
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason – money. While governments and organizations have been investing in new methods to protect financial services, malicious users have been investing in how to bypass them. This has fueled many changes in how online financial services and payment systems, large banks and POS terminals are being used.
The past year has seen a wide range of changes in the financial cyberthreats landscape, with new infiltration techniques, attack vectors and extended geography. But perhaps the most interesting thing to have happened is the changes in how people are victimized. With block chain and cryptocurrency now becoming popular, many new means of payment emerged on both on the white and black markets – attracting unwanted criminal attention.
Cryptocurrency became the hottest topic in 2018. Definitely being the story of the year, it stole the headlines from the threat of ransomware, turning the eyes of the cybersecurity community to a new danger. Wherever users were eager to pay for something with cryptocurrency – criminals were there. Threats were delivered in two ways – enriching malware with mining capacities to capitalize without noise and attacks on cryptocurrency infrastructure (wallets, exchanges, etc.). Even major APT actors like Roaming Mantis tried to capitalize, not to mention malicious software like PowerGhost; basically a cryptocurrency mining multi tool. As it was also pointed out, Lazarus, one of the most active financial predators in 2018, gradually expanded its list of targets. The latter now includes banks, fin-tech companies, PoS terminals, ATMs, as well as crypto-exchanges.
In the summer, we also covered an interesting case that proves the above – Lazarus was found to be hitting a cryptocurrency exchange with a fake installer and macOS malware. In this case, criminals created special software that looked legitimate and carried out legitimate functions. However, the program also uploaded a malicious update that turned out to be a backdoor. This is a new type of attack, which infects its targets via the supply chain; one of the key scenarios of the past year. This became one of the most creative attacks seen in 2018.
However, several months after that, the cybersecurity landscape brought an even bigger surprise to the community, yet again pointing out that even traditional, and experienced, financial enterprises could be endangered. In December, Kaspersky Lab revealed the DarkVishnya operation: a new series of unprecedented cyber-robberies targeting financial organizations in Eastern Europe. Incident responses, provided by our experts, discovered that in each case the corporate network was breached through an unknown device, controlled by the attackers, which had been smuggled into a company building and connected to the network. At least eight banks in the region have been attacked in this way, with estimated losses running into tens of millions of dollars. The conclusion here is simple – even when investing into cybersecurity, you may never know what how a cybercriminal will attack you. We all should be twice as vigilant.
This are a worrisome sign. While banks are experienced and have learnt how to improve their defenses, young fin-tech companies and crypto-exchanges could face a higher risk, due to the infancy of their security systems. Also, new unprecedented attack methods should be a warning for traditional financial organizations to be on guard.
Another cause for concern in that criminals decided to not only focus their efforts on financial services, but also on the financial departments of industrial companies, where payments of hundreds of thousands of dollars would not cause much suspicion. In the summer of 2018, Kaspersky Lab experts revealed a new wave of financial spear-phishing emails disguised as legitimate procurement and accounting letters that hit at least 400 industrial organizations in an attempt to earn money for cybercriminals.
We should also not forget about ATMs and treat its security seriously as within the last year, Kaspersky Lab specialists discovered six new families, meaning that there are now more than 20 of this kind. The greatest damage associated with attacks on ATMs was caused by infections from internal banking networks, such as FASTCash and ATMJackPot, which allowed attackers to reach thousands of ATMs. Apart from that, 2018 gave birth to a new toolkit for stealing money directly from such machines – we dubbed it KoffeyMaker.
Wrapping up on big businesses, the industry also witnessed good news – in 2018, police arrested a number of well-known cybercrime group members responsible for Carbanak/Cobalt and Fin7, among others. These groups have been involved in attacks on dozens, if not hundreds of companies and financial institutions around the world.
Going one level lower – from big organizations to small and medium enterprises – there were also a lot of attacks on organizations that use banking systems. Kaspersky Lab’s machine learning-based behavioral analysis system detected several waves of malicious activity related to the spread of the Buhtrap banking Trojan when attackers embedded their code in popular news sites and forums.
Moving down one more step – from SMEs to individual users – we can say that 2018 didn’t give the latter much respite from financial threats. Infamous mobile bankers are still there, hunting for money. Considering the above mentioned changes in the landscape, it is of no surprise that they expand the capacities, often combining various functions – like Rotexy that across the years have evolved to being banker and ransomware simultaneously. Some of them add mining capacities to ensure they make a profit. Other actors invested in new ways to compromise users – for instance, in 2018 Kaspersky Lab experts detected quite a rare Chrome extension designed to steal credentials.
