
As in previous months, this malware rating is compiled from data generated by the Kaspersky Security Network (KSN). However, slightly different methods have been used to select and analyze the data.
As before, two Top Twenties have been compiled from the data generated by KSN.
The first Top Twenty lists malicious programs, adware and potentially unwanted programs that were detected and neutralized when accessed for the first time, i.e. by using the on-access scanner. Using on-access statistics makes it possible to analyze the most recent, most dangerous and most widespread malicious programs that were blocked when launched on users’ computers or when downloaded from the Internet.
| Position | Name | Number of infected computers |
| 1 | Net-Worm.Win32.Kido.ih | 58200 |
| 2 | Virus.Win32.Sality.aa | 28758 |
| 3 | Trojan-Dropper.Win32.Flystud.ko | 13064 |
| 4 | Trojan-Downloader.Win32.VB.eql | 12395 |
| 5 | Worm.Win32.AutoRun.dui | 8934 |
| 6 | Trojan.Win32.Autoit.ci | 8662 |
| 7 | Virus.Win32.Virut.ce | 6197 |
| 8 | Worm.Win32.Mabezat.b | 5967 |
| 9 | Net-Worm.Win32.Kido.jq | 5934 |
| 10 | Virus.Win32.Sality.z | 5750 |
| 11 | Trojan-Downloader.JS.LuckySploit.q | 4624 |
| 12 | Virus.Win32.Alman.b | 4394 |
| 13 | Packed.Win32.Black.a | 4317 |
| 14 | Net-Worm.Win32.Kido.ix | 4284 |
| 15 | Worm.Win32.AutoIt.i | 4189 |
| 16 | Trojan-Downloader.WMA.GetCodec.u | 4064 |
| 17 | Packed.Win32.Klone.bj | 3882 |
| 18 | Email-Worm.Win32.Brontok.q | 3794 |
| 19 | Worm.Win32.AutoRun.rxx | 3677 |
| 20 | not-a-virus:AdWare.Win32.Shopper.v | 3430 |
Even though the way in which threats were analyzed changed, this had no influence on the leaders in this ranking: Net-Worm.Win32.Kido.ih remained in first place. Two more modifications of the worm – Kido.jq and Kido.ix – also appeared in the rating. This Kido crop is due to the fact that this family of malware can also spread in varied ways, including via removable media which are then connected to unprotected computers.
Two worms from the AutoRun family, AutoRun.dui and AutoRun.rxx, also made it into the ranking by dint of the same method.
Trojan-Downloader.JS.LuckySploit.q is an interesting script Trojan that is frequently used by cybercriminals; there are further details later in this report.
In twentieth place is an adware program, Shopper.v. It’s one of the most common programs of its type (the development company, Zango, formerly Hotbar, was closed down a few months ago). The application installs various toolbars to the browser and mail client and uses them to display advertising banners. Removing the toolbars can be difficult.
The second Top Twenty presents data generated by the web antivirus component and reflects the online threat landscape. This ranking includes malicious programs detected on web pages and malware which attempted to load from web pages. In other words, the second ranking answers two questions: ‘What malware most often infects web pages?’ and ‘Which malicious programs are most often downloaded – with or without the user’s knowledge – from malicious or infected pages?’
| Position | Name | Number of infected web pages |
| 1 | Trojan-Downloader.JS.Gumblar.a | 27103 |
| 2 | Trojan-Downloader.JS.Iframe.ayt | 14563 |
| 3 | Trojan-Downloader.JS.LuckySploit.q | 6975 |
| 4 | Trojan-Clicker.HTML.IFrame.kr | 5535 |
| 5 | Trojan-Downloader.HTML.IFrame.sz | 4521 |
| 6 | Trojan-Downloader.JS.Major.c | 4326 |
| 7 | Trojan-Downloader.Win32.Agent.cdam | 3939 |
| 8 | Trojan-Clicker.HTML.IFrame.mq | 3922 |
| 9 | Trojan.JS.Agent.aat | 3318 |
| 10 | Trojan.Win32.RaMag.a | 3302 |
| 11 | Trojan-Clicker.SWF.Small.b | 2894 |
| 12 | Packed.JS.Agent.ab | 2648 |
| 13 | Trojan-Downloader.JS.Agent.czm | 2501 |
| 14 | Exploit.JS.Pdfka.gu | 2441 |
| 15 | Trojan-Clicker.JS.Agent.fp | 2332 |
| 16 | Trojan-Dropper.Win32.Agent.aiuf | 2002 |
| 17 | Exploit.JS.Pdfka.lr | 1995 |
| 18 | not-a-virus:AdWare.Win32.Shopper.l | 1945 |
| 19 | not-a-virus:AdWare.Win32.Shopper.v | 1870 |
| 20 | Exploit.SWF.Agent.az | 1747 |
The top position is rightfully occupied by Gumblar.a, a Trojan-Downloader program, which is an excellent example of malware used in drive-by downloads.
Gumblar.a is a small encrypted script which, when executed, redirects the user to a malicious website. A series of vulnerabilities is then exploited to download a malicious executable file from the website and install it on the user’s computer. Once installed, the file affects the user’s web traffic by modifying Google search results. It also searches the computer for passwords to FTP servers in order to infect them.
The result is a botnet of infected servers created by cybercriminals which can be used to download any type of malicious program to users’ computers. The number of infected servers is enormous and, furthermore, the malware is still spreading to unprotected computers.
Another notable example of drive-by download malware is a Trojan-Downloader program, LuckySploit.q, which is in third place in the second ranking and is also present in the first Top Twenty.
This is a skillfully obfuscated script, which first harvests browser configuration data from the user’s computer. It then encrypts the data using an RSA public key and sends it to a malicious website. The data is decrypted on the server using the private RSA key and a selection of scripts (browser configuration dependent) is returned to the user. The scripts exploit vulnerabilities on the victim machine and download malicious programs to it. In addition to everything else, this multi-step approach seriously hinders analysis of the original script that harvests browser information: if the server that decrypts the data is not accessible, it is impossible to find out which scripts will be returned in any particular case.
A number of malicious programs exploit vulnerabilities in products from major vendors. The presence of such exploits as Trojan-Clicker.SWF.Small.b, Exploit.JS.Pdfka.gu, Exploit.JS.Pdfka.lr and Exploit.SWF.Agent.az in the ranking is testimony both to the popularity and to the vulnerability of Adobe Flash Player and Adobe Reader. Vulnerabilities in Microsoft products are also actively exploited: Trojan-Downloader.JS.Major.c attempts to exploit several vulnerabilities in different Windows and Microsoft Office components simultaneously.
Recently there has been a clear trend for cybercriminals to use a range of sophisticated drive-by downloads to install malware on victim machines. Overall, cybercriminals are becoming increasingly Web-oriented.
This makes it particularly important for users to update their operating systems and application software regularly and to keep their antivirus solutions up-to-date.
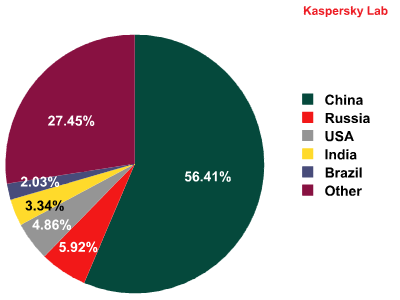
The final new feature of this monthly report is shown below: the table shows the countries which rank most highly in terms of attempts to infect computers via the web.


















Monthly Malware Statistics: June 2009