, self-respecting stores and payment systems will not have suspicious addresses such as www.ds3a1000r1sad.isd3.com. Online stores that are registered with free hosting services (such as narod.ru, freehosting.com, etc.) should also be treated with suspicion.
If the store’s Internet address looks suspicious, you can find out who registered the domain name, and how long it has been up.
You can find and review the registration information about the domain of an unknown online store using one of the many available whois services — special websites that make domain registration information available. All you have to do is navigate to one of these services (which are easy to find via online searches) and enter the domain name in the search field.
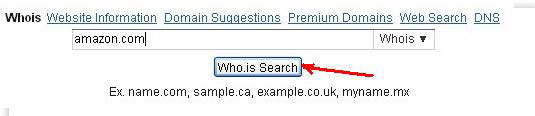
Note the domain’s registrant, and how long the domain has been operating.
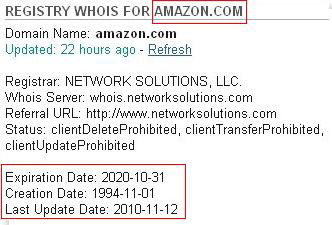
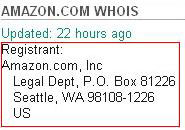
The domain of an online store registered as a legal entity should be more reliable than a domain where the registrant is a private individual. There are cases in which the registrant’s name is hidden and simply listed as “private person” or “DOMAIN WHOIS PROTECTION SERVICE”, and that means that the registrant did not wish to disclose his personal data and opted for this service during registration. It would be surprising to find this in the whois data for large or well-known online shops.
The longer a domain has been active, the better. Typically, fraudulent stores shut down quickly and aren’t registered for a long period of time. If the domain has been operating for longer than one year, then the chances are it will be reliable.
Secure connections
Once you have found an acceptable online store and selected the item you want to purchase, you will need to process and pay for your order. In order to prevent malicious users from intercepting your confidential user data entered on the online store’s website, the data must be sent in encrypted form.
There is a special cryptographic secure SSL (Secure Sockets Layer) protocol designed to encrypt data flows exchanged between the client and the server. The need for secure SSL connections led to the development of the HTTPS protocol, which is an encrypted HTTP protocol that supports encryption. It is designed to ensure protection against attacks launched from tracking network connections. HTTPS is used by the majority of legitimate websites to protect user-entered confidential data when it is transferred to the server.
The first thing that you should look for before entering your private data is the letter ‘S’ in the Internet address, i.e., “HTTPS“. A server address with a secure connection should look like this: https://www.online-shop.com.
However, the mere presence of the ‘S’ in HTTPS in the URL is not enough to be fully confident in a website’s security. Each website that uses the SSL protocol should have a digital certificate issued with a signature from a certification authority, i.e., an electronic document that identifies the owner. This certificate guarantees that:
- the website has been verified by a certification authority;
- the connection is secured by a cryptographic algorithm;
- the company that registered the website actually exists;
- the website belongs to the organization to which the certificate was issued.
You can tell if a website has a certificate with a currently valid signature from a legitimate, authorized center if there is a little lock icon in the address field or the browser status field (on the bottom of the browser window). The little lock will look different depending on the browser and version, and the browser customizations and other browser plug-ins.
