
As a security analyst we often get asked the question: “What threats and vulnerabilities do you expect us to see in the future?” This is a very interesting question but also an indication that the way we think about and discuss IT-security is fundamentally wrong. Do we really need to invest time and resources to focus on future threats when we are still vulnerable to attacks that have been discussed for over 20 years?
If you take a look at some of the major breaches we have seen in the past, the attackers did not use zero day vulnerabilities. Also if you look in the exploit kits, only very few are actually equipped with exploits taking advantage of zero day vulnerabilities. To analyze this in depth, Kaspersky researcher David Jacoby joined forces with Outpost24’s CSO Martin Jartelius, gaining access to unique statistics related to technical risk exposures from the vulnerability management vendor and performed several security audits which included both social engineering tests and penetration tests. However, everything was performed without exploiting any vulnerabilities.
We started to analyze the statistics that we obtained and it did not take very long until our theories were proved to be correct. We looked into the frequency of old vulnerabilities, meaning what vulnerabilities are we actually vulnerable against. We chose to include statistics for Sweden and Benelux in this report.
Even the statistics show that we are quite good at protecting ourselves against vulnerabilities which are new, but strangely enough we have a tendency to forget about older vulnerabilities. Some systems are still vulnerable to vulnerabilities older than 10 years.
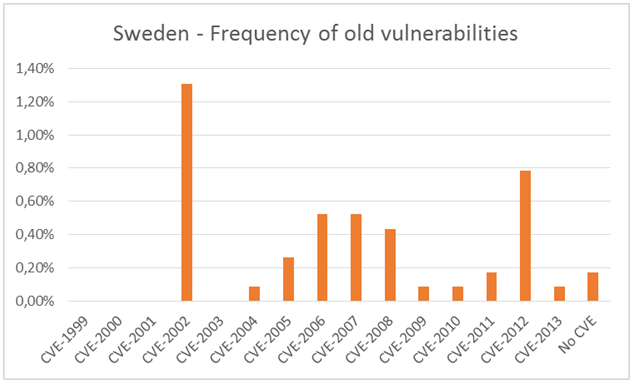
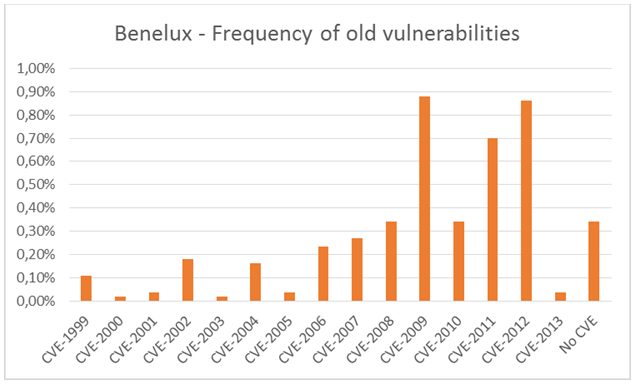
Another interesting question is: ‘what systems do we actually try to secure?’ It’s a very hot topic to talk about critical infrastructure, but what other kind of “public resources” are out there which might be critical? What about for example hotels? Or hospitals? Or radio stations for example?
When doing research it’s always important to get real facts, and one of the ways to do this is to get your hands dirty. During our research we also wanted to perform a practical challenge for a few companies from different industries. The idea was to go out and visit the companies and perform a security audit with a pre-defined checklist based on the results from the research. Our goal was to check and see if they had any systems vulnerable to old threats and also review their security routines and a lot of additional tests. However, only a handful of companies actually wanted to participate in this challenge. We both think that this is absolutely one of today’s key problems; we spend rather more time on new exciting vulnerabilities and threats than actually taking care of the real problems. We decided to perform the challenge anyway, and the results were pretty interesting.
Read the full research paper here.





















Exposing the Security Weaknesses We Tend to Overlook