
Money mule recruitment emails are nothing new, for years these have been spammed out all over the globe. What is new though is the recent wave aimed at “English-speaking Japanese residents”. It started at the end of July and we have received hundreds of such themed spam emails since then.
The content typically promises an easy job, just requiring some hours per week with very few other requirements.
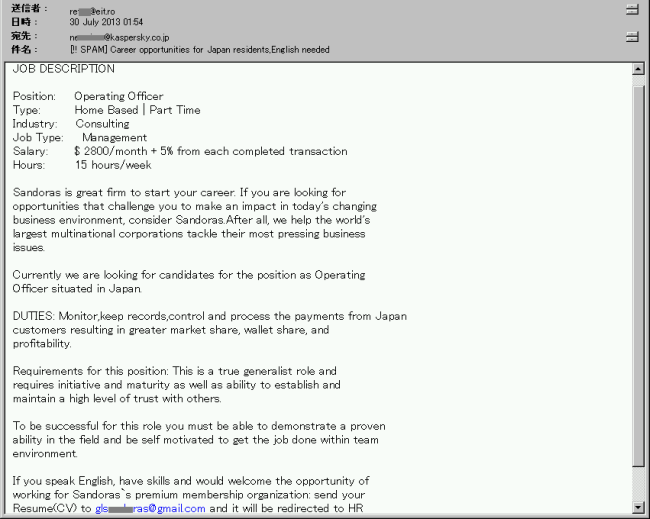
Probably this spam wave has not been too successful. One explanation lies in the fact that many Japanese people I know will simply trash English emails IF they are not commonly working with them. Also, as in our case, most of these emails are filtered and placed in the trashcan by security software already. Another reason may be that Japanese who indeed speak English are also smart enough to smell something phishy here.
And speaking of phishy … actually phishing and money mules are closely related. The phishers steal login information for online banking accounts and that’s it. The gathered information is then sold to the next team of criminals, the money mule recruiters. Their job is to “cash out” the stolen accounts.
What happened near the end of August was the first _ever_(?) appearance of money mule recruitment emails in the Japanese language. In the email, a person named “Martin” explains briefly about this new job opening with rewards of ~600.000 Yen. All the emails of this kind came from addresses like “Blah.Blah@outlook.com”.
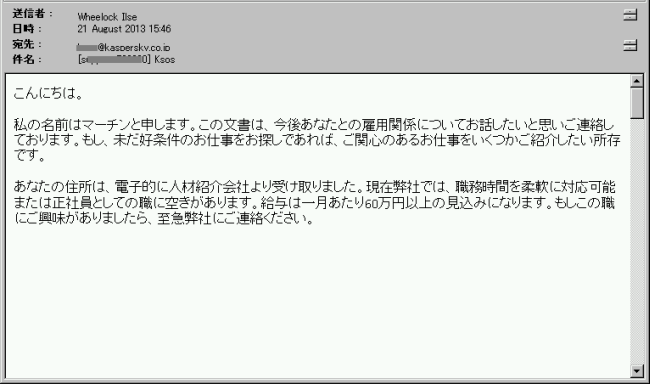
We took the opportunity to reply to some of them (“Please tell me more …”) in order to observe what would happen.
It didn’t take too long until we got replies – an email from a “Martin” as well, but from a totally different email address of a “consulting” company supposedly based in Sweden. From the email headers we concluded that the two servers used to send emails are located in Russia. One of the domains is registered to (what looks like) a person in Italy, the other one in the US.
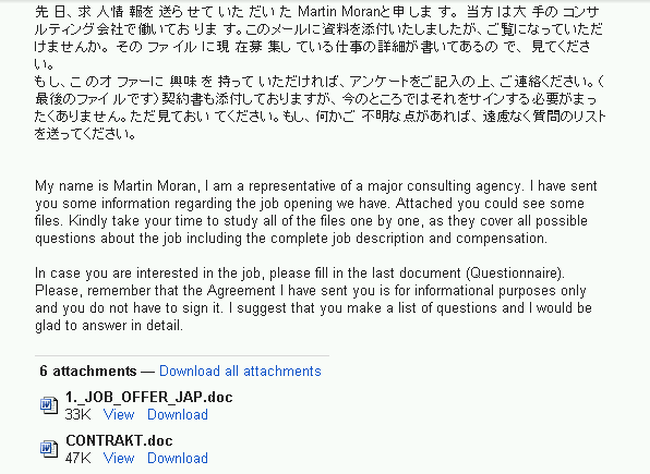
Now the content was even bilingual and the attached data contained a “Contrakt” (sic) and some other papers explaining how this whole project is supposed to work. Next we created some nonsense questions for a reply which led to some email Ping-Pong, enabling us to collect more details of the sender(s). This “employer” advised us to create a new bank account (“Preferences: Resonabank, Sevenbank,Shinseibank …”) and included another attachment for filling in our bank information.
And this is as far as we could go because the next step would have been to receive (stolen) money to that account with the final purpose of forwarding about 90% of the received money via wire transfer and keeping the remaining sum as our fee.

We can only advise everyone to ignore approaches of this kind; being a money mule is not fun, but a very serious crime and a quick ticket to the police station.

















Mule Flood in Japan