
Introduction
The evolution of mobile malware all but stopped after the publication of our first two articles on the subject. This is why there has been an interval of nearly three years between articles.
Mobile malware evolved rapidly during the first two years (2004 – 2006) of its existence. During this period, a wide range of malicious programs targeting mobile phones appeared, and these programs were very similar to malware which targeted computers: viruses, worms, and Trojans, the latter including spyware, backdoors, and adware.
This threat landscape created conditions which could be used for an all-out attack on smartphone users. However, such an attack did not occur. The reason for this was the rapidly changing situation of the mobile devices market. Two years ago, Symbian was the undisputed market leader. If the situation had remained unchanged, there would now be an enormous amount of malware for Symbian smartphones. However, things have changed: Symbian (and Nokia) have lost their leading market share to other mobile operating systems and devices. At present, Nokia’s share of the smartphone market is around 45%.
Microsoft was the first to strike a competitive blow with its Windows Mobile platform. Windows Mobile 5 laid the foundation for Microsoft’s success and was supported by many major phone manufacturers. Version 6 was then released, with the source code of the operating system being published. Today, Windows Mobile holds about a 15% share of the global smartphone market, and is the market leader in some countries. Four of the biggest mobile phone manufacturers (excluding Nokia) have licensed Windows Mobile from Microsoft. Sales of mobile phones running Windows Mobile may currently exceed 20 million devices a year.
RIM has also strengthened its market position considerably as its Blackberry device (which runs a proprietary operating system) has become very popular in the USA. No malware for this platform has been identified to date, apart from BBproxy, a proof-of-concept backdoor created by vulnerability researchers from German company Praetorian Global.
The launch of Apple’s iPhone was the most memorable and significant event in the recent history of mobile devices. The iPhone uses the mobile version of Mac OS X, and very quickly became one of the best selling mobile devices across the world. Apple announced its intention to sell 10 million iPhones by the end of 2008, and achieved this. By now, more than 21 million iPhones of all types have been sold; if sales of the iPod Touch (an iPhone without the phone) are included, then the total number reaches 37 million.
Add the recently launch of the first phone using Google’s Android platform, which offers a lot of possibilities for creating applications and using Google services and suddenly, it’s very unclear which platform could be seen as being the leader.
This situation differs dramatically from the world of PCs, which is clearly Windows-dominated. After all, it’s the popularity of an operating system that makes it a target for cybercriminal attack.
When virus writers realized that there was no clear leading operating system for mobile devices, they also realized it wouldn’t be possible to target the majority of mobile device users with a single attack. Because of this, they started focusing less on writing malware which targeted specific platforms, and more on creating programs capable of infecting several platforms.
This article discusses the results of this approach.
Malware families and modifications: Statistics and changes.
The list of mobile malware given in Mobile Malware Evolution, Part 1 was dated 30 August, 2006, and included 5 platforms which had been targeted by virus writers. Only one more platform has been added to the list in the three years that have passed: S/EGOLD (classified as SGold by Kaspersky Lab), used on Siemens phones. S/EGOLD is an open platform which allows users to install their own applications.
| Platform | Number of families |
Number of modifications |
| Symbian | 62 | 253 |
| J2ME | 31 | 182 |
| WinCE | 5 | 26 |
| Python | 3 | 45 |
| SGold | 3 | 4 |
| MSIL | 2 | 4 |
The data in the table above can also be represented as a diagram:
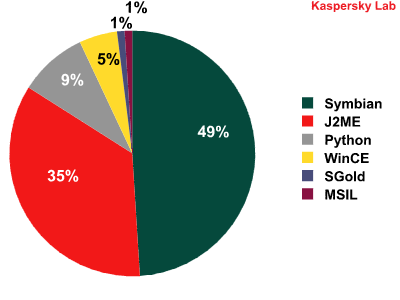
Distribution of mobile malware across platforms
Virus writers have managed to solve the issue mentioned above of which platform to target. The solution appeared as virus writers were attempting to create “cross-platform” malware. As they had rejected the idea of creating malware for a specific platform, they turned their attention to Java 2 Micro Edition.