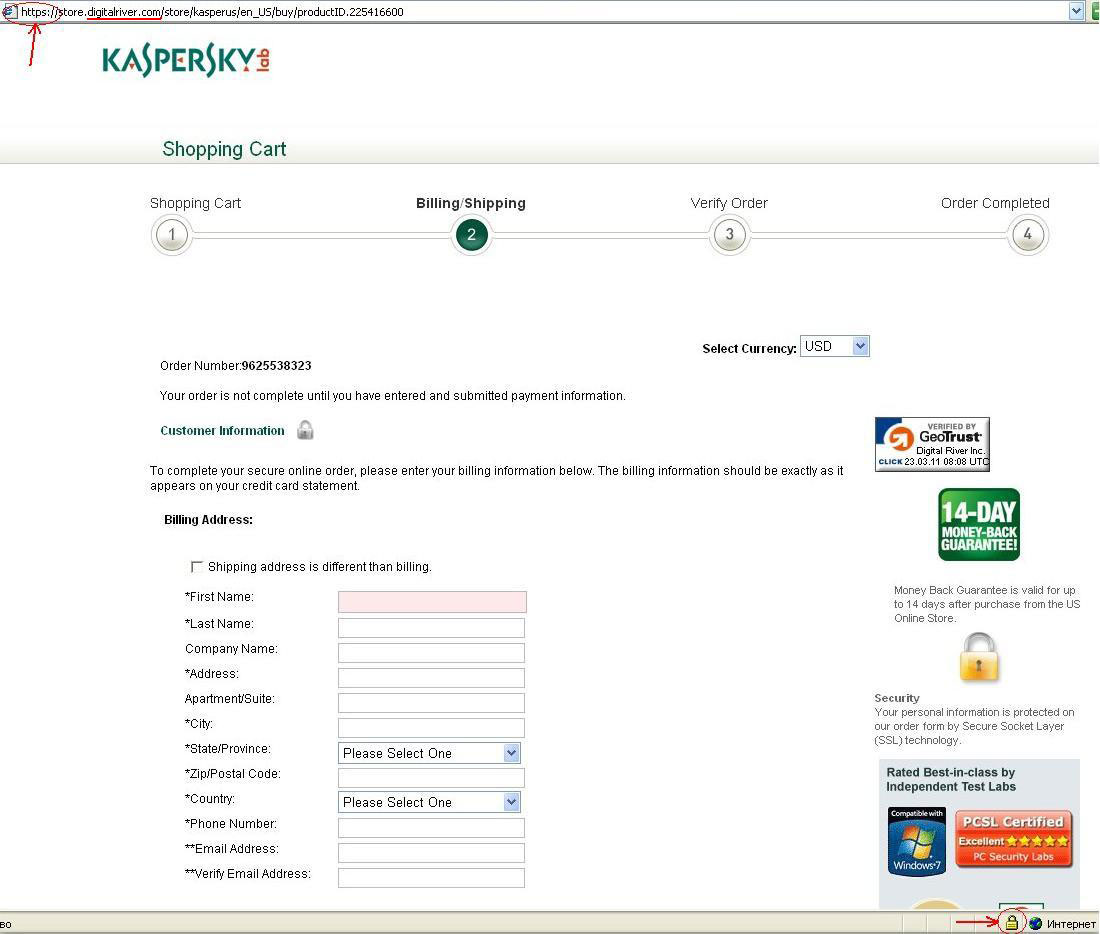
A secure connection in Internet Explorer

A secure connection in Google Chrome 3

A secure connection in Opera 10
The presence of https in the address and the authentication certificate are the most important indicators of a website’s legitimacy. One cannot say a website is truly secure if the address has https but there is no authentication certificate.
Often, scammers will attempt to confuse Internet users by adding images of a little “security lock” on a page that does not in fact have an authentication certificate. It is important to remember that the closed lock icon confirming the existence of a certificate will only be found in the URL field, and if you double-click on it, you should be able to see the certificate data.
