
January in figures
The following statistics were compiled in January using data from computers running Kaspersky Lab products:
- 213,915,256 network attacks blocked;
- 68,956,183 attempted web-borne infections prevented;
- 187,234,527 malicious programs detected and neutralized on users’ computers;
- 70,179,070 heuristic verdicts registered.
Online scammers
The majority of malware will attempt to conceal its presence on users’ computers and function without the users’ knowledge, especially the more sophisticated types. Cyber fraud, however, requires the participation of users. To prevent users falling victim to the various scams out there, it’s very important that they know about them.
Dangerous prizes
Cybercriminals often exploit the popularity of an online service or product, and they have clearly not overlooked the popularity of Kaspersky Lab in their attempts to make a quick buck.
For instance, there are currently utilities on the Internet that allow some Kaspersky Lab products to be used without being activated. We detect these programs as potentially unwanted programs (PUPs) belonging to the Kiser family. Two representatives of this family even made it into January’s Top 20 most popular programs detected on users’ computers, showing up at 9th and 11th places respectively.
In the first half of the month we detected a Trojan dropper masquerading as a key generator for Kaspersky Lab products. The old adage “There’s no such thing as a free lunch” is particularly fitting here as the dropper goes on to install and launch two malicious programs. One of them steals program registration data and passwords for online games. The second is a backdoor that also has keylogger functionality.
In early January our experts also came across a fake Kaspersky Lab site that differed from www.kaspersky.ru by a single letter. The site urged users to download Kaspersky Internet Security 2011 for free.
However, users got more than they bargained for, as along with the Kaspersky Lab product they also received Trojan-Ransom.MSIL.FakeInstaller.e for free! This malicious program causes the victim’s computer to reboot, before displaying a fake window resembling the Russian-language social networking site Odnoklassniki informing the user they had won a Samsung Galaxy S telephone for the price of 1200 rubles, or approximately 30 euros. Users were told that all they needed to do to claim their prize was to send an SMS to a premium-rate number. Of course, the only ‘prize’ that any gullible user received was a hole in their mobile balance that wasn’t there before.
We strongly recommend that users only ever use the products and services offered on our official sites.
Free Internet Explorer… for a small fee
Internet Explorer is another program whose popularity has been exploited by cybercriminals. In January, a web page was detected that offered users the chance to “update” their Microsoft web browsers. When the update was selected and supposedly installed, a message appeared stating that an SMS had to be sent to activate the software.
After sending the SMS to a premium-rate number, users received a link to an Internet Explorer 8 installer that is freely available to anyone, as well as, ironically, an article about computer security.
These fraudulent web pages are detected as Hoax.HTML.Fraud.e, and appear in 17th place in the Top 20 most malicious programs on the Internet in January.
Empty archives
There is another type of fraud that is still popular with online scammers everywhere – fake archives. A new variant – Hoax.Win32.ArchSMS.mvr – entered the Top 20 rating of malware on the Internet at 11th place, and also popped up in 17th place in the Top 20 rating of malware detected on users’ computers.
Attacks via Twitter
In last month’s report we talked about the spread of malicious links on Twitter that had been shortened using the goo.gl service. In mid-January the mass distribution of these types of links continued. As was the case in December, after a number of redirects, the link led users to a page promoting a Rogue AV program. Also as before, the Rogue AV opened a window that resembled My Computer on a Windows operating system, initiated a fictitious scanning process and suggested that the user pay for a license so that the “detected” malware could be removed.
Adware
Adware is still spreading fast. For example, AdWare.Win32.WhiteSmoke.a, at 12th place in our online malware rating, adds the shortcut “Improve your PC” to a computer’s desktop without seeking the user’s permission first. If the user then clicks on the shortcut, a window opens that offers to remove errors from their computer. If the user agrees, a program called RegistryBooster 2011 is downloaded which scans the system and demands payment for rectifying any errors it supposedly detects.
Screenshot of RegistryBooster 2011
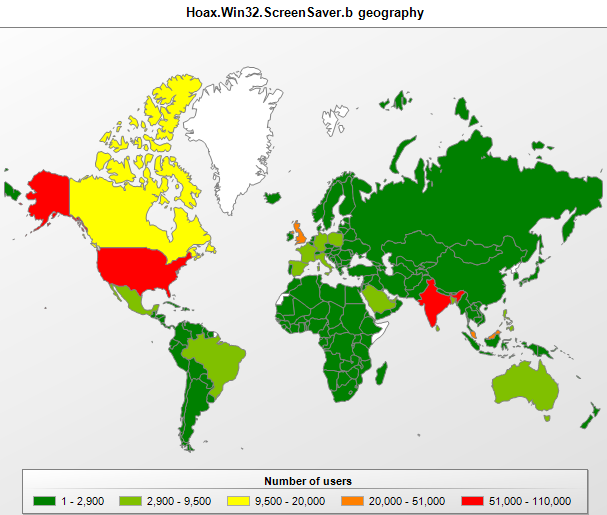
The highest new entry in our rating for malware detected on users’ computers was Hoax.Win32.ScreenSaver.b, a component of the popular adware program FunWeb, which shot straight in at 4th place. AdWare.Win32.FunWeb is one of the most popular adware families, members of which frequently appear in our Top 20 ratings. These programs are particularly prevalent in English-speaking countries such as the USA, Canada, the UK and India.
