
These statistics are based on detection verdicts of Kaspersky Lab products received from users who consented to provide statistical data.
Q3 figures
According to Kaspersky Security Network:
- Kaspersky Lab solutions blocked 947,027,517 attacks launched from online resources located in 203 countries.
- 246,695,333 unique URLs were recognized as malicious by Web Anti-Virus components.
- Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 305,315 users.
- Ransomware attacks were registered on the computers of 259,867 unique users.
- Our File Anti-Virus logged 239,177,356 unique malicious and potentially unwanted objects.
- Kaspersky Lab products for mobile devices detected:
- 1,305,015 malicious installation packages
- 55,101 installation packages for mobile banking Trojans
- 13,075 installation packages for mobile ransomware Trojans.
Mobile threats
Q3 events
Perhaps the biggest news of the reporting period was the Trojan-Banker.AndroidOS.Asacub epidemic. It peaked in September when more than 250,000 unique users were attacked – and that only includes statistics for those with Kaspersky Lab’s mobile products installed on their devices.
Number of users attacked by the mobile banker Asacub in 2017 and 2018
The scale of the attack involving Asacub by far surpasses the largest attacks we have previously observed while monitoring mobile threats. The Trojan’s versions have sequential version numbers, suggesting the attacks were launched by just one threat actor. It’s impossible to count the total number of affected users, but it would need to be in the tens of thousands to make such a massive malicious campaign profitable.
Mobile threat statistics
In Q3 2018, Kaspersky Lab detected 1,305,015 malicious installation packages, which is 439,229 less packages than in the previous quarter.

Number of detected malicious installation packages, Q3 2017 – Q3 2018
Distribution of detected mobile apps by type
Among all the threats detected in Q3 2018, the lion’s share belonged to potentially unwanted RiskTool apps (52.05%); compared to the previous quarter, their share decreased by 3.3 percentage points (p.p.). Members of the RiskTool.AndroidOS.SMSreg family contributed most to this.

Distribution of newly detected mobile apps by type, Q2 – Q3 2018
Second place was occupied by Trojan-Dropper threats (22.57%), whose share increased by 9 p.p. Most files of this type belonged to the Trojan-Dropper.AndroidOS.Piom, Trojan-Dropper.AndroidOS.Wapnor and Trojan-Dropper.AndroidOS.Hqwar families.
The share of advertising apps continued to decrease and accounted for 6.44% of all detected threats (compared to 8.91% in Q2 2018).
The statistics show that the number of mobile financial threats has been rising throughout 2018, with the proportion of mobile banker Trojans increasing from 1.5% in Q1, to 4.38% of all detected threats in Q3.
TOP 20 mobile malware
| Verdicts* | %** | |
| 1 | DangerousObject.Multi.Generic | 55.85 |
| 2 | Trojan.AndroidOS.Boogr.gsh | 11.39 |
| 3 | Trojan-Banker.AndroidOS.Asacub.a | 5.28 |
| 4 | Trojan-Banker.AndroidOS.Asacub.snt | 5.10 |
| 5 | Trojan.AndroidOS.Piom.toe | 3.23 |
| 6 | Trojan.AndroidOS.Dvmap.a | 3.12 |
| 7 | Trojan.AndroidOS.Triada.dl | 3.09 |
| 8 | Trojan-Dropper.AndroidOS.Tiny.d | 2.88 |
| 9 | Trojan-Dropper.AndroidOS.Lezok.p | 2.78 |
| 10 | Trojan.AndroidOS.Agent.rt | 2,74 |
| 11 | Trojan-Banker.AndroidOS.Asacub.ci | 2.62 |
| 12 | Trojan-Banker.AndroidOS.Asacub.cg | 2.51 |
| 13 | Trojan-Banker.AndroidOS.Asacub.ce | 2.29 |
| 14 | Trojan-Dropper.AndroidOS.Agent.ii | 1,77 |
| 15 | Trojan-Dropper.AndroidOS.Hqwar.bb | 1.75 |
| 16 | Trojan.AndroidOS.Agent.pac | 1.61 |
| 17 | Trojan-Dropper.AndroidOS.Hqwar.ba | 1.59 |
| 18 | Exploit.AndroidOS.Lotoor.be | 1.55 |
| 19 | Trojan.AndroidOS.Piom.uwp | 1.48 |
| 20 | Trojan.AndroidOS.Piom.udo | 1.36 |
* This malware rating does not include potentially dangerous or unwanted programs such as RiskTool or adware.
** Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked.
First place in our TOP 20 once again went to DangerousObject.Multi.Generic (55.85%), the verdict we use for malware that’s detected using cloud technologies. Cloud technologies work when antivirus databases do not yet contain the data to detect a malicious program but the company’s cloud antivirus database already includes information about the object. This is basically how the very latest malicious programs are detected.
In second place was Trojan.AndroidOS.Boogr.gsh (11.39%). This verdict is given to files that our system recognizes as malicious based on machine learning..
Third and fourth places went to representatives of the Asacub mobile banker family – Trojan-Banker.AndroidOS.Asacub.a (5.28%) and Trojan-Banker.AndroidOS.Asacub.snt (5.10%).
Geography of mobile threats

