
There have been several reports about malware hosted on Mozilla and Google code servers. Now we also found malware hosted on My Opera community servers. The screenshot below shows an example of this:
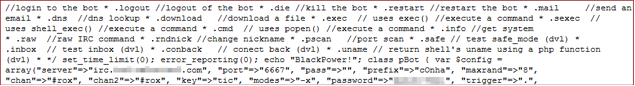
It’s a PHP based IRC botnet. Analyzing the code I found some evidences that it comes from Brazil.
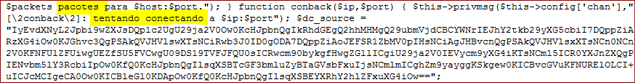
We can see that criminals appreciate and actively use any and all available free web space.
Based on the statistics from one of our proactive web crawlers, I took a look at which free web hosts are most popular among criminals for uploading and spreading malware. The following graph shows the top 10 free web hosts used by criminals during the last 8 months:
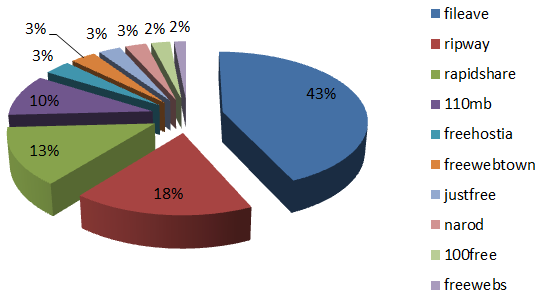
Fileave is a really well known server for hosting tons of different kinds of malware. I noticed that some secure DNS providers block access to the domains listed above and show an alert message stating that these sites are known sources of phishing and malware.
So, what does that tell us? The usual – when you browse the internet always check links before clicking, and if the domain is suspicious, don’t. Just don’t click. And if you’re owner of a web site, make sure to secure your server properly to prevent the criminals from compromising it easily.






















Google, Mozilla and now Opera… Who’s next?