Just about all modern mobile phones, not to mention smartphones, support Java and can run Java applications which can be downloaded from the Internet. In creating malicious Java applications, virus writers have transcended the limits of a single-platform approach and have managed to significantly extend the number of infectable devices, which now includes regular mobile phones as well as smartphones.
In late August 2006, there were 31 mobile malware families and 170 modifications. As of mid-August this year, Kaspersky Lab had identified 106 families and 514 modifications, giving 202% growth within the space of three years. The number of malware families has increased by 235%.
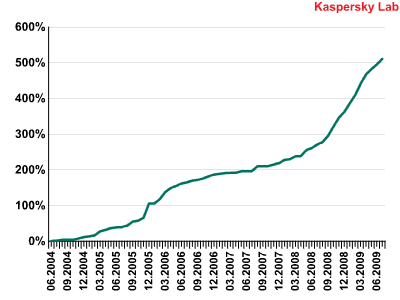
Growth in number of known modifications (2004–2009)
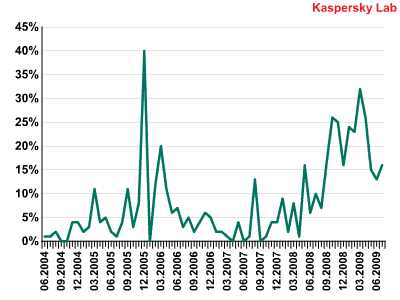
Number of new modifications per month (2004–2009)
The table below gives a breakdown of mobile malware detected between September 2006 and August 2009 by family:
| Family | Date of detection |
Platform | Brief description |
Number of modifications |
| Wesber | Sep 06 | J2ME | Sends SMS messages | 1 |
| Acallno | Sep 06 | Symbian | Steals data | 2 |
| Flerprox | Oct 06 | Symbian | Replaces system boot loaders | 2 |
| Hidmenu | Oct 06 | Symbian | Hides the menu | 1 |
| Unlock.a | Oct 06 | Symbian | Unlocks the phone | 1 |
| Smarm | Jan 07 | J2ME | Sends SMS messages | 10 |
| Mead | Feb 07 | Sgold | Infects files | 2 |
| Mrex | Mar 07 | Symbian | Changes color schemes | 1 |
| Viver | May 07 | Symbian | Sends SMS messages | 2 |
| Feak | May 07 | Symbian | Sends SMS messages containing a link to itself in a zip-archive | 1 |
| SHT | Aug 07 | Symbian | Hacker utility | 1 |
| Konopla | Aug 07 | Sgold | Disrupts settings, changes themes and pictures | 1 |
| Reboot | Aug 07 | Symbian | Restarts the device | 2 |
| Delcon | Aug 07 | Symbian | Deletes contacts | 1 |
| SMSFree | Oct 07 | J2ME | Sends SMS messages | 10 |
| Flocker | Oct 07 | Python | Sends SMS messages | 44 |
| Deladdr | Nov 07 | Sgold | Deletes files from the phone (address book, applications, SMSs, wap profiles) | 1 |
| HatiHati | Dec 07 | Symbian | Spreads via MMC memory cards, sends SMS messages | 1 |
| Fonzi | Jan 08 | Symbian | Deletes files | 1 |
| Killav | Jan 08 | Symbian | Deletes antivirus solutions | 3 |
| Beselo | Jan 08 | Symbian | Spreads via Bluetooth and MMS | 2 |
| Swapi | Feb 08 | J2ME | Sends SMS messages | 44 |
| SrvSender | Mar 08 | Symbian | Answers all incoming SMSs and calls with a random SMS. Deletes messages | 1 |
| Kiazh | Mar 08 | Symbian | Demands money, deletes all incoming and outgoing SMS messages | 1 |
| InfoJack | Mar 08 | WinCE | Copies itself to removable disks, steals data, loads software without the user’s consent, disables protection | 3 |
| Gpiares | Apr 08 | Symbian | Sends SMS messages | 2 |
| Kuku | May 08 | Symbian | Sends SMS messages | 1 |
| SmsSpy | May 08 | Symbian | Sends the user’s messages to a number specified in a sfg-file | 1 |
