
Two Top Twenties have been compiled from data generated by the Kaspersky Security Network (KSN) throughout March 2009.
The first Top Twenty is based on data collected by Kaspersky Lab’s version 2009 antivirus product. The ranking is made up of the malicious programs, adware and potentially unwanted programs most frequently detected on users’ computers.
| Position | Change in position | Name |
| 1 |  1 1 |
Net-Worm.Win32.Kido.ih |
| 2 |  -1 -1 |
Virus.Win32.Sality.aa |
| 3 |  2 2 |
Trojan.Win32.Autoit.ci |
| 4 |  4 4 |
Trojan-Downloader.Win32.VB.eql |
| 5 |  2 2 |
Packed.Win32.Krap.g |
| 6 |  0 0 |
Worm.Win32.AutoRun.dui |
| 7 |  -4 -4 |
Packed.Win32.Krap.b |
| 8 |  -4 -4 |
Packed.Win32.Black.a |
| 9 |  New New |
Trojan-Dropper.Win32.Flystud.ko |
| 10 |  5 5 |
Virus.Win32.Sality.z |
| 11 |  1 1 |
Worm.Win32.Mabezat.b |
| 12 |  -2 -2 |
Virus.Win32.Alman.b |
| 13 |  1 1 |
Worm.Win32.AutoIt.ar |
| 14 |  New New |
Trojan.JS.Agent.ty |
| 15 |  2 2 |
Email-Worm.Win32.Brontok.q |
| 16 |  3 3 |
Worm.Win32.AutoIt.i |
| 17 |  Return Return |
Virus.Win32.VB.bu |
| 18 |  New New |
Packed.Win32.Katusha.a |
| 19 |  New New |
Trojan.Win32.RaMag.a |
| 20 |  New New |
Trojan.Win32.Autoit.xp |
There were no significant changes to this ranking in March.
The network worm Net-Worm.Win32.Kido.ih, also known as Conficker and Downadup, topped the list. However, we don’t expect to see the latest version of this now infamous malicious program among the leaders in the following months: it’s now detected by Kaspersky Lab as Trojan-Downloader.Win32.Kido.a and unlike previous variants, this one is unable to spread independently across networks.
The highest new entry Trojan-Dropper.Win32.Flystud.ko is the highest ranking new entry; it came straight in at number nine and is a typical Trojan designed to stealthily install other Trojans. It is written in the FlyStudio script language that, along with AutoIt, is one of the most popular languages among malware writers. Both FlyStudio and the programs written in it originate in China.
Speaking of AutoIt, March’s ranking sees the Autoit.ci Trojan joined by a similar program called Autoit.xp.
At the lower end of the ranking there are two other new entries: Packed.Win32.Katusha.a and Trojan.Win32.Ramag.a. The former detects a compression utility used to pack both certain modifications of the fraudware program FraudTool and the malware which downloads these modifications. The Ramag.a Trojan is a modified WinRAR archive which has no malicious payload apart from carrying other malware.
There were fewer script downloader programs; only Trojan.JS.Agent.ty, with its traditional iframe, is present in the first Top Twenty.
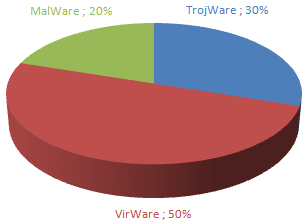
All malicious, advertising and potentially unwanted programs in the first Top Twenty can be grouped according to the main classes of threats which we detect. There has been no significant change in the balance between these classes for the last three months. The number of self-replicating programs also remains relatively high.
In total, 45857 unique malicious, advertising, and potentially unwanted programs were detected on users’ computers in March. This figure is almost exactly the same as last month’s.
The second Top Twenty presents data on which malicious programs most commonly infected objects detected on users’ computers. Malicious programs capable of infecting files make up the majority of this ranking.
| Position | Change in position | Name |
| 1 |  0 0 |
Virus.Win32.Sality.aa |
| 2 |  0 0 |
Worm.Win32.Mabezat.b |
| 3 |  1 1 |
Virus.Win32.Virut.ce |
| 4 |  -1 -1 |
Net-Worm.Win32.Nimda |
| 5 |  0 0 |
Virus.Win32.Xorer.du |
| 6 |  0 0 |
Virus.Win32.Sality.z |
| 7 |  0 0 |
Virus.Win32.Alman.b |
| 8 |  0 0 |
Virus.Win32.Parite.b |
| 9 |  3 3 |
Virus.Win32.Virut.q |
| 10 |  0 0 |
Trojan-Downloader.HTML.Agent.ml |
| 11 |  8 8 |
Virus.Win32.Small.l |
| 12 |  2 2 |
Email-Worm.Win32.Runouce.b |
| 13 |  New New |
Net-Worm.Win32.Kido.ih |
| 14 |  -3 -3 |
Virus.Win32.Virut.n |
| 15 |  -2 -2 |
Virus.Win32.Parite.a |
| 16 |  0 0 |
Virus.Win32.Hidrag.a |
| 17 |  -8 -8 |
Trojan-Clicker.HTML.IFrame.acy |
| 18 |  -3 -3 |
P2P-Worm.Win32.Bacteraloh.h |
| 19 |  Return Return |
Worm.Win32.Otwycal.g |
| 20 |  Return Return |
Worm.Win32.Fujack.k |
Net-Worm.Win32.Kido.ih also made its mark in the second of our rankings and held its own among the more common types of self-replicating programs. This is most probably due to the fact that not all users installed the necessary security updates to their operating system in March.

















Monthly Malware Statistics: March 2009