
Background
Recently we came across a new family of cross-platform backdoors for desktop environments. First we got the Linux variant, and with information extracted from its binary, we were able to find the variant for Windows desktops, too. Not only that, but the Windows version was additionally equipped with a valid code signing signature. Let´s have a look at both of them.
DropboxCache aka Backdoor.Linux.Mokes.a
This backdoor for Linux-based operating systems comes packed via UPX and is full of features to monitor the victim’s activities, including code to capture audio and take screenshots.
![]()
After its first execution, the binary checks its own file path and, if necessary, copies itself to one of the following locations:
- $HOME/$QT-GenericDataLocation/.mozilla/firefox/profiled
- $HOME/$QT-GenericDataLocation/.dropbox/DropboxCache
One example would be this location: $HOME/.local/share/.dropbox/DropboxCache. To achieve persistence, it uses this not very stealthy method: it just creates a .desktop-file in $HOME/.config/autostart/$filename.desktop. Here’s the template for this:
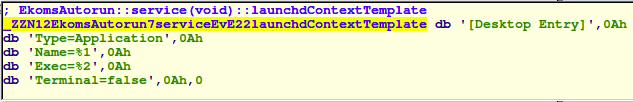
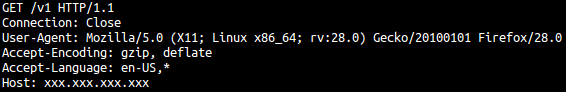
Next, it connects to its hardcoded C&C Server. From this point, it performs an http request every minute:
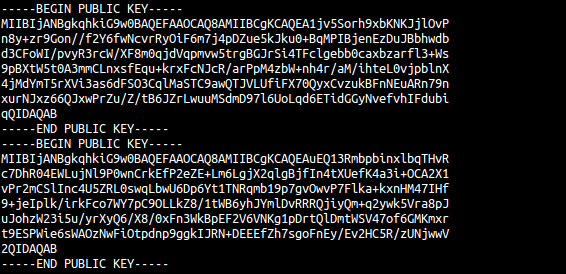
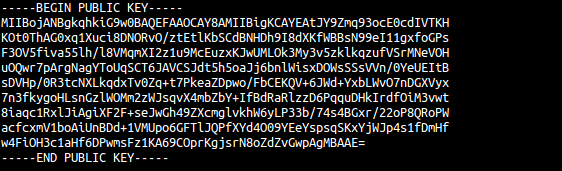
This “heartbeat” request replies with a one-byte image. To upload and receive data and commands, it connects to TCP port 433 using a custom protocol and AES encryption. The binary comes with the following hardcoded public keys:
The malware then collects gathered information from the keylogger, audio captures and screenshots in /tmp/. Later it will upload collected data to the C&C.
- /tmp/ss0-DDMMyy-HHmmss-nnn.sst (Screenshots, JPEG, every 30 sec.)
- /tmp/aa0-DDMMyy-HHmmss-nnn.aat (Audiocaptures, WAV)
- /tmp/kk0-DDMMyy-HHmmss-nnn.kkt (Keylogs)
- /tmp/dd0-DDMMyy-HHmmss-nnn.ddt (Arbitrary Data)
DDMMyy = date: 280116 = 2016-01-28
HHmmss = time: 154411 = 15:44:11
nnn = milliseconds.
However, audio capturing is not activated in the event timer of this binary, just like the keylogging feature. Since the authors have statically linked libqt, xkbcommon (the library to handle keyboard descriptions) and OpenSSL (1.0.2c) to the binary, the size of the binary is over 13MB. The criminals also didn’t make any effort to obfuscate the binary in any way. In fact, the binary contains almost all symbols, which is very useful during analysis.