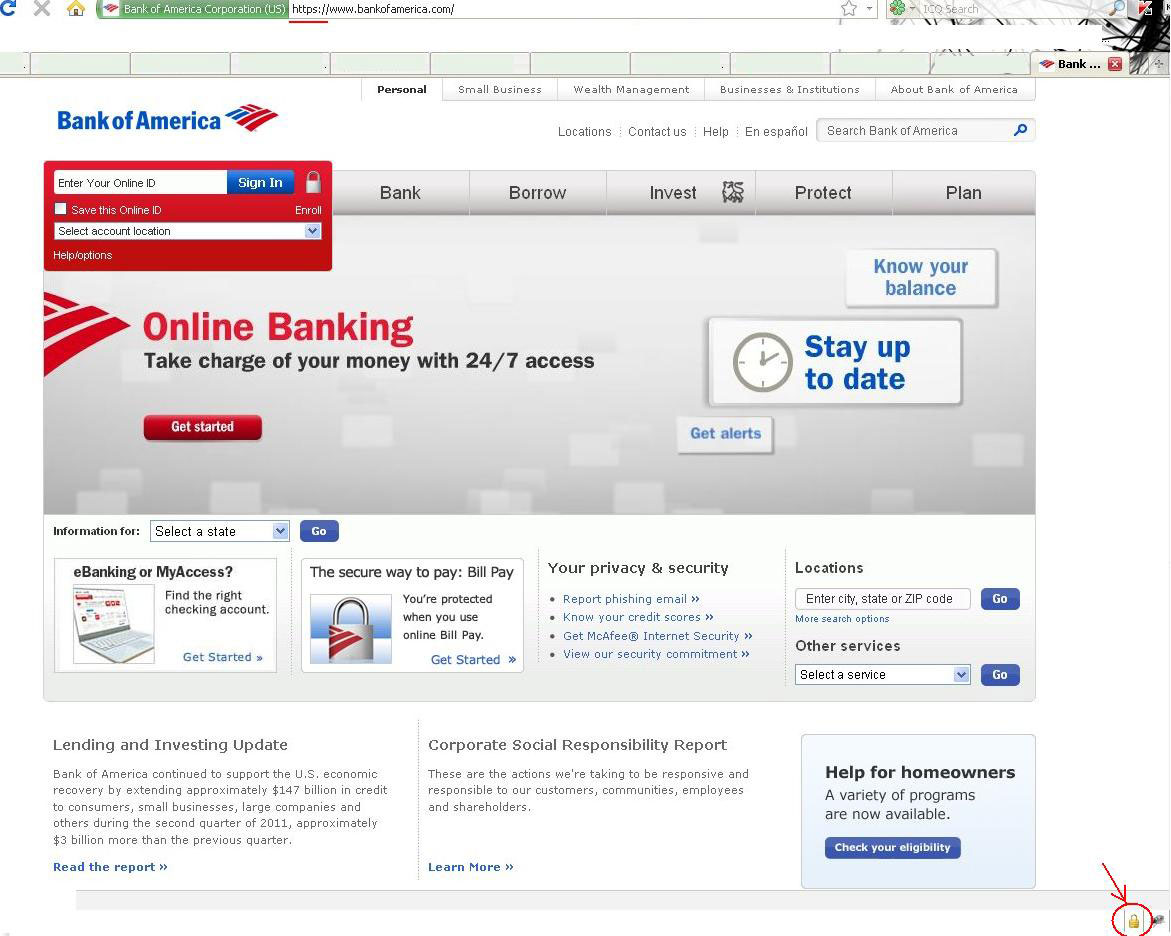
An example of a bank’s website with a secure https connection
Below you can see some examples of fraudulent websites. Links to these sites are spread via spam emails. In the screenshots, you can clearly see that the website’s address starts with http, which means that the connection is not secure, even though the text on the site tries to assure visitors it is. The images of locks on these sites are just that — images. They are not authentication certificates, and do not indicate any secure SSL connection. These sites are not secure.