The presented report continues the series of Kaspersky Lab reports (see here and here) that provide an overview of how the financial threat landscape has evolved over the years. It covers the common phishing threats that users encounter, along with Windows-based and Android-based financial malware.
The key findings of the report are:
Phishing:
- In 2018, the share of financial phishing decreased from 53.8% to 44.7% of all phishing detections, still accounting for almost a half of overall detections.
- Around one in five attempts to load a phishing page blocked by Kaspersky Lab products is related to banking phishing.
- The share of phishing related attacks to payment systems and online shops accounted for almost 14% and 8.9% respectively in 2018. This is slightly less (single percentage points) than in 2017.
- The share of financial phishing encountered by Mac users slightly grew, accounting for 57.6%.
Banking malware:
- In 2018, the number of users attacked with banking Trojans was 889,452 – an increase of 15.9% in comparison with 767,072 2017.
- 24.1% of users attacked with banking malware were corporate users.
- Users in Russia, Germany, India, Vietnam, Italy, US and China were the most often attacked by banking malware.
- Zbot and Gozi are still the kings when comes to most widespread banking malware family (over 26% and 20% of attacked users), followed by SpyEye (15.6%).
Android banking malware:
- In 2018, the number of users that encountered Android banking malware more than tripled to 1,799,891 worldwide.
- Just three banking malware families accounted for attacks on the vast majority of users (around 85%).
- Russia, South Africa, and the United States were the countries with the highest percentage of users attacked by Android banking malware.
Financial Phishing
Financial phishing, one of the most typical ways for criminals to make money, doesn’t require a lot of investment to be potentially profitable. If successful, criminals receive credentials that can either be used to take the money or can be sold for a good price.
This combination of technical simplicity and effectiveness makes this type of malicious activity attractive to criminals. As Kaspersky Lab’s telemetry systems show, this type of activity accounts for around half of all phishing attacks over the past few years.
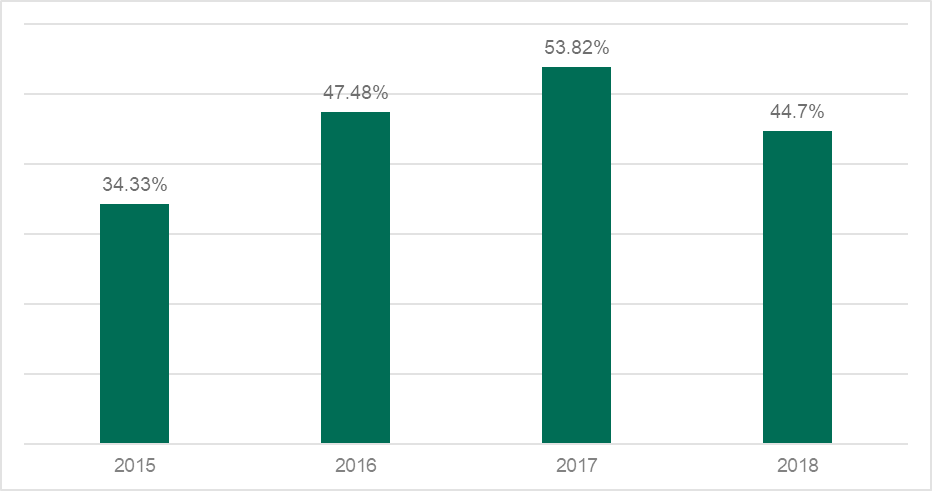
Fig. 1: The percentage of financial phishing attacks (from overall phishing attacks) detected by Kaspersky Lab in 2015-2018
In 2018, Kaspersky Lab’s anti-phishing technologies detected 482,465,211 attempts to visit different kinds of phishing pages. Of those, 44.7% of heuristic detections were attempts to visit a financial phishing page – almost 10% less than the share of phishing detections registered in 2017 (when it was 53.8%, the highest percentage of financial phishing ever registered by Kaspersky Lab).
This was mainly due to the increase in other phishing attacks categories. But first, let’s have a closer look on financial categories.