Vulnerabilities and updates
We once again call on users not to ignore critical updates. The new entry Exploit.JS.Agent.bbk, which exploits the vulnerability CVE-2010-0806, ended January in 20th place in our rating of the most widespread threats detected on users’ computers. This is despite the fact that this loophole was closed back at the end of March 2010. As well as Agent.bbk, a couple of other exploits for this particular vulnerability made it in at 6th and 13th places in the rating. This means that there are still a lot of computers out there running unpatched software, and the cybercriminals are making the most of the opportunity while it lasts.
Downloading malicious files containing Java malware
The downloading of malicious files containing Java malware that use the OpenConnection method, which cybercriminals started using last October, is now one of the most popular download methods. This is highlighted by the two new representatives of the Trojan-Downloader.Java.OpenConnection family that entered the online malware Top 20 in 9th and 20th places.
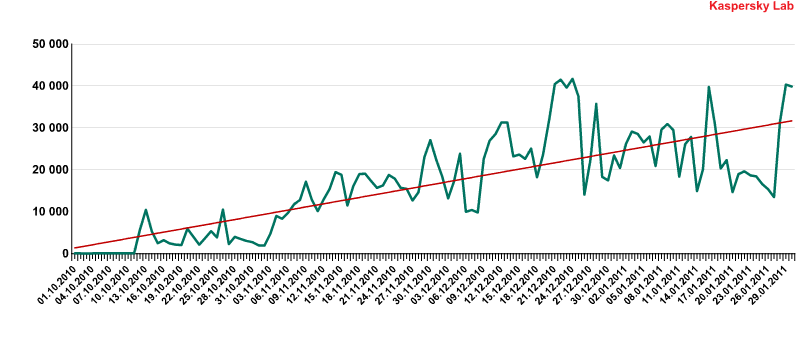
The number of unique cases of Trojan-Downloader.Java.OpenConnection
detected for the period October-January 2010
When using the latest versions of the Java Runtime Environment (JRE), users will be warned about the launch of a dangerous Java applet. Infection can be prevented by simply refusing to launch the applet.
Complex new mail worm
January saw the emergence of Email-Worm.Win32.Hlux. This new mail worm spreads via emails containing malicious links that prompt users to install a fake Flash Player, purportedly to view an e-card. The link leads to a dialog window that asks if the user agrees to download a file. Regardless of the response, the worm attempts to penetrate the system. Shortly after the dialog window opens, the user is redirected to a page containing a set of exploits and programs from the Trojan-Downloader.Java.OpenConnection family that start downloading Hlux to the victim machine.
In addition to propagating via email, Hlux also has bot functionality and adds infected computers to a botnet before connecting to its command center and executing its commands, which are primarily directed at sending pharmaceutical spam. The bot communicates with the command centers via a Fast-Flux network proxy servers. If an infected computer has an external IP address, it can be used as a link in the Fast-Flux network. A large number of infected machines allow the cybercriminals to regularly change the IP address of the domains where the botnet command centers are located.
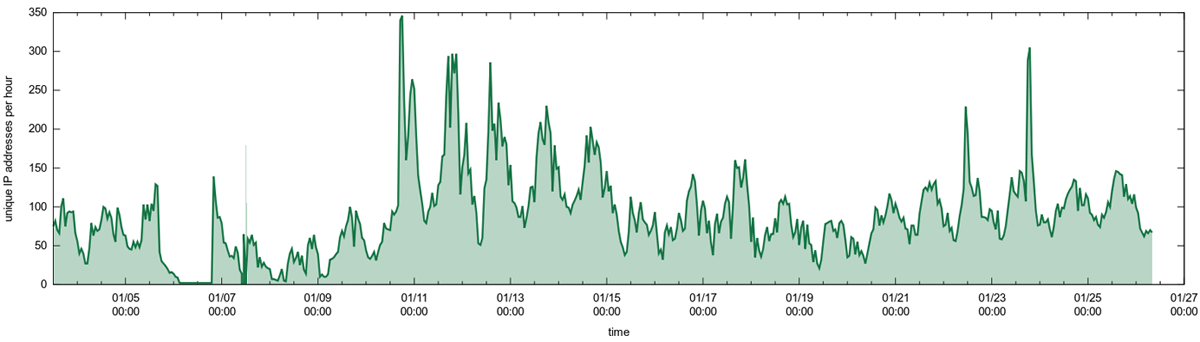
Frequency of IP address changes to Hlux botnet C&C domains
Trojan SMS: money theft with a twist
Cybercriminals came up with a different method of making money from mobile phone owners in January. The new Trojan-SMS.J2ME.Smmer.f spreads via SMSs containing links to virtual greeting cards – the standard method used by Java malware on mobile phones. After the Trojan is installed on a device it sends an SMS to two premium-rate numbers. Both messages are sent for free, so you might be wondering where the catch is. Well, the two numbers are used by a mobile operator to transfer money from one account to another. The first message that is sent by the Trojan indicates the sum to be transferred from the infected phone’s account – about 200 rubles or 5 euros – and includes the scammers’ number where the money is sent to. The second SMS simply confirms the transaction.