Map of attempted infections using mobile malware, Q3 2018
TOP 10 countries by share of users attacked by mobile malware:
| Country* | %** | |
| 1 | Bangladesh | 35.91 |
| 2 | Nigeria | 28.54 |
| 3 | Iran | 28.07 |
| 4 | Tanzania | 28.03 |
| 5 | China | 25.61 |
| 6 | India | 25.25 |
| 7 | Pakistan | 25.08 |
| 8 | Indonesia | 25.02 |
| 9 | Philippines | 23.07 |
| 10 | Algeria | 22.88 |
* Countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000) are excluded.
** Unique users attacked in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q3 2018, Bangladesh (35.91%) retained first place in terms of the share of mobile users attacked. Nigeria (28.54%) came second. Third and fourth places were claimed by Iran (28.07%) and Tanzania (28.03%) respectively.
Mobile banking Trojans
During the reporting period, we detected 55,101 installation packages for mobile banking Trojans, which is nearly 6,000 fewer than in Q2 2018.
The largest contribution was made by Trojans belonging to the family Trojan-Banker.AndroidOS.Hqwar.jck – this verdict was given to 35% of all detected banking Trojans. Trojan-Banker.AndroidOS.Asacub came second, accounting for 29%.

Number of installation packages for mobile banking Trojans detected by Kaspersky Lab, Q3 2017 – Q3 2018
| Verdicts | %* | |
| 1 | Trojan-Banker.AndroidOS.Asacub.a | 33.27 |
| 2 | Trojan-Banker.AndroidOS.Asacub.snt | 32.16 |
| 3 | Trojan-Banker.AndroidOS.Asacub.ci | 16.51 |
| 4 | Trojan-Banker.AndroidOS.Asacub.cg | 15.84 |
| 5 | Trojan-Banker.AndroidOS.Asacub.ce | 14.46 |
| 6 | Trojan-Banker.AndroidOS.Asacub.cd | 6.66 |
| 7 | Trojan-Banker.AndroidOS.Svpeng.q | 3.25 |
| 8 | Trojan-Banker.AndroidOS.Asacub.cf | 2.07 |
| 9 | Trojan-Banker.AndroidOS.Asacub.bz | 1.68 |
| 10 | Trojan-Banker.AndroidOS.Asacub.bw | 1.68 |
* Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked by banking threats.
In Q3 2018, the TOP 10 rating of banking threats was almost exclusively (nine places out of 10) occupied by various versions of Trojan-Banker.AndroidOS.Asacub.

Geography of mobile banking threats, Q3 2018
TOP 10 countries by share of users attacked by mobile banking Trojans:
| Country* | %** | |
| 1 | Russia | 2.18 |
| 2 | South Africa | 2.16 |
| 3 | Malaysia | 0.53 |
| 4 | Ukraine | 0.41 |
| 5 | Australia | 0.39 |
| 6 | China | 0.35 |
| 7 | South Korea | 0.33 |
| 8 | Tajikistan | 0.30 |
| 9 | USA | 0.27 |
| 10 | Poland | 0.25 |
* Countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (under 10,000) are excluded.
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q3 2018, Russia ended up in first place in this TOP 10 because of the mass attacks involving the Asacub Trojan. The USA, the previous quarter’s leader, fell to ninth (0.27%) in Q3. Second and third place were occupied by South Africa (2.16%) and Malaysia (0.53%) respectively.
Mobile ransomware Trojans
In Q3 2018, we detected 13,075 installation packages for mobile ransomware Trojans, which is 1,044 fewer than in Q2.

