
The cybercrime business is really no different from other types of business such as pasta making or selling spare parts for cars. It has its own expenses and overheads. A hacker, just like any businessman, tries to save on attacks and keep their costs down.
In general, a web attack needs a domain name and hosting in order to spread malicious files. Everything is fairly straightforward with regards to hosting: the criminals either buy it themselves or use cracked servers to store their files. Protective measures cannot extend to the blocking of whole file servers, as legitimate data may also be stored on them.
Domain names can be blocked quickly by integrated security solutions. Therefore, a black hat has to constantly change the domain names from which their attacks originate.
Registration of a second-level domain name is relatively expensive (on average from $5 to $20 per unit), which is why cybercriminals often try to save money and use free third-level domain names.
Lately, the co.cc and cz.cc services have been at the forefront of cybercriminal activity. Hundreds of domain names were being registered every day, spreading a huge amount of malware over the Internet.
However, a couple of weeks ago an unprecedented event occurred: Google removed all resources located at co.cc from its search results.
As a result, it was no longer profitable for cybercriminals to register domain name in this zone, especially for those who make use of search engines (e.g. for spreading rogue AV with the help of black search engine optimization).
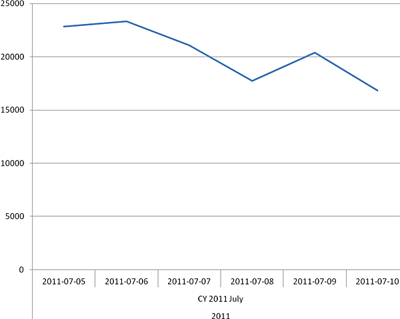
Number of users protected from attacks from domain names in the co.cc zone
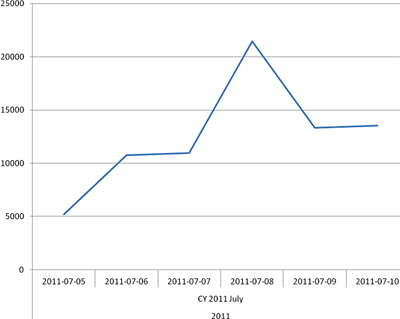
By analyzing the amount of users attacked from co.cc domain names, we can infer that there is a downward trend. However, it would be foolish to believe that the cybercriminals have given up and stopped attacking users. Domain names in the cz.cc zone continue to be used. Moreover, the number of users being attacked is growing steadily.
Number of users protected from attacks from domain names in the cz.cc zone
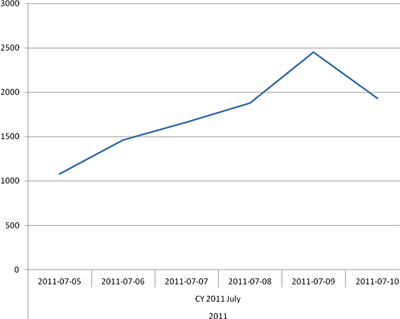
The same situation is seen with another DNS provider – uni.cc.
Number of users protected from attacks from domain names in the uni.cc zone
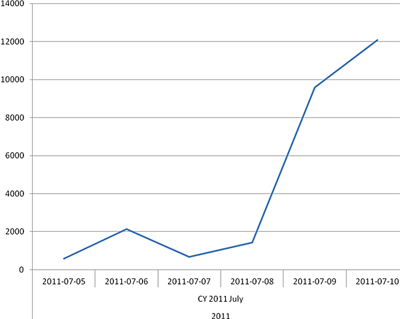
Finally, the biggest increase is in the bz.cm zone.
Number of users protected from attacks from domain names in the bz.cm zone
The above data suggests Google’s actions may not have been very beneficial. On the one hand, they have removed a huge amount of malicious resources from their resource. On the other hand, they have forced out a lot of legitimate websites. Moreover, as there are many services like co.cc, the cybercriminals will quickly switch over to another service, making the blocking of just one zone completely pointless.
We are constantly in touch with the owners of resources offering free registration for third-level domain name services, so that we can quickly block domains that are used to launch attacks on users.
We recommend that users be very careful when dealing with links to free hosting or to domain names in zones that offer free services.



















From Cocos Islands to Cameroon