
Two Top Twenties have been compiled from data generated by the Kaspersky Security Network (KSN) throughout April 2009.
The first Top Twenty is based on data collected by Kaspersky Lab’s version 2009 antivirus product. The ranking is made up of the malicious programs, adware and potentially unwanted programs most frequently detected on users’ computers.
| Position | Change in position | Name |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ih |
| 2 |  0 0 |
Virus.Win32.Sality.aa |
| 3 |  6 6 |
Trojan-Dropper.Win32.Flystud.ko |
| 4 |  Return Return |
Trojan.Win32.Chifrax.a |
| 5 |  -2 -2 |
Trojan.Win32.Autoit.ci |
| 6 |  -2 -2 |
Trojan-Downloader.Win32.VB.eql |
| 7 |  0 0 |
Packed.Win32.Krap.b |
| 8 |  -2 -2 |
Worm.Win32.AutoRun.dui |
| 9 |  New New |
Exploit.HTML.CodeBaseExec |
| 10 |  -2 -2 |
Packed.Win32.Black.a |
| 11 |  -1 -1 |
Virus.Win32.Sality.z |
| 12 |  New New |
Virus.Win32.Virut.ce |
| 13 |  New New |
Trojan.JS.Agent.xy |
| 14 |  -3 -3 |
Worm.Win32.Mabezat.b |
| 15 |  -3 -3 |
Virus.Win32.Alman.b |
| 16 |  -11 -11 |
Packed.Win32.Krap.g |
| 17 |  Return Return |
Packed.Win32.Klone.bj |
| 18 |  -5 -5 |
Worm.Win32.AutoIt.ar |
| 19 |  New New |
Exploit.JS.Agent.agc |
| 20 |  -5 -5 |
Email-Worm.Win32.Brontok.q |
Making an impression this month were two newcomers, Virus.Win32.Virut.ce and Exploit.HTML.CodeBaseExec.
Virut.ce entered near the top of our second ranking in February and now looks set to dominate the first ranking as well. New versions of the virus are appearing every day, which suggests that cybercriminals are monitoring how and when the malware is detected by antivirus programs and trying to increase the size of the botnet made up of infected machines. The epidemic caused by this virus is gaining momentum and May could well see Virut.ce moving several places up the rankings.
The second newcomer is a little piece of malware history – the first version of this program was detected by Kaspersky Lab way back in 2004. It featured regularly in our malware rankings in 2006, but is now flagged as a newcomer because the format and methods used to compile our Top Twenty rankings have changed. The malware exploits a simple vulnerability in versions 5.01, 5.5 and 6.0 of Internet Explorer. It seems that the cybercriminals are hoping that there will still be a significant number of people who have not installed the relevant security updates or who still use older versions of Internet Explorer.
Trojan.Win32.Chifrax.a dropped out of our ranking last October but has now returned and gone straight in at number four. This Trojan, like RaMag.a, is a modified WinRAR archive, which in this instance is a self-extracting archive.
The April ranking includes two script downloaders – Trojan.JS.Agent.xy and Exploit.JS.Agent.agc – that are perfect examples of the type of programs used in drive-by downloads, a topic we recently published a paper on https://securelist.com/.
All malicious, advertising and potentially unwanted programs in the first Top Twenty can be grouped according to the main classes of threat which we detect. In the past few months, the changes in the balance between these classes have not exceeded 5%.
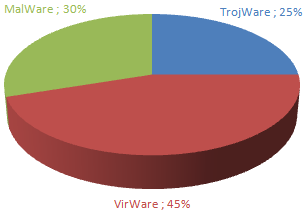
A total of 45190 unique malicious, advertising, and potentially unwanted programs were detected on users’ computers in April. This figure is almost exactly the same as last month’s.
The second Top Twenty presents data on which malicious programs most commonly infected objects detected on users’ computers. Malicious programs capable of infecting files make up the majority of this ranking.
| Position | Change in position | Name |
| 1 |  0 0 |
Virus.Win32.Sality.aa |
| 2 |  0 0 |
Worm.Win32.Mabezat.b |
| 3 |  0 0 |
Virus.Win32.Virut.ce |
| 4 |  0 0 |
Net-Worm.Win32.Nimda |
| 5 |  0 0 |
Virus.Win32.Xorer.du |
| 6 |  0 0 |
Virus.Win32.Sality.z |
| 7 |  1 1 |
Virus.Win32.Parite.b |
| 8 |  1 1 |
Virus.Win32.Virut.q |
| 9 |  -2 -2 |
Virus.Win32.Alman.b |
| 10 |  1 1 |
Virus.Win32.Small.l |
| 11 |  1 1 |
Email-Worm.Win32.Runouce.b |
| 12 |  1 1 |
Net-Worm.Win32.Kido.ih |
| 13 |  -3 -3 |
Trojan-Downloader.HTML.Agent.ml |
| 14 |  0 0 |
Virus.Win32.Virut.n |
| 15 |  0 0 |
Virus.Win32.Parite.a |
| 16 |  0 0 |
Virus.Win32.Hidrag.a |
| 17 |  3 3 |
Worm.Win32.Fujack.k |
| 18 |  0 0 |
P2P-Worm.Win32.Bacteraloh.h |
| 19 |  -2 -2 |
Trojan-Clicker.HTML.IFrame.acy |
| 20 |  New New |
Virus.Win32.Virut.av |
There was little change to the second Top Twenty ranking in April. The only real activity of note was the appearance of another Virut modification in the ranking – Virus.Win32.Virut.av. This virus was first detected by Kaspersky Lab in 2007 and is still active.
It means the Virut family claims four places in this Top Twenty, which amounts to 20% of the self-replicating programs in our second ranking.


















Monthly Malware Statistics: April 2009