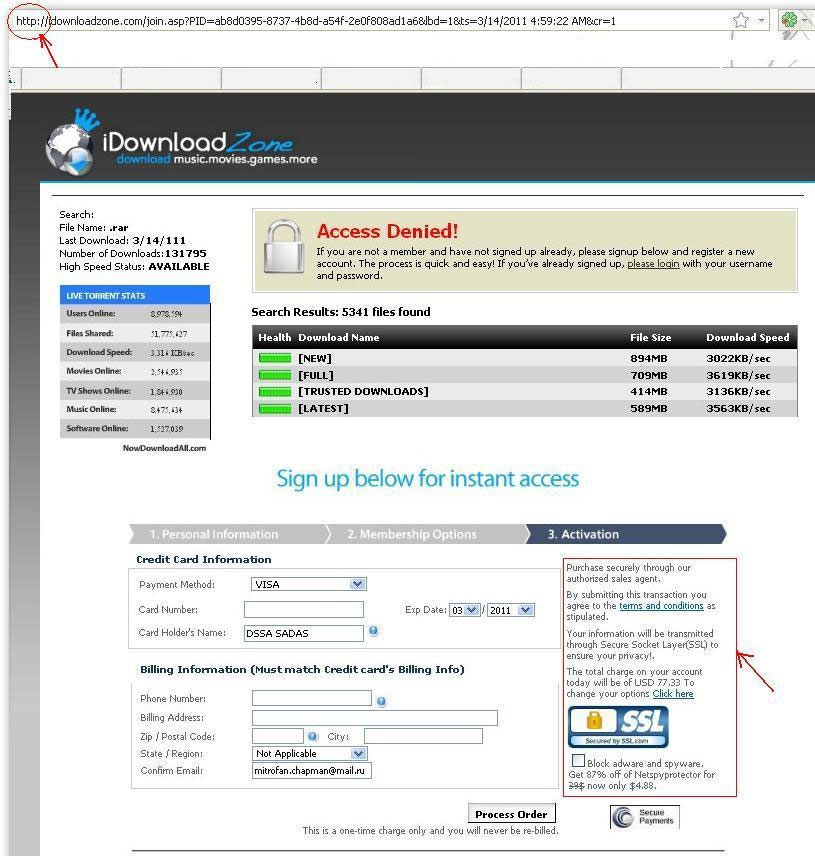
Fraudulent online store websites
Authentication certificates
It is important to verify the legitimacy of an authentication certificate — unfortunately, scammers have figured out how to use authentic certificates. There are plenty of loopholes for “true professionals”. For example, malicious users can steal certificates, or obtain a certificate from a certification authority for another website and use it for attacks. Furthermore, they can create their own certificates and provide their own signatures — so-called self-signed certificates.
A website’s authentication certificate can be verified by clicking on the security lock symbol. The important thing to note is the name of the authorization center, i.e., who issued the certificate (for example, the most well-known and trusted certification centers are Geotrust, Twante Consulting, and Verisign), to whom the certificate was issued, and for how long the certificate is valid.
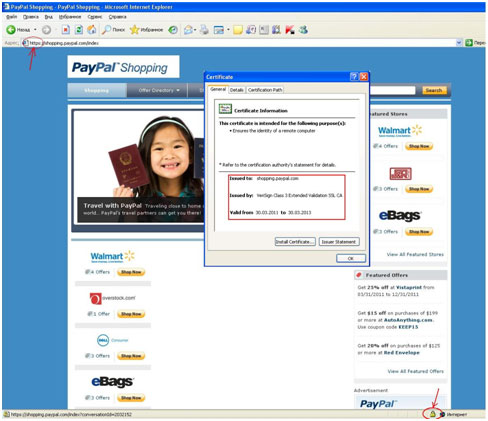
A certificate signed by a trusted center (in Internet Explorer)
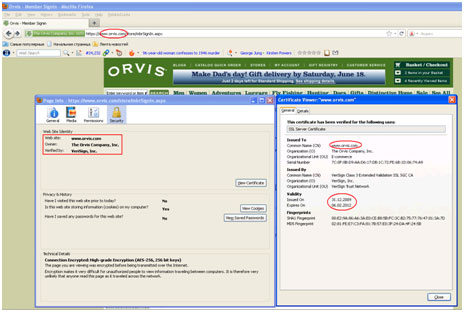
A legitimate digital certificate (in Firefox)
If you have found that:
- the domain for which the certificate was issued does not match the website’s domain,
- the term for which the certificate was issued has already expired,
then the certificate is most likely fraudulent.
Modern browsers feature a built-in security system. The list of root certificate centers has been entered into the browser by developers. The browser will find a certificate to be authentic only if the certification center that issued it is on a list of trusted organizations written into the browser or if a certificate was issued by a partner company of one of the allowlisted certification centers. If the website has https but does not have a certificate, or the certificate was issued by an organization that is not on the list of trusted sources, or if the certificate is expired, then the browser will alert the user.