| Forvir | May 08 | Symbian | Displays fake messages about system errors and reports a virus has been installed on the phone | 1 |
| Hoaxer | May 08 | J2ME | Sends SMS messages | 6 |
| KillPhone | May 08 | Symbian | Phone cannot be started after reboot | 3 |
| Xanel | May 08 | J2ME | Sends SMS messages | 4 |
| SMSi | May 08 | J2ME | Sends SMS messages | 15 |
| Konov | May 08 | J2ME | Sends SMS messages | 14 |
| Kros | Jun 08 | Symbian | Replaces executable files | 1 |
| Blocker | Jun 08 | Symbian | Blocks some operating system functions | 1 |
| Boxer | Sep 08 | J2ME | Sends SMS messages | 15 |
| Redoc | Sep 08 | WinCE | Sends SMS messages | 19 |
| Espaw | Sep 08 | J2ME | Sends SMS messages | 7 |
| KaspAV | Aug 08 | J2ME | Fake antivirus | 3 |
| PMCryptic | Oct 08 | WinCE | Polymorphic companion virus, worm (memory card) | 1 |
| MultiNum | Oct 08 | Symbian | Sends SMS messages | 1 |
| Razan | Oct 08 | J2ME | Displays fake message saying phone has been infected | 1 |
| Onro | Oct 08 | J2ME | Sends SMS messages | 3 |
| DoctorW | Nov 08 | J2ME | Fake antivirus | 1 |
| SMSSender | Nov 08 | J2ME | Sends SMS messages | 1 |
| Sspy | Dec 08 | Python | Spyware | 1 |
| Tagsa | Dec 08 | Symbian | Sends SMS messages | 1 |
| Small | Dec 08 | J2ME | Sends SMS messages | 7 |
| Noti | Jan 09 | J2ME | Mobile content for SMSs | 1 |
| Okpon | Jan 09 | J2ME | Sends SMS messages | 1 |
| Yxe | Jan 09 | Symbian | Spreads via SMSs, collects data | 4 |
| CoS | Jan 09 | Symbian | Hacker utility to send specially crafted SMSs | 2 |
| Kinap | Jan 09 | Symbian | Changes fonts, icons, logos | 7 |
| Vers | фев.09 | Symbian | Sends SMS messages | 1 |
| Yakki | Feb 09 | Symbian | Deletes fonts | 1 |
| Disabler | Feb 09 | Symbian | Blocks SMSs, MMSs, calls | 1 |
| Getas | Feb 09 | J2ME | Imitates a virus | 1 |
| Xef | Feb 09 | J2ME | Sends SMS messages | 2 |
| GameSat | Feb 09 | J2ME | Sends SMS messages | 1 |
| Rebrew | Feb 09 | J2ME | SMS-Flooder | 1 |
| Mexasa | Mar 09 | J2ME | Sends SMS messages | 4 |
| Xavava | Mar 09 | J2ME | Sends SMS messages | 3 |
| Kblock | Mar 09 | Symbian | Locks phone | 1 |
| Garlag | Mar 09 | J2ME | Sends SMS messages | 2 |
| Redrob | Mar 09 | J2ME | Sends SMS messages | 4 |
| Fnusob | Mar 09 | J2ME | Sends SMS messages | 1 |
| Pornidal | Apr 09 | Symbian | Makes calls to paid services | 2 |
| SMSRtap | Apr 09 | Symbian | Monitors SMSs, calls etc. | 3 |
| Trojan-SMS.Agent | May 09 | J2ME | Sends SMS messages | 4 |
| Caneo | Jun 09 | Symbian | Monitors SMSs, calls etc. | 2 |
| Crymss | Jun 09 | J2ME | Sends SMS messages | 1 |
| Smypa | Jun 09 | Python | SMS-Flooder | 1 |
| Enoriv | Jul 09 | Symbian | Sends SMS messages | 1 |
| Smofree | Aug 09 | J2ME | Makes calls to paid services | 1 |
Total: 75 new families
Between 2006 and 2009, the amount of malware for mobile devices trebled. This shows that the growth rate demonstrated between 2004 and 2006 has been maintained.
