
Earlier this year, about 6.5 million LinkedIn account password hashes were published on a hackers forum. The hashes were simple SHA1 digests computed from the users passwords, as stored into the LinkedIn backend infrastructure.
It didnt take long for hackers to start cracking them, with over half of them cracked in almost no time.
There are two main reasons why such fast cracking was possible:
* the usage of the SHA1 function itself
* fast GPUs
Lets take a look look at both.
The SHA1 function was mainly designed to replace the weaker function MD5. It was created to be fast, and indeed it is. On an AMD / ATI 7970 graphic card, hashcat (see https://hashcat.net/oclhashcat-plus/) calculates a bit over two billion SHA1 hashes per second. This means a lot of combinations can be tested in a very short time.
To overcome this problem, modern and more secure algorithms exist, such as the sha512crypt function used in Ubuntu and recent versions of Fedora Core Linux. Instead of 2 billion hashes per second, the same GPU card cracks only a bit over 12,000 sha512crypt combinations per second. For instance, checking one billion sha512crypt combinations takes about 24 hours; but less than 1 second for SHA1.
Because of todays fast GPUs, one good advice when it comes to security is to choose a complex password, that:
* includes both uppercase and lowercase chars
* includes at least one space character
* includes numbers
* includes several symbols such as !@#
* it is not based on a known word
* its at least 12 chars in size, but the longer the better
Many of the people I know use passphrases that are between 20 and 50 chars in size. This is a good advice which makes it unlikely that even in the event that your password hash is leaked, nobody will crack it.
Imagine my surprise today when I tried logging into an older Hotmail account and got the following:
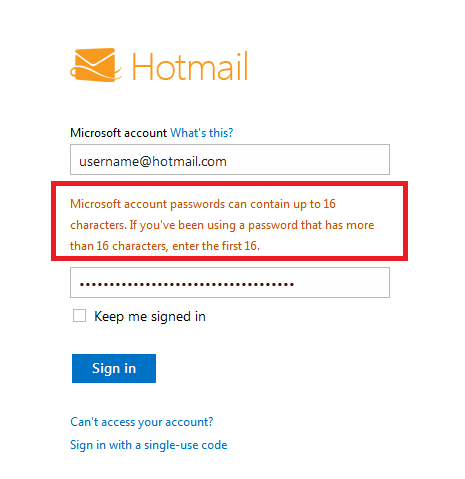
Microsoft account passwords can contain up to 16 characters.
If you’ve been using a password that has more than 16 characters, enter the first 16.
My previous password has been around 30 chars in size and now, it doesnt work anymore. However, I could login by typing just the first 16 chars.
This limitation is well known (see Graham Cluleys excellent post on the password limits of various services) however, what caught my attention was that by cutting the password to 16 chars, it would work.
To pull this trick with older passwords, Microsoft had two choices:
* store full plaintext passwords in their db; compare the first 16 chars only
* calculate the hash only on the first 16; ignore the rest
Storing plaintext passwords for online services is a definite no-no in security. The other choice could mean that since its inception, Hotmail was silently using only the first 16 chars of the password.
To be honest, Im not sure which one is worse.
PS: My teacher said always think positively and try to end with an optimistic note. So here goes: Thanks Google for GMail.




















Hotmail: Your password was too long, so we fixed it for you