
October in figures
The following statistics were compiled in October using data collected from computers running Kaspersky Lab products:
- 161,003,697 network attacks were blocked;
- 72,207,273 web-borne infections were prevented;
- 205,822,404 malicious programs were detected and neutralized on user computers;
- 80,900,079 heuristic verdicts were registered.
The cybercriminals’ new bag of tricks
Duqu – the new Stuxnet
The month’s top story was the detection of the Duqu Trojan and its apparent connection with Stuxnet, the first well-known example of a cyber-weapon. Experts at Hungary’s Crysys research lab found numerous similarities in the coding of Duqu and Stuxnet. These striking parallels suggest that they were both written by the same group of people, or that the Stuxnet source code was used. Despite many rumors to the contrary, the Stuxnet code has not been made publically available.
Unlike Stuxnet, which contained code capable of modifying the operation of high-frequency convertor drives and allegedly targeted a uranium enrichment plant in Iran, Duqu contains no functionality targeting industrial systems. When the first recorded incident was investigated in Hungary, Duqu files were found to include a main module which ensured the Trojan functioned properly and established contact with the command server. The files also included an additional Trojan-Spy module. This module was capable of intercepting data entered via the keyboard, capturing screenshots, gathering information about the system etc. The stolen data could then be sent to the Trojan’s command server, located at that time in India. With industrial espionage – rather than Stuxnet-style industrial sabotage – clearly its main aim, a whole host of questions suddenly arose as to the true purpose of Duqu.
During their research, the experts at Kaspersky Lab not only managed to identify new Duqu victims, primarily in Iran (once again echoing the parallels with Stuxnet), but also to find new and previously unknown Duqu files. This confirms our suspicions that the people behind Duqu are continuing their activity, and their attacks (unlike the mass infections by Stuxnet) target carefully selected victims. Moreover, a unique set of files is used for every targeted attack. It is also possible that other modules are used, and not just a Trojan-Spy but modules with a range of other functions.
Our research is ongoing and we hope that our next report will be able to offer a more detailed insight into Duqu.
Attacks on individual users
Bundestrojan: permissible limits
A major scandal erupted in Germany in October following the discovery of a backdoor used by the German police to intercept voice traffic and messages from suspects’ computers. There was an outcry not only because five federal states confirmed the use of the Trojan but also because the country’s federal laws only allow law enforcement agencies to intercept suspects’ Skype traffic, while the Trojan was capable of spying on many other types of programs.
An investigation by Chaos Computer Club, a German hacker community, which later involved experts from Kaspersky Lab’s German office, revealed that Backdoor.Win32.R2D2 (also known as “0zapftis”) not only intercepted messages in Skype but also the most popular browsers, various instant messenger services and VoIP programs: ICQ, MSN Messenger, Low-Rate Voip, paltalk, SimpPro, sipgate X-Lite, VoipBuster and Yahoo! Messenger. It was also found that the backdoor was capable of working on 64-bit versions of Windows.
The Trojan at the center of the scandal was installed on a suspect’s computer by the police during an examination at Munich airport. Documents that subsequently appeared on WikiLeaks suggest that the German company DigiTask was entrusted with developing the Trojan at an estimated cost of over 2 million euros.
This case once again raises questions about the existence of so-called governmental Trojan programs and the legal issues associated with their use. It is worth stressing here that our company, like most other antivirus vendors, takes a firm stance on such questions: we detect, and will continue to detect, all malicious programs regardless of who developed them and why.
Mobile threats: Android leads the way
Statistics
October also saw some major incidents in the world of mobile threats. According to our statistics, the total number of malicious programs for Android has now outstripped that for Java 2 Micro Edition (it had already done so with regards to Symbian by mid-summer). Over the last two years malware for J2ME has been the most prevalent among mobile threats. We’ve written several times about the reasons for this, so won’t go into the details here. However, this dramatic growth suggests that virus writers are likely to concentrate on Android malware – at least for the foreseeable future.
By the close of the month we had detected 1,916 malicious programs for Android belonging to 92 malware families. 1,610 variations from 60 families were detected for J2ME. The following graph shows the breakdown of malicious programs for all mobile platforms:
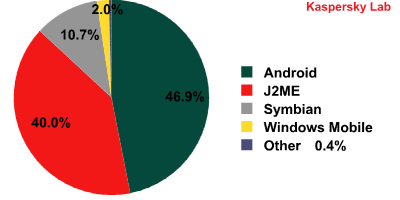
Breakdown of mobile threats by platform
As of the end of October, the total number of mobile threats detected stood at 4,053 variations from 289 families.