What’s new?
Three years ago, mobile malware was capable of:
- Spreading via Bluetooth, MMS
- Sending SMS messages
- Infecting files
- Enabling remote control of the smartphone
- Modifying or replacing icons or system applications
- Installing “fake” or non-working fonts and applications
- Combating antivirus programs
- Installing other malicious programs
- Locking memory cards
- Stealing data
Mobile malware has adopted a number of new technologies and techniques within the past three years and now includes the following :
- Spreading via removable media (memory sticks)
- Damaging user data
- Disabling operating system security mechanisms
- Downloading other files from the Internet
- Calling paid services
- Polymorphism
Technologies and approaches
A relatively large number of malicious programs which target PCs spread by copying themselves to removable media or USB flash drives. Although it is primitive, this propagation method has proved to be very effective.
Mobile virus writers have followed suit and used this method in mobile malware. Worm.WinCE.InfoJack is one example of malware which uses this method. This worm copies itself to the E: drive. In smartphones running Windows Mobile, this letter designates the device memory card.
In addition to its propagation routine, InfoJack has some other interesting features. Firstly, the worm spreads as part of a cab installer that also contains legitimate applications and games. Obviously, this trick is used to hide the worm activity. Secondly, InfoJack disables application signature check, one of the defense mechanisms implemented in Windows Mobile. This means that if the user attempts to install an unsigned application (which could be malicious), the operating system will fail to notify the user that the application lacks a signature. Thirdly, the worm tries to download additional malicious modules once the smartphone is connected to the Internet. So InfoJack also has downloader functionality. And finally, the worm will send the user’s personal data to its author.
All in all, this is malware that can replicate, download files from the Internet, disable operating system defenses and spy on the user. And it’s also pretty good at disguising itself.
Worm.WinCE.PMCryptic.a is another example of a worm that copies itself to the memory card. However, this worm is notable for a different reason: it’s the first polymorphic worm and companion virus for smartphones! The worm, which has Chinese origins has not been detected in the wild, and is merely proof of concept code. However, the mere fact that polymorphic malware can be created for smartphones is alarming.
Various primitive Trojans that corrupt or delete user data have also caused problems for smartphone owners. Trojan.SymbOS.Delcon.a is one example: it infects smartphones running Symbian and is only 676 bytes in size! Once the sis-archive has been launched, a file called contacts.pdb which contains the user’s contacts is replaced by a different file from the malicious archive. The malicious version of the contacts.pdb file contains the following message in English and Russian:
Series60 is only for professionals…(c)
by KoS. 2006 ))””Если вы установили эту программу, вы действительно глупы 😀
Series 60 – только для профессионалов… (c)
KoS. 2006 ))”
Not-a-virus:Porn-Dialer.SymbOS.Pornidal.a is a malicious program that makes international calls to international premium-rate numbers. Before this program appeared, such malware only targeted PCs.
Not-a-virus:Porn-Dialer.SymbOS.Pornidal.a works as follows: when the sis-file is launched, a license agreement is displayed which says the application will make international calls to premium-rate numbers in order to gain full access to a pornographic website. The application calls premium-rate numbers in a number of countries around the world, including four European countries, four countries in Africa and one in the Australia/ Pacific region.
Such programs are dangerous because they can be modified by cybercriminals to have a malicious payload and be used to make money illegally. For instance, the warning that the application will call premium-rate numbers can be removed. Besides, many people do not pay much attention to license agreements and accept them almost mechanically, skipping over information about what the application may do (in this case, call premium-rate numbers).