If the connection on a page where a user is meant to enter confidential data is not secure, we recommend that you select a different online store to make your purchase.
Payment
Buyers often have a choice between processing payments using the store’s own payment form or taking advantage of another payment system (PayPal, payonlinesystem, WebMoney, YandexDengi, and others). If you do not completely trust the online store or the company that issued the certificate, you can opt to use a service that you trust more. This does not completely protect you against scammers, but it does keep your personal data safe and protects you against greater losses.
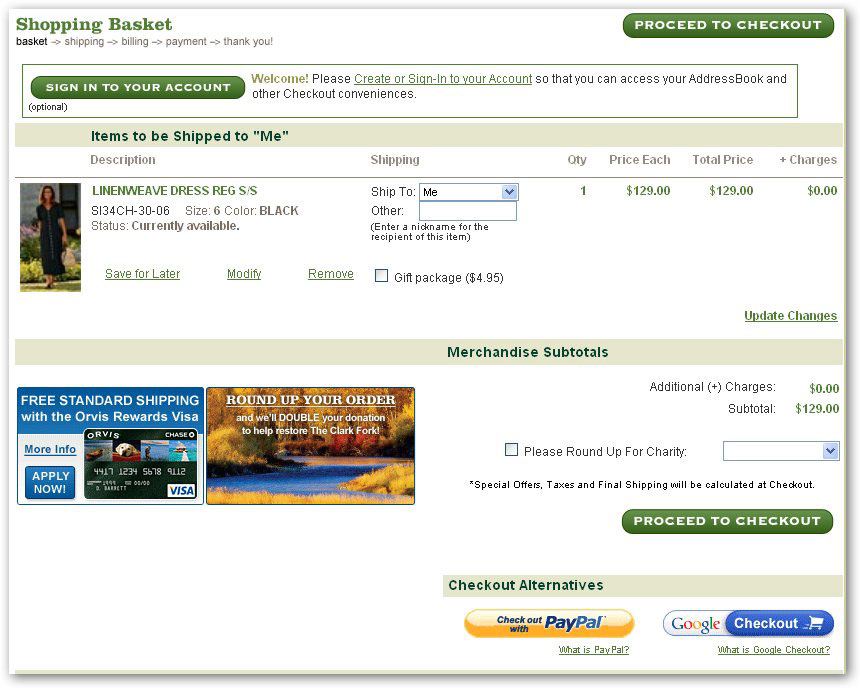
The website of an online store offering customers the option to select a payment method
After redirecting to the page where you enter your card information, it is very important to take a careful look at the URL. If you have decided to pay using one of the available payment services, such as Paysystem.com, and clicked on the link to do so, but the URL shows something slightly different from the official address (such as PaysiPaysi stem.com), or if the connection is not protected with HTTPS, then you have most likely been redirected to a fraudulent website. Needless to say, do not, under any circumstances, enter your personal data!
Chargeback
There are cases in which stores accept only 100% prepayment for an item and then disappear into thin air without shipping anything at all. If you end up in this situation, don’t lose hope: you have the right to conduct a chargeback.
A chargeback is a means of refunding a buyer’s money from the seller’s account when the buyer has submitted sufficient evidence to show that the transaction was invalid or fraudulent. The non-receipt of a purchased item or a difference in quality from that which was stated are sufficient reasons for a cash refund. Visit the bank which issued the card, and your bank should conduct an investigation into the disputed transaction (where the purchase was made, at what time, from what account money was withdrawn, the item that was purchased) and typically, the money will be refunded to your card within 30 days.
Banking transactions on the Internet
Unfortunately, money can be lost from actions other than purchases. If you are the client of a bank and you use online banking services, you also need to proceed with caution to avoid the traps set by cybercriminals.
The tactics of malicious users
Cybercriminals on the hunt for the details of Internet users’ plastic cards have an entire arsenal of tactics and resources. We will address some of these below.
