
Firefox (FF) users should be aware of a use-after-free vulnerability affecting Firefox versions 3.6.11 and earlier. The security team at Firefox has been working on getting a patch out since at least early Tuesday morning, delivering a v3.6.12 release candidate available for brave nightly build developers and testers last night.
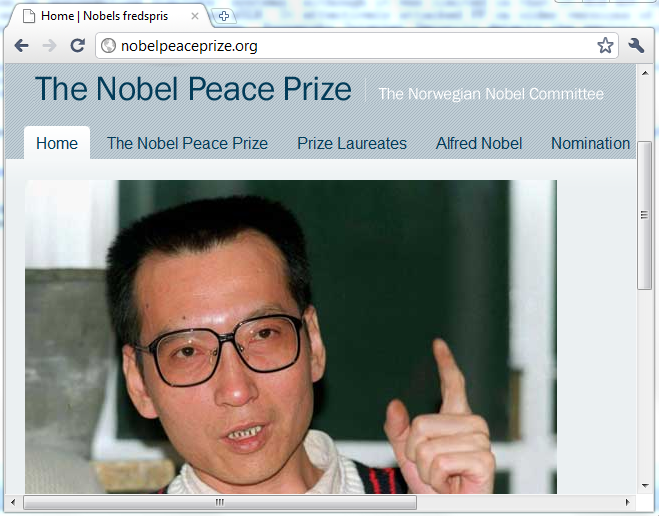
A zero day exploit attacking this vulnerability was used at the compromised Nobel Peace Prize website to drop a trojan on unsuspecting visitors’ systems, although the 0day was limited in that it did not implement well known ROP or JOP techniques (link to zipped pdf of VB2010 presentation slides) to effectively attack defensive technologies on newer Windows Vista and 7 platforms like DEP and ASLR. It effectively attacked newer FF on older versions of Windows.
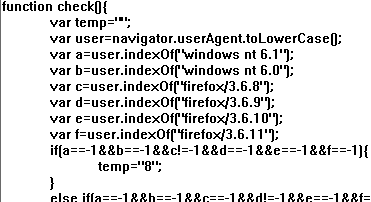
To deal with this inadequacy, the attackers’ javascript unusually checked for only newer versions of Firefox browsers and older versions of Windows. It only delivers the exploit code for those combinations. The writers must have felt rushed to get this exploit out.
Firefox users also can prevent attacks on the vulnerability by using the NoScript add-on or disabling javascript in their FF browser. Kaspersky Internet Security detects and prevents the exploit code as Exploit.JS.CVE-2010-3765.a.
UPDATE: Mozilla Firefox build 3.6.12 is out! In Firefox 3.6.11, you can click Help -> Check for updates… It includes the patch for msfa2010-73, “Heap buffer overflow mixing document.write and DOM insertion”, a problem otherwise described as the previously posted “use after free”. Readers interested in technical details of the vulnerability should check out the bug link previously posted above, the report “Interleaving document.write and appendChild can lead to duplicate text frames and overrunning of text run buffers” is now open to the public. Updating Firefox v3.6.11 takes under a minute, but requires a Firefox restart. The browser makes a best effort to restore any tabs that you may have had open at time of restart.
At this point, I suppose the dirty secret buried amongst the “FF 0day are rare!” hype is that the numbers of users hit with this stuff right now are extremely low, for both the Firefox exploit itself and the “Belmoo” trojan that was delivered with it. But now is not the time to be lackadaisical about patching or maintaining security software — the exploit will predictably be enhanced with ROP (or other DEP/ASLR bypasses) and added to pages all over the web over the next couple of weeks and the following months. Dependent rss reader software is vulnerable too, so expect updates to those packages, and be aware that they run javascript and may be vulnerable.


















Firefox Tricked – Current 0day