SMS Trojans: the main threat
A brief look at the evolution of mobile malware behavior shows that sending SMS messages to premium-rate numbers without the user’s consent dominates. Three years ago, only two families of mobile malware included this function, in contrast to the current 32 families. Some 35% of all mobile malware which Kaspersky Lab detects sends SMS messages. This shows that SMS Trojans are the leading type of mobile threat today. An article on malware evolution published in September 2008 describes the trends behind this situation.
Payload
Java 2 Micro Edition (J2ME) is the main habitat of SMS Trojans. The SMS Trojans written for this platform pose a threat because they are cross-platform. If a mobile phone (not necessarily a smartphone) has an integrated Java Virtual Machine, Trojan-SMS.J2ME will be able to run on the device.
The vast majority of J2ME Trojans work in the following way: a jar-archive contains several class files, one of which sends a chargeable SMS message to a short number. The other class-files are there simply to disguise the presence of the malicious file. The archive may also include images, typically of an erotic nature, and a manifest file that may occasionally be used by the malware to sending messages.
Immediately after launching, Trojan-SMS.J2ME attempts to send an SMS message with a certain text to a short number. In this case, the Java machine warns the user that the application is trying to send an SMS. This may make the user suspicious, and they may refuse to allow the SMS to be sent. Some virus writers have realized that and started to design their malware that malicious activity is masked in more complex, and sometimes rather unconventional, ways.
For example, once launched Trojan-SMS.J2ME.Swapi.g displays a greeting asking if the user wants to see a pornographic image. To see the picture, the user has to press “yes” while a short tune is being played. (The program’s jar-archive stores both a png-file containing the image and a midi-file with the tune). In trying to press “yes” at the same time as the tune is playing, the user has no idea that each time they press the key (regardless of whether the tune is playing or not) an SMS is sent to a short number, and a certain amount of money is deducted from their account.
One site where cybercriminals offer their services in creating such malicious programs in return for payment contains the following message: “This program is very profitable, it’s like a photo album. When it’s run, it displays a pretty picture then a dialogue box appears: “You must be over 18 in order to proceed. Are you 18 or older?”. If the user answers “Yes”, the program will send an SMS to a short number…”
Programs in the Trojan-SMS.Python.Flocker family are written for a different platform, Python, but are essentially the same as J2ME Trojans. The sis-archive includes the main script written in Python, which sends SMS messages to a short premium-rate number. The archive also includes additional files designed to mask malicious activity.
Flocker modifications have proved very similar to each other, differing mostly in the short numbers used. This similarity seemed to suggest that the script source code may be publically available, and this hypothesis has proved correct. The Python script source was published on a forum, and parts of this script were identical to the malicious scripts already detected. Interestingly, the script available for download could also infect other scripts written in Python stored on the phone.
Propagation
Virus writers in Russia are now extensively using a range of Trojan-SMS programs. One of the most popular ways (and there are only a few) to spread such malware is via WAP portals, which offer various ringtones, pictures, games and applications for mobile phones. The vast majority of SMS Trojans are presented as applications that can be used to send free SMS messages or get free Internet access. Others are presented as being erotic or pornographic content.
Why WAP portals? The answer is simple: Russia is among the top 4 countries with the highest number of mobile Internet users. Many users visit WAP sites to download content to their phones.
The majority of sites which host malware allow users to upload their own files. Minimal, if any, registration requirements and free access to online resources of this type give cybercriminals the opportunity to freely distribute their primitive creations. All virus writers have to do is give the malicious file a tempting name, (free_gprs, super_porno etc.), write an attractive description of the program, and wait for visitors who want to “send free SMS” or “see porn pics” to rise to the bait.
Once cybercriminals have placed their malware on a WAP site, they have to promote it. This is often done via mass mailing ICQ users, or spamming forums. ICQ is used because this instant messaging service is popular in Russia and the former Soviet Union. Many people have ICQ clients installed on their phones so they can stay in touch wherever they are; a pool of potential victims.