Kaspersky Lab categorization considers several types of phishing pages as “financial” – banks, well known payment brands such as PayPal, Visa, MasterCard, American Express and others, and internet shops and auction sites like Amazon, Apple store, Steam, E-bay and others. In 2018 all of them experienced slight relief: the share of phishing attacks against banks, payment systems and online shops decreased by 5.3, 1.8, and around 2 percentage points respectively.
While in 2017 for the first time in our observations, payment systems and online shops hit the top three in all categories of phishing detections, 2018 became the year of going back to normal with global online portals being in first position. However, the presented chart shows that almost every second phishing attack was financially-related.
We believe that this change happened due high media attention to targets like Facebook amid various scandals across the year. If we have a look on the global internet portal category, it fell from second place in 2016 with 24.1% to fourth place in 2017 with 10.9%. In 2018 it restored its position, accounting for over 24%.
At the same time, the victimology has not experienced any change – top transnational banks, popular payment systems and internet shops and auction sites are still the most appealing targets for cybercriminals.
Financial phishing on Mac
MacOS has been continuously considered relatively safe platform when it comes to cybersecurity due to small number of malware families that targets it. However, phishing is OS-agnostic criminal activity – it is all about social engineering. Moreover, according to Kaspersky Lab’s statistics, MacOS users often face phishing threats – if not with the same frequency as other users.
In 2016, 31.4% of phishing attacks against Mac-users were aimed at stealing financial data. This is almost half that seen in 2017, when 55.6% of financial attacks blocked by Kaspersky Lab were financially-themed. The past year also indicated slightly growth with overall share at the level of 57.6%, meaning that the threat is not fading.
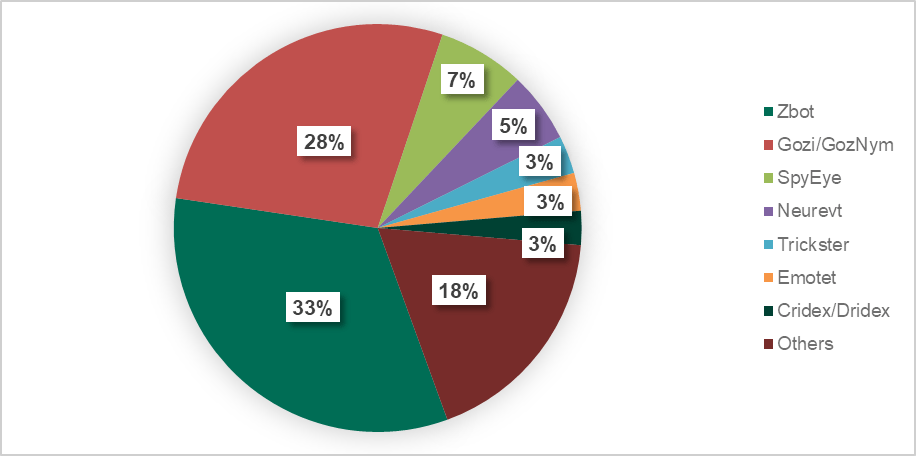
Overall, in 2017 the split looked like this:

Fig. 4: The distribution of different types of financial phishing detected by Kaspersky Lab on Mac in 2017
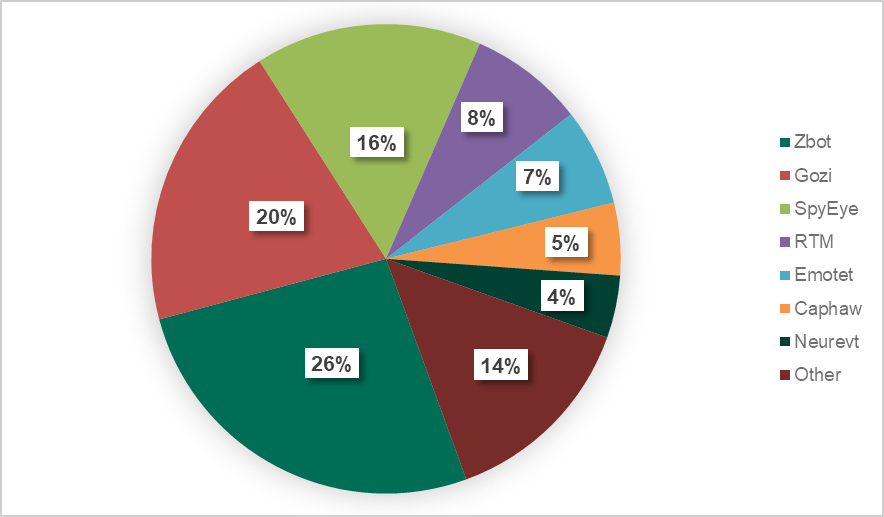
One year later, the ‘Other’ category slightly fell, leading to the overall growth of financially related attacks.