Number of installation packages for mobile ransomware Trojans detected by Kaspersky Lab, Q3 2017 – Q3 2018
| Verdicts | %* | |
| 1 | Trojan-Ransom.AndroidOS.Svpeng.ag | 47.79 |
| 2 | Trojan-Ransom.AndroidOS.Svpeng.ah | 26.55 |
| 3 | Trojan-Ransom.AndroidOS.Zebt.a | 6.71 |
| 4 | Trojan-Ransom.AndroidOS.Fusob.h | 6.23 |
| 5 | Trojan-Ransom.AndroidOS.Rkor.g | 5.50 |
| 6 | Trojan-Ransom.AndroidOS.Svpeng.snt | 3.38 |
| 7 | Trojan-Ransom.AndroidOS.Svpeng.ab | 2.15 |
| 8 | Trojan-Ransom.AndroidOS.Egat.d | 1.94 |
| 9 | Trojan-Ransom.AndroidOS.Small.as | 1.43 |
| 10 | Trojan-Ransom.AndroidOS.Small.cj | 1.23 |
* Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus attacked by ransomware Trojans.
In Q3 2018, the most widespread mobile ransomware Trojans belonged to the Svpeng family – Trojan-Ransom.AndroidOS.Svpeng.ag (47.79%) and Trojan-Ransom.AndroidOS.Svpeng.ah (26.55%). Together, they accounted for three quarters of all mobile ransomware Trojan attacks. The once-popular families Zebt and Fusob were a distant third and fourth, represented by Trojan-Ransom.AndroidOS.Zebt.a (6.71%) and Trojan-Ransom.AndroidOS.Fusob.h (6.23%) respectively.

Geography of mobile ransomware Trojans, Q3 2018
TOP 10 countries by share of users attacked by mobile ransomware Trojans:
| Country* | %** | |
| 1 | USA | 1.73 |
| 2 | Kazakhstan | 0.36 |
| 3 | China | 0.14 |
| 4 | Italy | 0.12 |
| 5 | Iran | 0.11 |
| 6 | Belgium | 0.10 |
| 7 | Switzerland | 0.09 |
| 8 | Poland | 0.09 |
| 9 | Mexico | 0.09 |
| 10 | Romania | 0.08 |
* Countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (under 10,000) are excluded.
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
Just like in Q2, first place in the TOP 10 went to the United States (1.73%). Kazakhstan (0.6%) rose one place to second in Q3, while China (0.14%) rose from seventh to third.
Attacks on IoT devices
In this quarter’s report, we decided to only present the statistics for Telnet attacks, as this type of attack is used most frequently and employs the widest variety of malware types.
| Telnet | 99,4% |
| SSH | 0,6% |
The popularity of attacked services according to the number of unique IP addresses from which attacks were launched, Q3 2018
Telnet attacks

Geography of IP addresses of devices from which attacks were attempted on Kaspersky Lab honeypots, Q3 2018
TOP 10 countries hosting devices that were sources of attacks targeting Kaspersky Lab honeypots.
| Country | %* | |
| 1 | China | 27.15% |
| 2 | Brazil | 10.57% |
| 3 | Russia | 7.87% |
| 4 | Egypt | 7.43% |
| 5 | USA | 4.47% |
| 6 | South Korea | 3.57% |
| 7 | India | 2.59% |
| 8 | Taiwan | 2.17% |
| 9 | Turkey | 1.82% |
| 10 | Italy | 1.75% |
* Infected devices in each country as a percentage of the global number of IoT devices that attack via Telnet.
In Q3, China (23.15%) became the leader in terms of the number of unique IP addresses directing attacks against Kaspersky Lab honeypots. Brazil (10.57%) came second, after leading the rating in Q2. Russia (7.87%) was third.
Successful Telnet attacks saw the threat actors download Downloader.Linux.NyaDrop.b (62.24%) most often. This piece of malware is remarkable in that it contains a shell code that downloads other malware from the same source computer that has just infected the victim IoT device. The shell code doesn’t require any utilities – it performs all the necessary actions within itself using system calls. In other words, NyaDrop is a kind of universal soldier, capable of performing its tasks irrespective of the environment it has been launched in.
It was the Trojans of the family Backdoor.Linux.Hajime that downloaded NyaDrop most frequently, because this is a very convenient self-propagation method for Hajime. The flow chart in this case is of particular interest:
- After successfully infecting a device, Hajime scans the network to find new victims.
- As soon as a suitable device is found, the lightweight NyaDrop (just 480 bytes) is downloaded to it.
- NyaDrop contacts the device that was the infection source and slowly downloads Hajime, which is much larger.
All these actions are only required because it’s quite a challenge to download files via Telnet, though it is possible to execute commands. For example, this is what creating a NyaDrop file looks like:
|
1 |
echo -ne "\x7f\x45\x4c\x46\x01\x01\x01\x00\x00 |
480 bytes can be sent this way, but sending 60 KB becomes problematic.
TOP 10 malware downloaded to infected IoT devices in successful Telnet attacks
| Verdicts | %* | |
| 1 | Trojan-Downloader.Linux.NyaDrop.b | 62.24% |
| 2 | Backdoor.Linux.Mirai.ba | 16.31% |
| 3 | Backdoor.Linux.Mirai.b | 12.01% |
| 4 | Trojan-Downloader.Shell.Agent.p | 1.53% |
| 5 | Backdoor.Linux.Mirai.c | 1.33% |
| 6 | Backdoor.Linux.Gafgyt.ay | 1.15% |
| 7 | Backdoor.Linux.Mirai.au | 0.83% |
| 8 | Backdoor.Linux.Gafgyt.bj | 0.61% |
| 9 | Trojan-Downloader.Linux.Mirai.d | 0.51% |
| 10 | Backdoor.Linux.Mirai.bj | 0.37% |
* Proportion of downloads of each specific malicious program to IoT devices in successful Telnet attacks as a percentage of all malware downloads in such attacks.
The rating did not differ much from the previous quarter: half the top 10 is occupied by different modifications of Mirai, which is the most widespread IoT malware program to date.
Financial threats
Q3 events
The banking Trojan DanaBot that was detected in Q2 continued to develop rapidly in Q3. A new modification included not only an updated C&C/bot communication protocol but also an extended list of organizations targeted by the malware. Its prime targets in Q2 were located in Australia and Poland, but in Q3 organizations from Austria, Germany and Italy were also included.
To recap, DanaBot has a modular structure and is capable of loading extra modules to intercept traffic and steal passwords and crypto wallets. The Trojan spread via spam messages containing a malicious office document, which subsequently loaded the Trojan’s main body.
Financial threat statistics
In Q3 2018, Kaspersky Lab solutions blocked attempts to launch one or more malicious programs designed to steal money from bank accounts on the computers of 305,315 users.