A similar scam was recorded a couple of years ago in Indonesia. Now it appears to have surfaced again in Russia.
TOP 20 malicious programs on the Internet
| Position | Change in position | Name | Number of unique attacks* |
| 1 |  0 0 |
AdWare.Win32.HotBar.dh | 169173 |
| 2 |  0 0 |
Trojan-Downloader.Java.OpenConnection.cf | 165576 |
| 3 |  New New |
Exploit.HTML.CVE-2010-1885.aa | 140474 |
| 4 |  New New |
AdWare.Win32.FunWeb.gq | 114022 |
| 5 |  -2 -2 |
Trojan.HTML.Iframe.dl | 112239 |
| 6 |  New New |
Trojan.JS.Redirector.os | 83291 |
| 7 |  7 7 |
Trojan-Clicker.JS.Agent.op | 82793 |
| 8 |  -4 -4 |
Trojan.JS.Popupper.aw | 80981 |
| 9 |  New New |
Trojan-Downloader.Java.OpenConnection.cg | 66005 |
| 10 |  2 2 |
Trojan.JS.Agent.bhr | 53698 |
| 11 |  New New |
Hoax.Win32.ArchSMS.mvr | 47251 |
| 12 |  New New |
AdWare.Win32.WhiteSmoke.a | 44889 |
| 13 |  5 5 |
Trojan.JS.Fraud.ba | 44561 |
| 14 |  -4 -4 |
Exploit.JS.Agent.bab | 42800 |
| 15 |  -7 -7 |
Trojan.JS.Redirector.lc | 42231 |
| 16 |  -8 -8 |
Exploit.Java.CVE-2010-0886.a | 41232 |
| 17 |  New New |
Hoax.HTML.Fraud.e | 37658 |
| 18 |  New New |
Trojan-Clicker.JS.Agent.om | 36634 |
| 19 |  -6 -6 |
Trojan-Downloader.JS.Small.os | 35857 |
| 20 |  New New |
Trojan-Downloader.Java.OpenConnection.cx | 35629 |
* Total number of unique incidents detected by web antivirus on users’ computers
TOP 20 malicious programs detected on users’ computers
| Position | Change in position | Name | Number of unique users* |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 466686 |
| 2 |  1 1 |
Virus.Win32.Sality.aa | 210635 |
| 3 |  -1 -1 |
Net-Worm.Win32.Kido.ih | 171640 |
| 4 |  New New |
Hoax.Win32.Screensaver.b | 135083 |
| 5 |  0 0 |
AdWare.Win32.HotBar.dh | 134649 |
| 6 |  -2 -2 |
Trojan.JS.Agent.bhr | 131466 |
| 7 |  -1 -1 |
Virus.Win32.Sality.bh | 128206 |
| 8 |  -1 -1 |
Virus.Win32.Virut.ce | 114286 |
| 9 |  New New |
HackTool.Win32.Kiser.zv | 104673 |
| 10 |  -2 -2 |
Packed.Win32.Katusha.o | 90870 |
| 11 |  New New |
HackTool.Win32.Kiser.il | 90499 |
| 12 |  -2 -2 |
Worm.Win32.FlyStudio.cu | 85184 |
| 13 |  -1 -1 |
Exploit.JS.Agent.bab | 77302 |
| 14 |  -1 -1 |
Trojan-Downloader.Win32.Geral.cnh | 62426 |
| 15 |  -1 -1 |
Trojan-Downloader.Win32.VB.eql | 58715 |
| 16 |  0 0 |
Worm.Win32.Mabezat.b | 58579 |
| 17 |  New New |
Hoax.Win32.ArchSMS.mvr | 50981 |
| 18 |  -1 -1 |
Packed.Win32.Klone.bq | 50185 |
| 19 |  Returned Returned |
Worm.Win32.Autoit.xl | 43454 |
| 20 |  New New |
Exploit.JS.Agent.bbk | 41193 |
* Number of unique computers where objects were detected





















Monthly Malware Statistics, January 2011