The financial side
SMS messages are effectively the only way (so far) for mobile virus writers to make money illegally. Back in mid-2007, we analyzed Viver, the first SMS Trojan for Symbian, and this included detailed analysis of how cybercriminals used it to make money. The same scheme is still being used in more or less the same form today, and is used by all SMS Trojans.
In order to make money illegally, cybercriminals have to sign up for a prefix, or keyword, linked to a short number. Many virus writers enter into so-called “partnership programs” to share short number prefixes rather than leasing them individually. When cybercriminals sign up to these partnership programs, they receive a “prefix + partner ID” combination rather than the entire prefix.
The money deducted from the accounts of infected mobile device owners gets split between the members of the partnership program.
SMS fraud
Mobile malware is not the only threat to mobile phones. Unfortunately, SMS fraud is becoming more and more popular with cybercriminals; the threat is international and has been for some considerable time.
The telecommunications department of India issued a statement in 2007 expressing its concern about the rise of SMS phishing in the country, and announced it was reviewing a proposal to forbid mobile operators from processing SMS messages sent from abroad via web-sites. Fraudulent messages had been sent to Indian phone users asking them to call a designated number and “confirm” transaction details. Calls were answered by an answering machine with a message asking for banking details and other confidential data. Naturally, the answering machine belonged to criminals.
Such scams are not only popular in India, but in many other countries as well.
Importantly, mobile operators are paying attention to this problem. They are being fairly proactive in informing users about threats, publishing information about attacks and examples of phishing messages, and giving advice on what to do in such cases.
Russian scammers take a rather different approach.
Variation 1:
The scammer composes an SMS message saying something like: “Hi. I’m in trouble, can’t give you the details here. Could you put money either on this account or on +79xx-xxx-xx-xx? I’ll pay you back later.” Such messages don’t include the name of either the sender or the recipient, so anyone could think that the message is intended for them.
If the message recipient calls either numbers, they get a message along the lines of “the subscriber is unavailable”. After this, they may well think: “Something really might have happened to my friend/relative/contact”, and put money, as requested, on the scammer’s account.
Variation 2:
This scam involves chargeable SMS messages sent to short numbers. The scam messages vary e.g. “Hi! Send an SMS saying *** to 3649, and you’ll get a 150 ruble bonus on your account. The SMS is free: I tried it and it worked.” Or: “Hello! Your number is a winner! To receive the prize, send an SMS saying *** to 1171. The SMS costs 3 rubles”.
Such attacks have the following distinctive features :
- The criminals use the most expensive short numbers.
- Most messages offer some kind of instant “bonus” or “win”.
- The messages do not include the name of the sender or the recipient.
Significantly, such messages aren’t only sent to mobile phones, but can also be sent via ICQ, email or social networking sites.
Vulnerabilities
At the very beginning of 2009, a new vulnerability was detected in smartphones running the following versions of Symbian:
- S60 2nd edition, Feature Pack 2;
- S60 2nd edition, Feature Pack 3;
- S60 3rd edition;
- S60 3rd edition, Feature Pack 1.
What is this vulnerability, and how it gets exploited? If a specially crafted SMS is sent to a phone running one of the operating systems listed above, the phone can neither send nor receive SMS/ MMS messages. The malcrafted message is not visible in the incoming messages list, and the exploit does not leave any visible traces. This led to it being dubbed “The Curse of Silence”.
As a result, the phone now longer offers short messaging services, but otherwise continues to function as normal. It may therefore take the user some time to realize find out that something is wrong with the phone. Unfortunately, the problem cannot be fixed by deleting previous incoming or outgoing messages; the only solution is a hard reset.
Mobile threats in the wild
Previous publications on Mobile Malware Evolution included statistics on the spread of Bluetooth and MMS worms in different countries around the world. Cabir and ComWar were the most widespread mobile threats, as each was detected in more than 30 countries. The most high-profile incident occurred in Spain when more than 115 thousand users were infected with a ComWar variant in the spring of 2007.