Number of unique users attacked by financial malware, Q3 2018
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, we calculated the share of users of Kaspersky Lab products in each country that faced this threat during the reporting period out of all users of our products in that country.
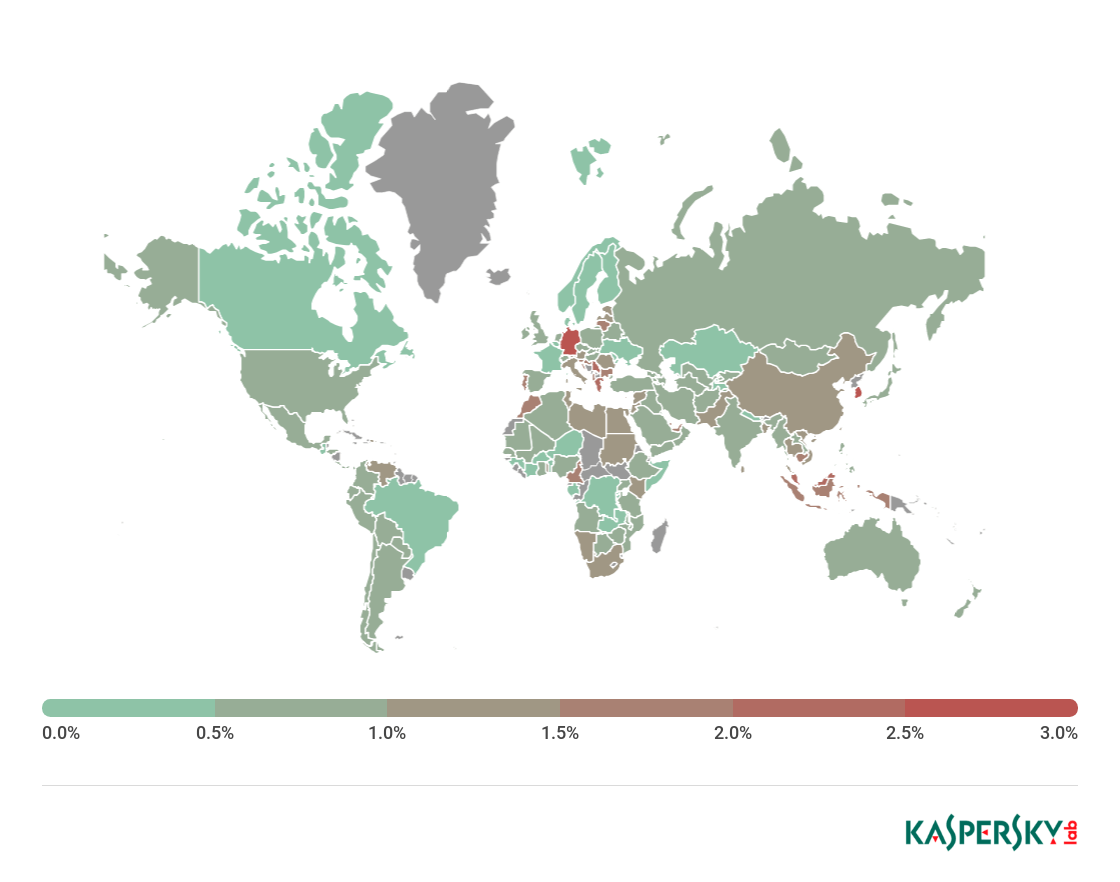
Geography of banking malware attacks, Q3 2018
TOP 10 countries by percentage of attacked users
| Country* | %** | |
| 1 | Germany | 3.0 |
| 2 | South Korea | 2.8 |
| 3 | Greece | 2.3 |
| 4 | Malaysia | 2.1 |
| 5 | Serbia | 2.0 |
| 6 | United Arab Emirates | 1.9 |
| 7 | Portugal | 1.9 |
| 8 | Lithuania | 1.9 |
| 9 | Indonesia | 1.8 |
| 10 | Cambodia | 1.8 |
* Countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000) are excluded.
** Unique users attacked by mobile banking Trojans in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in that country.
TOP 10 banking malware families
| Name | Verdicts | %* | ||
| 1 | Zbot | Trojan.Win32.Zbot | 25.8 | |
| 2 | Nymaim | Trojan.Win32.Nymaim | 18.4 | |
| 3 | SpyEye | Backdoor.Win32.SpyEye | 18.1 | |
| 4 | RTM | Trojan-Banker.Win32.RTM | 9.2 | |
| 5 | Emotet | Backdoor.Win32.Emotet | 5.9 | |
| 6 | Neurevt | Trojan.Win32.Neurevt | 4.7 | |
| 7 | Tinba | Trojan-Banker.Win32.Tinba | 2.8 | |
| 8 | NeutrinoPOS | Trojan-Banker.Win32.NeutrinoPOS | 2.4 | |
| 9 | Gozi | Trojan.Win32. Gozi | 1.6 | |
| 10 | Trickster | Trojan.Win32.Trickster | 1.4 |
* Unique users attacked by the given malware as a percentage of all users that were attacked by banking threats.
In Q3 2018, there were three newcomers to this TOP 10: Trojan.Win32.Trickster (1.4%), Trojan-Banker.Win32.Tinba (2.8%) and Trojan-Banker.Win32.RTM (9.2%). The latter shot to fourth place thanks to a mass mailing campaign in mid-July that involved emails with malicious attachments and links.
Overall, the TOP 3 remained the same, though Trojan.Win32.Nymaim ceded some ground – from 27% in Q2 to 18.4% in Q3 – and fell to second.
Cryptoware programs
Q3 events
In early July, Kaspersky Lab experts detected an unusual modification of the notorious Rakhni Trojan. What drew the analysts’ attention was that in some cases the downloader now delivers a miner instead of ransomware as was always the case with this malware family in the past.
August saw the detection of the rather unusual KeyPass ransomware. Its creators apparently decided to make provisions for all possible infection scenarios – via spam, with the help of exploit packs, and via manual brute-force attacks on the passwords of the remote access system, after which the Trojan is launched. The KeyPass Trojan can run in both hidden mode and GUI mode so the threat actor can configure encryption parameters.
Meanwhile, law enforcement agencies continue their systematic battle against ransomware. Following several years of investigations, two cybercriminals who distributed the CoinVault ransomware were found guilty in the Netherlands.
Statistics
Number of new modifications
In Q3, the number of detected cryptoware modifications was significantly lower than in Q2 and close to that of Q1.