Antammi
Unfortunately, malware frequently appears on Android Market. After being notified by Kaspersky Lab in October, the online store removed yet another malicious app which we detected as Trojan-Spy.AndroidOS.Antammi.b. This particular piece of malware was designed for users in Russia.
Users can find a wide range of ringtone apps on Android Market, and while Antammi.b also contains ringtone functionality (users have to send text messages to a paid service to receive tunes), it also steals virtually every bit of personal data it can find on a phone: contacts (copied, for example, to the memory card in the file: /sdcard/bestringtones/contacts.txt), SMS archives, GPS coordinates etc. The malicious program then sends information about its activity to a Gmail address and the stolen data is uploaded to a server.
Antammi.b appeared in the official Android store at the beginning of September and before it was removed more than 5,000 users had downloaded the malicious application.
Mac OS threats: new features
Trojan-Downloader.OSX.Flashfake.d, a new version of the Flashfake Trojan for Mac OS X was detected in mid-October. Like its predecessors, its main function is to download files and it is still masquerading as an Adobe Flash Player installation file. However, functionality has been added that is completely new to OS X malware.
Two years ago Apple added an antivirus protection system to Mac OS X called XProtect that is basically a minimalist signature scanner. Since 31 May 2011, following the MacDefender incident, it has checked for the presence of malware database updates on a daily basis. However, Trojan-Downloader.OSX.Flashfake.d is capable of disabling XProtect by damaging its main files. This prevents the protection system from receiving updates from Apple, rendering it more or less useless. It is possible to disable XProtect because the developers failed to include a self-defense mechanism.
Once Trojan-Downloader.OSX.Flashfake.d has launched on a computer, it not only protects itself from being deleted but also makes the system vulnerable to other malicious programs that would have been detected by the built-in protection system. As a result, this particular Trojan is much more dangerous than other OS X malware.
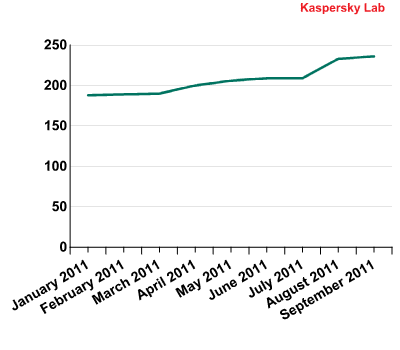
The increasing number of malicious program variations for OS X in 2011
The emergence of new malicious programs for Mac OS X is primarily linked to the increasing popularity of Apple’s computers. Unfortunately, Mac OS X users don’t pay enough attention to security and there are lots of computers out there without antivirus protection. The technology used in the built-in protection system is already outdated, making Apple computers an easy target for virus writers.
Attacks on state and corporate networks
When it came to attacks on corporate and state organizations, October was full of incident.
Japan: in the hackers’ sights
First of all, there are more details about the August attack on Mitsubishi Heavy Industries that we wrote about last month.
The investigation conducted by the Tokyo police revealed that about 50 different malicious programs were found on the 83 computers targeted in the attack. Twenty-eight were detected on one computer alone. It was also found that the infected system was accessed over 300,000 times by the hackers. The search for the source of the attack led to yet another infected computer that belonged to the Society of Japanese Aerospace Companies (SJAC). The hackers used this computer to send malicious emails to Mitsubishi Heavy and Kawasaki Heavy and covered their tracks by accessing the machine at SJAC from an anonymous proxy server in the US. Nevertheless, Japanese experts continue to advance the theory that the hackers hail from China.
Initially it was claimed that no confidential information had been stolen. However, almost a month after the investigation began into the incident, stories appeared in the press stating that the hackers managed to steal data about fighter jets and nuclear power plants.
Japan featured in another incident in October when an attack was detected against members of the country’s lower house of parliament and several diplomatic missions around the world. Thirty-two infected computers were found in parliament and it is highly likely that the hackers gained access to internal documents and all the emails of the affected parliamentarians. Malware was also detected on computers in the Japanese embassies in France, the Netherlands, Myanmar, the US, Canada, China and South Korea. The malicious programs contacted two servers located in China that have already been used in an attack on Google.
