
This is the first report in a series from Kaspersky Lab tracking the evolution of malicious websites and malware delivered via the web.
In recent years, malware delivery mechanisms have changed from fixed media (diskettes) to email (e.g. the infamous LoveLetter email worm) and direct network attacks (e.g. CodeRed). The most recent step in the evolution process is a move to delivering malware via the world wide web.
We believe a few factors lie behind the increase in web-based malware. One is of course the relatively large number of vulnerabilities in Microsoft Internet Explorer that were identified between 2003-2006. Another is a slight philosophical or design incompatibility between most antivirus engines and the way websites are accessed through the Internet. Since most antivirus engines need a full copy of a file to determine if it is infected or not, that caused problems when it comes to scanning streams, as is the case with web pages. Of course, this issue can be addressed by solutions at proxy level that cache the stream then pass it to the antivirus engine once it is completely downloaded. However, these are not yet very popular.
Another factor that influenced the increase of web-based malware is probably the attempts made to block executable attachments in emails. Back in 2003 and 2004, when most malware was delivered via emails (as .EXE/.SCR/.PIF etc. files) many system administrators simply decided to completely ban executable content in email. A direct result of this was malware authors starting to use archives – for instance ZIP files – to distribute their creations. Back in 2006, Microsoft Office documents containing exploits were also a popular attack vector.
Malware authors then came up with a simple solution to address this issue: instead of delivering the body of the malicious program by email, they started sending URLs linking to websites which host the malware. Since a mail gateway antivirus solution only checks the body of the email, it will not be able to detect the malware linked to within the mail.
The factors listed above are among the reasons for the migration of malware being delivered directly to your inbox towards malware hosted on a web server, when the user will be tricked either into running it manually (social engineering), or, by exploiting a vulnerability in his/her web browser.
Methods of distribution
There are two major ways for malware hosted on a website to infect a machine.
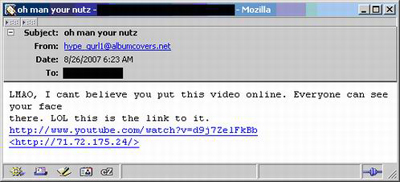
The first method involves a social engineering attack. For instance, the attacker sends an email containing a URL which purportedly links to something of interest. Here’s an example of such an email:
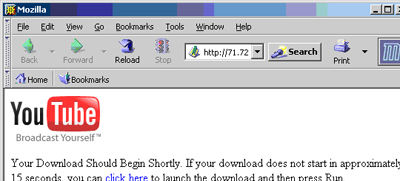
Fig. 1: Email containing link leading to malware
In the email above, the YouTube link is just a decoy and leads to a “video missing” page. The HREF link for the film, however, points to an IP address which is hosting a website. This is what the user will see when s/he visits it:
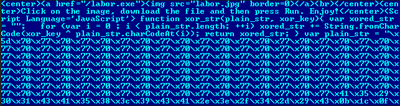
2. Fake website hosting the malicious executable
The “click here” link points to an executable file called “video.exe”, a variant of Zhelatin
(a.k.a the “Storm” worm.
The other method which malware uses to infect a system via the web is the use of web browser exploits. Here’s an example:
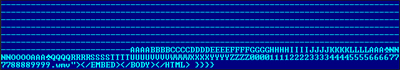
3. Source of an HTML page containing an exploit targeting Mozilla Firefox
The image above shows a fragment from a page hosting an encrypted web browser exploit. Most websites containing web browser exploits use some kind of obfuscation in order to avoid basic IDS detection which can be achieved by scanning the TCP/IP stream for known patterns as well as simple signature-based antivirus systems. Once decrypted, the exploit code can be analyzed:
4. Part of the decrypted exploit (Trojan-Downloader.JS.Agent.ep)
In this case, the malicious code simply tries to load a “.WMV” file with a very long name, which is a Windows Media Player Plug-In EMBED Overflow exploit (documented in Microsoft Security Bulletin MS06-006 – “Vulnerability in Windows Media Player Plug-in with Non-Microsoft Internet Browsers Could Allow Remote Code Execution (911564)). Modern browsers will pass such requests to Windows Media Player and if vulnerable, this will result in a system compromise. Interesting, even if the system has the latest version of the web browser, but a vulnerable Windows Media Player, the system will be infected.
As stated above, there are two major ways for malware to arrive on a victim machine via the web: through the use of social engineering techniques or through web browser exploits. It shouldn’t come as a surprise that in most cases, malware authors rely on a combination of these two in order to maximize the chances of success.