Fortunately, the mobile operators’ focus on emerging threats and the implementation of antivirus scanning of MMS traffic helped arrest the propagation of these worms. Other measures which also helped combat local epidemics included antivirus products for mobile devices, which were often pre-installed on the device; new protection methods being integrated into operating systems, which ensured only signed applications were allowed to run; and lastly, the phones vulnerable to Cabir and ComWar have gradually disappeared from the market.
However, there has been at least one mobile worm in the last three years that was able to spread in several European countries.
Worm.SymbOS.Beselo
In late December 2007, a new clone of ComWar, the so-called “.y variant”, was added to antivirus databases. In January 2008 it became necessary to take a closer look at this malicious program when it surfaced in the traffic of a major European mobile operator.
An analysis by F-Secure, the Finnish cyber security company, revealed that this program was actually an entirely new family and did not have anything to do with ComWar, which had been created in Russian three years earlier.
The worm was classified as Worm.SymbOS.Beselo.a (another variant, Beselo.b – has also been detected). It acts in a similar way to ComWar, and uses an approach classic for this type of worm. It spreads by sending infected SIS-files via MMS and Bluetooth. When run, the worm starts sending itself to all contacts in the address book to all accessible devices within Bluetooth range.
Luckily, Beselo was fairly quickly prevented from spreading, and no further mobile worms have been detected in the wild in Europe since.
However, Asia also entered the picture in the form of China, the home of most modern malware.
Worm.WinCE.InfoJack
In early 2008, information about users getting infected with an unknown program which ran under Windows Mobile started surfacing. This proved to be InfoJack.a, the Trojan mentioned earlier in this article.
The malicious program was spread from a Chinese website distributing a variety of legitimate software. The Trojan was included in distributions of phone software, such as the Google Maps client or games. The owner of the site said he had not had any criminal intention, but simply wanted to collect information about users to the site in order to provide an improved service and to analyze the mobile applications market.
A few days later the site was blocked, probably in the course of an investigation by the Chinese police.
Prior to this, Chinese hackers had targeted online gamers using PCs. However, the InfoJack case showed that China did provide opportunities for conducting epidemics using mobile viruses.
So China became the first country affected by a Trojan running under Windows Mobile. The person who created InfoJack might not have had criminal aims, but the foundation stone had been laid…
Worm.SymbOS.Yxe
A year later, in January 2009, we detected a new malicious program for mobile phones running Symbian. This might not seem particularly new or interesting, but this worm turned out to be quite remarkable.
Worm.SymbOS.Yxe was the first family of Symbian worms for a long time. It differed from its predecessors in its propagation routine, spreading not via Bluetooth or MMS but by SMS!
Worm.SymbOS.Yxe sent frivolous messages to everyone on the infected phone’s contact list. The messages included a link to a web-site http://www*****.com/game which hosted a copy of the worm. When the user followed that link, they found a regular Symbian installer with two files in it: an executable file and an auxiliary rsc file. If the user agreed to install the application, the worm after a while would start sending SMS messages to the contacts on the infected phone, thus creating malicious SMS traffic.
The Chinese electronic mass media published a lot of reports about Worm.SymbOS.Yxe. There was also a lot of discussion on forums where people complained about receiving odd SMS messages etc. The media reports talked about messages with pornographic content and a strange link, messages being sent without authorization to contacts, and money being charged for the SMS messages which were sent.
The worm distinguished itself in one further way. It was created for smartphones running Symbian S60 3rd edition, and is signed with a legal certificate. This means that the worm can be installed on any phone running Symbian S60 3rd edition.
The certificate looks like this:
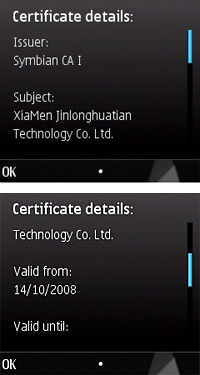
According to the signature, the certificate is valid for ten years. An investigation showed the malware had gone through the automatic signing procedure.