Fig. 5: The distribution of different types of financial phishing detected by Kaspersky Lab on Mac in 2018
All in all, our data shows that the financial share of phishing attacks on Macs is also quite solid – as seen for Windows. Let’s have a closer look at both categories.
Mac vs Windows
In 2017, we found out an interesting twist when Apple became the most frequently used brands in the online shop category both in MacOS and Windows statistics, pushing Amazon down to the second place in the latter platform. Even more interesting is that in 2018 Apple has kept its position in Windows statistics, but Amazon went back to leading MacOS statistics for the first time since we started tracking this activity.
| Mac | Windows |
| Amazon.com: Online Shopping | Apple |
| Apple | eBay |
| Alibaba Group | Amazon.com: Online Shopping |
| eBay | MercadoLibre |
| Americanas | Steam |
| groupon | Alibaba Group |
| Bell Canada | Americanas |
| Shopify | Netflix Inc |
| Hostway | Wal-Mart Stores, Inc. |
Fig. 6: The most frequently used brands in ‘online shop’ financial phishing schemes
When it comes to attacks users of payment systems, the situation is as follows:
| Mac | Windows |
| PayPal | Visa Inc. |
| Visa Inc. | PayPal |
| MasterCard International | American Express |
| American Express | MasterCard International |
| Skrill Ltd. | Cielo S.A. |
| adyen payment system | qiwi.ru |
| Authorize.Net | alipay |
| qiwi.ru | Skrill Ltd. |
| Perfect Money | Ripple |
Fig.7: The most frequently used brands in ‘payment systems’ financial phishing schemes
Overall, the situation is more or less the same apart from the fact that Paypal overrun Mastercard and took the first ranking in MacOS statistics.
The tables above can serve as advisory lists for the users of the corresponding systems: they illustrate that criminals will use these well-known names in an attempt to illegally obtain user payment cards, online banking and payment system credentials.
Phishing campaign themes
Apart from the traditional campaigns that will be covered below, there was one distinctive feature in phishing disguises in comparison with 2016 and 2017 – entertainment. While it is not fully financially related, criminals still could steal users’ credentials or account for sale or personal use. The list of topics is no longer limited to fairly old copies of online banking, payment systems or internet shop web pages.
Here is a closer look on how the most targeted sectors were movies streaming services.
Digital gaming platforms.
Typical commercial and payment brands were also targeted –usually urging a victim to enter credentials as soon as possible.
Of course, by clicking the link or entering the credentials, a user would not get access to their account – they would just pass their important personal information on to fraudsters.
This is one of the most common tricks to intimidate a victim – the threat of blocking or breaking in to an account (“your account has been suspended”).
Don’t show your credit card data to strangers
Due to the human nature and social engineering, phishing has been in the cybercriminals’ arsenal for years, being a major tool not only for monetization, but also for major APT actors as a method to initially compromise a targeted system.
That said, always stay vigilant. Double check the legitimacy of the website while paying online. Double check the legitimacy of emails, especially if they urge you to do something – like change your password.
If you can’t be sure of the above – don’t click the link.
And don’t forget to use a proven security solution with behavior-based anti-phishing technologies. This will make it possible to identify even the most recent phishing scams that haven’t yet been added to anti-phishing databases.
Banking malware
When discussing financial malware in this paper – for clarity – we mean the typical banking Trojans, designed to steal the credentials used to access online banking or payment system accounts and to intercept one-time passwords.
Across 2016, there was a steady growth in the number of users attacked with any kind of financial malware – after falls in 2014 and 2015. 2017 and first half of 2018 has seen falls once again. In 2017, the decrease returned with the number of attacked users falling to 767,072 from 1,088,933 users worldwide in 2016 – almost a 30% decline.