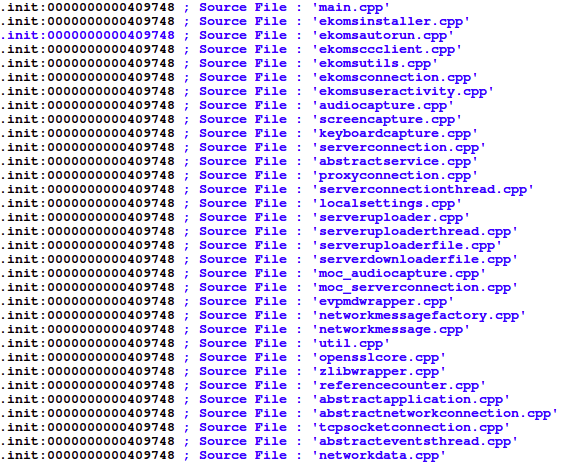
There are also references to the author’s source files:
Apparently, it’s written in C++ and Qt, a cross-platform application framework. According to the binary’s metadata it was compiled using “GCC 4.8.4 (Ubuntu 4.8.4-2ubuntu1~14.04)” on Ubuntu 14.04 LTS “Trusty Tahr”. According to the qt_instdate timestamp, the last time the Qt sources were configured was on 2015-09-26 (qt/qtbase.git: deprecated), which implies the compilation time of the malware to be not earlier than end of September 2015.
We detect this type of malware as Backdoor.Linux.Mokes.a.
OLMyJuxM.exe aka Backdoor.Win32.Mokes.imv
Just a few days ago, we came across a rather familiar looking sample, although it was compiled for machines running Microsoft Windows. It quickly turned out to be a 32-bit Windows variant of Backdoor.Linux.Mokes.a.
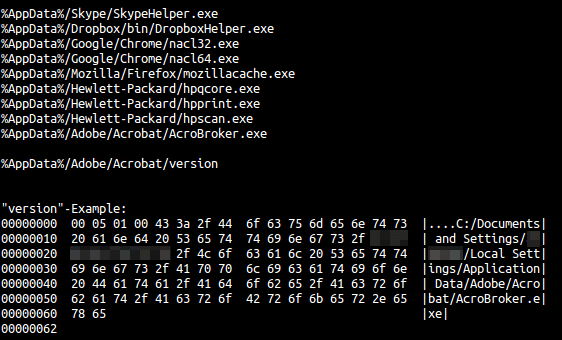
After execution, the malware randomly chooses one of nine different locations in %AppData% to persistently install itself on the machine. The binary also creates a “version”-file in the same folder. As its name implies, it stores just version information, together with the full installation path of the malware itself:
Then the corresponding registry keys are created in HKCU\Software\Microsoft\Windows\CurrentVersion\Run to ensure persistence in the system.
After the malware has executed its own copy in the new location, the SetWindowsHook API is utilized to establish keylogger functionality and to monitor mouse inputs and internal messages posted to the message queue.
The next stage in its operation is to contact the hardcoded C&C server. Besides the different IP addresses and encryption key, we see almost identical behavior.
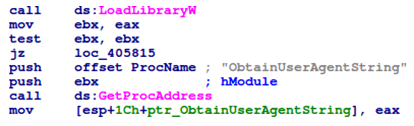
However, this particular variant uses a slightly different implementation and tries to obtain the default Windows user-agent string.
If this is not successful, the sample uses its hardcoded version:
Like the Linux variant, it connects to its C&C server in the same way: once per minute it sends a heartbeat signal via HTTP (GET /v1). To retrieve commands or to upload or download additional resources, it uses TCP Port 433.
It uses almost the same filename templates to save the obtained screenshots, audiocaptures, keylogs and other arbitrary data. Unlike the Linux variant, in this sample the keylogger is active. Below you can see the content of a keystroke logfile, located in %TEMP% and created by this sample:
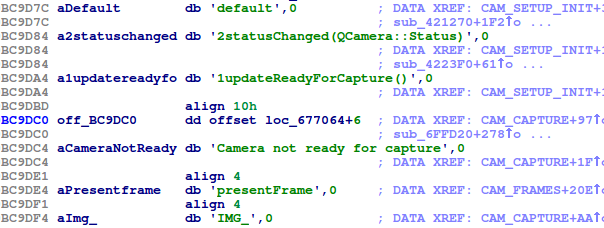
And again, we spotted some unexpected code. The following screenshot shows references to code which is able to capture images from a connected camera, such as a built-in webcam.
Similar to the Linux version, the author left quite a number of suspicious strings in the binary. The following string is surprisingly honest.