Trojan-SMS.Python.Flocker
January 2009 was rich in events related to mobile malware. Apart from the Yxe worm and the Curse of Silence exploit, several new variants of Trojan-SMS.Python.Flocker (.ab – .af) were detected.

A Trojan-SMS.Python.Flocker modification
What was special about the six new modifications? Prior to their appearance, all Trojan-SMS malware we had identified had been created in the former Soviet Union, and sent messages to short numbers belonging to Russian mobile operators.
The new variants of Flocker send SMS messages to 151, a short number which is not registered in Russia. Moreover, we had been unaware of any 3-digit short numbers. The message text was also peculiar: TP .
In short, there are several malicious programs sending similar text messages to the same short number. Which gives rise to the old question: where is the money going?
Long before the new variants of Flocker were detected, an Indonesian mobile company published a press release saying that owners of a specific type of SIM card could send money from their account to the account of anyone who had the same type of SIM card. In order to send money, a message had to be sent to short number 151 with the text “TP “.
Scammers then exploited this opportunity: a Trojan of Russian origin was modified by somebody to work with Indonesian mobile operators, and distributed among Indonesian users.
All the cases above show that mobile threats are continuing to spread around the world. However, the nature of the threat has changed dramatically: global worm epidemics have been replaced by local outbreaks in specific countries or regions. This situation is identical to the situation with computer viruses.
The countries and regions most affected by the threat posed by mobile viruses are Russia, China, Indonesia and Western Europe.
Conclusion
Smartphones are popular and are being used more and more often to do business, surf the Internet, access bank accounts, and pay for goods and services. This will lead to an increased number of cybercriminals and scammers wanting to exploit these actions for illegal gains.
Today’s malware is capable of doing many things: stealing and transmitting the contact list and other data, locking the device completely, giving remote access to criminals, sending SMS and MMS messages etc. With smartphones increasingly being used in business for remote working or while travelling, a disabled phone can be a serious handicap. And if a cybercriminal gains access to a corporate network or email, this creates a breach in the company’s security system.
As for the iPhone (which has 4% of the global mobile market, and 20% of the American market) and Android, the potential for malicious attack on these platforms differs greatly. For iPhones, infection is only likely if the user hacks the handset and installs unsigned applications. Android will probably not require official certificates for applications, and owners of legitimate phones may be able to install whatever they want.
It’s too early to discuss how malware for the iPhone and for Android may evolve. As we see it, the major risk to these platforms will be software vulnerabilities and cybercriminals using them to gain unauthorized access.
An extremely important factor is the nascent competition between netbooks and smartbooks. These devices differ from each other in that smartbooks are built on a distinctly different architecture, analogous to that of mobile phones. Expert evaluations say that 98% of all mobile phones, including the Apple iPhone, are based on ARM processors.
The designers’ intention is that smartbooks incorporate the best features of both netbook and smartphone: they have a full keyboard, a relatively large screen, are light-weight and have long battery life. Most importantly, the platform is designed to support mobile networks, and smartbooks are designed to include a modem in the processors. This facilitates easy and transparent integration of network services into the program shell.
Intel in its turn is attempted to create a market for mobile devices based on its Atom processor. By the end of this year, Atom processors will be produced in system-on-a-chip format. In practice, this means that the x86-compatible microprocessor architecture familiar to many programmers could be built into anything: car processors, refrigerator or microwave chips, vacuum cleaners, clocks, TV sets, coffee machines etc.
All these factors and the anticipated technology wars could change the situation beyond recognition. Smartbooks may become a more popular target for malware attacks than smartphones. On the other hand, if x86 processors make it into home appliances, the potential scope of malicious attacks could be radically extended.



















Mobile Malware Evolution: An Overview, Part 3