Number of new cryptoware modifications, Q4 2017 – Q3 2018
Number of users attacked by Trojan cryptors
In Q3 2018, Kaspersky Lab products protected 259,867 unique KSN users from Trojan cryptors. The total number of attacked users rose both against Q2 and on a month-on-month basis during Q3. In September, we observed a significant rise in the number of attempted infections, which appears to correlate with people returning from seasonal vacations.

Number of unique users attacked by Trojan cryptors, Q3 2018
Geography of attacks

Geography of Trojan cryptors attacks, Q3 2018
TOP 10 countries attacked by Trojan cryptors
| Country* | %** | |
| 1 | Bangladesh | 5.80 |
| 2 | Uzbekistan | 3.77 |
| 3 | Nepal | 2.18 |
| 4 | Pakistan | 1.41 |
| 5 | India | 1.27 |
| 6 | Indonesia | 1.21 |
| 7 | Vietnam | 1.20 |
| 8 | Mozambique | 1.06 |
| 9 | China | 1.05 |
| 10 | Kazakhstan | 0.84 |
* Countries with relatively few Kaspersky Lab users (under 50,000) are excluded.
** Unique users whose computers were attacked by Trojan cryptors as a percentage of all unique users of Kaspersky Lab products in that country.
Most of the places in this rating are occupied by Asian countries. Bangladesh tops the list with 5.8%, followed by Uzbekistan (3.77%) and the newcomer Nepal (2.18%) in third. Pakistan (1.41%) came fourth, while China (1.05%) fell from sixth to ninth and Vietnam (1.20%) fell four places to seventh.
TOP 10 most widespread cryptor families
| Name | Verdicts | %* | |||
| 1 | WannaCry | Trojan-Ransom.Win32.Wanna | 28.72% | ||
| 2 | (generic verdict) | Trojan-Ransom.Win32.Phny | 13.70% | ||
| 3 | GandCrab | Trojan-Ransom.Win32.GandCrypt | 12.31% | ||
| 4 | Cryakl | Trojan-Ransom.Win32.Cryakl | 9.30% | ||
| 5 | (generic verdict) | Trojan-Ransom.Win32.Gen | 2.99% | ||
| 6 | (generic verdict) | Trojan-Ransom.Win32.Cryptor | 2.58% | ||
| 7 | PolyRansom/VirLock | Virus.Win32.PolyRansom | 2.33% | ||
| 8 | Shade | Trojan-Ransom.Win32.Shade | 1,99% | ||
| 9 | Crysis | Trojan-Ransom.Win32.Crusis | 1.70% | ||
| 10 | (generic verdict) | Trojan-Ransom.Win32.Encoder | 1.70% | ||
* Unique Kaspersky Lab users attacked by a specific family of Trojan cryptors as a percentage of all users attacked by Trojan cryptors.
The leading 10 places are increasingly occupied by generic verdicts, suggesting widespread cryptors are effectively detected by automatic intelligent systems. WannaCry (28.72%) still leads the way among specific cryptoware families. This quarter saw two new versions of the Trojan GandCrab (12.31%) emerge, meaning it remained in the most widespread ransomware rating. Among the old-timers that remained in the TOP 10 were PolyRansom, Cryakl, Shade, and Crysis, while Cerber and Purgen failed to gain much distribution this quarter.
Cryptominers
As we already reported in Ransomware and malicious cryptominers in 2016-2018, ransomware is gradually declining and being replaced with cryptocurrency miners. Therefore, this year we decided to start publishing quarterly reports on the status of this type of threat. At the same time, we began using a broader range of verdicts as a basis for collecting statistics on miners, so the statistics in this year’s quarterly reports may not be consistent with the data from our earlier publications.
Statistics
Number of new modifications
In Q3 2018, Kaspersky Lab solutions detected 31,991 new modifications of miners.

Number of new miner modifications, Q3 2018
Number of users attacked by cryptominers
In Q3, Kaspersky Lab products detected mining programs on the computers of 1,787,994 KSN users around the world.

Number of unique users attacked by cryptominers, Q3 2018
Cryptomining activity in September was comparable to that of June 2018, though we observed an overall downward trend in Q3.
Geography of attacks
TOP 10 countries by percentage of attacked users
| Country* | %** | |
| 1 | Afghanistan | 16.85% |
| 2 | Uzbekistan | 14.23% |
| 3 | Kazakhstan | 10.17% |
| 4 | Belarus | 9.73% |
| 5 | Vietnam | 8.96% |
| 6 | Indonesia | 8.80% |
| 7 | Mozambique | 8.50% |
| 8 | Ukraine | 7.60% |
| 9 | Tanzania | 7.51% |
| 10 | Azerbaijan | 7.13% |
* Countries with relatively few Kaspersky Lab product users (under 50,000) are excluded.
** Unique Kaspersky Lab users whose computers were targeted by miners as a percentage of all unique users of Kaspersky Lab products in the country.
Vulnerable apps used by cybercriminals
The distribution of platforms most often targeted by exploits showed very little change from Q2. Microsoft Office applications (70%) are still the most frequently targeted – five times more than web browsers, the second most attacked platform.
Although quite some time has passed since security patches were released for the two vulnerabilities most often used in cyberattacks – CVE-2017-11882 and CVE-2018-0802 – the exploits targeting the Equation Editor component still remain the most popular for sending malicious spam messages.
An exploit targeting the vulnerability CVE-2018-8373 in the VBScript engine (which was patched in late August) was detected in the wild and affected Internet Explorer 9–11. However, we are currently observing only limited use of this vulnerability by cybercriminals. This is most probably due to Internet Explorer not being very popular, as well as the fact that VBScript execution is disabled by default in recent versions of Windows 10.