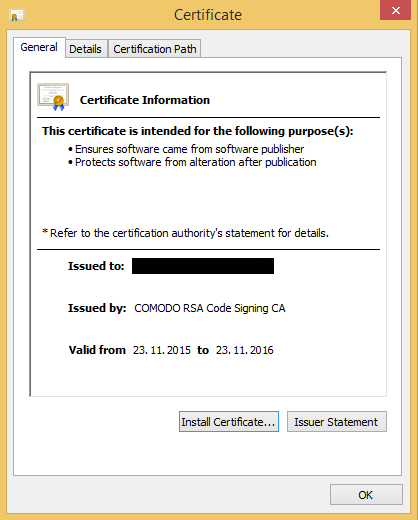
From the criminal’s point of view, it’s important that the software looks legitimate and that Windows doesn’t asks the user for confirmation prior to execution of unknown software. On Windows machines this can be achieved by using Trusted Code Signing Certificates. In this particular case, the criminal managed to sign the binary with a trusted certificate from “COMODO RSA Code Signing CA”.
We detect this type of malware as Backdoor.Win32.Mokes.imv.
What’s next
Since this software was intentionally designed to be platform independent, we might see also corresponding Mac OS X samples in the future. Update: We found it. See Update section below.
Update
(2016-02-01 10:45 UTC): We just got Backdoor.Win32.Mokes.imw. This is the first time we see a variant of Mokes, which comes with the audio capture module activated. The malware creates a new audio file every 5 minutes.
(2016-09-07 13:19 UTC): We just come across the OS X variant of this malware and posted an analysis on this blog.
IOCs
Backdoor.Linux.Mokes.a
c9e0e5e2aeaecb232120e8573e97a6b8
$HOME/$QT-GenericDataLocation/.mozilla/firefox/profiled
$HOME/$QT-GenericDataLocation/.dropbox/DropboxCache
$HOME/.config/autostart/profiled.desktop
$HOME/.config/autostart/DropboxCache.desktop
/tmp/ss0-$date-$time-$ms.sst
Backdoor.Win32.Mokes.imv & .imw
f2407fd12ec0d4f3e82484c027c7d149 (imw)
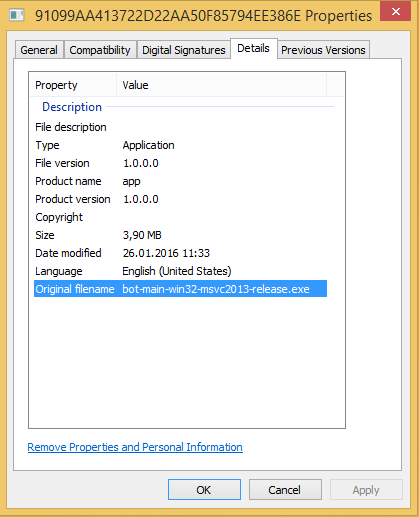
91099aa413722d22aa50f85794ee386e (imv)
%AppData%\Skype\SkypeHelper.exe
%AppData%\Skype\version
%AppData%\Dropbox\bin\DropboxHelper.exe
%AppData%\Dropbox\bin\version
%AppData%\Google\Chrome\nacl32.exe
%AppData%\Google\Chrome\version
%AppData%\Google\Chrome\nacl64.exe
%AppData%\Google\Chrome\version
%AppData%\Mozilla\Firefox\mozillacache.exe
%AppData%\Mozilla\Firefox\version
%AppData%\Hewlett-Packard\hpqcore.exe
%AppData%\Hewlett-Packard\version
%AppData%\Hewlett-Packard\hpprint.exe
%AppData%\Hewlett-Packard\version
%AppData%\Hewlett-Packard\hpscan.exe
%AppData%\Hewlett-Packard\version
%AppData%\Adobe\Acrobat\AcroBroker.exe
%AppData%\Adobe\Acrobat\version
%TEMP%\aa$n-$date-$time-$ms.aat (imw)
where $n is a decimal hash-value calculated from the soundcard’s name
%TEMP%\ss0-$date-$time-$ms.sst
%TEMP%\dd0-$date-$time-$ms.ddt
%TEMP%\kk$date.kkt
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “%PERSISTENT-FILENAME%”, “%PERSISTENT-FILEPATH%”
where %PERSISTENT-FILENAME% is one of the filenames above
and %PERSISTENT-FILEPATH% is the corresponding path
From Linux to Windows – New Family of Cross-Platform Desktop Backdoors Discovered























a.oryema
very interesting, I had this Bios Malware in my laptop which can not be detected and run in separate memory, I move away from windows, formatted hard drive, clean install Linux mint 17.2, what I notice after installation, there are some applications like Desk top shearing and many more was which I did not install is already there before I did software updates, I removed them, but when the window was due to restart, it was giving warning that unknown signal from unknown source was received, modem Manager, service name, I forced manually restart and immediately at that precised time I saw command was being written very fast to left hand corner and the window closes, after I tried to open, I log in normally but the window can not open.