However, a sharp increase in May to November 2018 has changed the landscape, rebalancing the decline and overall growing to 889,452 by 15.95% in comparison with the previous year. This is the first incident of year-to-year growth since 2016. This happened due to explosive growth in RTM banker activities that would be explored bellow.
The geography of attacked users
As shown in the charts below, more than half of all users attacked with banking malware in 2017 and 2018 were located in only ten countries. In 2017, the leader was Germany, followed by Russia and China.
Here is what happened in 2018:
For the last year, Russia has outrun Germany. India did the same to China, closing the top three ranking. The latter at the same time dropped to the seventh position. Overall, picture looks more or less stable with the leader occupied about one out of five users, while the ‘Others’ category accounts for around 40% of the share.
The type of users attacked
2017 has shown a slight growth of this sector, confirming our hypothesis that criminals are shifting to targeted attacks on business – despite the overall fall of banking malware detection, the corporate users’ share is still showing a steady rise.
This is alarming, as we see that for the last three years in a row, almost every fifth banking malware attack was focused on the corporate sector. And the share is growing. The reason behind this is clear – while attacks on consumers will only give a criminal access to banking or payment system accounts, successful hits on employees will also compromise a company’s financial resources.
2018 has once again proven this:
The share of corporate users has grown by over 4 percentage points.
The main actors and developments
The banking malware landscape has been continuously occupied by several major players. In 2017, Zbot was the leader, actively challenged by Gozi.
The latter increased its share by more than 10 percentage points, while Zbot decreased its own from more than 44% to 32.9%.
One more particularly interesting thing about 2017 was that the share of the ‘others’ category, which more than doubled, indicating that the financial threat landscape is becoming more and more diverse. That said, while the proportion of leaders was reducing, smaller players were becoming more active.
2018 saw a trend in the major players decreasing their attacks – Zbot fell to 26.4% and Gozi to a little bit over 20%. At the same time, ‘other’ category also reduced. The landscape is obviously stabilizing with “middle-class” families strengthening their positions.
This is very inconvenient for the security research community as it is much easier to track several big players than many attackers that are small and flexible in their tactics.
Of particular interest was the RTM banking Trojan, whose explosive growth pumped up the figures for 2018. Kaspersky Lab has warned about this family when there was a surge in its activity with the overall number of users attacked in 2018 exceeding 130,000 – an increase from as few as 2,376 attacked users in 2017.
The pace of attacks appears to be continuing into 2019, with more than 30,000 users attacked during the first month and a half of the year, making RTM one of the most active banking Trojans on the threat landscape.
What’s interesting, the Trojan targets not financial organizations per se but rather people responsible for financial accounting in small and medium-sized businesses, with a particular focus on the IT and legal sectors. This makes RTM attacks part of a general trend where cybercriminals are spreading their activities from financial organizations, pulling their attention towards the private sector where entities in general invest less in security solutions. So far, the Trojan has hit mostly companies based in Russia. But there were multiple cases in the industry when successful cyber threats were first used in Russia and later went international. RTM banking Trojan can easily become yet another example of the same development cycle.
Kaspersky Lab estimates that during the course of two years, the attackers may have conducted multiple illegal transactions, up to a million rubles (the equivalent of $15,104) each.
That is why we urge organizations that can become potential targets of this malware to take preventative measures and make sure their security products detect and block this threat.
We also recommend that users be cautious when conducting financial operations online from PCs in general. Don’t underestimate the professionalism of modern cybercriminals by leaving your computer unprotected.
Mobile Banking Malware
We have reviewed the methodology behind the mobile section of this year’s report. Traditionally, we have analyzed Android banking malware statistics through KSN data gathered from Kaspersky Internet Security solution. But since Kaspersky Lab develops new mobile security solutions and features, statistics gathered from one product alone becomes less relevant. That is why this year we decided to shift to expanded data, gathered from multiple mobile solutions.
And here is the result:
Over the last few years, Android banking malware evolved – with several peaks in 2016. The overall number of attacked users was 786,325.
2017 was more stable and the number of users who encountered mobile malware reached 515,816. But then there was a game changer.
In April 2018 the number of attacked users started to rise rapidly, with the overall figure reaching 1,799,891 – which means that it has more than tripled in just a year. As it can be seen, this was mainly due to two peaks in the periods from April to June and July to September.
Kaspersky Lab experts took a closer look at the reasons why this may have happened.