Distribution of exploits used by cybercriminals, by type of attacked application, Q3 2018
Q3 was also marked by the emergence of two atypical 0-day vulnerabilities – CVE-2018-8414 and CVE-2018-8440. They are peculiar because information about the existence of these vulnerabilities, along with detailed descriptions and all the files required to reproduce them, was leaked to the public domain long before official patches were released for them.
In the case of CVE-2018-8414, an article was published back in June with a detailed description of how SettingContent-ms files can be used to execute arbitrary code in Windows. However, the security patch to fix this vulnerability was only released in Q3, one month after the article became publicly available and active exploitation of the vulnerability had already began. The researchers who described this technique reported it to Microsoft, but initially it was not recognized as a vulnerability requiring a patch. Microsoft reconsidered after cybercriminals began actively using these files to deliver malicious payloads, and a patch was released on July 14. According to KSN statistics, the SettingContent-ms files didn’t gain much popularity among cybercriminals, and after the security patch was released, their use ceased altogether.
Another interesting case was the CVE-2018-8440 security breach. Just like in the case above, all the information required for reproduction was deliberately published by a researcher, and threat actors naturally took advantage. CVE-2018-8440 is a privilege-escalation vulnerability, allowing an attacker to escalate their privilege in the system to the highest level – System. The vulnerability is based on how Windows processes a task scheduler advanced local procedure call (ALPC). The vulnerable ALPC procedure makes it possible to change the discretionary access control list (DACL) for files located in a directory that doesn’t require special privileges to access. To escalate privileges, the attacker exploits the vulnerability in the ALPC to change access rights to a system file, and then that system file is overwritten by an unprivileged user.