I went to recovery mode, i sow a lot was installation which previously was not thinking, remote execution files, Net Bios connection and many more, but the recovering came to abraft end after cpu fan booted so laud and could not proceed .Now the malware block the recovery from registry by default. all what you explain above is now exactly what is happening in my laptop, I had GUFW fire wall to prevent UDP, TCP close all the ports but still it was transmitting data, also had antivirus there but malware prevented it from updating.
Dennis
Great work and a proof that a av is necessary on a Linux workstation.
Abdullah
Linux works differently form windows, for instant in Linux systems we do not download software from the web nor give execution permission for unknown software -no software could run without explicit permission-, unlike windows, were just inserting an unknown CD drive will trigger the executable -.exe- file automatically.
No, we do not need Anti-Virus in Linux as we need more awareness.
Take an example, the impact surface of ransom software would mostly be on Windows & Mac OSX, since both the users of these systems intend to download different software from the web, relying on others software vendors to do different work, while on Linux almost all the software are free & open sourced, so we do rely on our self mostly and trust each other -for obis reasons-.
augustine oryema
well, as it as been proved and I am the casualty of it, the cross platform does exist, as we talk now, I am unable to use my laptop now, the Linux mint is unable to open, block and the recovering also block. I Had this denying service Trojan from window 10, it shut down window 10. I order a copy of CD from US and install in my lap top, but the window can not restart saying it received signal from unknown source, window is shutting down, Modem Manager, its’ service Name. I forced close from power button but then a command run very fast to left top side of the screen and window closed. push on power button log into and the window stay like that with the Linux Mint Logo in the middle of the screen, it will not open, went to recovering mode and it was at that point that I saw malware had finish setting all remote setting, connecting through Net Bios, shearing files all that was happening in window 10 was now there, but then it block recovering from going on.
when I look at the application installed, I found out that I now have desktop shearing, personal file searing, it down load packages automatically without your knowledge something you will not believed, I installed Gufw fire wall and block all UDP ports from 67:64882 and TCP ports Samba, I also installed Clamtk antivirus but Malware block it from updating, well this is BioMalware and can not be remove, I gave up now.
If you want to find out by yourself, I will give you one of the infected hard drive, install Linux on it and you will see for yourself.
Kevin
Quite a naive stance you have there 🙂 Typical of Linux elitists. No, Windows does not automagically launch .EXEs just by inserting a disk. It was a huge deal when Stuxnet exploited a zeroday in the autorun feature of USB flash drives (please note, the autorun feature does NOT automatically run any .EXE files.) Linux can be exploited just like Windows can. The difference being that Windows is a much larger pool of potential victims than Linux, not that Linux is a much more hardened system.
If you do minimal research, you will find a number of different vulnerabilties on Linux. The most recent I saw was a huge thing on ArsTechnica where Dan Goodin writes “For almost three years, millions of servers and smaller devices running Linux have been vulnerable to attacks that allow an unprivileged app or user to gain nearly unfettered root access.”
You can find the article here:
http://arstechnica.com/security/2016/01/linux-bug-imperils-tens-of-millions-of-pcs-servers-and-android-phones/
In response to downloading software from the “web”… This is more or less silly. Yes, Linux software repositories are “the web” and are just as capable of carrying malicious software as any other source. By that same token, if you use only trusted repositories from reliable sources, that’s akin to a Windows user only downloading trusted software from trusted sources. Totally besides that, Linux users can download and launch programs just like Windows users can.