A good example of this combination of techniques is Zhelatin which was mentioned abover. The backend which distributes the worm seems to be written in PHP and before serving up the malicious webpage to the visitor, it does a couple of things. Most importantly of all, it checks the “User-Agent” browser identification string. If the browser identification string is something less common, like Safari on MacOS or Lynx on Linux, then it will attempt to serve a page which uses a social engineering technique. If the browser identification string appears to belong to Internet Explorer, e.g. “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)”, then it serves a special page which contains specific IE exploits. The same is true for Firefox.
TOP 20 malicious programs distributed via the web
Early in 2006, having observed the increase in malware distributed via the web as opposed to the then-classic email and network-based distribution methods, Kaspersky Lab developed “Akross”, a system which continuously monitors websites for malicious content. Since it was brought online, Akross has identified over 53000 distinct websites containing malware, of which over 28000 were identified during the first six months of 2007.
| Rank | Malware name | %% |
| 1 | Trojan-Downloader.Win32.Small.on | 11.26 |
| 2 | Trojan-Downloader.Win32.Zlob.bbr | 6.01 |
| 3 | Trojan-Downloader.Win32.Zlob.bjt | 4.59 |
| 4 | Trojan.Win32.DNSChanger.is | 3.19 |
| 5 | Trojan-Downloader.Win32.Zlob.bon | 3.17 |
| 6 | Trojan.Win32.DNSChanger.ih | 2.74 |
| 7 | Trojan.Win32.DNSChanger.hk | 2.50 |
| 8 | not-a-virus:Porn-Dialer.Win32.PluginAccess.s | 2.08 |
| 9 | Trojan.Win32.DNSChanger.io | 1.77 |
| 10 | Trojan.Win32.DNSChanger.jb | 1.02 |
| 11 | Trojan.Win32.DNSChanger.ik | 0.76 |
| 12 | Trojan-Downloader.Win32.Small.damtd> | 0.62 |
| 13 | Trojan-Spy.Win32.Banker.ciy | 0.59 |
| 14 | Trojan-PSW.Win32.OnLineGames.es | 0.48 |
| 15 | Backdoor.Win32.Rbot.gen | 0.48 |
| 16 | Trojan-Spy.Win32.Banker.anv | 0.42 |
| 17 | Trojan-Spy.Win32.Banker.awa | 0.40 |
| 18 | Trojan-Downloader.Win32.CWS.j | 0.36 |
| 19 | Trojan.Win32.DNSChanger.hj | 0.36 |
| 20 | Trojan-Spy.Win32.Bancos.zm | 0.34 |
5. Top 20 malicious programs downloaded from malicious
websites (Jan-July 2007)
Trojan-Downloader.Win32.Small.on, which tops the rankings, is actually a very generic Trojan downloader, which fetches another executable from a hardcoded URL and then executes it. Trojan downloaders are generally widely used in multi-level malicious websites, where usually a very memory tight exploit loads a small Trojan downloader which further loads the final payload or yet another downloader.
Zlob is another interesting case, with several variants populating the top of the chart. Zlob used to be very popular near the beginning of the year; however, it started fading out to such an extent that it is rarely seen now. Zlob was mostly installed using careful social engineering: specific websites were created which purported to be distribution points for video codecs which allow the playback of DVDs and various movie formats.
5. Fake website used for distributing Zlob variants
As the Top Twenty shows, DNSChanger is also widespread. There is actually a connection between Zlob and DNSChanger – we believe they were created by the same gang. Although DNSChanger underwent many changes during its lifespan, basically what it does is simply change the DNS servers from the user’s computer to a set of two specific IP addresses. The IP addresses are selected from a huge pool and the variation comes in distributing thousand of different DNSChanger binaries, each one setting the DNS servers to distinct IP addresses. While changing the DNS servers may not be regarded as something seriously malicious, an attacker who achieves this can actually do a lot of harm – for instance, redirecting websites such as Amazon.com or Bank Of America to phishing installations almost entirely without any sign of warning to the user. To complicate removal, the most recent DNSChangers include rootkit components and even download additional malware.
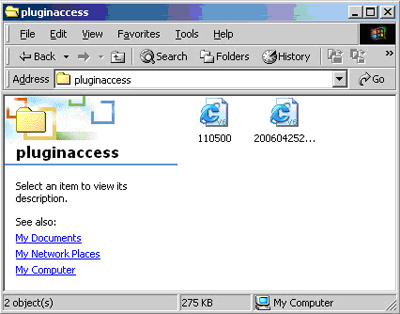
not-a-virus:Porn-Dialer.Win32.PluginAccess.s is, as its name suggests, not a virus. This classification denotes a family of programs which border between malicious and something some users might choose to have on your computer.