Attacks via web resources
The statistics in this chapter are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are created by cybercriminals, while web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks. In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In the third quarter of 2018, Kaspersky Lab solutions blocked 947,027,517 attacks launched from web resources located in 203 countries around the world. 246,695,333 unique URLs were recognized as malicious by web antivirus components.
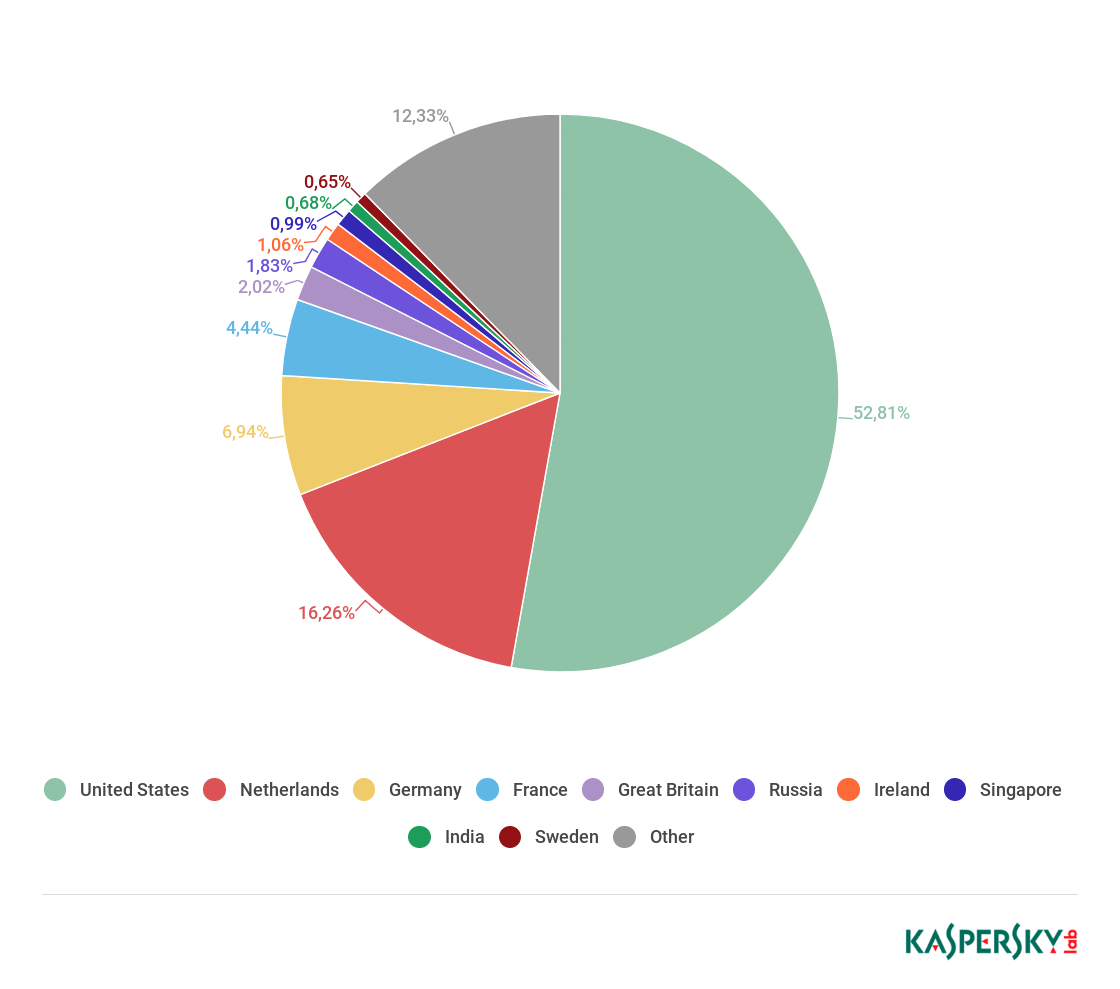
Distribution of web attack sources by country, Q3 2018
In Q3, the USA (52.81%) was home to most sources of web attacks. Overall, the leading four sources of web attacks remained unchanged from Q2: the USA is followed by the Netherlands (16.26%), Germany (6.94%) and France (4.4%).
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users on whose computers Web Anti-Virus was triggered in each country during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malware-class malicious programs; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
| Country* | %** | |
| 1 | Venezuela | 35.88 |
| 2 | Albania | 32.48 |
| 3 | Algeria | 32.41 |
| 4 | Belarus | 31.08 |
| 5 | Armenia | 29.16 |
| 6 | Ukraine | 28.67 |
| 7 | Moldova | 28.64 |
| 8 | Azerbaijan | 26.67 |
| 9 | Kyrgyzstan | 25.80 |
| 10 | Serbia | 25.38 |
| 11 | Mauritania | 24.89 |
| 12 | Indonesia | 24.68 |
| 13 | Romania | 24.56 |
| 14 | Qatar | 23.99 |
| 15 | Kazakhstan | 23.93 |
| 16 | Philippines | 23.84 |
| 17 | Lithuania | 23.70 |
| 18 | Djibouti | 23.70 |
| 19 | Latvia | 23.09 |
| 20 | Honduras | 22.97 |
* Countries with relatively few Kaspersky Lab users (under 10,000) are excluded.
** Unique users targeted by malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 18.92% of internet users’ computers worldwide experienced at least one malware-class web attack.

