
Cybercriminals like to register domain names that are very similar to actual, well known domain names but with one or more letters changed. In many cases a potential victim will mistype a letter and in this way arrives at a fake Web site instead of the original one.
Here is just one example of this: a copy of the official Russian Web page of Kaspersky. The criminals added just one small line inside of the ‘downloads’ tab promoting a fake download for a free, one year copy of Kaspersky Internet Security 2011.
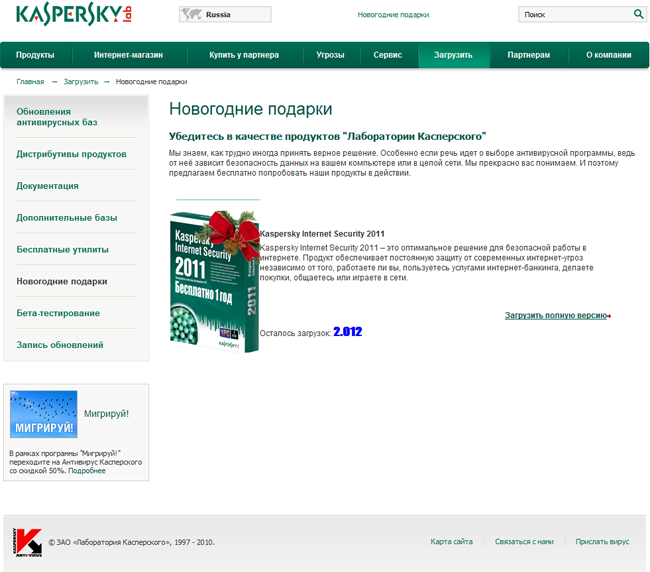
Instead of KIS 2011 the victim gets malware. This is ransomware which, after the installation, forces a reboot of your PC. Upon completing the reboot the malware shows a fake message that you’ve won a prize of a Samsung Galaxy S cellphone for just 1200 rubles (40 USD)! To claim this prize, you should pay via SMS text or, optionally through one of the popular on-line payments systems in Russia.
Kaspersky Anti-Virus detects this threat as Trojan-Ransom.MSIL.FakeInstaller.e
In the time of writing of this blogpost the malicious site was still on-line and also detected by Kaspersky Internet Security Web Anti-Virus as a fraudulent one.





















Mistyping leads to infections!