6. Two ‘not-a-virus:Porn-Dialer.Win32.PluginAccess.s’ executables with specific icons
PluginAccess.s sub-variants usually contain a large set of country-specific premium numbers inside, which are selected depending on the dialing rules of your Phone and Modem Options Control Panel applet in Windows. Once the user dials the premium number s/he will receive an authentication token which later allows access to various services through the Internet. Social engineering is the usual method used to install PluginAccess, with the program being touted as a method for obtaining access to various adult websites. The cost of access is mentioned and an attentive user will notice this accidental infections with PluginAccess are rare. This is why the program is not classified as malware per se but as “not-a-virus”. The reason for the popularity of such programs is probably due to the fact that they allow access to various paid services without the need for a credit card – the charge goes directly on the user’s phone bill.
Trojan-Spy.Win32.Banker.ciy is another notable presence in the top. Banker Trojans are malicious programs that attempt to steal e-banking credentials; some even go so far as to conduct man-in-the-middle attacks against the user’s web session. Particularly in recent months there has been an increasing number of attacks against banks using Trojans from the Banker family group. Trojan-Spy.Win32.Banker.ciy was even nominated as the “Greediest Trojan Targeting Plastic Cards” in Kaspersky Lab’s March 2007 Malware Miscellany (https://securelist.com/malware-miscellany-march-2007/30320/). It received the nomination as it targeted 5 plastic card systems instead of 3 – the previous record.
Another highly significant trend in malware evolution is the creation and distribution of Trojans which steal virtual items from online games such as World of Warcraft, EVE Online or Legend of Mir. These games are particularly popular in Asian countries, most notably in Korea and China, but the number of players around the world runs into the millions. Rare virtual items in these games can be incredibly expensive – and they are commonly traded on eBay or other auction sites either for virtual currency or for real money. As the demand for such items is very high, fraud involving virtual items is also on the rise. As an example of how much a virtual item can be worth, the most expensive space ship in EVE Online (http://www.eve-online.com/), equipped with a complete set of weapons and defenses, can cost as much as the equivalent of $10,000 real world money. It’s therefore no surprise there is a massive interest in the devlopment of malware that targets virtual property – there’s a clear profit motive.
Trojan-PSW.Win32.OnLineGames.es is a typical example of its genre. Though there are many modifications of this Trojan, most of them target the online game World of Warcraft (http://www.worldofwarcraft.com/). They monitor the game process and collect information about all keystrokes typed by the user, and this information is later forwarded to the attackers. They can then login to the game using the stolen account and sell on items, currency or characters. In order to avoid detection, complex virtual money laundering schemes are used, making the tracing of virtual property even more difficult.
And finally, a mention of Trojan-Downloader.Win32.CWS.j, another common site on malicious websites. This downloader is basically a small stub which downloads and installs variants of CWS, perhaps better known as CoolWebSearch. CoolWebSearch is a malicious program which was first reported circa 2003. Ever since, a huge number of variants have been found in the wild, most of them following the same pattern of hijacking the browser startup page and displaying pornographic pop-ups. Over time, CWS variants have become more and more complex and the latest versions include rootkit stealth components and retro features designed to terminate antivirus programs.
To summarize, most of the malicious content distributed via websites during the first half of 2007 can be split into four main categories: fake movie/DVD players and codecs which are installed through social engineering (Zlob etc.), online banking Trojans, malware targeting online games, and so-called ‘grey-border’ software which facilitates access to adult websites.
Top 20 countries hosting malware
So where does all this malware come from? In order to answer that question, it’s necessary to take a look at the solutions used by cyber criminals to host malware.
Malware hosted on the Internet can be present through a range of ways. It can be found on compromised home machines, which are infected with bots running tiny HTTP servers that become distribution points. Or it can be present on the hacked websites of ISPs. A very popular choice is companies that give away small amounts of free web space for users to build their own homepage. Such samples include www.pochta.ru, www.googlepages.com, www.100freemb.com, www.dump.ru or www.home.ro.
There have also been cases where stolen credit cards were used to purchase a domain name and a hosting package from a legitimate ISP; these were then used to distribute malware.
Earlier this year, a medium-sized US hosting company suffered an attack where cyber criminals exploited a vulnerable Control Panel version and gained access to all the accounts hosted on the company servers. The attackers went through the ‘index’ pages of all websites hosted on the compromised machines and added a small script which exploited an IE vulnerability. The exploit further installed malware, including a rootkit. Similarly, in February, the Super Bowl Dolphins Stadium website was hacked and exploits were injected in the page source code. Perhaps the most recent in this long line of website hacks is the Bank of India website hack, which took place at the end of August 2007. In this attack the home page code was modified to include an IE IFRAME exploit, which further served malware.