Phishing
Do not follow a link to a bank or payment system sent in an email or through a social network, even if the message was received from the bank, the payment system, or another organization. In this case, the probability is high that it is in fact a so-called phishing site.
Phishing is a type of Internet fraud involving the mass mailing of emails in the name of financial organizations, banks, postal services, etc., and which contain links that lead to fake sites that are designed to look like the official websites of the company that the phishers are impersonating. The phishers’ primary objective is to steal confidential data (usernames, passwords to accounts, and credit card information) and use it to make money.
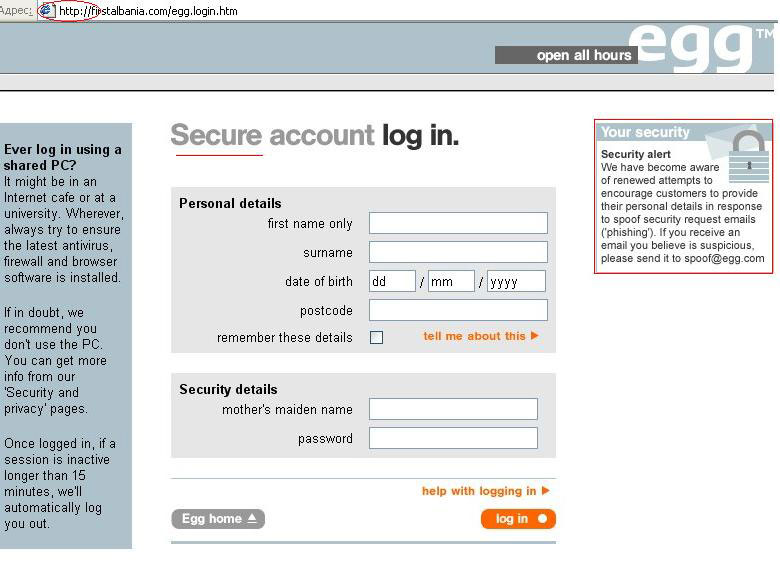
A phishing webpage designed to look like the website of Egg bank
Sometimes the link in a phishing email will look different from the address of the website to which it actually leads:
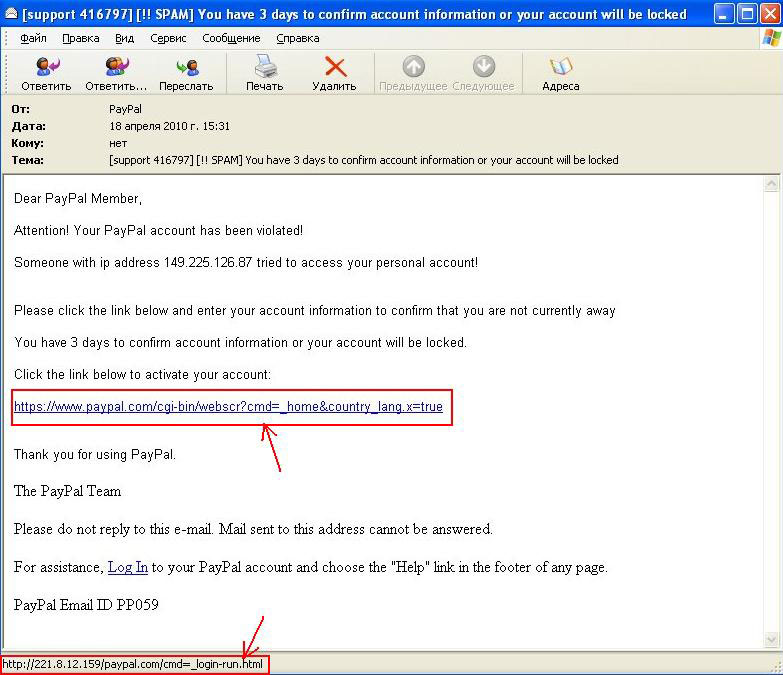
An example of a phishing email
Links to phishing websites can spread through social networks and instant messaging services, not just email. They can even spread through messages sent from friends. It’s also possible to end up on a phishing site if you click on a banner ad on suspicious websites or links in pop-up windows.
