
When iPhone jailbreaking was declared legal earlier this year, in June, Apple fans from all around the world rejoiced. Sites such as Jailbreakme.com appeared, which make it simple and straightforward to jailbreak older iPhones.
Indeed, the keyword here is “older” – when Apple started selling the new iPhone 4G, it also patched the vulnerabilities that made it possible for users to jailbreak it.
This is why until now it’s been impossible to jailbreak newly purchased iPhones that come with iOS 4.0.2 or iOS 4.1.
But earlier this month, though, a hacker going by the handle pod2g announced that he was working on a new exploit that would make it possible to jailbreak all existing iPhones through a vulnerability in the bootrom. Due to its nature, this vulnerability will be extremely hard for Apple to fix in software, if not impossible. So if the exploit ever appears, it would mean it would be possible to jailbreak all existing iPhones and iPads through a simple exploit, regardless of the OS version being run. A groundbreaking announcement indeed.
Still, as of September 20, there was no exploit available from pod2g that would jailbreak iOS 4.0.2 and iOS 4.1. Users of iPhone 4Gs running these versions of iOS are pretty much unable to do anything, unless they downgrade the OS to an earlier version. And for the iPhones that came with 4.0.2 from the factory, it’s impossible to downgrade them.
You might wonder why I’m talking about this topic. After all, “hacker”, “exploit” and “vulnerability” are some quite emotive terms, and you might think we wouldn’t want to be encouraging this sort of behavior. But there’s a good reason for this post: jailbreaking iPhones is, as I said, now legal, but there are lots of bad guys out there who are looking to take advantage. I see this post as kind of being like safe sex advice: the more you know, the better protected you’re going to be.
Cybercriminals have definitely been riding the buzz around the supposed jailbreaking tool. It’s presumed to be called “Greenpois0n” and it’s expected to be released any day now. Not surprisingly, we’ve seen a number of fake “Greenpois0n” Trojans.
If you search for the Greenpois0n tool on Google or popular torrent sites you might be in for a surprise:
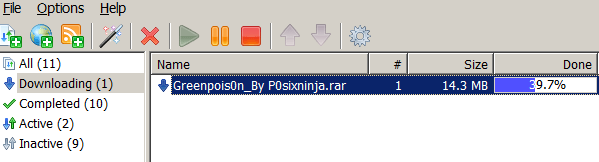
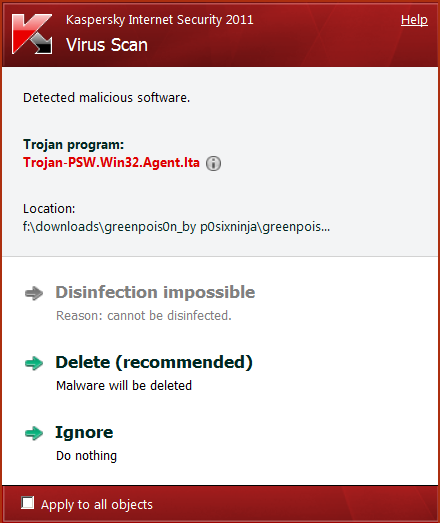
All the existing “greenpois0n” archives at the moment contain Trojans designed to steal passwords and other private data from your system:
In addition to the Trojans, fake (rogue) jailbreaking websites have appeared; they pretend to sell tools that can jailbreak any version of iPhone with any version of iOS. The average cost for these is $25-$40.
As usual, you shouldn’t be fooled: currently there is no working jailbreaking tool for iPhone 4s running iOS 4.0.2 / 4.1. If the pod2g exploit turns out to be valid, there’ll no doubt be a lot of noise about it. Until then, stay away from fake jailbreaking tools and websites!






















iPhone Jailbreaking, Greenpois0n and SHAtter Trojans