To do this, they reviewed the most widespread families across the year.
Back in 2017, the distribution of the major families was calm and smooth with the statistic looking more or less balanced.
If we take the overall number of detections, the absolute leaders in 2017 were Asacub, Faketoken and Hqwar. Let’s look at them a bit more closely.
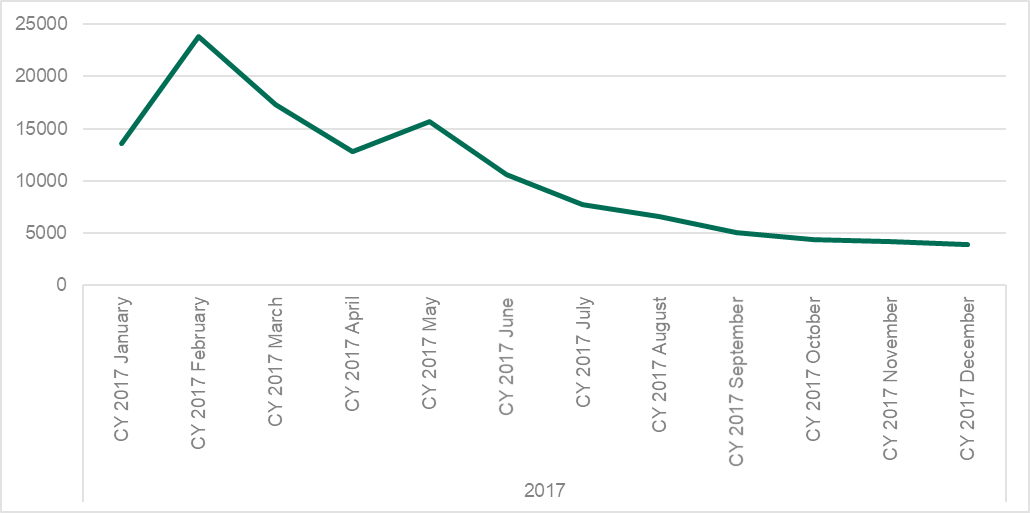
Asacub, constantly evolving malware, is spread via SMS and its distribution is uneven with several peaks across the year:
At the same time, Faketoken evened out its activities, gradually lowering its hits from 13,563 in January, to 3,872 in December.
The third major player in the field, Hqwar, demonstrated an almost identical picture.
2018 was different.
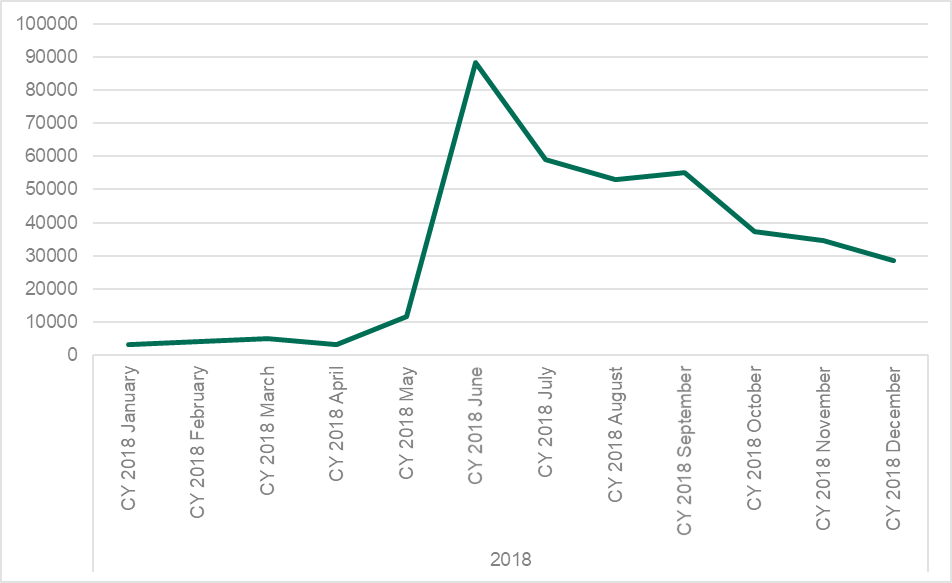
Asacub peaked more than twice to almost 60%, followed by Agent(14.28%) and Svpeng (13.31%). All three of them experienced explosive growth in 2018, especially Asacub as it peaked from 146,532 attacked users in 2017 to 1,125,258.
