
In 2015, the game Clash of Clans was bringing in about 1.5 million dollars per day for its developer, Supercell. Later on, the company launched a new project, Clash Royale, after addressing the flaws of their first game and implementing battles with real players into the new game, which shares the same characters and the same cartoonish design as the first project. Yet, the more popular game is, the higher the probability that fraudsters will be looking to make a fortune on that popularity by, for example, organizing phishing attacks on the player base.
The money-making model for both of the games has been thoroughly thought-out: anyone can play without investing real money. But this would mean putting a lot of effort into the games and losing more often to other players who basically purchase and upgrade either rare and strong cards with extremely low drop rates or battle units and building levels (when talking about Clash of Clans). In this regard, the majority of the game’s players do not have much money but are full of ambition. These players often seek not-so-legal ways to procure and upgrade rare cards to put less effort into winning battles and ranking up to play in the premier leagues.
This has been exploited by fraudsters, who subtly abuse human foibles such as cupidity, love for freebies, and the desire to be the top player. Phishing attacks, though always quite similar in their nature, are very competently planned. Phishing websites are designed with holidays in mind (either New Year’s Eve or Christmas) or are linked to game updates that include additions to the game or changes in the game’s mechanics (new cards, units, balancing, etc.).
Here, for example, is the headline of a phishing website targeted at Clash of Clans players. It was designed specially for New Year’s Eve, and, according to the published description, the developer of the game supposedly gives out New Year’s gifts to players, including game currency, building level upgrades, etc.
The address of the website contains the phrase “eventchristmasandnewyear”, which makes the website look even more credible.
Victims can choose what they want from a list that includes gold, crystals, resources, and building upgrades.
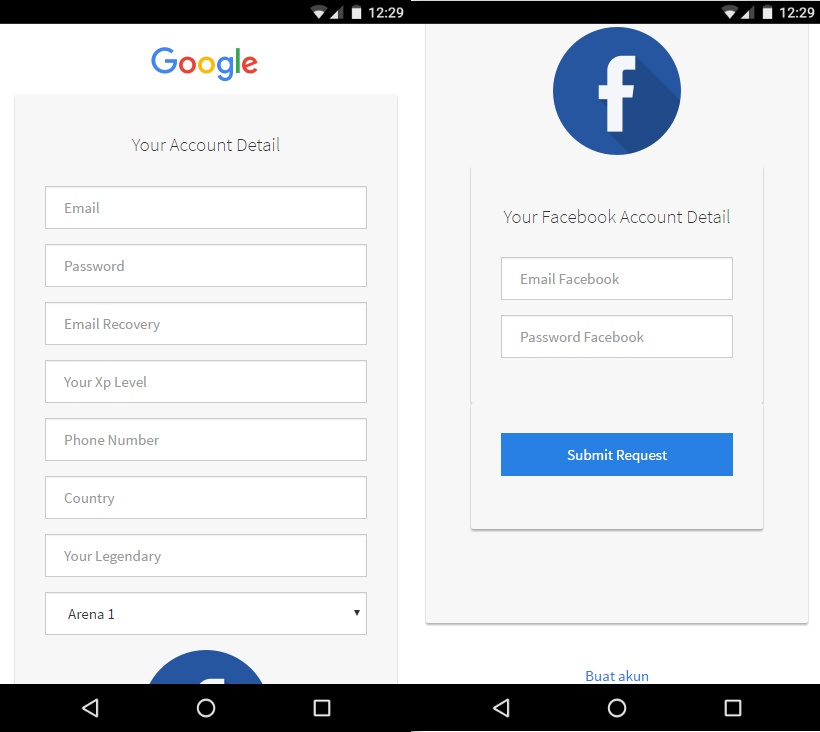
The intention of the fraudsters becomes obvious as early as at the next step, where victims are prompted fill out a form by entering the credentials of their Google and Facebook accounts. After that, these credentials are passed on to the fraudster and the victims are robbed of both of their accounts.
The form created by the fraudsters offers “authorization” with Google and Facebook credentials
Also, fraudsters reacted quickly to the release of the latest updates, which included new battle arenas and legendary cards. On behalf of Supercell, players were offered their choice of one of the “legendaries”, as well as gold and crystals. Of course, in order to obtain these, Google and Facebook credentials were required.
One of their recent releases was “a gift from the developers”, which gives the player the option of selecting their desired hero or resources
Input fields for credentials
After sending the credentials, the victim receives a message to confirm their registration. It can be assumed that the evildoers may need this to ascertain the authenticity of the user-specified credentials.
To avoid falling victim to this fraudulent scheme, it is a good idea to follow these simple rules: do not use any links from social network groups, especially if the groups are not official, or from e-mail messages received from unknown users, even though they may promise you progress in the game or imminent profit. It certainly couldn’t hurt to install good security software that features anti-phishing functionality with database updates on malicious and phishing links that cover every subject. If the “free lunch” being offered proves to be too tempting, then go to the game developer’s official website and verify whether the holiday offer is genuine.
























Clash of Greed