Listing the originating IP addresses for malware detected using Akross results in a chart showing the geographical distribution of malicious content on the web:
| Rank | Country | %% |
| 1 | China | 31.44 |
| 2 | United States | 25.90 |
| 3 | Russia | 11.05 |
| 4 | Brazil | 4.40 |
| 5 | South Korea | 3.64 |
| 6 | Argentina | 2.90 |
| 7 | Germany | 2.31 |
| 8 | France | 1.70 |
| 9 | Panama | 1.53 |
| 10 | Netherlands | 1.31 |
| 11 | Ukraine | 1.26 |
| 12 | Canada | 1.24 |
| 13 | Spain | 1.15 |
| 14 | United Kingdom | 1.15 |
| 15 | Hong Kong | 0.83 |
| 16 | Italy | 0.72 |
| 17 | Portugal | 0.70 |
| 18 | Romania | 0.68 |
| 19 | Taiwan | 0.65 |
| 20 | Malaysia | 0.52 |
8. Top 20 countries hosting malware
With 31.44%, China leads as the country where most malicious websites are located, followed by the United States with 25.90%. These countries have dominated almost every malware-related statistic in recent years, changing places depending on trends in malware writing and evolution of operating systems. It is interesting to note that while in China the most popular carrier for malware is hacked websites and so called “bullet-proof hosting”, in US it’s mostly hacked “.com” websites and legitimate hosting packages purchased with stolen cards.
Russia and Brazil occupy 3rd and 4th place. These countries are similar to each other in that most of the malware is hosted on “free hosting packages” – ISPs that offer the user the opportunity to upload his/ her website to one of their computers.
The other countries in the rankings seem to strike a balance between hacked machines, free hosting packages and legitimate hosting packages purchased with stolen money.
Special cases
While monitoring malicious websites during 2007, a number of websites were detected which were a little bit more than just the usual web server delivering an executable on request or serving an HTML page with an exploit inside.
The most interesting of these cases are probably those involving so called “server side polymorphism”. Traditionally, polymorphic malware was characterized by polymorphic viruses which modify their own code during each replication cycle. Since the code which performs the shapeshifting is included in the virus itself, the modifications can be predicted and thus, detection algorithms can be created and code for the task be written.
To give a practical example: earlier in 2006 we detected a URL that served an EXE file which looked different each time it was downloaded. In this particular case, the EXE file itself wasn’t varying too much (it did change from time to time). However, the last 42 bytes of the file would be different for each download. In this particular case, it seemed that a combination between a timestamp and the downloading IP address was added at the end as a kind of marker for the downloaded malware. Later, when the malware (which was a Trojan-Spy) reported back to its author, it included the marker from near the end of file. In this way the author would be able to correlate each unique version of the malware with the IP that downloaded it and with infections all over the world.
2006 also brought cases where the attacker would create between 1000 and 5000 instances of a Trojan by packing it with an internal tool which used a random encryption key each time it was called. Then, a PHP front-end would select a sample at random and serve it to the user. To an antivirus company unaware of the technique, this would initially look like a neverending stream of new infections, at least until enough samples could be collected to enable generic detection. Close monitoring of this website and other similar websites enabled us to create generic detection and in some cases, generic unpacking for the new Trojans that kept appearing.
Another interesting case was observed earlier this year, when we started closely monitoring a website serving Zhelatin samples. The samples on the server kept changing roughly every 90 seconds, but once in approximately every 500 samples, an interesting thing would happen. The encryption tool used seemed to rely on a random value which was about 9 bits in size. When the random value hit a specific number (0?), the resulting sample would be unencrypted. This allowed us to obtain a couple of 0-generation samples from the Zhelatin family – useful for analysis due to the lack of obfuscation.
Conclusions
With constantly changing methods of malware distribution it is expected that malware authors will continue to dream up new ways of infecting computers. Trends already include the distribution of malware through P2P networks or through open source software.
At the moment, the web is without doubt the preferred distribution media for malware authors and this method seemed to reach a peak in May 2007. Since then the number of new malicious websites has decreased somewhat. Although this is good news, there are still many new malicious websites appearing every day and the social engineering techniques or exploits used to lure the users in are becoming ever more and more sophisticated..
China and the US are two giants in terms of malicious websites; despite the best efforts of the authorities in these two countries, they seem to be the undisputed winners of this dubious honour. While it is usually possible to close a malicious website in the US in less than 48 hours, the same is not true in China. We are aware of malicious websites in China which have been active for more than a year and all attempts to close them down have failed. Given this it is likely that more and more malicious websites will be hosted in China, as it is becoming such a reliable hosting ground for malware.
Kaspersky Lab will continuing monitoring the situation; data in future articles will make it possible to see if the combined efforts of antivirus companies and cyber law enforcement bodies have a positive impact on the number of websites hosting malicious code.
In the meantime, users should keep their operating systems up to date and move from Internet Explorer 6 to browsers such as Firefox, IE7 and Opera which have a better security record. And finally an antivirus product capable of monitoring web traffic is essential – as this article has shown, this is now the main infection vector for malware.



















Malicious website evolution: January – June 2007