As the statistics show, this is a general trend as almost all more or less active families ramped up their activities in 12 months. But let’s have a closer look on top three families in 2018.
As graph above shows, Asacub was quite stable across the year apart from two peaks that made it a leader – periods between May and July and July and October.
Agent experienced more consistent spikes – overall it was performing very active from February to April and Aprilto July, with a more stable distribution of attacks – around 20,000 to 30,000 attacked users per month.Svpeng demonstrates another picture entirely. This malware family was not very active for almost half a year, then kicking off in May and growing until June with almost 100,000 attacked users. There was then a gradual fall for the rest of the year.
Geography of attacked users
In previous reports, we calculated the distribution of users attacked with Android Banking Trojans by comparing the overall number of unique users attacked by this type of malware with the overall number of users in a region. There was always one problem – for the majority of detection found in Russia traditionally come from this malicious software due to the prevalence of SMS banking in the region, which allows attackers to steal money with a simple text message if an infection is successful. Previously, the same was true for SMS Trojans, but after regulative measures, criminals have found a new way to capitalize on victims in Russia.
This year we decided to change the methodology replacing the overall number of attacked unique users to the overall number of users registered in the respected region.
In 2017 the landscape was the following:
| Australia | 1.05% |
| Turkmenistan | 0.82% |
| Russia | 0.8% |
| Turkey | 0.46% |
| Kazakhstan | 0.39% |
| Uzbekistan | 0.37% |
| Tajikistan | 0.3% |
| Poland | 0.25% |
| Latvia | 0.22% |
| Germany | 0.22% |
Fig. 28: The top 10 countries with the highest percentage of users that encountered Android banking malware in 2017
In 2018, the picture changed:
| Russia | 2.32% |
| South Africa | 1.27% |
| US | 0.82% |
| Australia | 0.71% |
| Armenia | 0.51% |
| Poland | 0.46% |
| Moldova | 0.44% |
| Kyrgyzstan | 0.43% |
| Azerbaijan | 0.43% |
| Georgia | 0.42% |
Fig. 29: The top 10 countries with the highest percentage of users that encountered Android banking malware in 2018
As we can see, mobile malware is indeed on the rise with the around two-digit growth in the average level of infections in top 10 countries. In 2018, Russia jumped up to first place, followed by South Africa and the US. Australia dropped to fourth position while Turkmenistan left the chart for good.
Major changes to the Android banking malware landscape
While figures tell their own story, there are many more ways to explore changes and developments in the threat landscape. Our key method is the analysis of actual malware found in the wild.
As this analysis shows, 2018 could be the fiercest cybercriminal onslaught ever seen when it comes to malicious mobile software. Last year it seemed that the threat balanced both in terms of number of unique samples discovered and the number of attacked users.
However, 2018 indicated that the situation had radically changed for the worse. The root cause of this rise is not clear, but the main culprits are the creators of the Asacub and Hqwar Trojans. The former has quite a long history – according to our data, the group behind it has been at work for more than three years. Asacub itself evolved from an SMS Trojan that was armed from the get-go with tools to counteract deletion and intercept incoming calls and SMS messages. Later, the creators of the malware beefed up its logic and began mass distribution using the same attack vector as before: social engineering via SMS. Online forums where people often expect messages from unfamiliar users became a source of mobile numbers. Next, the avalanche propagation method kicked in, with infected devices themselves becoming distributors – Asacub would be sent everyone in a victim’s contact list.
However, banking Trojans in 2018 were noteworthy not just in terms of scale but mechanics as well. One aspect of this is the increasingly common use of Accessibility Services in banking threats. This is partly a response to new versions of Android that make it increasingly difficult to overlay phishing windows on top of banking apps, the Trojan lodges itself in the device so that users cannot remove it by themselves. What’s more, cybercriminals can use Accessibility Services to hijack a perfectly legitimate application and force it, for example, to launch a banking app to make a money transfer right there on the victim’s device. Techniques have also appeared to counter dynamic analysis; for example, the Rotexy Trojan checks to see if it is running in a sandbox. However, this is not exactly a new thing, since we have observed such behavior before. That said, it should be noted that combined with obfuscation, anti-dynamic analysis techniques can be effective if virus writers manage to infiltrate their Trojan into a popular app store, in which case both static and dynamic processing may be powerless. Although sandbox detection cannot be said to be common practice among cybercriminals, the trend is evident, and we are inclined to believe that such techniques will become very sophisticated in the near future.