If a user falls for the phisher’s bait and enters his personal data on a fraudulent website, that information will get into the hands of malicious users. This is the main method that is used to obtain users’ data. However, phishers may also use Trojans planted in email attachments with forms that ask users to fill in personal data or emails with requests to send back data in an email.
Remember, banks and other financial organizations will never send emails with requests for you to send them your personal data or to go online to go through authorization, and they will never ask you to enter personal data in pop-up windows.
For more information about phishing and how to protect yourself against it, refer to our article here.
Pharming
Pharming is the process of redirecting users without their knowledge to a different IP address using an altered system hosts file. As a rule, the hosts file contains only one string: “127.0.0.1 localhost.” However, malware can add other alphanumeric strings to the hosts file and IP addresses of sites chosen by malicious users, including popular online stores. Instead of sending a user to the proper IP address, it will redirect to a fraudulent IP. Users of infected computers who enter the addresses of these sites will end up on well-designed counterfeit websites. Furthermore, the URL will look just like the real thing. Any personal data entered on that website will be sent to the malicious users.
You can read more about pharming methods here.
Spyware
Spyware could be installed on a computer (such as keyloggers, which are used to steal passwords, among other things). The risk of disclosing your data is especially high when conducting transactions with bank cards in public spaces (an Internet café, libraries, bars, and restaurants) since computers that can be used by anyone are more vulnerable to infection. This infection can take place accidentally from a “dirty” flash drive, or it can be planned by malicious users in order to harvest confidential data.
Even if you use your own computer on a public Wi-Fi network, you can never be sure that your personal data is safe from third parties, especially if the network is not secured with a password.
Based on the above, usernames and passwords can be stolen using the following methods:
- absolutely all keystrokes are intercepted when the computer is on;
- keystrokes used to enter usernames and passwords for online stores and other websites that require authorization are intercepted;
- registration data entered in special fields on a bank’s website or the page of an online store is recorded;
- HTTP requests from a browser to the bank are intercepted in order to obtain the username and password;
- a bank’s official website will be substituted with a phishing website.
Protecting bank clients
In order to protect its clients against scammers, banks use a variety of security approaches. Typically, online banks use two passwords — the first is for entering the system and viewing an account balance, and the second is required to conduct any payments or other transactions. There is also a system that uses a one-time password that changes each time it is required, and the bank sends that password to the user’s cell phone. These types of passwords are active for 30 minutes. The next login to the system will require a new password. These are relatively difficult to intercept. Some banks provide clients with a list of one-time passwords for the sake of convenience, or in the form of a plastic card with shaded fields. Often, banks issue clients keys, or “tokens” which look like a keychain and will provide a one-time password at a user’s request. These passwords provide additional security when authorizing other user actions as well. Some banks offer special programs that have to be installed on a user’s computer via which online banking services can be used (instead of visiting a bank’s website on the Internet). The use of these programs for transactions reduces the probability that a user will end up on a fraudulent website. But, of course, all online banking transactions should be made via a secure SSL protocol connection (where the URL includes HTTPS, and the browser’s status bar or the URL field shows a secure lock icon).
How to protect your assets
What can attentive users of online banking services do in order to protect their money?
Be deliberate and careful when selecting your password. Choose a complex alpha-numeric combination for online banking, and be sure to use both uppercase and lowercase letters. Save your password and PIN in places that are not accessible to others. When entering your confidential data, use a virtual keyboard. Many banks offer a virtual keyboard for their online services and this means a keylogger cannot track the data. Another method is to use the products of leading antivirus companies. That will help minimize the risk of interception of your information by keyloggers.
When performing online transactions, you can use a so-called ‘sandbox’, which is included in many antivirus solutions, and helps minimize the risk of confidential data being intercepted.