Jules
HELP! I’m not too tech savvy but pretty freakin’ sure my laptop’s compromised too. Hasn’t shut down on me…completely…yet…(fingers crossed), but it’s doing all sorts of crazy things. I too saw the command being written very fast in the corner-like so fast it was a glimpse & then it was gone-disappeared-vanished completely.
Is this “COMODO RSA Code Signing CA” even a valid certificate group (not sure what you call them)? I know i’ve seen this one on my computer & the same for the %TEMP% & %AppData%….What you’re telling me is I should never see things files or anything on my laptop that starts with the % stuff? or is that incorrect?
Yep & the long backdoor file names (?) locators? Seen those too.
No making fun, but, I even purchased a separate subscription to a VPN provider that was on the Today show & a bunch of other reputable, supposed, places.
So….now what do I do???? I use my laptop for school (even though i’m a much older student) & the past couple days it’s like its been trying to operate from windows 8 & windows 10….2 different control panels (or one & then settings) then when i tried to go to microsoft’s link “how to tell if it’s microsoft link” pages keep timing out. my microsoft account’s all jacked up now.
for the future….what’s the best laptop/desktop (per your reviews) as far as safety goes & what should i steer clear of for fact? and do you invest in another, better, VPN subscription?
Any answers & help you can provide would be very awesome & so greatly appreciated for real!
a.oryema
I can only say you May be lucky if that Trojan is not yet taken control of your processor, and if it does, then forget about using Microsoft window, My laptop is completely taken over, it does not matter what window I installed, Malware just back on reboot, it changed the bios set up and controlling the processor.
I move to Linux Mint 17.3 Mate edition, from time to time, this malware had been trying to infiltrate my Linux installation and learn how to deal with. After installation of new Linux and it read to restart, it will come in and start interfering, it will prevent services, remove browsers on launch, and make Linux unusable.
I removed the laptop battery, plug in main, install clean Linux is ready to restart, I remove power main from the laptop and the installation is good, I install ” GUFW” fire wall,block port from 67:65199/udp and Samba 137,138udp,139,445tpc. you will see inside GUFW so many port being generated and if you do not block, it will still interference/block services.but some time it will generate more unknown ports inside firewall, as it happen twice to me, software update appear, but it was a from unknown source and Linux was saying it was unauthorized, but could not believed something can get in because I set software source code, I run it any way but it crushed Linux, the second time it happened again, I first closed the the new port, I check the update, it was for Google chrome and curl, I ignore it, but Linux was giving warning saying it was unauthenticated, I should not run. Now I know the trick, will check each update before I run if it is there in package manager, will get it from there, safer.
too much unknown is happening and this cross platform is real.
Install fire wall Gufw, will keep you safe and you will see all it attempt to come in.
monopoly
“The difference being that Windows is a much larger pool of potential victims than Linux, not that Linux is a much more hardened system.”
Unfortunately this is a LIE.
I have a mac, a windows pc, and a linux desktop.
Only found it in windows, not in mac or linux. Just did a simple scan today, surprised by how many virus I got in it.
I guess this is due to the pool and insecure design of software/package management in windows, compare to linux and mac.
In windows people normally download an exe from some website and install it, and when installing you got all privileges for it when ask (most user did that, believe me). You have no clue what it’s including, only cross finger it’ll not crash your computer too quick. Also windows has a very BAD design of user management, such as any local user will default has all privileges, make windows a completely security nightmare.
In contrast linux or mac use trusted software management like brew or apt/yum/packman , when installing something, you know what you’re doing.
Mike Falkenstein
Some how I got this and is OSX variant Backdoor.OSX. Mokes.a and a error codeox80070424 result is Windows Defenderfile will not turn on and get a message file does not exist. Was woundering if I do a complete Windows10 reinstall would clear it up.
augustine
if you got antivirus software, some of them will take control of window firewall and that is normal.
you can go to service and turn window defender to automatic.
If you got window 10 then you do not need to install new window, you can reset that same window, either to remove everything or leave your files and setting intact.
chris dean
very clever