Geography of malicious web attacks in Q3 2018
Local threats
Local infection statistics for user computers are an important indicator: they reflect threats that have penetrated computer systems by infecting files or via removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media. Analysis takes account of the malicious programs identified on user computers or on removable media connected to computers – flash drives, camera memory cards, phones and external hard drives.
In Q3 2018, Kaspersky Lab’s file antivirus detected 239,177,356 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
The rating includes only malware-class attacks. It does not include File Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
| Country* | %** | |
| 1 | Uzbekistan | 54.93 |
| 2 | Afghanistan | 54.15 |
| 3 | Yemen | 52.12 |
| 4 | Turkmenistan | 49.61 |
| 5 | Tajikistan | 49.05 |
| 6 | Laos | 47.93 |
| 7 | Syria | 47.45 |
| 8 | Vietnam | 46.07 |
| 9 | Bangladesh | 45.93 |
| 10 | Sudan | 45.30 |
| 11 | Ethiopia | 45.17 |
| 12 | Myanmar | 44.61 |
| 13 | Mozambique | 42.65 |
| 14 | Kyrgyzstan | 42.38 |
| 15 | Iraq | 42.25 |
| 16 | Rwanda | 42.06 |
| 17 | Algeria | 41.95 |
| 18 | Cameroon | 40.98 |
| 19 | Malawi | 40.70 |
| 20 | Belarus | 40.66 |
* Countries with relatively few Kaspersky Lab users (under 10,000) are excluded.
** Unique users on whose computers malware-class local threats were blocked, as a percentage of all unique users of Kaspersky Lab products in the country.

Geography of local malware attacks in Q3 2018
On average, 22.53% of computers globally faced at least one malware-class local threat in Q3.
IT threat evolution Q3 2018. Statistics
























joe
Just ask, can Kaspersky be protected for all this?
Dave Marksmen
Yes, Kaspersky is a real security machine. Its more reliable than the Pentagons current protocols!