The term sandbox was borrowed from firefighters, who use it to refer to a box of sand designed to work safely with highly flammable materials. The antivirus sandbox serves the same purpose. It provides an isolated environment in which any program or website can be launched without any threat to the rest of the system, and in this mode, the system is protected against any changes, including potentially threatening modifications. For example, if you switch on the safe review of websites in Kaspersky Internet Security, all modifications (saving of cookies, browser history, etc.) remain within a safe environment and are isolated from the operating system, meaning they cannot be intercepted by malicious users. Another option is to turn on the control features for access to online banking services, which can automatically identify bank websites. The solutions offered by other developers work along the same principles.
Monitor the activity on your accounts. These days, many banks offer an extremely useful service informing their clients of all transactions made with their cards via text message. If a withdrawal is made from a card, the client receives a message informing him. If a withdrawal is made without your knowledge, you can get in touch with your bank to block your account immediately. When opening accounts and obtaining your bank card, you can also agree on a daily maximum withdrawal amount. This way, you can be sure that scammers will not be able to empty your account.
How to protect your money online: basic rules
Don’t become a victim of malicious users! Follow these rules whenever you use online shopping or banking services.
- Use a special card for online purchases and keep a limited amount of money on that card.
- Do not visit sites by clicking on links in emails, messages on social network sites or chatrooms or clicking on banner ads on suspicious websites. Do not click on any links sent by people you do not know.
- Before making a purchase online, read reviews about the store you plan to use.
- Avoid stores registered with free hosting services.
- If a store’s website gives rise to any doubts at all, use a whois service to find out more information about the domain, how long it has been in use, and its owner. Note the period of time for which the domain has been paid.
- Enter the URL of a bank or payment system by hand instead of clicking on links.
- Financial organizations never send emails asking you to send them your personal data in an email, visit their site for authorization or enter your personal data in pop-up windows. Do not go to any website by following a link that you receive from a banking organization or payment system.
- Look carefully at the address of the pages you visit that have fields for entering confidential data. If the URL is made up of a random selection of letters and numbers or looks suspicious at all, do not fill anything out.
- Make sure that you are using an encrypted connection when sending any confidential data. If a connection is secure, the URL will start with https, and the address bar or the browser’s status bar will display a small lock icon.
- When you click on the lock icon, look closely at the information about the SSL authentication certificate issued to the site (when, by whom, and for what period of time it was issued).
- Try to avoid using online banking services or online shopping in public areas (Internet cafes, clubs, and libraries). These computers may have a variety of spyware programs running on then that can track and log keystrokes and intercept Internet traffic. Even if you use your own computer but are conducting online banking transactions on a free, public Wi-Fi network, there is a risk that the traffic might be intercepted by the network’s admin, other third parties, and that attacks might be launched with network worms, especially if the Wi-Fi network is not password protected.
- Always keep your operating system and antivirus software updated. The best way to protect yourself is to install the latest updates and patches for your operating system, spam filters, firewalls, and keep the latest versions of antivirus and anti-spyware programs with updated databases. For additional security, you can also install a firewall (the same as a standard firewall, only maintained with a special device that performs the function of a software firewall). To enhance protection, application and software-based firewalls can interact with one another as both have their own pros and cons.
Last, but not least: don’t be afraid to shop online or to use online banking services. Just be careful and follow these basic steps, and you will be able to safely and conveniently take advantage of everything the Internet has to offer.
Online shopping made safe and convenient





















J Pollard
Liked your article. One puzzle though, as the security certificate (https lock icon in EV green rectangle) can be spoofed, surely the only absolute security check is by comparing it’s thumbprint/fingerprint with one obtained from a secure site. This cannot, at this time, be duplicated therefore if a comparison of the website fingerprint and one from a secure source do not match then this may indicate the website’s certificate had been spoofed?
I have just subjected your EV Kaspersky Lab ZAO [RU] (securelist.com) to this scrutiny & it checks out OK! 62 4d 93 first 3 , but Barclays Bank uses several certificates (I have found 6) which could mean they are actually able to “read the so called safe HTTPS/ssl/TLS can be monitored and read by Barclays. I would be interested how Kasperky 2014 “Safe Money” deals with this anomally?