
Many things have been told already about the latest Skype malware spread via instant messages. However I just wanted to add something not mentioned yet. The first thing is about when the attack was launched first. According to Google Short URL service it first surfaced on Oct 6th:
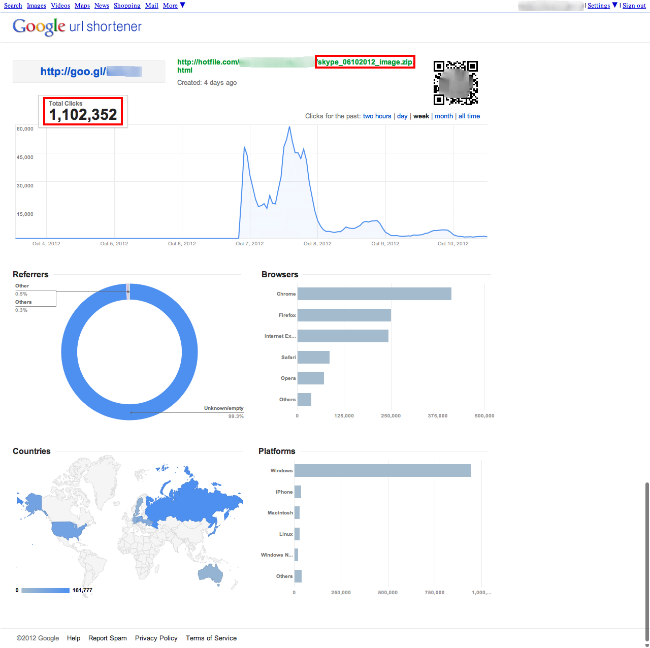
To be exact it happened at 8:00 PM Ecuadorian time (7:00 PM ET). In just 2 hours the number of clicks grew up to 484,111 clicks. I’d say most of the people who clicked got infected since the initial Virus Total (https://www.virustotal.com/) detection for the malware was only from 2 of the 44 AV engines. The actual detection now is 27/43 engines and the actual number of clicks is more than 1 million!
Despite the fact that the original Hotfile malicious URL is already dead, people are still clicking on it. It means the malicious campaign is maintaining a low level of activity and where most of the victims are in Russia. It’s a controversial situation because one of the payloads is the stealing of credit card information from one of the Ecuadorian banks!
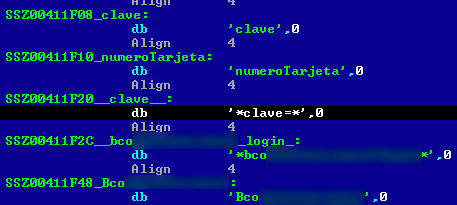
The malware “speaks” many languages, so when I obtained a sample it was spreading between Venezuelan users saying “¿es ésta tu foto de perfil nuevo?” (Translation: Is this your new profile picture?) It speaks at least; Spanish, Portuguese, English and Latvian languages and additionally steals user account information from: .iknowthatgirl, YouPorn, Brazzers, Webnames, Dotster, Enom, 1and1, Moniker, Namecheap, Godaddy, Alertpay, Netflix, Thepiratebay, Torrentleech, Vip-file, Sms4file, Letitbit, Whatcd, eBay, Twitter, Facebook, Yahoo, PayPal and many other services.
The Trojan has an autorun functionality to spread via USB devices. It’s able to spread via MSN Messenger too and all locally saved Skype passwords on the same infected machine by switching automatically between available accounts.
Kaspersky detects this threat as Trojan.Win32.Bublik.jdb





















Hidden Details about the last Skype Spread Malware