
The Olympic Games are a huge event. And scammers are obviously going to try and exploit the interest they generate. We’ve already written about “Olympic” spam mailings. Now, SMS spammers have also appeared on the scene.
On February 10 we registered a spam mailing, which supposedly led to the live stream of an Olympic event:
“Olympic live stream in Sochi hxxp://mms****.ru/olympic.apk”
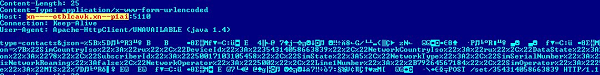
If unsuspecting users click on the link, a Trojan will be downloaded to their device. We detect the Trojan in question as HEUR:Trojan-SMS.AndroidOS.FakeInst.fb.
If this Trojan successfully downloads and launches, it addresses the C&C server and transfers the data gathered on the user’s phone, including the list of contacts.
After that the malicious program receives a command to send an SMS message.
The message is sent to one of Russia’s largest banks and contains the text BALANS. If the user is a client of the bank and uses a mobile banking service, he will receive a message with information about his account balance.
The Trojan intercepts all the messages and sends them to the scammer’s server. As a result, the criminal ends up with information about the victim’s bank account.
The bank targeted by the attack was not chosen at random – it offers its clients the option of topping up a mobile phone account from a bank card. This service required the user to send a specific type of text message to the bank’s number.
After receiving commands, the Trojan sends a text message to the bank’s number and money is transferred from the user’s bank account to the account of the infected phone.
The money is then transferred from the phone to accounts belonging to the scammers.
The Trojan can steal up to 10 000 rubles (approximately $285) per day, while all the messages about transfers will be hidden from the user.
Social engineering has always posed a danger. Users should be especially careful during major world events. At the very least, avoid clicking links sent in messages by people you don’t know. There’s always a risk that you’ll fall into a trap and lose quite a bit of money.
To minimize the risk of being infected by mobile malware, we recommend the following:
- Don’t turn off the vendor mode on mobile devices
- Don’t flag the field “install the applications from unknown sources”
- Only install apps from official channels (Google Play, Amazon Store, etc.)
- Pay attention to the rights requested by apps during installation
- If the set of requested permission rights does not correspond to an app’s intended functions (e.g., a game requests permission to send SMS messages), do not install the app
- Use security software





















Mobile Scammers Target Sports Fans