Conclusion and advice
2018 demonstrated that criminals keep updating their malware with new features, investing resources into new ways of distribution and into the development of detection avoidance techniques.
They also expand their list of victims adding new institution and industries to it.
This all means that they still get financial gain out of their activities.
As the above threat data shows, there is still plenty of room for financial fraud operations involving phishing and specific banking malware in this sphere. At the same time, mobile malware regained its power jeopardizing users across the world.
In order to avoid the risk of losing money as a result of a cyberattack, Kaspersky Lab’s experts advise the following:
For home users
- Don’t click on suspicious links. They are mostly designed to download malware onto your device or lead you to phishing webpages, which intend to steal your credentials.
- Never open or store unfamiliar files on your device as they could be malicious.
- Always stay vigilant when using public Wi-Fi networks as they can be insecure and unreliable, making hotspots a prime target for hackers to steal user information. To keep your confidential information safe, never use hotspots to make online payments or share financial information.
- Websites can be a front for cybercriminals, with the sole purpose of harvesting your data. To stop your confidential details from falling into the wrong hands, if a site seems suspicious or is unfamiliar, do not enter your credit card details or make a purchase.
- To avoid compromising your credentials through a mobile banking application, make sure you use the official app for your financial services, and ensure it is not compromised. Download apps only from official app stores, such as Google Play or the iOS App Store.
- To avoid falling into a trap, always check that the website is genuine, by double- checking the format of the URL or the spelling of the company name, before entering any of your credentials. Fake websites may look just like the real thing, but there will be anomalies to help you spot the difference.
- To give you more confidence when assessing the safety of a website, only use websites which begin with HTTPS:// and therefore run across an encrypted connection. HTTP:// sites do not offer the same security and could put your information at risk as a result.
- Never disclose your passwords or PIN-codes to anyone – not even your closest family and friends or your bank manager. Sharing these will only increase the level of risk and exposure to your personal accounts. This could lead to your financial information being accessed by cybercriminals, and your money stolen.
- To help prevent financial fraud, a dedicated security solution on your device, with built-in features, will create a secure environment for all of your financial transactions. Kaspersky Lab’s Safe Money technology is designed to offer this level of protection to users and provide peace of mind. Use reliable security solutions for comprehensive protection from a wide range of threats, such as Kaspersky Security Cloud and Kaspersky Internet Security.
- To keep your credentials safe, it is important to apply the same level of vigilance and security across all of your devices – whether desktop, laptop or mobile. Cybercriminal exploits have no boundaries, so your security needs to be just as widespread to minimize the risk of your information falling into the wrong hands. Use a reliable security solution for storing valuable digital data, such as Kaspersky Password Manager.
For businesses
- Pay specific attention to endpoints from which financial operations are being completed: update the software installed on these endpoints first, and keep their security solution up to date.
- Invest in regular cybersecurity awareness training for employees to educate them not to click on links or open attachments received from untrusted sources. Conduct simulated phishing attack to ensure that they know how to distinguish phishing emails.
- If you use cloud email services, make sure you have installed a dedicated protection for your email – such as Kaspersky Security for Microsoft Office 365 – to strengthen your protection against business email compromise.
- Ensure all levels of your corporate infrastructure are protected, from core data centers to specialized systems in the case of banking infrastructure (such as ATMs). For ATM and POS use solutions designed specifically for these systems, such as Kaspersky Embedded Systems Security, which protect even devices with weak or legacy hardware.
- Provide your security operation center team with access to Threat Intelligence so it remains up to date with the latest tactics and tools used by cybercriminals
- Leverage advanced detection and response technologies, such as Kaspersky Endpoint Detection and Response, part of Threat Management and Defense solution. It makes it possible to catch even unknown banking malware and gives security operation teams full visibility over the network and response automation.
- To ensure protection for their clients, financial institutions should use solutions that can prevent fraud. For example, Kaspersky Fraud Prevention analyzes events that occur during the entire session and prevents fraud in real time.






































Financial Cyberthreats in 2018