The US: new details about old incidents
Another country that is no stranger to cyber attacks is the US. In October, a special hearing in Congress revealed details of several incidents including those linked to the hack of RSA in March. Information was disclosed that claimed several hundred other companies all over the world could have been targeted in similar incidents by the same group of hackers. Here, once again, the finger has been pointed at China.
Details surrounding attacks on two US satellites in 2007 and 2008 were also revealed. It was claimed that hackers interfered with the operations of the two earth-mapping satellites Landsat-7 and Terra AM-1. There was no word on whether the culprits managed to steal any information or disrupt the satellites’ work. US authorities said the satellites did not play a major role in the country’s national security, but the very fact that they were attacked is worrying. In theory, once hackers gain access to a satellite, they could disable it or gain access to the data that it relays back to Earth.
A total of four attacks were recorded, during which the cybercriminals gained access to the satellites’ control systems. It is conjectured that the attacks were made possible after the computer system at a Norwegian satellite station was compromised.
This makes the story of a virus found on the ground control systems of pilotless planes at a US air base seem less dramatic. The Trojan credential stealer was detected in September on a portable hard drive and on the station’s computers which control the unmanned drones. According to a statement by an anonymous source at the US Department of Defense, the Trojan was designed to steal user data for a number of online games and most probably ended up on the air base’s system by accident, and was not part of an attack. Whatever the case may be, the incident is another example of unacceptably lax levels of security, especially at such an important military installation.
October ratings
Top 10 threats on the Internet
| 1 | Malicious URL | 82.47% | 0 |
| 2 | Trojan.Script.Iframer | 2.25% | +1 |
| 3 | Trojan.Win32.Generic | 1.41% | +4 |
| 4 | Trojan.Script.Generic | 1.18% | 0 |
| 5 | Exploit.Script.Generic | 1.03% | +2 |
| 6 | AdWare.Win32.Shopper.il | 0.46% | New |
| 7 | Trojan-Downloader.Script.Generic | 0.46% | +1 |
| 8 | AdWare.Win32.Eorezo.heur | 0.32% | -3 |
| 9 | Trojan.JS.Popupper.aw | 0.27% | New |
| 10 | AdWare.Win32.Shopper.jq | 0.23% | New |
Top 10 sources of malware
| 1 | USA | 25.43% | 0 |
| 2 | Russia | 22.68% | 0 |
| 3 | Germany | 10.46% | 0 |
| 4 | Netherlands | 10.09% | 0 |
| 5 | Ukraine | 7.52% | +1 |
| 6 | United Kingdom | 4.58% | -1 |
| 7 | Virgin Islands, British | 3.86% | +1 |
| 8 | China | 3.35% | -1 |
| 9 | Japan | 1.87% | New |
| 10 | Romania | 1.76% | 0 |
TOP 10 malware hosts
| 1 | stats1.in | 16.59% |
| 2 | ru-download.in | 8.61% |
| 3 | 72.51.44.90 | 8.39% |
| 4 | e46l.cc | 8.2% |
| 5 | adult-se.com | 7.88% |
| 6 | rx-downloader.in | 7.88% |
| 7 | lxtraffic.com | 5.1% |
| 8 | literedirect.com | 4.75% |
| 9 | au.imgfarm.com | 4.48% |
| 10 | tizerplatform.com | 3.79% |
TOP 10 malicious domain zones
| 1 | com | 29549282 |
| 2 | ru | 11275285 |
| 3 | in | 3229968 |
| 4 | info | 2284435 |
| 5 | net | 2096213 |
| 6 | org | 1625163 |
| 7 | me | 1382158 |
| 8 | tv | 962598 |
| 9 | cc | 649231 |
| 10 | biz | 387681 |
Top 10 countries with the highest percentage of attacks against users’ computers (Web Antivirus)
| 1 | Russia | 36.9% | 0 |
| 2 | Armenia | 33.7% | 0 |
| 3 | Belarus | 31,0% | +1 |
| 4 | Iraq | 30.8% | +5 |
| 5 | Mongolia | 30.2% | New |
| 6 | Ukraine | 28.8% | +1 |
| 7 | Sudan | 27.7% | +3 |
| 8 | Kazakhstan | 26.9% | -5 |
| 9 | Republic of Korea | 26.9% | -1 |
| 10 | Azerbaijan | 26.7% | -4 |


















Monthly Malware Statistics: October 2011