
Whenever we discuss the most active malware-producing countries, Russia, China and Brazil are always atop the list. But there’s a new country that’s starting to appear in the top five:Mexico
In our monthly Latin America malware analysis published on https://securelist.lat/ and Threatpost (both in Spanish),we already mentioned that Mexico is known for producing local botnets.
On Aug 21, we (Kaspersky Lab) detected a new instant messenger worm that spreads through almost all well-known IM programs, including Skype, GTalk, Yahoo Messenger and Live MSN Messenger. The name of the threat is “IM-Worm.Win32.Zeroll.a”
It “speaks” 13 different languages (including Spanish and Portuguese) according to the local language of the infected
Windows computer. There are some characteristics that show the worm originated Mexico. It is written in VB and the C&C is located on an IRC channel (an old botnet technique recycled by the Mexican coders).
Our statistics based on the KSN data show the biggest infections were registered in Mexico and Brazil.
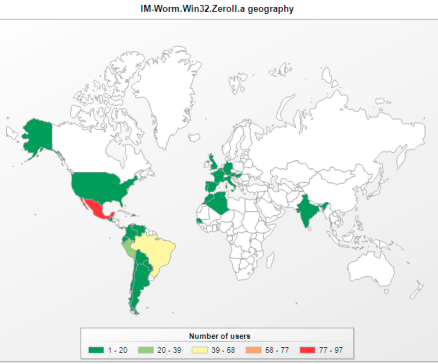
It seems like the criminals behind the worm are now at the first stage of the crime — infecting as many machines as they can to have “a good” offers after to another criminals: pay per install, spam and others.
It’s worth mentioning that only three anti-virus programs (including Kaspersky) detect the threat.





















New IM Worm Squirming in Latin America